Summary
The Infy Iranian threat group is probably the most persistent and active Iranian APT ever discovered since 2007. Infy group starts an attack by infecting a victim with Foudre (lightning in French) which collects data from the victim’s machine and exfiltrates it to the C2 server. If the victim is found to be interesting, a second malware called Tonnerre (thunder in French) is installed. Tonnerre includes additional spying capabilities such as a reverse shell and voice recording using the microphone on the victim’s machine. Foudre and Tonnere use a domain generating algorithm (DGA) for generating domain names on the fly. This technique is in use because malware that depends on a fixed domain or IP address can be quickly blocked. So, rather than producing a new version of the malware or setting everything up again on a new server, the malware switches to a new domain at regular intervals.
SafeBreach Labs developed a generic method for breaking Foudre’s domain generation algorithm (DGA). Using this method, we discovered “ROV4”- a new DGA prefix being used by a new unknown executable version of Foudre (probably version 25 and above). This relatively new sample has probably only been used since July 7, 2021. With SafeBreach’s generic method, we were able to predict future C2 domains even before finding the new samples which connect to them. Through our method, we discovered both Foudre and Tonnerre active C2 servers. We also discovered Tonnerre version 15 binary, which is the most updated version of Foudre. The Iranians have recently changed their infection strategy and infected all victims with both Foudre and Tonnerre (except for the victims’ machines that include security controls that pose a threat to Tonnerre such as Kaspersky AntiVirus and deepFreeze). We were able to identify two Iranian victims infected with both Foudre and Tonnerre and a third unknown victim infected with Foudre.
Background
The Infy Iranian threat group is probably the most persistent Iranian APT ever discovered. In earlier research [1], Palo Alto Networks revealed that their first campaign started in 2007. According to research presented at BlackHat 2016 [2], the Iranian threat group tried to regain control over their lost victims’ endpoints by manipulating the traffic in the central Iranian network company and redirecting the sinkhole of Iranian victims to a new C2 server. In 2017, following the lessons learned from the C2 servers’ takeover, the adversary changed the malware arsenal to include a DGA which was discovered in August of that year. This time the internal name of the malware chosen by the adversary was Foudre.
- On February 9, 2021 – Checkpoint and SafeBreach released a paper with a full analysis of Foudre versions 1-22 and Tonnerre version 11 (the full advanced Iranian threat group’s malware)[3].
- On February 18, 2021 – Bitdefender discovered Foudre version 23 [4].
- In June 2021 – Foudre version 24 was discovered with two different variants, one which is installed by a malicious macro and a second – a compressed RAR archive with an mp4.scr extension[5][6]
Breaking Foudre DGA
The first step – Finding the C2 Domains
Foudre DGA generates 101 hostnames for each TLD (.xyz,.688.org,.space) each week using the following formula:
1) crc32(“{}{}{}{}”.format(dgaprefix,date.year,date.month,weeknumber)
2) crc32(“{}{}{}{}”.format(dgaprefix,date.year,date.month,weeknumber+”1”)
…
101) crc32(“{}{}{}{}”.format(dga_prefix,date.year,date.month,weeknumber+”100”)
The CRC32 is serialized with 8 hex digits. hostName = “{:08x}”.format(int(crc))
The dgaprefix is constructed with three capital letters and a digit. Each sample of Foudre has a version number which is reported to the C2 server. The C2 uses the version number in the trojan update process, if Foudre’s code is changed there it will include a new version number. The first Foudre versions used NRV1,NRV2 while Foudre version 24 used RDI4 as the dgaprefix.
For example: ROV420211040 (which stands for year=2021,month=10, weeknumber=40) will generate the domain 6285f7c9.xyz, if Foudre doesn’t receive a response it will use this formula: ROV4202110401 to generate domain name: 61061054.xyz, etc. Our goal is to discover the new Foudre C2 server without the need to discover the new version of the Foudre binary and reverse it to extract the dga_prefix. We found several legit sites providing a long list of all registered domains by date. The average number of new registered servers per day can reach a million domains.
