SafeBreach Labs has updated the Hacker’s Playbook™ with new attack methods for malware samples, URLs, and domains described in US-CERT: Sophisticated Spearphishing Campaign Targets Government Organizations, IGOs, and NGOs which addresses a spearphishing campaign leveraged by the threat actor Nobelium (part of APT29) specifically targeting government organizations, intergovernmental organizations (IGOs), and non-governmental organizations (NGOs). The threat actor leveraged a compromised end-user account from Constant Contact, a legitimate email marketing software company, to spoof a U.S.-based government organization and distribute phishing emails to more than 7,000 accounts across approximately 350 government organizations, IGOs, and NGOs. The phishing email delivers an HTML attachment which, when clicked, automatically downloads and mounts an ISO (Optical Disc Image) file and executes the Cobalt Strike Beacon Loader* (a malicious shortcut file).
19 newly developed playbook methods related to AA21-148A
Infiltration
- #6412 – Communication with a real malicious NOBELIUM_SpearPhishing server using HTTP/S
- #6413 – Communication with NOBELIUM_SpearPhishing using HTTP
- #6416 – Transfer of NOBELIUMisoimage malware over HTTP/S
- #6418 – Email NOBELIUMisoimage malware as a ZIP attachment
- #6421 – Transfer of NOBELIUMCobaltStrikeloader malware over HTTP/S
- #6423 – Email NOBELIUMCobaltStrikeloader malware as a ZIP attachment
- #6426 – Transfer of NOBELIUM_lnk malware over HTTP/S
- #6428 – Email NOBELIUM_lnk malware as a ZIP attachment
- #6429 – Phishing email with ISO attachment
- #6430 – Communication with a real malicious NOBELIUM C2 server using HTTP/S
Host-Level
- #6414 – Write NOBELIUMisoimage malware to disk
- #6419 – Write NOBELIUMCobaltStrikeloader malware to disk
- #6424 – Write NOBELIUM_lnk malware to disk
Lateral Movement
- #6415 – Transfer of NOBELIUMisoimage malware over HTTP/S
- #6417 – Email NOBELIUMisoimage malware as a ZIP attachment
- #6420 – Transfer of NOBELIUMCobaltStrikeloader malware over HTTP/S
- #6422 – Email NOBELIUMCobaltStrikeloader malware as a ZIP attachment
- #6425 – Transfer of NOBELIUM_lnk malware over HTTP/S
- #6427 – Email NOBELIUM_lnk malware as a ZIP attachment
2 existing playbook methods related to AA21-148A
- #109 – Covert data asset exfiltration using HTTP/s GET
- #2153 – Rundll
What you should do now
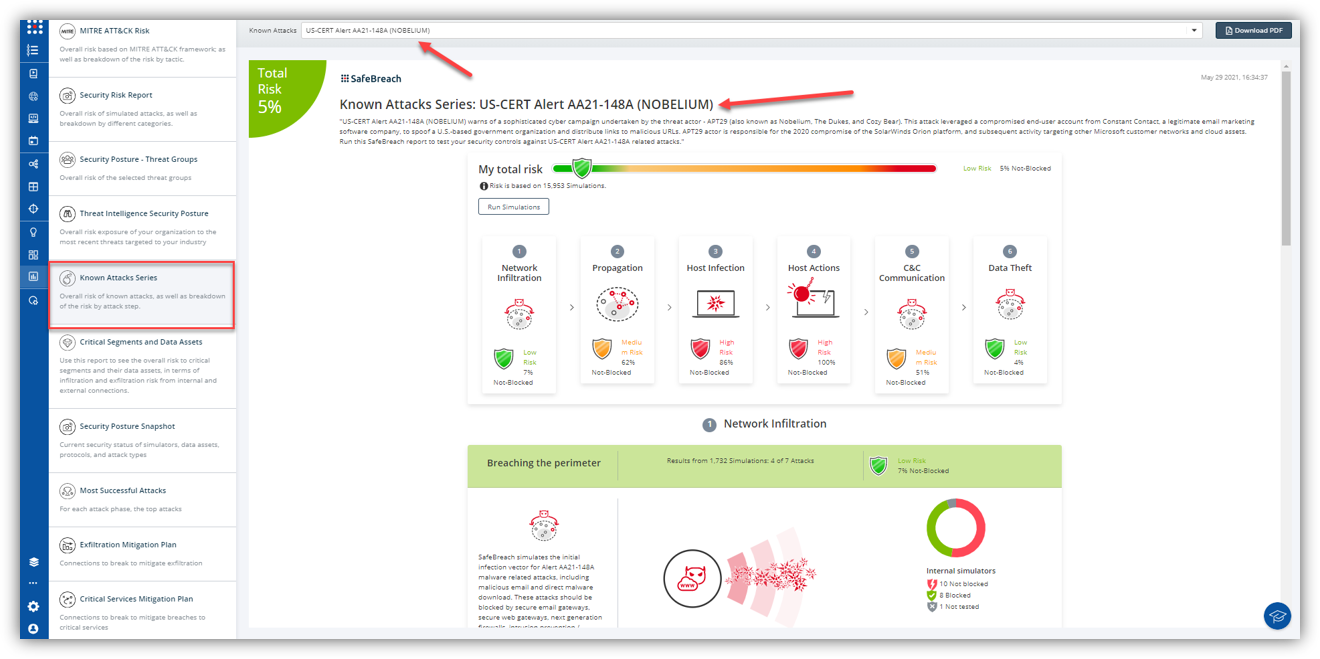
The new attack methods for US-CERT AA21-148A are already in the SafeBreach Hacker’s playbook and ready to be run across your simulators. The Known Attack Series report is updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT AA21-148A (Nobelium) report and select Run Simulations which will run all attack methods.
NOTE – Cobalt Strike is a commercial penetration testing tool used to conduct red team operations. It contains several tools that complement the cyber threat actor’s exploitation efforts, such as a keystroke logger, file injection capability, and network services scanners. The Cobalt Strike Beacon is the malicious implant that calls back to attacker-controlled infrastructure and checks for additional commands to execute on the compromised system