On September 22nd, the Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and the Federal Bureau of Investigation (FBI) alerted about the increased use of Conti ransomware in more than 400 attacks on U.S. and international organizations. Details of the various tactics, techniques, and procedures (TTPs) are described in US-CERT Alert (AA21-265A) – Conti Ransomware. Threat actors leveraging Conti Ransomware steal files, encrypt servers and workstations and demand a ransom payment.
Conti ransomware uses the ransomware-as-a-service (RaaS) model and threat actors leveraging Conti ransomware often gain access to organizations in one of the following ways:
- Using spear-phishing campaigns that leverage malicious attachments or malicious links
- Stolen or weak Remote Desktop Protocol (RDP) credentials
- Having users download fake software
- Exploiting common vulnerabilities in external-facing assets
According to the details provided by CISA and FBI, the ransomware during its execution phase, uses Router Scan, a penetration testing tool, to maliciously scan for and brute force routers, cameras, and network-attached storage devices with web interfaces. Threat actors have also been observed to use Kerberos attacks in an attempt to get the Admin hash to conduct brute force attacks. CISA and FBI also observed that Conti actors are known to exploit legitimate remote monitoring and management software and remote desktop software as backdoors to maintain persistence on victim networks.
During the exfiltration phase, Conti actors often use the open-source Rclone command line program. After the actors steal and encrypt the victim’s sensitive data, they employ a double extortion technique in which they demand the victim pay a ransom for the release of the encrypted data and threaten the victim with the public release of the data if the ransom is not paid.
It is worth noting that the SafeBreach Hacker’s Playbook™ already incorporates 24 attacks that leverage the identified TTPs including:
- #5318 – Pre-execution phase of Conti ransomware (eae876)
- #6482 – Remote Code Execution via CVE-2021-34527 (PrintNightmare)
- #6481 – Local Privilege Escalation using CVE-2021-1675 (PrintNightmare)
- #6473 – Agentless lateral movement via RDP
- #2188 – Extract Process List using Windows Commands
- #6372 – Modify Volume Shadow Copy (VSS)
- #1511 – Remote exploitation of an SMB server exploiting CVE-2017-0144 (WannaCry)
- #5319 – Write Conti ransomware to disk (eae876)
- #5321 – Transfer of Conti ransomware over HTTP/S (eae876)
- #1309 – Brute force attack over the RDP protocol
- #2273 – Pass the Hash over SMB using Mimikatz
- #5320 – Transfer of Conti ransomware over HTTP/S (eae876)
- #6246 – Exploit ZeroLogon (CVE-2020-1472) (Windows)
- #794 – Extract Login Information using MimiKatz
- #3830 – Extract credentials using PwDump through PowerShell
- #5487 – Exploit CVE-2020-1472 ZeroLogon
- #5323 – Email Conti ransomware as a ZIP attachment (eae876)
- #5322 – Email Conti ransomware as a ZIP attachment (eae876)
- #5106 – Execute a simulation of a Conti ransomware variant
- #2192 – Collect Data from Local Shared Drives using System Commands
- #5107 – Stop a service using net stop command
- #3829 – Run obfuscated Mimikatz on host
- #192 – Brute force attack over RDP protocol
- #163 – Malicious EXE File Inside a Macro of an Excel File
What you should do now
The existing attack methods for US-CERT AA21-265A Conti Ransomware are already in the SafeBreach Hacker’s playbook and ready to be run across your simulators. The Known Attack Series report is updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT AA21-265A (Conti Ransomware) report and select Run Simulations which will run all attack methods.
