On October 18th, the Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and the Federal Bureau of Investigation (FBI) alerted about the increasing use of BlackMatter ransomware in attacks targeting multiple U.S. critical infrastructure entities, including two U.S. Food and Agriculture Sector organizations. Details of the various tactics, techniques, and procedures (TTPs) are described in US-CERT Alert (AA21-291A) – BlackMatter Ransomware.
According to CISA, BlackMatter is a new threat actor and has been active since July 2021. The BlackMatter ransomware has been observed using the Ransomware-as-a-Service (RaaS) model. It is also suspected that BlackMatter could be a possible rebrand of DarkSide Ransomware.
It is yet unclear what TTPs are being used by BlackMatter to infiltrate an organization. Once inside, the ransomware leverages embedded admin/user credentials that were previously compromised to discover all hosts in the organizational Active Directory (AD) using Server Message Broadcast (SMB) or Lightweight Directory Access Protocol (LDAP). These stolen credentials and the SMB protocol are then used to remotely encrypt files on the affected hosts. Additionally, the data is also exfiltrated and held for ransom. The ransom demanded ranges from $80k to $15 million and is expected to be paid in Bitcoin and Monero.
NOTE – The SafeBreach Hacker’s Playbook has been updated to include the newly discovered tactics and techniques from this US-CERT alert. We encourage you to test your preparedness against the BlackMatter Ransomware by running the attacks listed below. Additionally, we would also request you to run DarkSide related attacks to ensure more comprehensive coverage.
6 newly developed playbook methods related to BlackMatter Ransomware
- #6644 – Pre-execution phase of BlackMatter malware (Host-Level)
- #6645 – Write BlackMatter malware to disk (Host-Level)
- #6646 – Transfer of BlackMatter malware over HTTP/S (Lateral Movement)
- #6647 – Email BlackMatter malware as a ZIP attachment (Lateral Movement)
- #6648 – Transfer of BlackMatter malware over HTTP/S (Infiltration)
- #6649 – Email BlackMatter malware as a ZIP attachment (Infiltration)
It is worth noting that the SafeBreach Hacker’s Playbook™ already incorporates 6 attacks that leverage the identified TTPs in the US-CERT including:
- #6127 – Extract LSASS memory dump using PowerShell and Rundll32 – (Host Action)
- #6581 – Discover domain computers using LDAP method – (Host Action)
- #6550 – Agentless lateral movement via remote service execution w/o Mimikatz – (Host Action)
- #2188 – Extract Process List using Windows Commands – (Host Action)
- #1339 – Remote command execution by PSExec – (Infiltration)
- #1338 – Remote command execution by PSExec – (Infiltration)
What you should do now
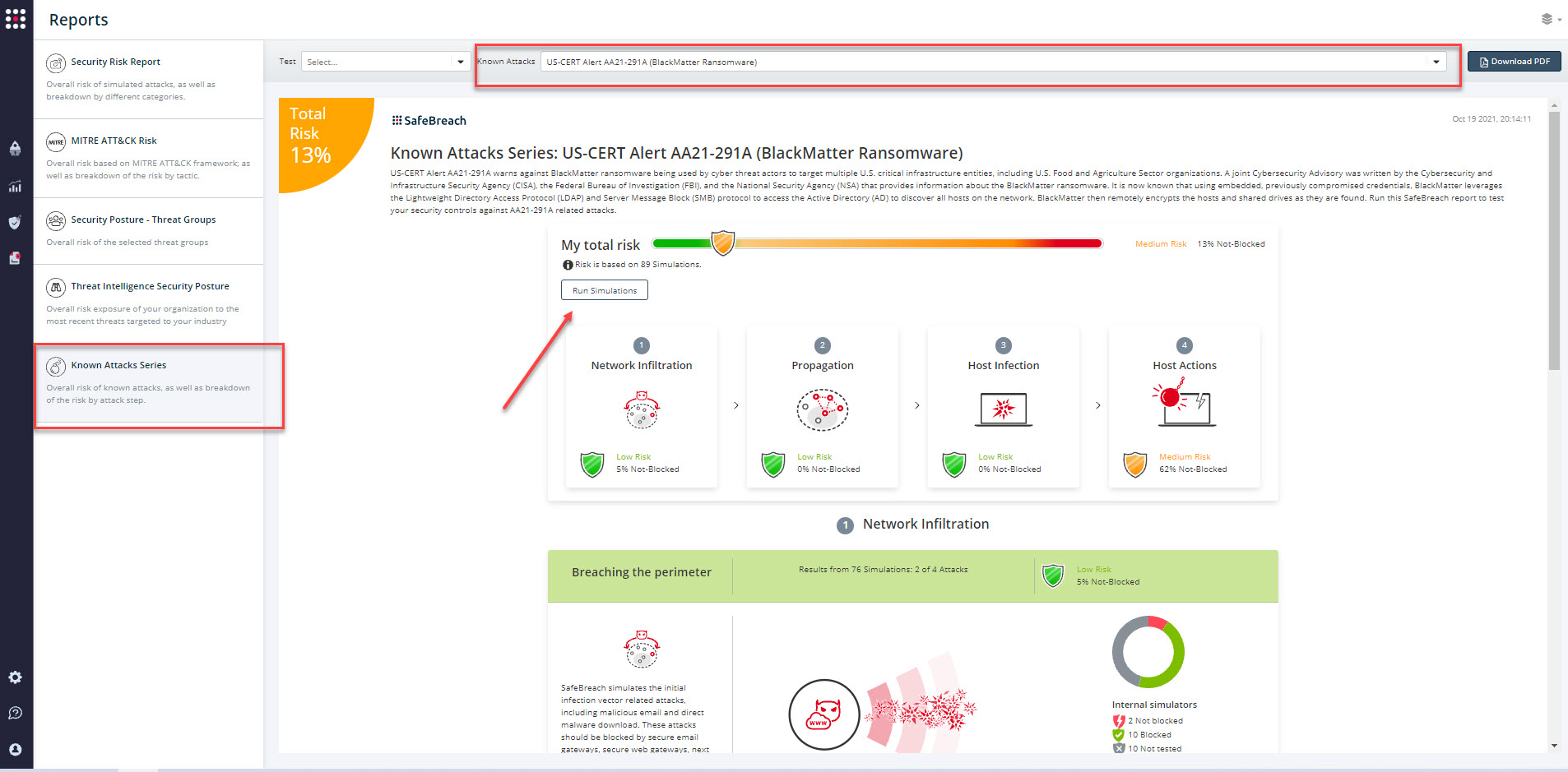
The newly updated and existing attack methods for US-CERT Alert AA21-291A (BlackMatter Ransomware) are already in the SafeBreach Hacker’s playbook and ready to be run across your simulators. The Known Attack Series report is updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT Alert AA21-291A (BlackMatter Ransomware) report and select Run Simulations which will run all attack methods.
