On July 19th, the U.S. Department of Justice unsealed an indictment against four APT40 threat actors for their illicit computer network exploitation (CNE) activities. Details of the various tactics, techniques, and procedures (TTPs) from the unsealed indictment are described in the US-CERT Alert AA21-200A and US-CERT Alert AA21-200B. APT40 is also known by the names – BRONZE MOHAWK, FEVERDREAM, G0065, Gadolinium, GreenCrash, Hellsing, Kryptonite Panda, Leviathan, MUDCARP, Periscope, Temp.Periscope, and Temp.Jumper. This threat group has primarily targeted governmental organizations, companies, and universities in a wide variety of verticals including biomedical, robotics, and medical research across the United States, Canada, Europe, and the Middle East.
The U.S. DoJ has identified the following trends in the Chinese state-sponsored malicious operations through proactive and retroactive analysis –
- Acquisition of Infrastructure and Capabilities – The attackers use a revolving series of virtual private servers (VSPs) and common open-source or commercial pentest tools to mask their activity.
- Exploitation of Public Vulnerabilities – The attackers typically scan target networks for critical and high vulnerabilities within days of the vulnerability’s public disclosure. This allows them to gain access before the targets have had time to patch their environment.
- Encrypted Multi-Hop Proxies – The attackers are often observed using virtual private servers (VSPs) or small office and home office (SOHO) routers as operational devices to evade detection.
The SafeBreach Hacker’s Playbook™ already incorporates attacks that leverage the identified TTPs included in US-CERT Alerts AA21-200A and AA21-200B:
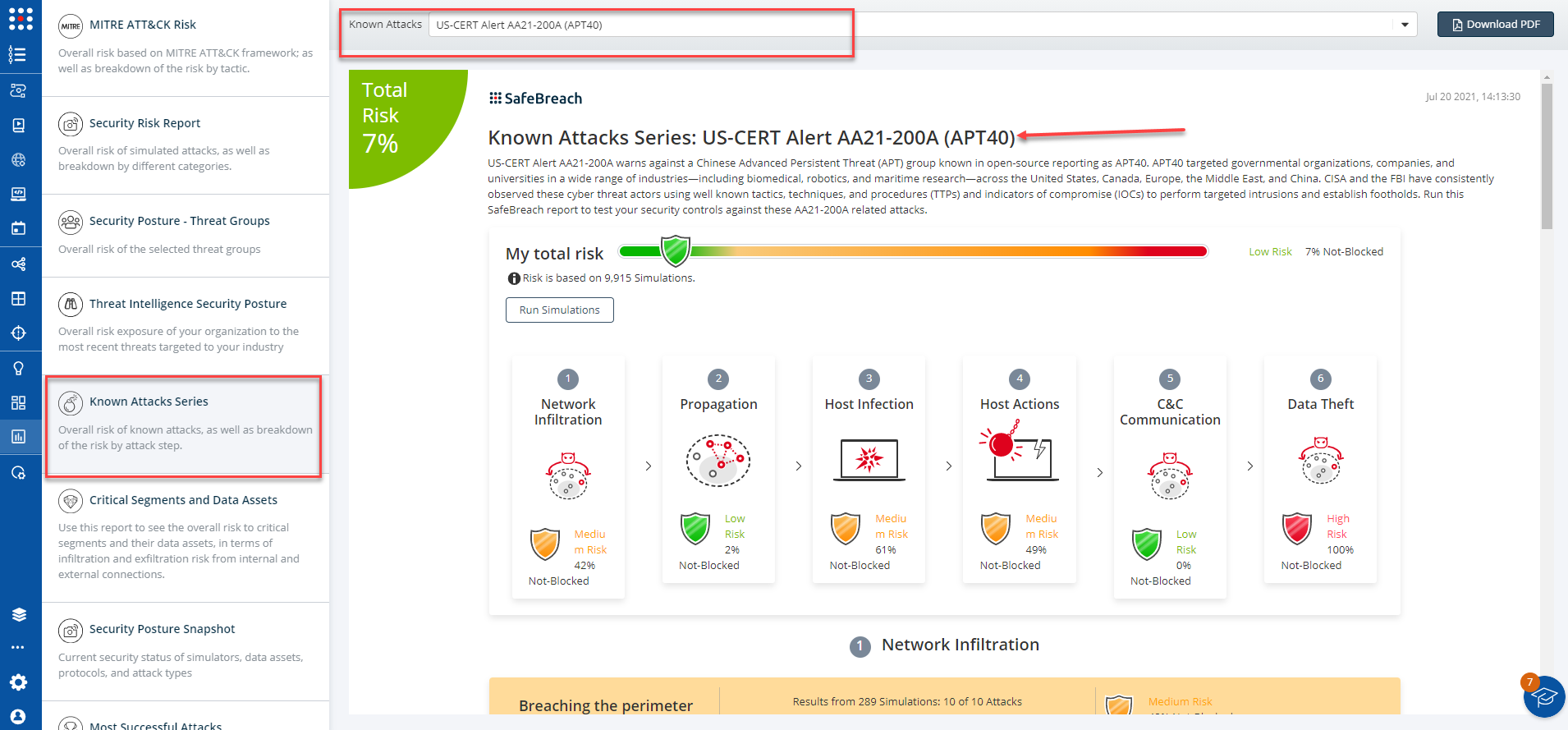
US-CERT Alert AA21-200A (APT40)
- #806 – Collect Files using ZIP
- #794 – Extract Login Information using MimiKatz
- #6473 – Agentless lateral movement via RDP
- #6127 – Extract LSASS memory dump using PowerShell and Rundll32
- #5833 – Extract Login Information using MimiKatz DCSync
- #5673 – Agentless lateral movement via Remote PowerShell (WMI)
- #5317 – Signed Binary Proxy Execution using Regsvr32.exe
- #5307 – Event Triggered Execution using PowerShell Profile