We developed a script that downloads all domain name lists and filters them using several filters:
- The domain name must be exactly 8 characters.
- The domain name includes only 0-9 and a-f characters.
- The domain includes at least one digit and at least one letter.
The filter was effective, leaving only a few possible C2 domain candidates per day.
Contacting those domains with the previous malware logic provided us with several Foudre active C2 domain names without any false positives.
Second step – Brute-forcing the DGA
Once we found active domains, we brute-forced the DGA by generating a domain name for each possible dgaprefix with the corresponding date. Then we compared the generated DGA to the domain name we found to be active for that date. The total space is \~175K (263*10) possible prefixes. We ran the algorithm for a couple of minutes and revealed the dgaprefix.
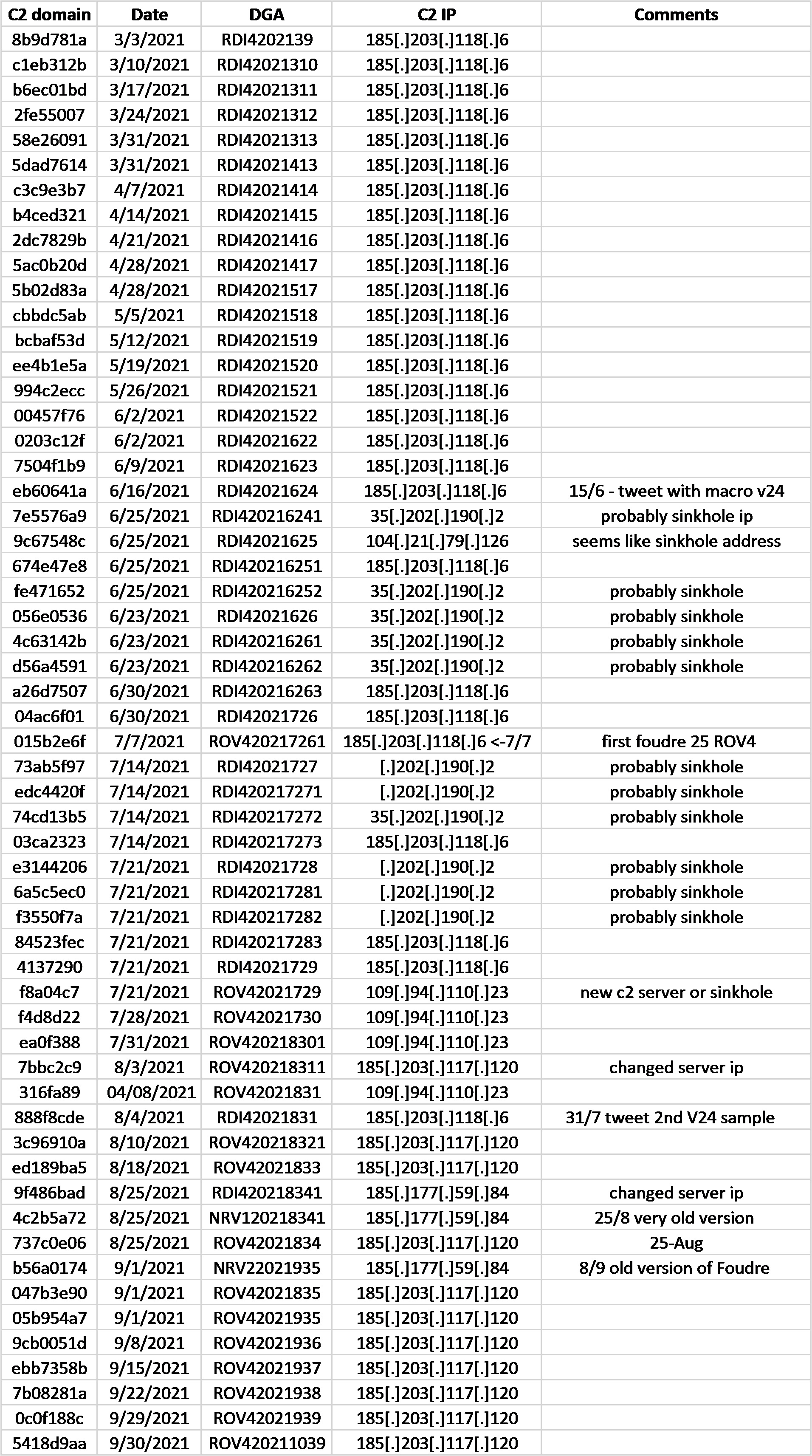
We discovered that the Iranian threat group created Foudre 24 at the beginning of March (only one month after our previous white paper with Checkpoint) and registered the domain 8b9d781a.xyz using the DGA: RDI4202139 (year=2021, March=3, weekNumber=9). The server IP was 185[.]203[.]118[.]6. This method of breaking DGA is not difficult and works in a generic way, quickly, and without false positives.
