On August 11, the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) released a joint advisory US-CERT Alert (AA22-223A) Zeppelin Ransomware that highlighted crucial details about the Zeppelin ransomware identified through extensive FBI investigations conducted as recently as June 21, 2022. This advisory also contains crucial tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) that can allow security operations teams to effectively detect and block this ransomware strain.
Additional Details about Zeppelin Ransomware
According to the advisory, the Zeppelin ransomware is a derivative of the Delphi-based Vega malware family and can function on a ransomware-as-a-service (RaaS) model. Threat actors have continually used this strain from 2019 to 2022 to target a wide range of businesses and critical infrastructure entities, including defense contractors, educational institutions, manufacturers, technology companies, and especially healthcare and medical industries.
These threat actors typically gain access to a victim’s network via remote desktop protocol (RDP) exploitation, exploiting SonicWall vulnerabilities, and phishing campaigns. Once they gain access, they spend one to two weeks understanding and mapping the victim’s network to identify data enclaves, including cloud storage and data backups. They then deploy the Zeppelin ransomware as a [dot]exe, [dot]dll file, or contained within a PowerShell loader. A ransom note file is left on compromised systems. Zeppelin threat actors execute the malware multiple times within the victim’s network, resulting in multiple levels of encryption. They have been known to request ransom amounts ranging from a few thousand to over a million dollars – paid in Bitcoin.
Important Note for SafeBreach Customers – Coverage for AA22-223A
As soon as details and IOCs were made available by CISA and the FBI, corresponding attacks were immediately added to the SafeBreach Hacker’s Playbook™ on August 12th. We encourage you to run the following new attacks to ensure preparedness against the Zeppelin ransomware.
5 newly added playbook methods for AA22-223A
- #7445 – Write Zeppelin malware to disk (Host-Level)
- #7446 – Transfer of Zeppelin malware over HTTP/S (Lateral Movement)
- #7447 – Transfer of Zeppelin malware over HTTP/S (Infiltration)
- #7448 – Email Zeppelin malware as a ZIP attachment (Lateral Movement)
- #7449 – Email Zeppelin malware as a ZIP attachment (Infiltration)
What You Should Do Now
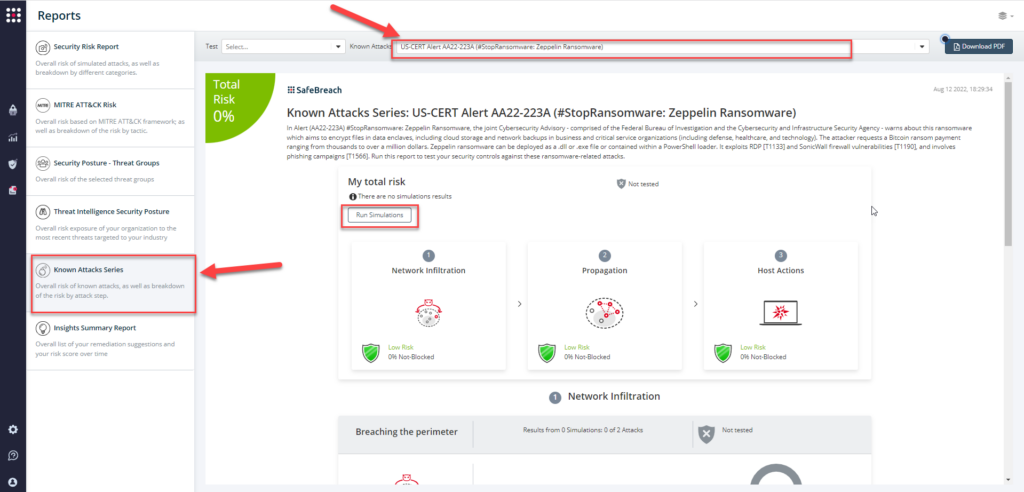
Attack methods related to US-CERT Alert AA22-223A are ready to run across your simulators. The Known Attack Series report has been updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT Alert AA22-223A (#StopRansomware: Zeppelin Ransomware) report and select Run Simulations which will run all attack methods.
