Back in the summer of 2021, we introduced SafeBreach Scenarios—an incredibly easy and versatile way to find and execute attacks based on SafeBreach recommendations as well as the latest threats in the wild, the top threat groups, and the top MITRE ATT&CK techniques. SafeBreach Scenarios was created to enable security teams to easily find and execute attacks that help them gain a complete quantitative view of the organizational security posture.
Additionally, SafeBreach Scenarios offered security teams a simple way to benchmark an organization’s current security preparedness against the evolving threat landscape. When we first launched Scenarios, they were available in the following categories:
- Recommended Scenarios – These are SafeBreach’s picks for the top scenarios to run from each listed category.
- Security Controls – These scenarios allow teams to validate the coverage and efficiency of the security control categories in your environment by running attacks that are expected to be prevented by each control category.
- Known Attack Series – These scenarios allow teams to test their defenses against attack campaigns and elements that have been released as warnings to the public by organizations such as CISA.
- Threat Groups – These scenarios allow teams to test their security controls against attacks attributed to known threat groups, which are defined by sets of related intrusion activities and methodologies.
- Baseline Scenarios – These scenarios provide a benchmark of expected security posture for various activity types within your environment.
- MITRE ATT&CK – These scenarios allow teams to test themselves against real-world attacks listed in the MITRE ATT&CK framework.
What’s New
The SafeBreach Hacker’s Playbook™ is the most up-to-date collection of known attacks comprising over 25,000 breach methods incorporating real-time threat intelligence from our own research as well as multiple threat-intelligence providers. The SafeBreach team is committed to continuously improving and enhancing the user experience by introducing features and capabilities that not only make the tool more powerful, but also easier to use.
With that goal in mind, we are excited to announce the SafeBreach platform now offers the ability to validate your deployed security controls against the Top 16 TTPs as seen in the MITRE ATT&CK framework. These TTPs made up 90% of the observed techniques from April 2019 to July 2021. We have mapped these TTPs across our entire attack playbook and our customers can now choose to run the Top 16 TTPs or full MITRE coverage scenarios (for their vertical/industry) to test their preparedness against these advanced threats.
By mapping the Top-16 MITRE TTPs, we have made the MITRE ATT&CK framework more actionable. Our platform is the only continuous validation platform that calculates real attack paths from the hacker’s perspective based on real malware behavior and real actions, all run in a controlled manner, safely, and at scale. This allows us to drive prioritization and timely validation of real attacks based on specific threat profiles targeting an organization or industry.
What Are The Top-16 TTPs?
In order to provide our customers with a comprehensive list of the most prevalent attacks by industry/vertical, the SafeBreach team referenced the US-CERT Alerts (between April 2019 and July 2021), the 2022 Threat Detection Report by Red Canary, and the MITRE Engenuity report titled Sightings Ecosystem: A Data-driven Analysis of ATT&CK in the Wild. This list was then mapped to the appropriate verticals allowing us to create industry/vertical-specific scenarios that allow customers to validate their security controls against the most relevant threats. Below is the list of Top-16 TTPs (descriptions available on attack.mitre.org) operationalized by our team:
- T1059 – Command and Scripting Interpreter – Adversaries may abuse command and script interpreters to execute commands, scripts, or binaries. Commands and scripts can be embedded in Initial Access payloads delivered to victims as lure documents or as secondary payloads downloaded from an existing C2. Adversaries may also execute commands through interactive terminals/shells, as well as utilize various Remote Services in order to achieve remote Execution.
- T1218 – System Binary Process Execution – Adversaries may bypass the process and/or signature-based defenses by proxying execution of malicious content with signed, or otherwise trusted, binaries. Binaries used in this technique are often Microsoft-signed files, indicating that they have been either downloaded from Microsoft or are already native in the operating system.
- T1543 – Create or Modify System Process – Adversaries may create or modify system-level processes to repeatedly execute malicious payloads as part of persistence. When operating systems boot up, they can start processes that perform background system functions. Services, daemons, or agents may be created with administrator privileges but executed under root/SYSTEM privileges. Adversaries may leverage this functionality to create or modify system processes in order to escalate privileges.
- T1053 – Scheduled Task/Job – Adversaries may abuse task scheduling functionality to facilitate initial or recurring execution of malicious code. Adversaries may use task scheduling to execute programs at system startup or on a scheduled basis for persistence. These mechanisms can also be abused to run a process under the context of a specified account (such as one with elevated permissions/privileges).