On July 7, 2021, the Iranian threat group used a new unknown dga_prefix ROV420217261 to generate a new C2 server 015b2e6f.688.org. This is a DGA belonging to an unknown Foudre sample, probably version 25 or above. We believe that this is the Iranian threat group’s reaction to the publication of the Foudre version 24 sample in the middle of June. They continued to use the RDI4 generated domains until August 25 and then switched to the ROV4 generated domains. They also changed the server IP on that date as a failed attempt to evade security researchers.
The following lists the C2 domains and IP Addresses:
As a result of breaking the DGA one can predict future domain names and purchase them before the Iranian threat group does, which will result in blocking the communication of Foudre’s infected machines. That way, Foudre won’t be able to connect to the DGA and get an updated version with the new DGA, which instead will become a zombie that is useless for the Iranian threat group. Since Foudre’s DGA code will try to connect to all C2 domains in a specific week (until a domain is verified using RSA signature verification), all (303) domains per week must be purchased. The purchased C2 domains can also provide a recording of Foudre-infected machines’ requests for the C2 server and generate a heat map based on the victim’s IP addresses.
The following is a list of future Foudre domains:
- 2021-10-06 6285f7c9.xyz
- 2021-10-13 1582c75f.xyz
- 2021-10-20 8c8b96e5.xyz
- 2021-10-27 fb8ca673.xyz
- 2021-11-03 642a59e7.xyz
- 2021-11-10 132d6971.xyz
- 2021-11-17 8a2438cb.xyz
- 2021-11-24 fd23085d.xyz
- 2021-12-01 6fdaab95.xyz
We also found the Foudre C2 domain log1host.info.gf, which is not generated by a DGA.
It was registered on May 21 and it seems like a backend server to backup Foudre’s exfiltrated files.
Tonnerre
We were able to discover that the current version of Tonnerre is version 15 (see image below).
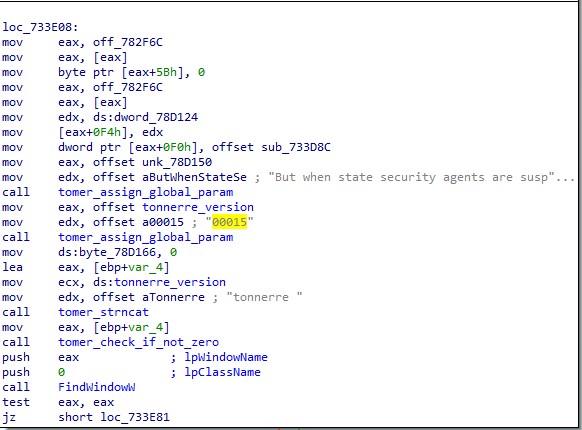
Version 11 was used until February 2021 (see After Lightning Comes Thunder, Feb 2021).