- #4136 – Execute EXE file using process hollowing (PowerShell)
- #4135 – Data Asset Exfiltration with the Email Attachment
- #3830 – Extract credentials using PwDump through PowerShell
- #3829 – Run obfuscated Mimikatz on host
- #3819 – Windows Credentials Collection using LaZagne
- #3391 – Email homefry malware as a ZIP attachment
- #3390 – Email homefry malware as a ZIP attachment
- #3389 – Transfer of homefry malware over HTTP/S
- #3388 – Transfer of homefry malware over HTTP/S
- #3387 – Write homefry malware to disk
- #3320 – Email china chopper malware as a ZIP attachment
- #3319 – Email china chopper malware as a ZIP attachment
- #3318 – Transfer of china chopper malware over HTTP/S
- #3317 – Transfer of china chopper malware over HTTP/S
- #3316 – Write china chopper malware to disk
- #3315 – Pre-execution phase of china chopper malware
- #3165 – Pre-execution phase of murkytop malware
- #2813 – Email nanhaishu malware as a ZIP attachment
- #2812 – Email nanhaishu malware as a ZIP attachment
- #2811 – Transfer of nanhaishu malware over HTTP/S
- #2810 – Transfer of nanhaishu malware over HTTP/S
- #2809 – Write nanhaishu malware to disk
- #2803 – Email murkytop malware as a ZIP attachment
- #2802 – Email murkytop malware as a ZIP attachment
- #2801 – Transfer of murkytop malware over HTTP/S
- #2800 – Transfer of murkytop malware over HTTP/S
- #2799 – Write murkytop malware to disk
- #264 – Remote Control using Meterpreter to Execute File Commands
- #2611 – Extract system date using PowerShell
- #2608 – PowerShell – Run Script File (csc build no powershell)
- #2527 – Email derusbi malware as a ZIP attachment
- #2526 – Email derusbi malware as a ZIP attachment
- #2525 – Transfer of derusbi malware over HTTP/S
- #2524 – Transfer of derusbi malware over HTTP/S
- #2523 – Write derusbi malware to disk
- #240 – SMB- Upload File
- #2273 – Pass the Hash over SMB using Mimikatz
- #2267 – Add an exclusion to Windows Defender using PowerShell
- #2248 – Masquerading
- #2244 – Windows Management Instrumentation Event Subscription
- #2222 – Discover Remote Systems using PowerShell
- #2221 – Modify the Registry Run keys
- #2213 – Write data into an Alternate Data Stream of a file