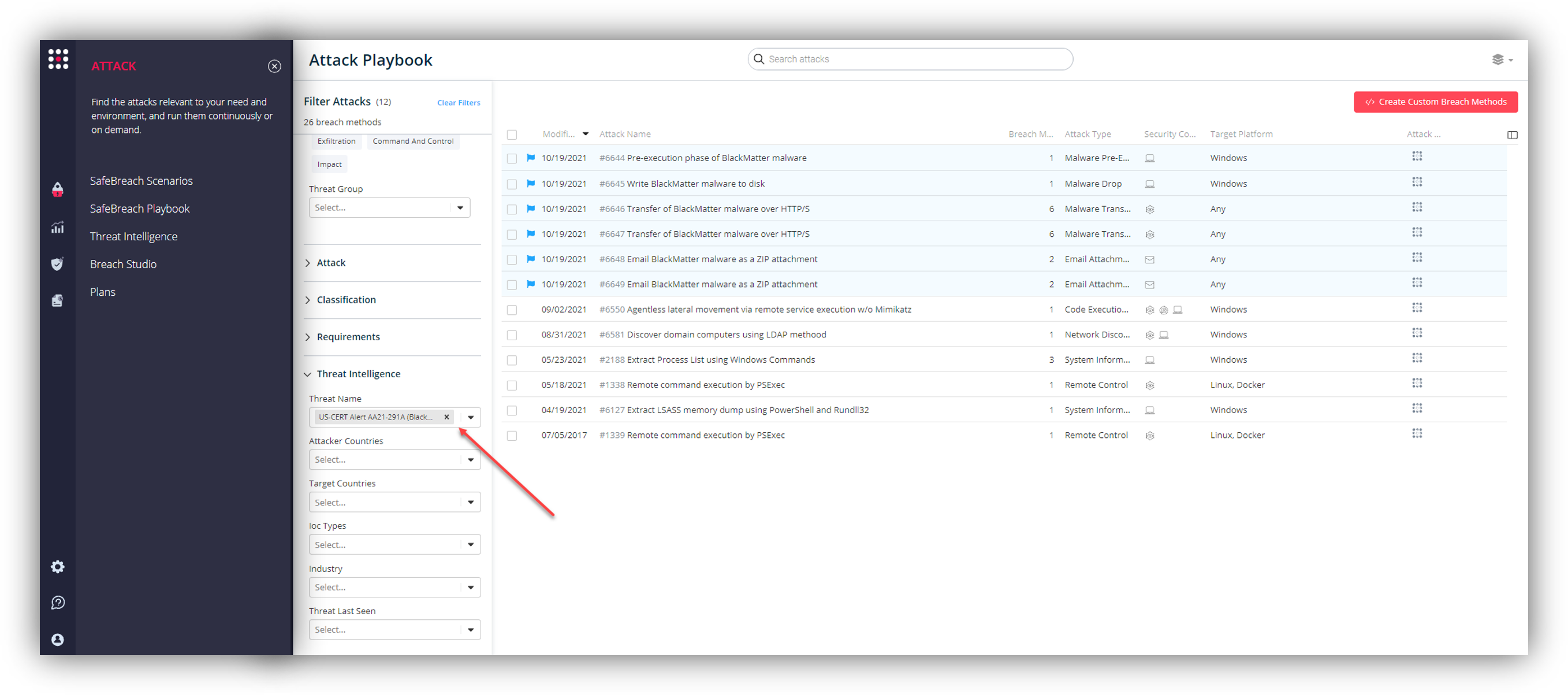
Additionally, you can also select all the attacks related to US-CERT Alert AA21-291A (BlackMatter Ransomware), by going to the SafeBreach Playbook and filtering by Threat Name – US-CERT Alert AA21-291A (BlackMatter Ransomware)
NOTE – CISA, NSA, and FBI also recommend the following mitigations to secure your organization against the BlackMatter Ransomware:
- Implement and enforce backup and restoration policies and procedures.
- Use strong, unique passwords.
- Use multi-factor authentication.
- Implement network segmentation and traversal monitoring.