We also found that the Iranian threat group registered the domain 4fc92184.site on September 6, 2021, and it was resolved to the same active C2 server used for Foudre, but this Tonnerre C2 has not been activated yet. Actually the last time we saw evidence that it was active was at the beginning of March 2021, so we returned to reversing Foudre to search for new leads to prove that Tonnerre is still active.
We discovered that two samples of Foudre version 24 included a new tiny code add-on that was missed by other researchers. This code was added to the Foudre executable instead of the main DLL which includes the connections to the C2 server logic. The malware code, that was first found in June, probably attempts to download a new version of Tonnerre using a hardcoded and obfuscated URL: http://2fe55007.xyz/pinner/tdupdatex.dat instead of using a DGA.
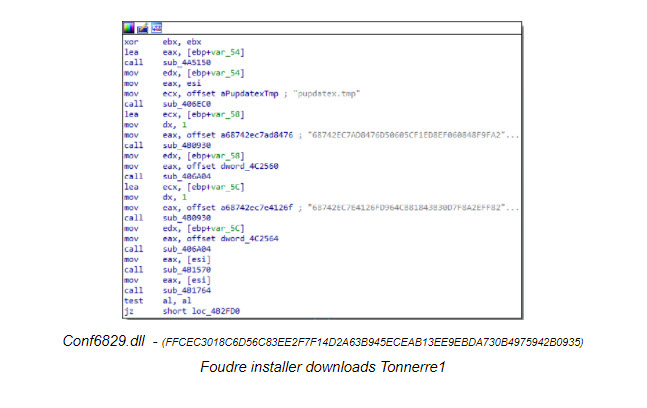
We believe it’s Tonnerre since “pinner” was used previously as a part of Tonnerre’s version 10 C2 server hostname: pinner.website. If the C2 is not available after that attempt, a second attempt tries to download it from: https://www.dropbox.com/s/ppf7ebfp8eicpzt/tdupdatex.dat?dl=1.
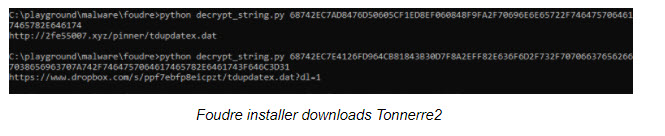
Interestingly the 2fe55007.xyz C2 server was registered on March 23, 2021, and is now used as an infection/update server. This is interesting because until now Tonnerre would be installed as a second stage malware only when an “interesting” victim is found by Foudre, but now it is installed on all Foudre victims (after the Foudre installer verifies that the victim’s computer doesn’t include security tools that pose a threat to Tonnerre).
Tonnerre version 15 analysis
The malware is similar to the previous version but includes 6 forms but without any new capabilities. (The older version included 5 forms)
The DGA formula used included a new prefix: NIN2 and a new TLD privatedns.org (.com and .website is also used as TLD). Two domains that were used as C2 servers both resolved to the same IP address as Foudre C2:
- 2021-08-17, domain: 834972e3.privatedns.org, DGA prefix: NIN220218331
- 2021-08-24, domain: cc08e424.privatedns.org, DGA prefix: NIN220218341
The Infy group added a regular domain name probably as part of a backend logic to back up the exfiltrated files. The domain name is: f1host.info.gf
This C2 server has been resolved since August 23 to the same IP address as Foudre’s C2 server 185.203.117.120.
Appendix A – IOC – C2
Foudre versions 24-25+ HTTP server
- 185.203.117.120 (has been active since 18/8/2021)
- 185.177.59.84 (was active between 25/8/2021-8/9/2021 mostly for older versions)
- 185.203.118.6 (was active between 3/3/2021-4/8/2021)
log1host.info.gf
Tonnerre
f1host.info.gf
[2]https://www.blackhat.com/docs/us-16/materials/us-16-Guarnieri-Iran-And-The-Soft-War-For-Internet-Dominance-wp.pdf
[3]https://www.safebreach.com/blog/2021/After-Lightning-Comes-Thunder
[5] https://twitter.com/ShadowChasing1/status/1405512103650152454