- #2206 – Extract Security Packages using PowerShell
- #2205 – Extract NTLM Hashes using Invoke-Kerberoast (PowerShell)
- #192 – Brute force attack over RDP protocol
- #176 – Remote control using the China Chopper Web Shell
- #1693 – Collect Windows system data using CMD
- #1562 – Remote command execution by WMIC (persistence)
- #1220 – Inject Mimikatz using PowerShell to Extract Credentials
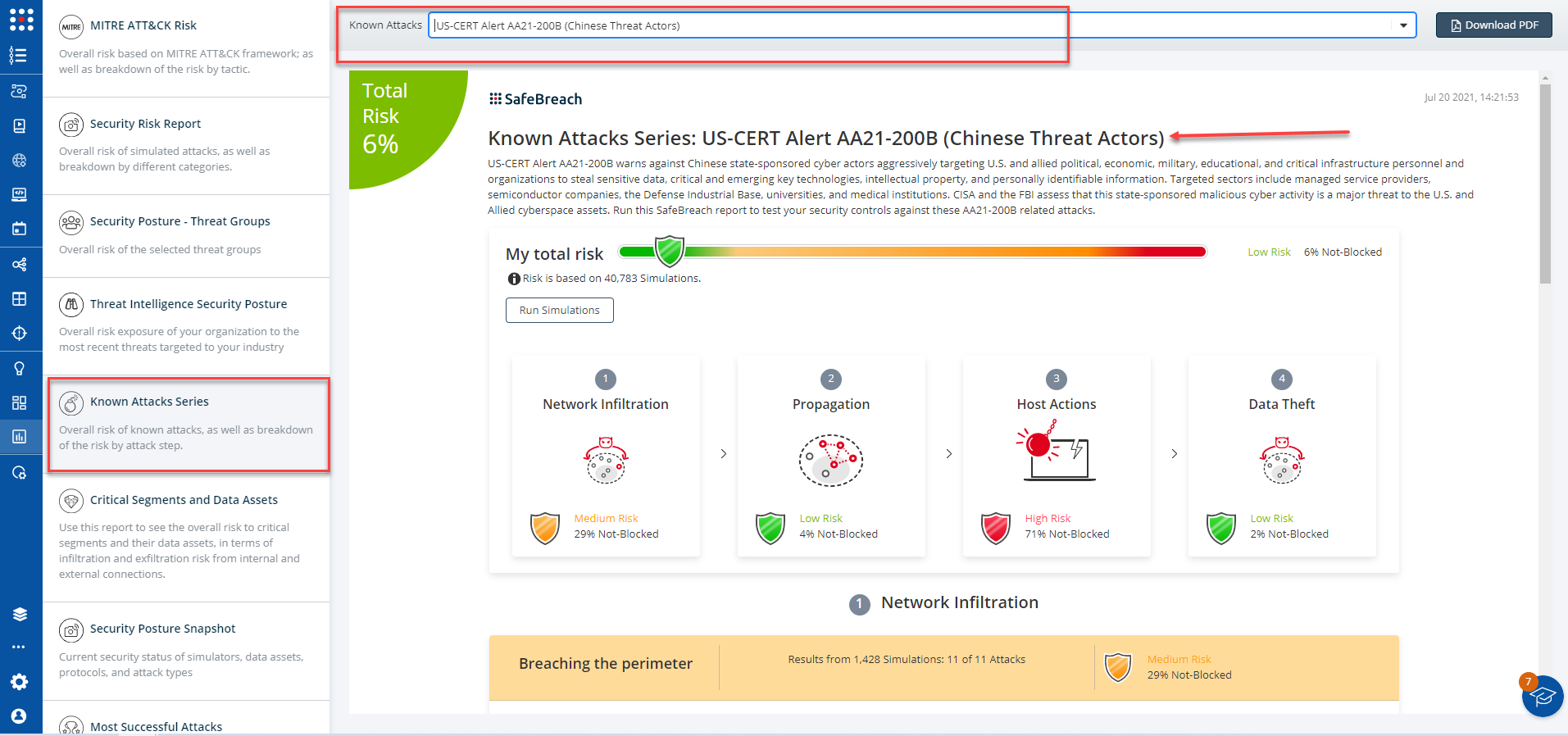
US-CERT Alert AA21-200B (Chinese Threat Actors)
- #806 – Collect Files using ZIP
- #6132 – Discover Linux file system information using bash commands
- #3830 – Extract credentials using PwDump through PowerShell
- #3829 – Run obfuscated Mimikatz on host
- #312 – Obfuscation of EXE inside Encrypted ZIP over HTTP protocol
- #2268 – List Microsoft Outlook PST files
- #2251 – Network Share Connection Removal
- #2249 – Indicator Removal on Host (Linux)
- #2245 – Indicator Removal on Host (Windows)
- #2244 – Windows Management Instrumentation Event Subscription
- #2243 – Indicator Removal from Tools
- #2222 – Discover Remote Systems using PowerShell
- #2213 – Write data into an Alternate Data Stream of a file
- #2188 – Extract Process List using Windows Commands
- #2175 – Discover Linux user configurations using Bash (Linux)
- #2174 – Extract users and groups using net.exe (Windows)
- #171 – Obfuscation of Malicious EXE inside an Encrypted ZIP file using HTTP
- #170 – Obfuscation of Malicious EXE inside a WSF (XML-based) using HTTP
- #1695 – Discover Linux processes using Bash scripts
- #164 – Obfuscation of a malicious executable inside an Unecrypted RAR file over HTTP
- #161 – Malicious EXE File Inside a Macro of a Word File
- #160 – Obfuscation of a malicious executable inside a JavaScript file over HTTP
- #158 – Obfuscation of a malicious executable inside an HTA file over HTTP
- #153 – Obfuscation of a malicious executable inside a CHM file
- #1511 – Remote exploitation of an SMB server exploiting CVE-2017-0144 (WannaCry)
- #1338 – Remote command execution by PSExec
- #1220 – Inject Mimikatz using PowerShell to Extract Credentials
- #106 – Covert data exfiltration using HTTP (GET)
- #101 – Covert data assets exfiltration over TCP