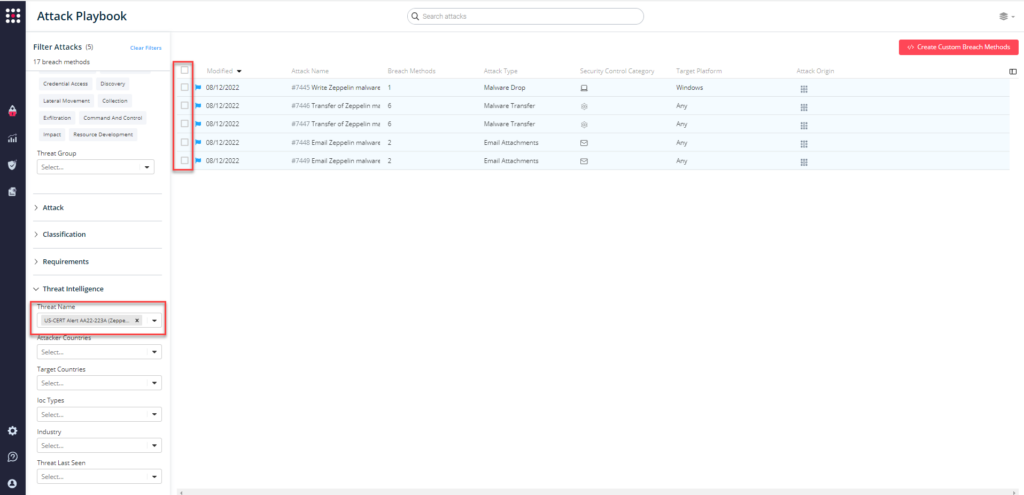
You can also select all the attacks related to US-CERT Alert AA22-223A by going to the SafeBreach Playbook and filtering by Threat Name – US-CERT Alert AA22-223A (Zeppelin Ransomware)
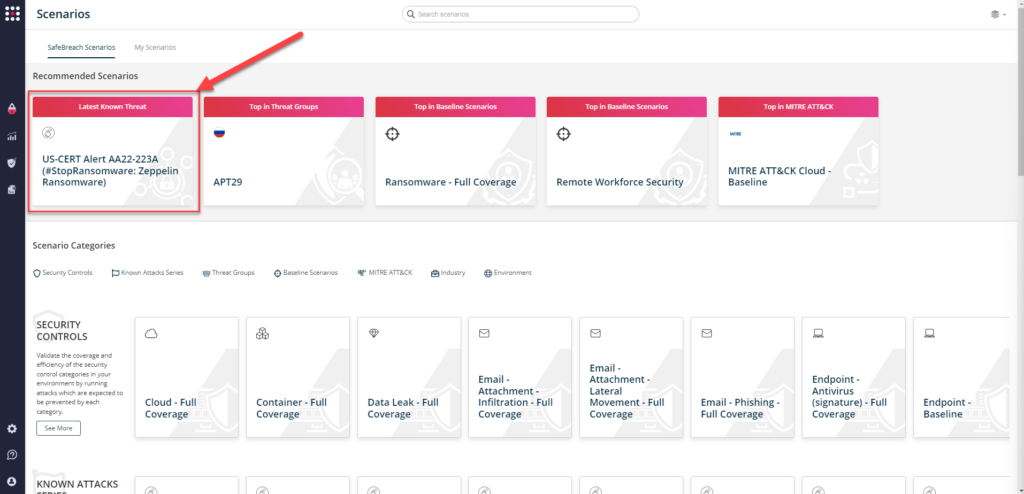
or you can go to “SafeBreach Scenarios” page and choose the US-CERT Alert AA22-223A (#StopRansomware: Zeppelin Ransomware) scenario from the list of available scenarios.
NOTE: The following actions have been recommended by CISA and the FBI to mitigate any threat originating from the Zeppelin ransomware.:
- Prioritize remediating known exploited vulnerabilities.
- Train users to recognize and report phishing attempts.
- Enable and enforce multifactor authentication.
- Implement a recovery plan.
- Segment networks to prevent the spread of ransomware.
- Implement time-based access for admin accounts.
- Disable command line scripting activities and permissions.