SafeBreach is the only continuous security validation platform that automatically calculates all attack paths within your environment based on real malware behavior and real actions. This allows us to provide enterprise security teams with detailed insights for both high- and low-value targets, the ability to prioritize vulnerabilities based on their environment, and actionable intelligence for remediation. For the last several years, we’ve distinguished ourselves from other breach and attack simulation (BAS) vendors by being the only provider to offer its customers a 24-hour service-level agreement (SLA) on incorporating newly identified threats from US-CERT alerts to our extensive Hacker’s Playbook™. We are excited to announce that SafeBreach will now offer the same 24-hour SLA on new-and-emerging threats identified in FBI Flash alerts. Adding rapid coverage of these newly identified TTPs and IOCs will allow our customers to proactively validate their security controls against the rapidly evolving threat landscape.
Why Does This Matter?
The FBI Flash alerts are designed to help cybersecurity professionals and system administrators’ guard against the persistent malicious actions of cyber actors. SafeBreach customers can now gain the ability to leverage this critical threat intelligence provided by the SafeBreach Labs team to gain an understanding of precisely which threats pose an organizational risk and accordingly devise a plan to respond to such threats. Incorporating the FBI’s newly identified threats into our Hacker’s Playbook in under 24 hours will empower our customers to drive prioritization and timely validation of real attacks. Counter threat intelligence (CTI) teams can also leverage this information to identify which attack scenarios to run and which TTPs to simulate to maintain a hardened security posture.
Examples of Past Coverage
When a new and relevant US-CERT/FBI Flash alert (with actionable IOCs) is issued, SafeBreach Labs researchers add the threat to the Hacker’s Playbook within 24 hours—guaranteed. This allows us to ensure that the SafeBreach platform provides customers with the most salient and up-to-date threat information that they can validate their controls against. Below is a timeline of our coverage for threats included in the US-CERTs in the last 11 months.
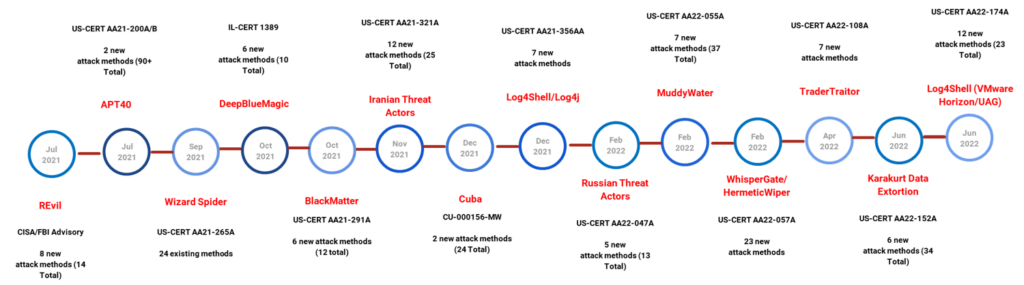
Incorporating newly identified attacks in our playbook within 24 hours has allowed our customers to protect themselves against critical attacks such as SolarWinds, Log4Shell, Cuba Ransomware, nation-state sponsored threats like MuddyWater, and many more.
What Can SafeBreach Customers Expect?
When new attacks are added to the playbook, customers can choose to run these attacks and understand their level of exposure in one of three ways:
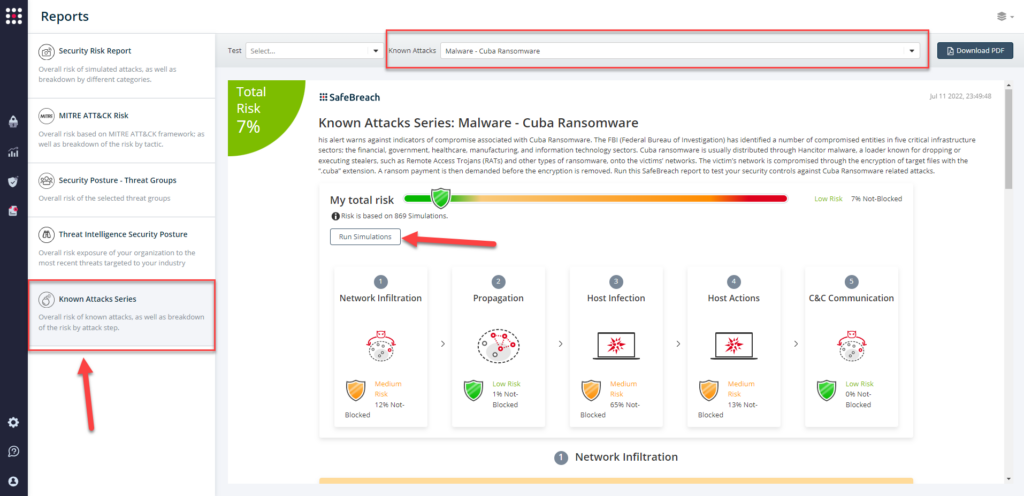
- Known Attacks Report (KAR) – Customers can select the corresponding KAR from the Reports tab and choose “Run Simulations” to run all attacks corresponding to the FBI Flash.