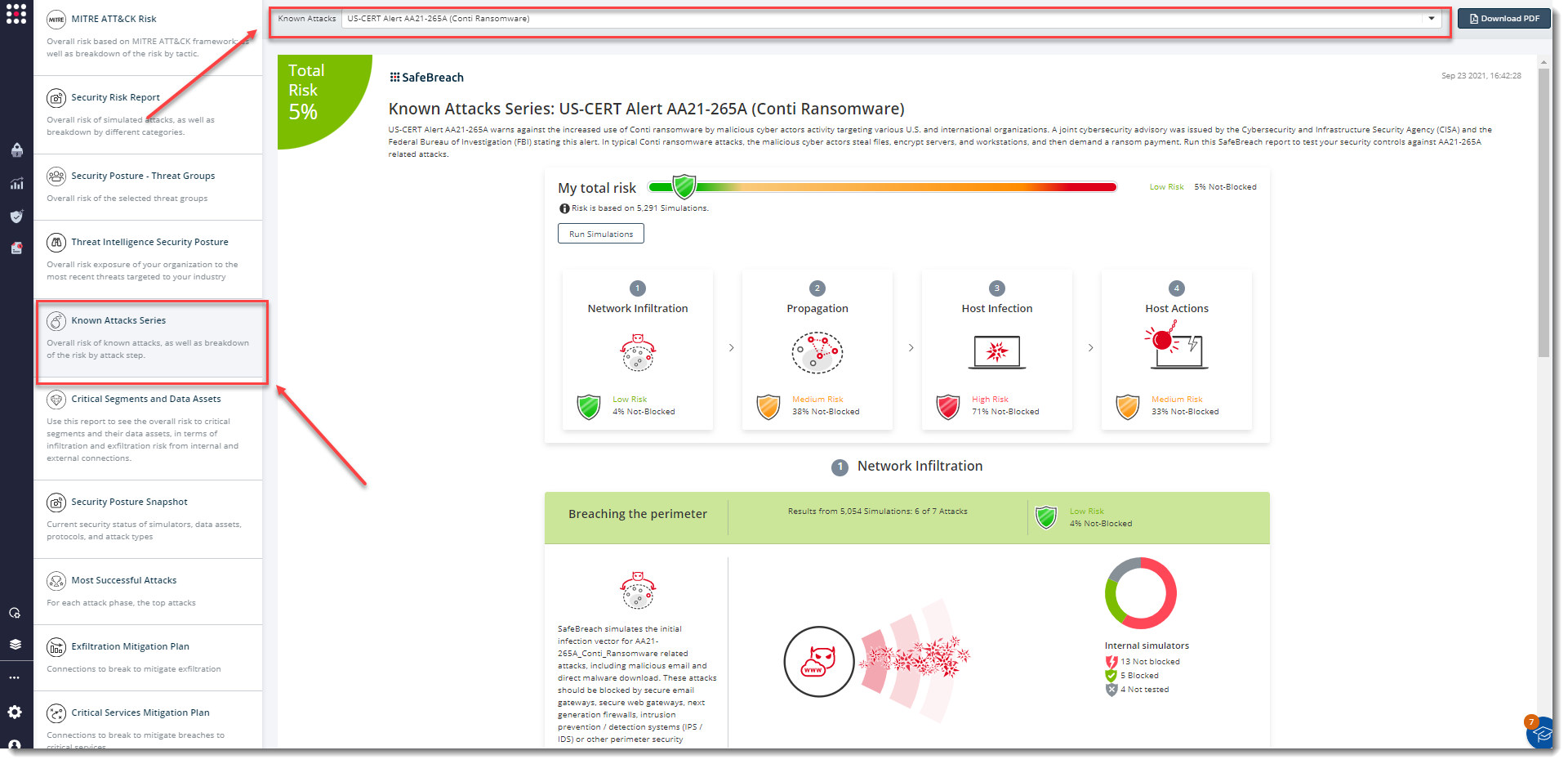
Additionally, CISA, FBI, and NSA are recommending that security teams apply the following mitigations to reduce the risk of compromise by Conti Ransomware attacks:
- Use multi-factor authentication
- Implement network segmentation and filter traffic
- Scan for vulnerabilities and keep software updated
- Remove unnecessary applications and apply controls
- Implement endpoint and detection response tools
- Limit access to resources over the network, especially by restricting RDP
- Secure user accounts