The second in a series of blogs from CEO, and former CISO, Guy Bejerano
Every year we see hundreds of new security startups emerge, all with the promise that they have found the solution that all the “old” security technologies cannot provide. Just by going to The RSA Security Conference, Black Hat, or any of the other major shows, you can get dizzy from all the new logos. The overwhelming number of startup booths to visit, let alone understand the product offering, will test the patience and fitness levels of any CISO.
But do we really need all these new toys when we haven’t really played with all the ones we already have? There are certainly new vendors each year, but under scrutiny, are they are all saying the same thing? I walked these shows this year, and I heard the same thing over and over. Because there are soooo many vendors, everyone tries to shine, and you end up with ridiculous statements like:
“We’re the only solution that uses [insert Machine Learning or Artificial Intelligence] to stop all threats.”
Now, there certainly is a lot of real innovation going on, but there are also a ton of buzzwords being thrown around. It’s hard not to get cynical! They can’t all be exactly the same, but at the marketing level, they sure sound the same. And what are they aiming to do that existing security controls cannot? The “old guard” of proxies, next generation firewalls, endpoint security solutions, they all intend to stop these same threats. So, is this chase after the shiny new toy really required?
Making the most of what you have
Before we, as security professionals, start investigating a new technology or solution, we have to ask ourselves, “Have we fully utilized our existing controls?” Are we getting anything close to 100% out of our investment in security technology? These are questions every CISO should ask themselves. These are the questions I had to answer as a CISO. And trust me – I didn’t like my answers.
In fact, that’s what led me to found SafeBreach. We believe that the missing part of the puzzle is the offensive layer. By simply adding that layer to your security stack you’ll be able to realize how good (or how terrible) your existing controls are. And so far, after hundreds of millions of simulations in real production deployments, we have proven that over 92% of attacks can be stopped with existing controls already in place. But typically, these attacks are not stopped. In fact, we find that 65-75% of attacks are able to make it through production security deployments.
Wait, what?
I can hear you now: “Wait, I thought you were trying to say “legacy” security controllers were good – but now you’re saying they are only 25% effective?!”
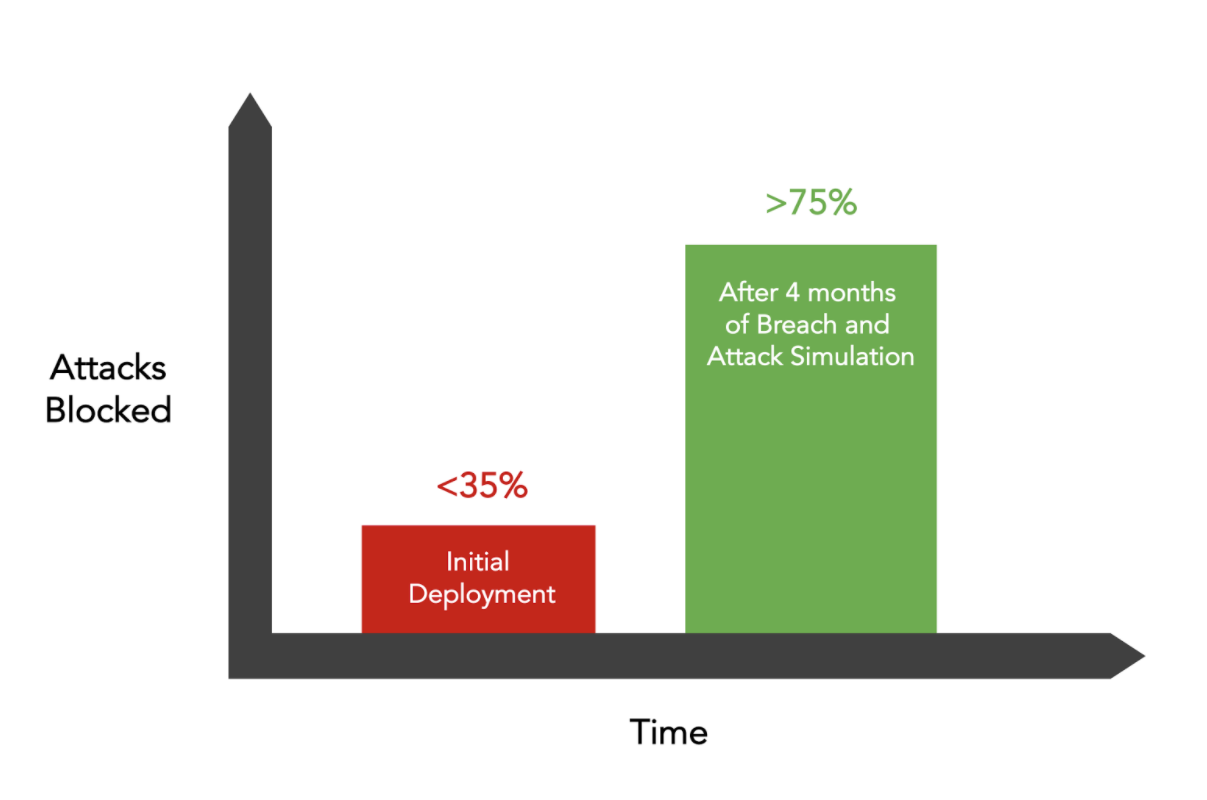
I want to be clear here: In our initial engagements, we see that production security stops less than 35% of all attacks. BUT! After security teams review the results, and implement the recommended actions, that number improves dramatically. In fact we see an average of 75% blocked attacks after 4 months of active deployment. And that’s typically without spending a dollar on new equipment or technologies—it’s simply from optimizing what’s in place.
