On June 1st, the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), the U.S. Treasury Department (Treasury), and the Financial Crimes Enforcement Network (FinCEN) issued a joint advisory highlighting malicious activities of the Karakurt data extortion group (also known as Karakurt Team or Karakurt Lair). Additional details about this group and its associated tactics, techniques, and procedures (TTPs) are available in US-CERT Alert (AA22-152A) Karakurt Data Extortion Group.
Karakurt’s Data Extortion Business
Karakurt is the data extortion arm of the Conti ransomware gang and is primarily focused on stealing data from companies and forcing them to pay ransom in exchange for not releasing the stolen data. As Karakurt is primarily focused on stealing data and extorting victims, they usually do not encrypt compromised machines or files like other ransomware-focused threat actors. Their known ransom demands have ranged from $25k to $13m in Bitcoin, with payment deadlines set to expire within a week of first contact with the victim.
To convince the victims that their data is indeed stolen, the Karakurt actors have typically provided screenshots or copies of stolen file directories. To create a sense of urgency and panic, they typically contact the victims’ employees, business partners, known associates, and customers by sending them harassing emails and phone calls. These emails typically contain examples of stolen data (social security numbers, payment accounts, private company emails, and sensitive business data) belonging to the victims’ employees or customers. While the Karakurt actors have typically provided some proof of deletion of the stolen files on payment of the ransom, some past victims have reported that the threat actors did not maintain the victim’s confidentiality after the ransom was paid. The U.S. government is strongly discouraging the payment of any ransom to Karakurt threat actors promising to delete stolen files in exchange for payments.
Additionally, to potentially demand larger amounts of ransom, the Karakurt threat actors have been observed to greatly exaggerate the amount and value of data stolen from a victims’ network. In some reported cases, they even claimed to have stolen more data than what their victims’ servers could even store.
Technical details about Karakurt’s Operation
Prior to January 5, 2022, Karakurt operated a leak and auction website found at https://karakurt[.]group. The domain and IP address originally hosting the website went offline in the spring of 2022. The website is no longer accessible on the open internet but has been reported to be located elsewhere in the deep web and on the dark web. As of May 2022, the website contained several terabytes of data purported to belong to victims across North America and Europe, along with several “press releases” naming victims who had not paid or cooperated, and instructions for participating in victim data “auctions.”
- Initial Intrusion – Karakurt actors appear to obtain access to victim devices primarily by either purchasing stolen credentials from the dark web, through their partners, or buying them off third-party intrusion broker networks.
- Common CVEs Exploited – The Karakurt threat actors have exploited commonly known vulnerabilities to gain initial access. These include:
- Outdated SonicWall SSL VPN devices which are vulnerable to multiple CVEs
- Log4Shell
- Phishing and social engineering
- Email attachments with malicious macros
- Outdated Fortinet FortiGate SSL VPN appliances
- Network Recon, Lateral Movement, and Exfiltration – Upon developing or obtaining access to a compromised system, Karakurt actors deploy Cobalt Strike beacons to enumerate a network, install Mimikatz to pull plain-text credentials, use AnyDesk to obtain persistent remote control, and utilize additional situation-dependent tools to elevate privileges and move laterally within a network.
- Extortion – Following the exfiltration of data, Karakurt actors present the victim with ransom notes by way of “readme.txt” files, via emails sent to victim employees over the compromised email networks, and emails sent to victim employees from external email accounts. The ransom notes reveal the victim has been hacked by the “Karakurt Team” and threaten public release or auction of the stolen data. The instructions include a link to a TOR URL with an access code. Visiting the URL and inputting the access code open a chat application over which victims can negotiate with Karakurt actors to have their data deleted. Karakurt actors then compress (typically with 7zip) and exfiltrate large sums of data—and, in many cases, entire network-connected shared drives in volumes exceeding 1 terabyte (TB)—using open-source applications and File Transfer Protocol (FTP) services, such as Filezilla, and cloud storage services including rclone and Mega.nz.
IMPORTANT NOTE for SafeBreach Customers – Coverage for AA22-152A
As soon as details and IOCs for Karakurt threat actors were first available, corresponding attacks were immediately added to the SafeBreach Hacker’s Playbook™ on June 1st. Additionally, since these threat actors have been leveraging previously known vulnerabilities to gain initial access and move laterally before stealing critical data, our playbook already contains over 28 attacks that cover these vulnerabilities. Attacks are now ready to run individually or as part of the AA22-152A Karakurt Data Extortion scenario. We encourage you to evaluate your preparedness against the Karakurt group by running the attacks listed below.