- #1370 – Remote exploitation of the Apache Struts 2 server using CVE-2017-5638
- #4271 – Remote exploitation of Pulse VPN vulnerability CVE-2019-11510
- #5570 – Directory Traversal of Citrix ADC vulnerability CVE-2019-19781
- #6130 – Remote exploitation of Pulse VPN vulnerability CVE-2020-8260
- #6128 – Remote exploitation of Pulse VPN vulnerability CVE-2021-22893
- #5984 – Exploitation of CVE-2021-26855 internal Exchange server
- #5983 – Exploitation of CVE-2021-26855 external Exchange server
- #6373 – Remote Exploitation of SonicWall SSLVPN using CVE-2021-20016
- #794 – Extract Login Information using MimiKatz
- #6473 – Agentless lateral movement via RDP
- #6127 – Extract LSASS memory dump using PowerShell and Rundll32
- #4135 – Data Asset Exfiltration with the Email Attachment
- #2355 – Modify the user’s PATH variable
- #2273 – Pass the Hash over SMB using Mimikatz
- #2248 – Masquerading
- #2246 – Hooking of GetSystemTime function using mavinject.exe with a custom DLL
- #2173 – Execute Code using Mshta
- #2164 – Scheduled Task
- #2153 – Rundll32
- #1693 – Collect Windows system data using CMD
- #1269 – Creating Windows schedule task (schtasks)
- #1224 – Create a Persistent Linux Service to Facilitate a Bind Shell
Additionally, our research team has added 2 new attack techniques to cover 10 of the additional C2 (Command and Control) servers included in the list provided by the U.S. DoJ. These include:
- #6511 – Communication with Leviathan_c2 using HTTP (Infiltration)
- #6512 – Communication with a real malicious Leviathan_c2 server using HTTP/S (Infiltration)
What you should do now
The new and existing attack methods for US-CERT AA21-200A (APT40) and US-CERT Alert AA21-200B (Chinese Threat Actors) are already in the SafeBreach Hacker’s playbook and ready to be run across your simulators. The Known Attack Series report is updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT Alert AA21-200A or US-CERT Alert AA21-200B report and select Run Simulations which will run all attack methods across all your deployed simulators. If you would like to run these attacks across specific simulators, you can do so by navigating to the Plans page and choosing the appropriate value from the “Threat Name” filter.