So you see, these new companies’ claims that the “legacy” solutions aren’t stopping threats might be right, from a certain point of view. But when adding the offensive layer to the mix, we see the reason for that state. When you can validate security configuration before and after updates, or optimize features of a security product, or address missing functionality with the vendor, you can get way more performance and effect out of existing solutions.
Prove it!
This all might sound a little academic, but here are some true stories to bring it home. After SafeBreach ran breach and attack simulations in customer environments, we found:
Servers and laptops that were victim to proven ransomware attacks
- Problem: These machines all had AV and a very popular endpoint protection solution installed, but it was misconfigured, and didn’t stop bad payloads from being installed on disk.
- Solution: A simple configuration change blocked all subsequent attempts to install various ransomware across all machines.
Successful malware command and control connectivity from production network
- Problem: Lack of outbound scanning allowed C2 traffic to establish connection outside the firewall, which opened risk for inbound traffic to follow that back due to stateful firewall rules.
- Solution: Existing next-gen firewall policy was updated to scan outbound traffic for known bad sources, as well as scan inbound for malicious payloads despite origin request from within the network.
Ability to exfiltrate credit card information via telnet
- Problem: Telnet was simply open over port 25, allowing for remote exfiltration out of the PCI segment of a regulated network. The firewall team was sure they had blocked this, but rule conflict amongst hundreds of rules on the firewall meant that port 25 was actually open and unscanned.
- Solution: A simple rule on another layer of security solved the problem in minutes, allowing the firewall team time to clean up the ruleset that initially cause the issue.
Spend less, do more
In each of the examples above (and in most of our deployments overall) we see that existing solutions simply aren’t optimized as well as they could be. It’s easy to see why – with so many security controls, myriad security features and so many different ways to configure, teams can get overwhelmed, or new initiatives can steal focus away from staying on top of already-deployed technology. This leads to never moving past default config, or stale config, or just compounding configuration errors, which attackers take advantage of to breach environments.
Even in well-designed environments, optimization can still be possible. In fact, in a recent deployment at a customer with a very mature security program, they found they were able to improve their perimeter security dramatically with just simple configuration changes. When they initially baselined with SafeBreach, just over 30% of infiltration simulations were able to successfully make it past their defenses. After modification configuration based on SafeBreach findings, that number was brought to just 9%.
Indeed, your best decision today could be to stop buying new technologies until you make sure you make the most of your current investment. Breach and Attack simulation—whether it’s from SafeBreach, or other players in the space—can help you determine where you can get more from your existing technologies.