6 newly added playbook attacks for Karakurt Group:
- #7081 – Pre-execution phase of Cobalt Strike malware (Host-Level)
- #7082 – Write Cobalt Strike malware to disk (Host-Level)
- #7083 – Transfer of Cobalt Strike malware over HTTP/S (Lateral Movement)
- #7084 – Transfer of Cobalt Strike malware over HTTP/S (Infiltration)
- #7085 – Email Cobalt Strike malware as a ZIP attachment (Lateral Movement)
- #7086 – Email Cobalt Strike malware as a ZIP attachment (Infiltration)
28 previously available playbook attacks for TTPs leveraged by the Karakurt Group:
- #103 – Data asset exfiltration using FTP STOR (ASCII) (exfiltration)
- #104 – Data asset exfiltration using FTP STOR (Binary) (exfiltration)
- #130 – Data asset exfiltration over TFTP (exfiltration)
- #161 – Malicious EXE File Inside a Macro of a Word File (lateral movement)
- #162 – Malicious EXE File Inside a Macro of a PPT File (lateral movement)
- #163 – Malicious EXE File Inside a Macro of an Excel File (lateral movement)
- #3829 – Run obfuscated Mimikatz on host (host level)
- #5532 – Email malicious Microsoft Word macro as a ZIP attachment (infiltration)
- #5567 – Path Traversal of Fortigate VPN vulnerability CVE-2018-13379 (infiltration)
- #5762 – Pre-execution phase of CobaltStrike_Beacon malware (host level)
- #5763 – Write CobaltStrike_Beacon malware to disk (host level)
- #5764 – Transfer of CobaltStrike_Beacon malware over HTTP/S (lateral movement)
- #5765 – Transfer of CobaltStrike_Beacon malware over HTTP/S (infiltration)
- #5766 – Email CobaltStrike_Beacon malware as a ZIP attachment (lateral movement)
- #5767 – Email CobaltStrike_Beacon malware as a ZIP attachment (infiltration)
- #6373 – Remote Exploitation of SonicWall SSLVPN using CVE-2021-20016 (infiltration)
- #6473 – Agentless lateral movement via RDP (host level)
- #6845 – Remote exploitation of Apache Log4j vulnerability CVE-2021-44228 (host level)
- #6857 -Obfuscated remote exploitation of Apache Log4j vulnerability CVE-2021-44228 (host level)
- #6861 – Remote exploitation of Apache Log4j vulnerability CVE-2021-44228 (infiltration)
- #6909 – RDP Connection Between 2 Simulators (infiltration)
- #7081 – Pre-execution phase of Cobalt Strike malware (host level)
- #7082 – Write Cobalt Strike malware to disk (host level)
- #7083 – Transfer of Cobalt Strike malware over HTTP/S (lateral movement)
- #7084 – Transfer of Cobalt Strike malware over HTTP/S (infiltration)
- #7085 – Email Cobalt Strike malware as a ZIP attachment (lateral movement)
- #7086 – Email Cobalt Strike malware as a ZIP attachment (infiltration)
- #794 – Extract Login Information using MimiKatz (host level)
What you should do now
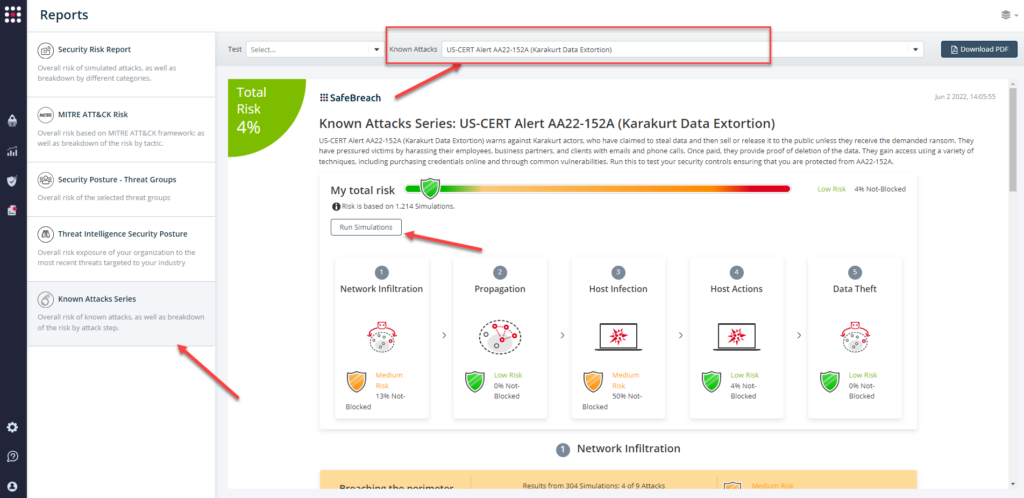
Attack methods related to US-CERT AA22-152A (Karakurt Data Extortion) are ready to run across your simulators. The Known Attack Series report has been updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT AA22-152A (Karakurt Data Extortion) report and select Run Simulations which will run all attack methods.
