Update –
Our initial coverage of Follina included delivery and transfer of the vulnerability. The SafeBreach research team has now included two new attacks that allow users to simulate the end-to-end execution of the Follina 0-day vulnerability. Both of these are advanced attacks that trigger the execution of CVE-2022-30190 (one using Office and the other using PowerShell). See below for the original coverage and the newly added attacks.
Original Coverage
On May 27th, security researchers discovered a malicious word document abusing a previously unidentified 0-day vulnerability (CVE-2022-30190) in Microsoft products. Exploiting this 0-day vulnerability, known as Follina allows remote and unauthenticated threat actors to achieve Remote Code Execution (RCE), with minimal user interaction.
According to the information available, attackers can exploit Follina even if Office macros are disabled. Office 2013/2016/2019/2021, and some versions of Office included with a Microsoft 365 license are vulnerable on both Windows 10 and Windows 11.
Additional details about Follina 0-day vulnerability
It was first identified in a suspicious-looking word document (uploaded from an IP address in Belarus). The document uses the Word remote template feature to retrieve an HTML file from a remote web server, and load malicious code and execute PowerShell.
The researchers observed that Microsoft Word was executing the code via Microsoft Support Diagnostic Tool (MSDT) even if macros were disabled. If you change the document to RTF form, the code runs without even opening the document. The attacker can then install programs, view/ change/ delete data, or create new accounts in the context allowed by the user’s rights.
Newly Added SafeBreach Coverage
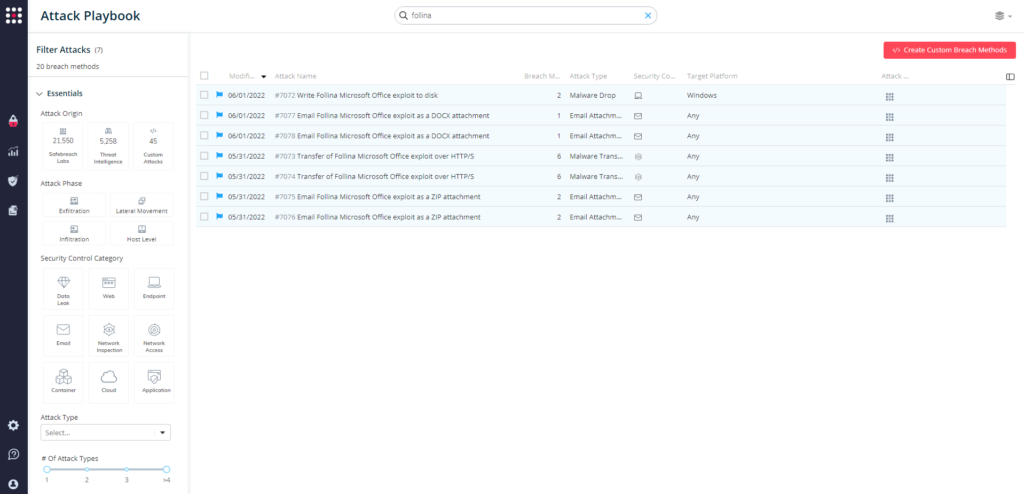
9 newly added Attacks for Follina 0-Day vulnerability:
- #7072 – Write Follina Microsoft Office exploit to disk (Host-Level)
- #7073 – Transfer of Follina Microsoft Office exploit over HTTP/S (Lateral Movement)
- #7074 – Transfer of Follina Microsoft Office exploit over HTTP/S (Infiltration)
- #7075 – Email Follina Microsoft Office exploit as a ZIP attachment (Lateral Movement)
- #7076 – Email Follina Microsoft Office exploit as a ZIP attachment (Infiltration)
- #7077 – Email Follina Microsoft Office exploit as a DOCX attachment (Lateral movement)
- #7078 – Email Follina Microsoft Office exploit as a DOCX attachment (Infiltration)
- #7070 – Remote exploitation of Follina CVE-2022-30190 using Powershell (NEW)
- #7069 – Remote exploitation of Follina CVE-2022-30190 using Office (NEW)
As additional information becomes available, the SafeBreach Labs team will add coverage for end-to-end exploitation of CVE-2022-30190 allowing customers to run advanced attacks that trigger and execute the vulnerability This will allow our customers to more thoroughly protect themselves from an attacker intending to exploit Follina in the organizational environment.
What you should do now
Attack methods related to Follina have been added to the Hacker’s Playbook™ and are ready to run across your simulators. From the Attack Playbook, select and filter attacks related to Follina (see below).
Additional Relevant Resources