- T1003 – OS Credential Dumping – Adversaries may attempt to dump credentials to obtain account login and credential material, normally in the form of a hash or a clear text password, from the operating system and software. Credentials can then be used to perform Lateral Movement and access restricted information.
- T1055 – Process Injection – Adversaries may inject code into processes in order to evade process-based defenses as well as possibly elevate privileges. Process injection is a method of executing arbitrary code in the address space of a separate live process. Running code in the context of another process may allow access to the process’s memory, system/network resources, and possibly elevated privileges. Execution via process injection may also evade detection from security products since the execution is masked under a legitimate process.
- T1027 – Obfuscated Files or Information – Adversaries may attempt to make an executable or file difficult to discover or analyze by encrypting, encoding, or otherwise obfuscating its contents on the system or in transit. This is common behavior that can be used across different platforms and the network to evade defenses.
- T1105 – Ingress Tool Transfer – Adversaries may transfer tools or other files from an external system into a compromised environment. Tools or files may be copied from an external adversary-controlled system to the victim network through the command-and-control channel or through alternate protocols such as ftp. Once present, adversaries may also transfer/spread tools between victim devices within a compromised environment (i.e., Lateral Tool Transfer).
- T1569 – System Services – Adversaries may abuse system services or daemons to execute commands or programs. Adversaries can execute malicious content by interacting with or creating services either locally or remotely.
- T1036 – Masquerading – Adversaries may attempt to manipulate features of their artifacts to make them appear legitimate or benign to users and/or security tools. Masquerading occurs when the name or location of an object, legitimate or malicious, is manipulated or abused for the sake of evading defenses and observation. This may include manipulating file metadata, tricking users into misidentifying the file type, and giving legitimate task or service names.
- T1574 – Hijack Execution Flow – Adversaries may execute their own malicious payloads by hijacking the way operating systems run programs. Hijacking execution flow can be for the purposes of persistence, since this hijacked execution may reoccur over time. Adversaries may also use these mechanisms to elevate privileges or evade defenses, such as application control or other restrictions on execution.
- T1090 – Proxy – Adversaries may use a connection proxy to direct network traffic between systems or act as an intermediary for network communications to a command-and-control server to avoid direct connections to their infrastructure.
- T1562 – Impair Defenses – Adversaries may maliciously modify components of a victim environment in order to hinder or disable defensive mechanisms. This not only involves impairing preventative defenses, such as firewalls and anti-virus, but also detection capabilities that defenders can use to audit activity and identify malicious behavior.
- T1021 – Remote Services – Adversaries may use Valid Accounts to log into a service specifically designed to accept remote connections, such as telnet, SSH, and VNC. The adversary may then perform actions as the logged-on user.
- T1095 – Non-Application Layer Protocol – Adversaries may use a non-application layer protocol for communication between host and C2 server or among infected hosts within a network.
- T1047 – Windows Management Instrumentation – Adversaries may abuse Windows Management Instrumentation (WMI) to execute malicious commands and payloads. An adversary can use WMI to interact with local and remote systems and use it as a means to execute various behaviors, such as gathering information for Discovery as well as remote Execution of files as part of Lateral Movement.