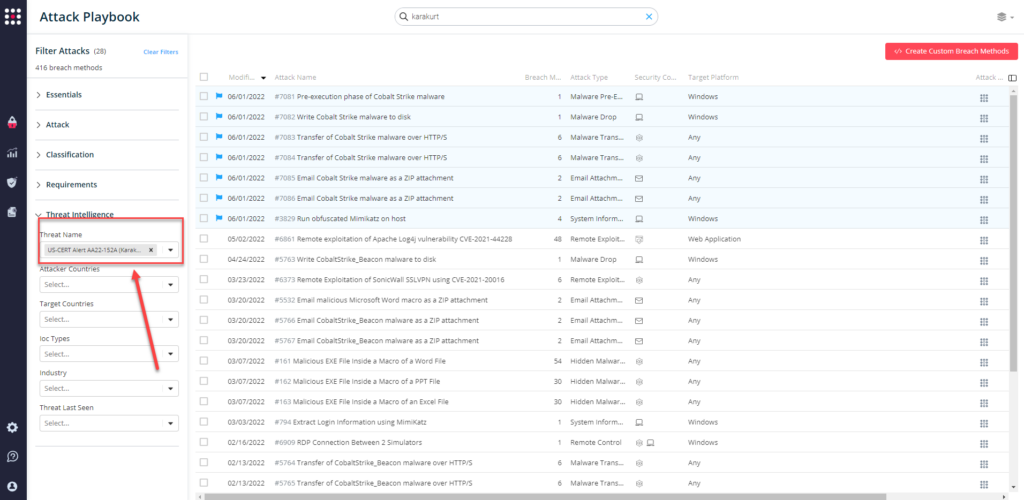
You can also select all the attacks related to US-CERT AA22-152A (Karakurt Data Extortion), by going to the SafeBreach Playbook and filtering by Threat Name – US-CERT AA22-152A (Karakurt Data Extortion)
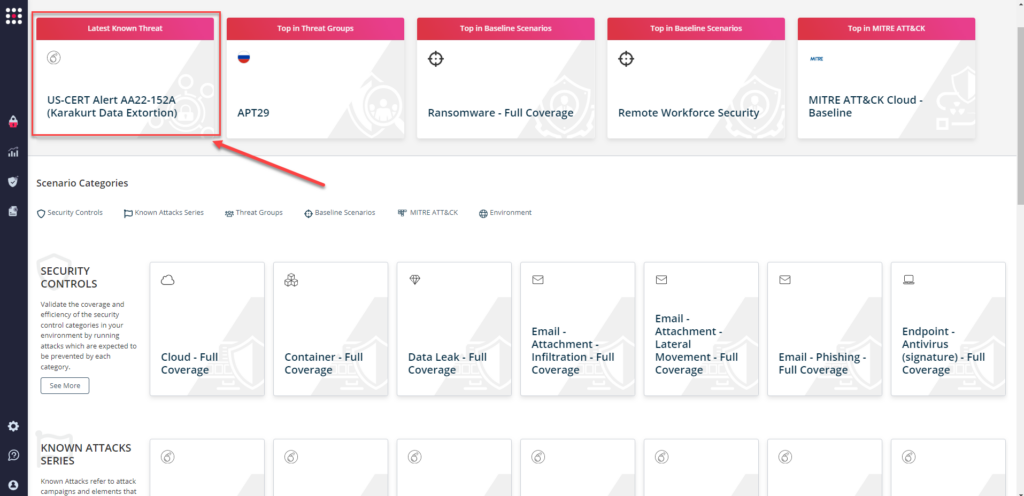
or you can go to “SafeBreach Scenarios” page and choose the US-CERT AA22-152A (Karakurt Data Extortion) scenario from the list of available scenarios.
NOTE – The following actions have been recommended to mitigate any potential attacks by the Karakurt Group:
- Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, and secure location (i.e., hard drive, storage device, the cloud).
- Implement network segmentation and maintain offline backups of data to ensure limited interruption to the organization.
- Regularly back up data and password protect backup copies offline. Ensure copies of critical data are not accessible for modification or deletion from the system where the data resides.
- Install and regularly update antivirus software on all hosts and enable real time detection.
- Install updates/patch operating systems, software, and firmware as soon as updates/patches are released.
- Review domain controllers, servers, workstations, and active directories for new or unrecognized accounts.
- Audit user accounts with administrative privileges and configure access controls with least privilege in mind. Do not give all users administrative privileges.
- Disable unused ports.
- Consider adding an email banner to emails received from outside your organization.
- Disable hyperlinks in received emails
- Enforce multi-factor authentication.