On March 14th Microsoft released a patch for CVE-2023-23397 – a critical privilege elevation/authentication bypass vulnerability in Microsoft Outlook for Windows that was discovered by Microsoft Threat Intelligence analysts. According to the analysts, this vulnerability affects all versions of Outlook and is a zero-touch exploit, meaning the security gap requires low complexity to abuse and requires no user interaction. Microsoft Threat Intelligence assesses that a Russia-based threat actor used the exploit patched in CVE-2023-23397 in targeted attacks against a limited number of organizations in government, transportation, energy, and military sectors in Europe.
How is CVE-2023-23397 Exploited?
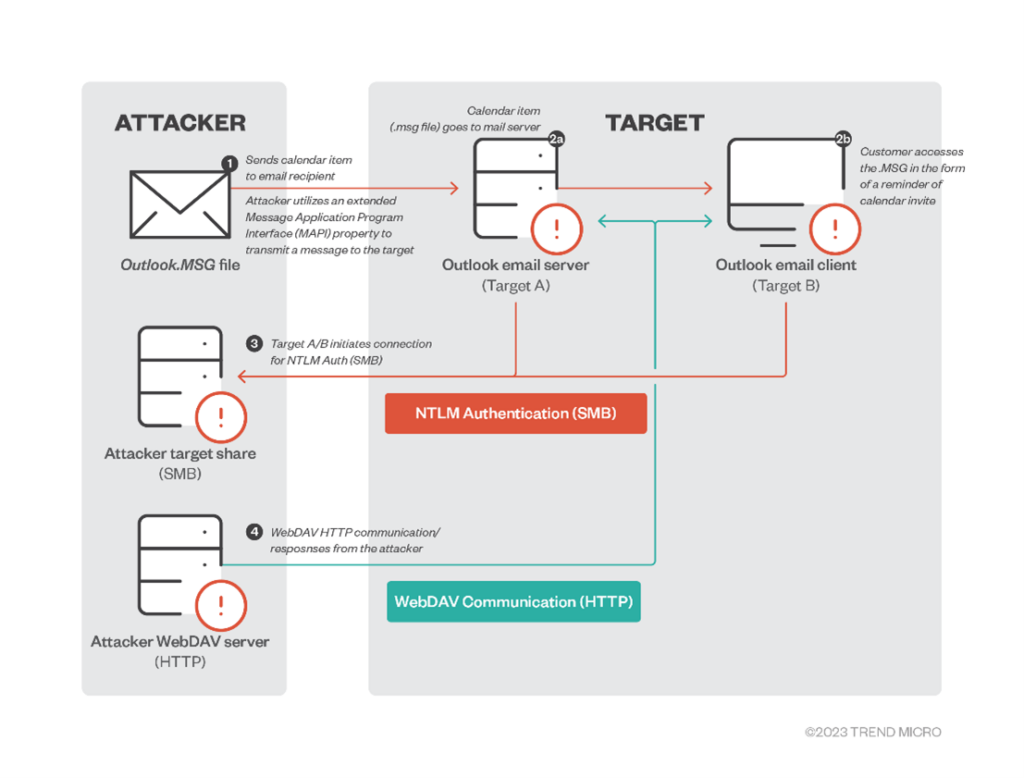
According to researchers from TrendMicro, threat actors are exploiting this vulnerability by sending malicious email—which, again, does not need to be opened. This vulnerability is triggered when an attacker sends a message with an extended MAPI property with a UNC path to an SMB (TCP 445) share on a threat actor-controlled server on an untrusted network.
The attacker remotely sends a malicious calendar invite represented by .msg — the message format that supports reminders in Outlook — to trigger the vulnerable API endpoint PlayReminderSound using “PidLidReminderFileParameter” (the custom alert sound option for reminders).
Important Note for SafeBreach Customers – Coverage for CVE-2023-23397
SafeBreach customers are encouraged to run the following attacks (in addition to leveraging mitigation instructions provided by Microsoft below) to ensure that their email gateways are secure against the vulnerability. SafeBreach researchers will continue to work on adding full-chain exploit coverage.
- #8728 – Email exploit CVE-2023-23397 via email attachment
- #8729 – Email exploit CVE-2023-23397 via email attachment
Both attacks listed above will take the following actions –
- Action: An attacker simulator sends an email containing the CVE-2023-23397 exploit. The email attachment is an Outlook message item file that contains an invite to a meeting with a sound notification that points to a UNC path.
- Expected behavior: The malicious attachment in the email does not reach the target mailbox.
SafeBreach also recommends the following remediation actions to ensure protection against the vulnerability:
- Restrict password-protected files – Implement a policy to quarantine password-protected files and apply an allowed list of senders to be excluded.
- Rigorously scan files and emails on the email gateway/ server – Execute files in a sandbox solution, before allowing the files to reach the user’s mailbox. For example: using Microsoft ATP’s Safe-Attachment and Safe Links features, using Gmail’s Security Sandbox and Advanced phishing and malware protection features or any other solution. If applicable, inspect the incoming email using multiple anti-malware engines that are preferably different from the anti-malware engines deployed on the servers and workstations.
- Enforce strict policies on internal email flow – Internal email flow between recipients in the same organization should follow the same inspection process as outside-sourced emails. This will prevent an attacker with access to an internal mailbox from sending malicious payloads internally while bypassing the perimeter security controls.
Microsoft Recommended Impact Assessment
To help you determine if your organization was targeted by actors attempting to use this vulnerability, Microsoft is providing documentation and a script at https://aka.ms/CVE-2023-23397ScriptDoc. The script will help you check the PidLidReminderFileParameter property of messages in your organization’s user mailboxes.
Organizations should review the output of this script to determine risk. Tasks, email messages, and calendar items that are detected and the PidLidReminderFileParameter property points to an unrecognized share or path should be reviewed to determine if those paths are malicious. If objects are detected, they can be removed, or the property can be cleared. If no objects are detected or you only see properties pointing to a blank value or a file name, malicious messages were not present in the data the script analyzed.
Interested in Protecting Against Advanced Ransomware?
SafeBreach now offers a complimentary and customized real-world ransomware assessment (RansomwareRx) that can allow you to gain unparalleled visibility into how your security ecosystem responds at each stage of the defense process. This ransomware assessment includes:
- Training – Understand the methodology around ransomware attacks, persistent threats, and malware attacks.
- Assessment – Review goals and ensure simulation connection to our management console and all configurations are complete.
- Attack Scenario – Run safe-by-design, real-world ransomware attacks across the cyber kill chain on a single device of your choice.
- Report – Receive a custom-built report that includes simulation results and actionable remediation insights.
Empower your team to understand more about ransomware attacks, methodologies, and behaviors—all through the lens of the attacker. Request your complimentary RansomwareRx assessment today.

