The SafeBreach Hacker’s Playbook™ already has coverage on attack methods described in **US-CERT (AA20-266A) Lokibot Malware **which notes an increase of the use of Lokibot malware. The attacks described in this US-CERT Alert employ trojan malware to steal sensitive information such as usernames, passwords, cryptocurrency wallets, and other credentials. These simple, yet effective, methods make them an attractive tool for a broad range of cyber actors across a wide variety of attacks. Listen below as SafeBreach Research Team Leader, Tomer Bar, describes the methods outlined by the US-CERT Alert:
19 newly developed playbook methods related to AA20-266A:
- #5488 – Pre-execution phase of aa20-266a_lokibot malware (Host-Level)
- #5489 – Write aa20-266a_lokibot malware to disk (Host-Level)
- #5490 – Transfer of aa20-266a_lokibot malware over HTTP/S (Lateral Movement)
- #5491 – Transfer of aa20-266a_lokibot malware over HTTP/S (Infiltration)
- #5492 – Email aa20-266a_lokibot malware as a ZIP attachment (Lateral Movement)
- #5493 – Email aa20-266a_lokibot malware as a ZIP attachment (Infiltration)
- #5494 – Pre-execution phase of aa20-266a_lokibot malware (Host-Level)
- #5495 – Write aa20-266a_lokibot malware to disk (Host-Level)
- #5496 – Transfer of aa20-266a_lokibot malware over HTTP/S (Lateral Movement)
- #5497 – Transfer of aa20-266a_lokibot malware over HTTP/S (Infiltration)
- #5498 – Email aa20-266a_lokibot malware as a ZIP attachment (Lateral Movement)
- #5499 – Email aa20-266a_lokibot malware as a ZIP attachment (Infiltration)
- #5500 – Write aa20-266a_lokibot malware to disk (Host-Level)
- #5501 – Transfer of aa20-266a_lokibot malware over HTTP/S (Lateral Movement)
- #5502 – Transfer of aa20-266a_lokibot malware over HTTP/S (Infiltration)
- #5503 – Email aa20-266a_lokibot malware as a ZIP attachment (Lateral Movement)
- #5504 – Email aa20-266a_lokibot malware as a ZIP attachment (Infiltration)
- #5505 – Communication with aa20-266a_lokibot using HTTP
- #5506 – aa20-266a_lokibot HTTP post request Real c2
11 existing playbook methods related to AA20-266A:
- #110 – Covert data asset exfiltration using HTTP/s POST (Exfiltration)
- #1693 – Collect Windows system data using CMD (Host-Level)
- #2295 – Accessibility Features (Host-Level)
- #3820 – Extract credentials stored in a browser using WebBrowserPassView (Host-Level)
- #4136 – Execute EXE file using process hollowing (PowerShell) (Host-Level)
- #5275 – Pre-execution phase of lokibot malware (Host-Level)
- #5276 – Write lokibot malware to disk (Host-Level)
- #5329 – Transfer of lokibot malware over HTTP/S (Lateral Movement)
- #5330 – Transfer of lokibot malware over HTTP/S (Infiltration)
- #5331 – Email lokibot malware as a ZIP attachment (Lateral Movement)
- #5332 – Email lokibot malware as a ZIP attachment (Infiltration)
What you should do now
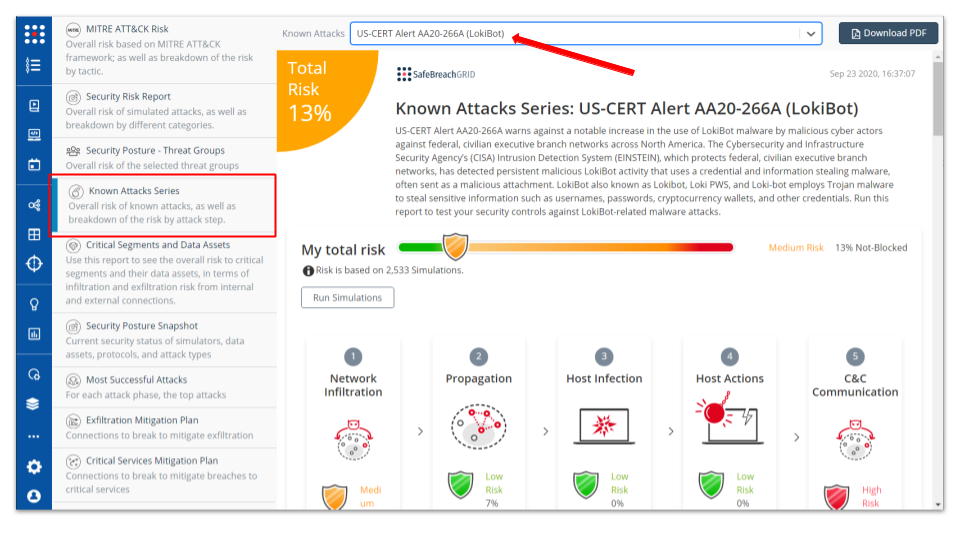
The new attack methods for US-CERT AA20-266A are already in the SafeBreach Hacker’s Playbook and ready to be run across your simulators. The Known Attack Series report is being updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT Alert AA20-266A (Lokibot Malware) report and select Run Simulations which will run all the attack methods.