Operationalizing The Top-16 MITRE TTP Scenarios
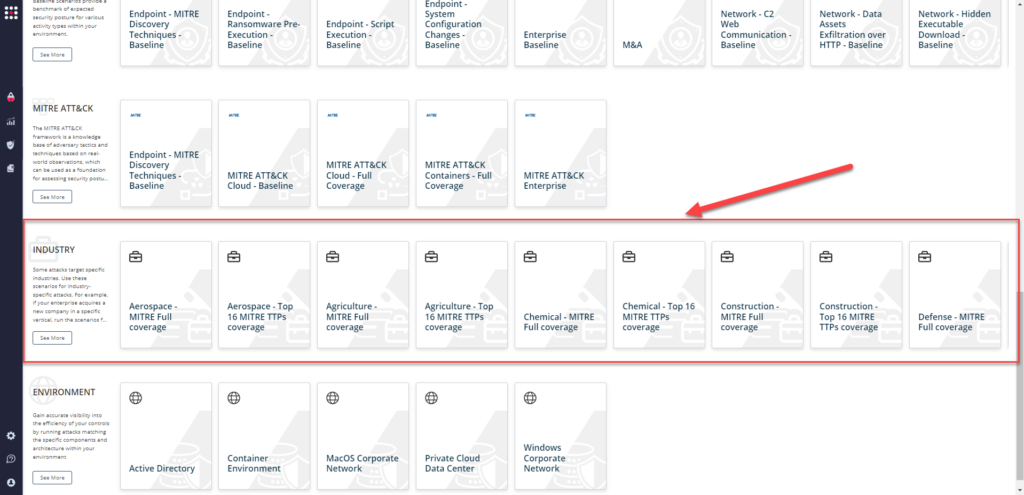
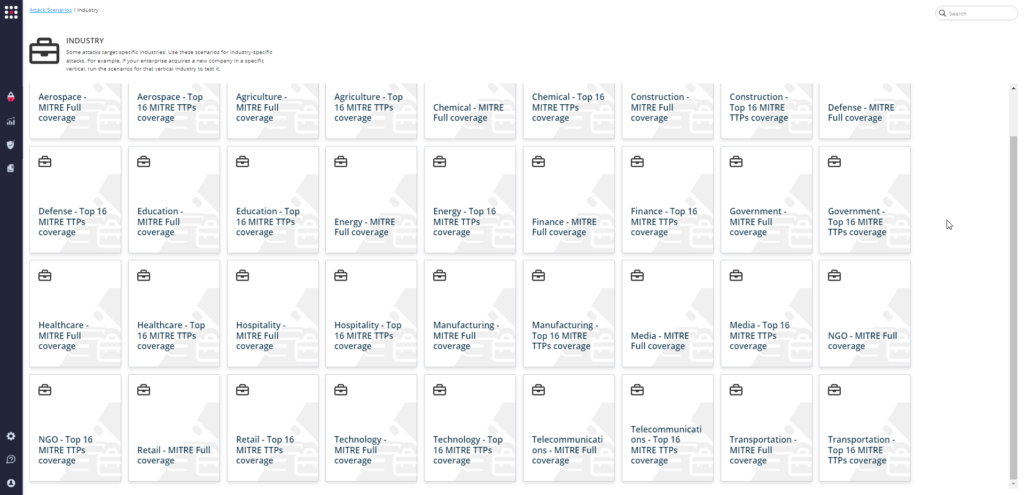
SafeBreach customers can easily choose and run the Top-16 attacks relevant to their industry/vertical by going to the “Scenarios” page and scrolling down to the “Industry” section and selecting a scenario they want to run: “Full Coverage” or “Top-16.”
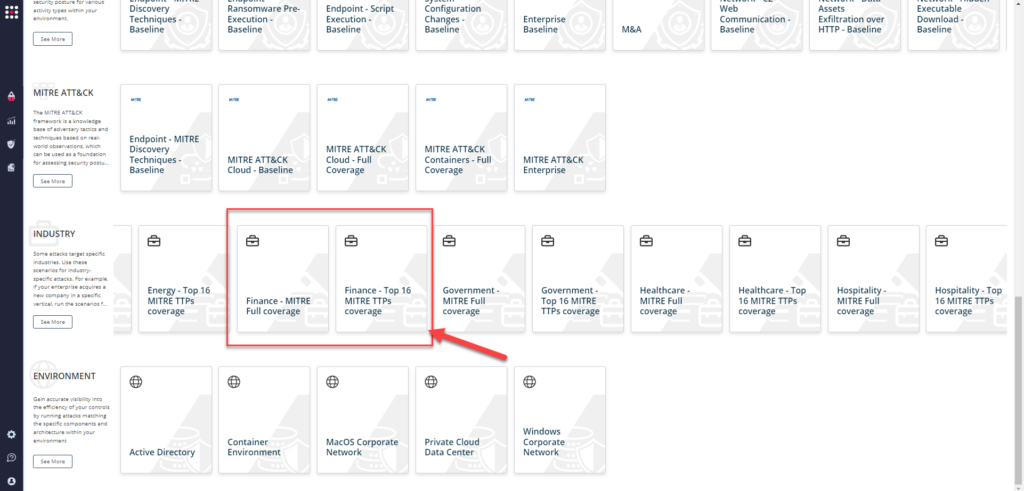
Once they select the scenario, they can easily view, customize, and run it using the newly introduced SafeBreach Studio capability.