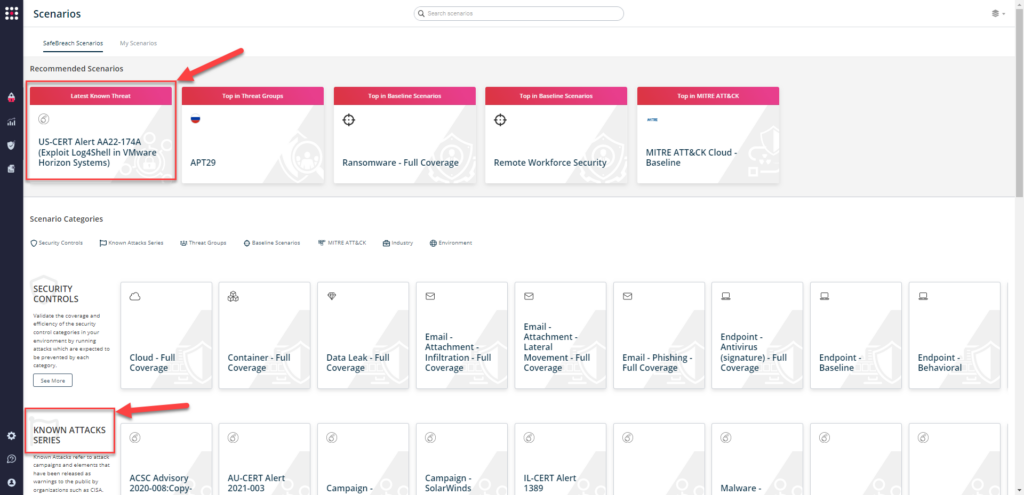
- SafeBreach Scenarios – Customers can go to the SafeBreach Scenarios page and choose the corresponding scenario from the “Known Attack Series” to run all the attacks associated with the FBI Flash.
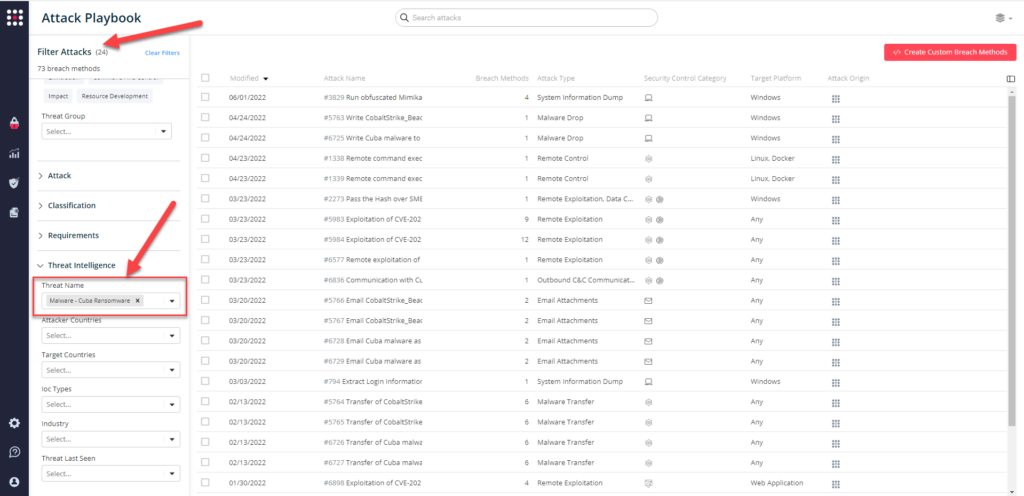
- From Hacker’s Playbook – Customers can select all the attacks related to the FBI Flash by going to the SafeBreach Playbook and filtering by the specific threat name.
Why Trust SafeBreach?
- SafeBreach is the only continuous security validation platform that automatically calculates all attack paths within your environment based on real malware behavior and real actions, all run in a controlled manner, safely, and at scale.
- Our continuous security validation platform provides mitigation and detection guidance from MITRE ATT&CK and real, actionable threat intelligence enabling remediation based on quantitative evidence of the efficacy of your security controls across technology, processes, and people.
- We uphold a 24-hour SLA with automatic US-CERT/FBI Flash alerts that provide updated threat intelligence to align with new TTPs and/or IOCs used by threat actors.
- We map to the Top-16 MITRE ATT&CK workflows that cover 90% of attacks from 2019 thru 2021.
- Our continuous security validation platform works seamlessly with your security controls and tech stack, including SIEM, SOAR, EDR, workflow management, and vulnerability management tools to automatically correlate events, actions, alerts, and activities.
- We provide an accurate picture with real data visualization from all your simulation results that provides you with in-depth details for both high- and low-value targets, prioritization of vulnerabilities, and actionable intelligence for remediation.
- Our platform combines real-time threat intelligence to ensure you know precisely which threats pose a safety or operational risk to get timely, accurate, and relevant information to those who need it.