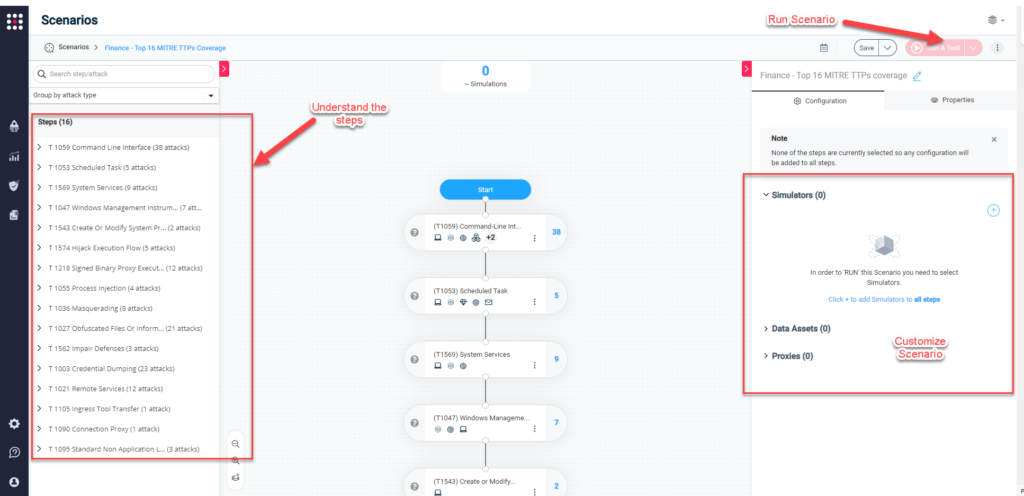
Upon successful completion, they can easily understand the performance of their deployed security controls against these attacks by going to the “Dashboards” tab and choosing the “MITRE ATT&CK – Top 16 TTPs” dashboard. This report allows you to visualize your control performance against the various MITRE TTPs and understand your gaps. You can also share this report with key stakeholders to help make better business and remediation decisions.
According to Derek Krien, SafeBreach’s Security Services Director, “By adding MITRE-level mitigation and detection guidance to the dashboard, customers can gain a complete MITRE workflow for operationalizing the MITRE ATT&CK framework. Each individual dashboard includes the MITRE technique and sub-techniques with MITRE-level mitigation guidance to allow customers to quickly understand their gaps and take appropriate remediation steps.”
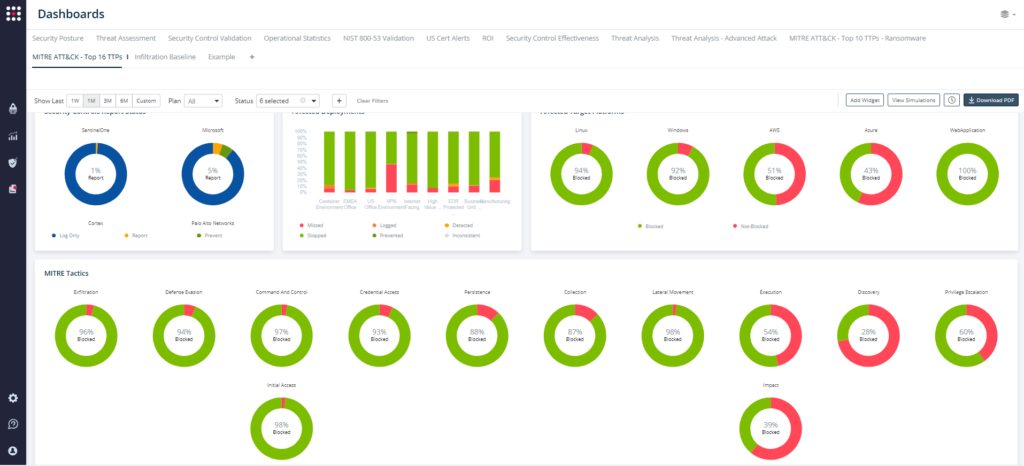
SafeBreach’s continuous security validation platform provides mitigation and detection guidance from MITRE ATT&CK and real, actionable threat intelligence enabling remediation based on quantitative evidence of the efficacy of your security controls across technology, processes, and people. Whether existing attacks or emerging threats, we allow customers to operationalize and validate threats that are important to their business. We mapped the Top-16 MITRE ATT&CK TTPs to build an attack plan visualized through comprehensive dashboards with explanation, attack details, MITRE-level mitigation, and detection guidance. To learn more about this capability, please contact us.