
In light of the ongoing cyber threat posed by the Iranian Islamic Revolutionary Guard Corps (IRGC) and other highly motivated nation-state actors, the Cybersecurity and Infrastructure Security Agency (CISA) is exhorting enterprises to choose a more proactive approach to defend themselves. This is the first time CISA and cybersecurity agencies around the world are recommending enterprises automate continuous validation of security controls to protect against the constantly evolving threat landscape.
CISA’s recommendation is very timely as it was discovered that Iranian nation-state threat actors were continuing to exploit known vulnerabilities like the Fortinet FortiOS vulnerability, MS Exchange vulnerabilities, ProxyShell vulnerability, and even the VMware Horizon Log4J vulnerability to target enterprises and critical U.S. infrastructure entities, gain access, steal sensitive data, and potentially hold it for ransom. According to CISA, continuously and proactively validating security controls can make the organization more resilient to threat attackers leveraging established TTPs to breach them.
According to SafeBreach CISO Avi Avivi, “This latest announcement and joint cybersecurity advisory highlights the rise in ransomware attacks. Whether state-backed, by criminal groups, or even individuals, the bottom line is they don’t necessarily care about who the victim is. Their goal is to ransom the victim companies for as much as they can. In that same manner, we recommend that companies not assume that just because they’re not a critical infrastructure vendor or a huge retailer, they are not impacted. These companies can easily be a target, and potentially a victim.”
How SafeBreach Can Help
Breach and attack simulation (BAS) solutions—designed to continuously test the effectiveness of security controls and identify potential vulnerabilities accessible to attackers—have emerged as a powerful tool to help organizations navigate this new reality. BAS solutions are quickly becoming a key technology for CISOs looking to properly leverage existing security controls and guard against security drift.
The SafeBreach BAS platform runs real-world attack simulations—based on real threat intelligence, real malware behavior, and real-world actions—against production applications and infrastructure within your environment safely and at scale. They test if systems are vulnerable to attacks by:
- Continuously validating that security controls are in place, properly configured, and working as intended
- Providing visibility into how the entire security ecosystem responds at each stage of the defense process
SafeBreach Coverage for US-CERT Alert (AA22-257A) – IRGC- Affiliated Threat Actors
On September 14, the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), U.S. Cyber Command (USCC) – Cyber National Mission Force (CNMF), the Department of the Treasury (Treasury), the Australian Cyber Security Centre (ACSC), the Canadian Centre for Cyber Security (CCCS), and the United Kingdom’s National Cyber Security Centre (NCSC) issued a joint advisory highlighting the ongoing and continued malicious cyber activity by advanced persistent threat (APT) actors affiliated with the Iranian Government’s Islamic Revolutionary Guard Corps (IRGC). Additional details about these threat actors and its associated tactics, techniques, and procedures (TTPs) are available in US-CERT Alert (AA22-257A) Iranian Islamic Revolutionary Guard Corps-Affiliated Cyber Actors Exploiting Vulnerabilities for Data Extortion and Disk Encryption for Ransom Operations.
Additional Technical Details
According to the advisory, IRGC threat actors are exploiting known Fortinet and MS Exchange vulnerabilities to gain initial access to a broad range of entities. These threat actors have also been observed exploiting the VMWare Horizon Log4j vulnerability to gain access and then perform disk encryption and data extortion. These threat actors don’t have specific targets, instead, they exploit known vulnerabilities on unprotected networks.
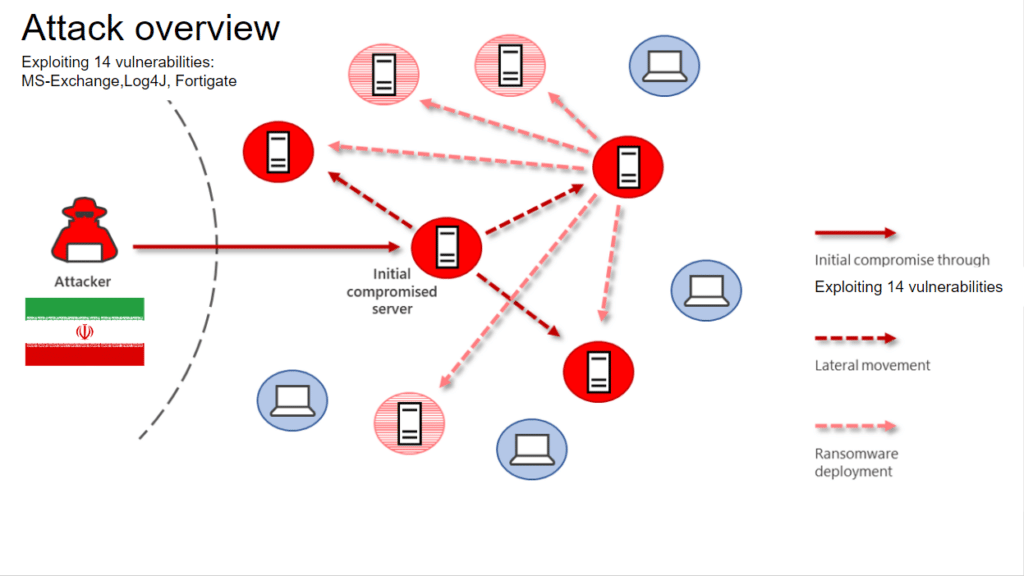
The IRGC-affiliated actors have used their access for ransom operations, including disk encryption and extortion efforts. After gaining access to a network, the IRGC-affiliated actors likely determine a course of action based on their perceived value of the data. Depending on the perceived value, the actors may encrypt data for ransom and/or exfiltrate data. The actors may sell the data or use the exfiltrated data in extortion operations or “double extortion” ransom operations where a threat actor uses a combination of encryption and data theft to pressure targeted entities to pay ransom demands.
Since December 2021, the IRGC-affiliated threat actors have been responsible for:
- Exploiting ProxyShell vulnerabilities (likely CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207) on a Microsoft Exchange server to gain access to the network of a U.S. police department.
- Exploiting ProxyShell vulnerabilities (likely CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207), on a Microsoft Exchange server to gain access to the network of a U.S. regional transportation company.
- Exploiting a Log4j vulnerability (likely CVE-2021-44228, CVE-2021-45046, and/or CVE-2021-45105) in a VMware Horizon application to gain access to the network of a U.S. municipal government.
- Exploiting a Log4j vulnerability (likely CVE-2021-44228, CVE-2021-45046, and/or CVE-2021) to gain access to the network of a U.S. aerospace company.
IMPORTANT NOTE for SafeBreach Customers – Coverage for AA22-257A
As soon as details and IOCs for the ongoing exploitation by IRGC-affiliated threat actors were made available, corresponding new attacks were immediately added to the SafeBreach Hacker’s Playbook™ on September 15. It is important to note that since the IRGC-affiliated threat actors have been leveraging known vulnerabilities, SafeBreach customers already had an existing level of protection against these threat actors if their security controls were validated against these known TTPs.
23 newly added playbook methods for US-CERT Alert AA22-257A:
- Malware IOCs
- #7593 – Pre-execution phase of IRGC (6d1a) malware (Host-Level)
- #7594 – Write IRGC (6d1a) malware to disk (Host-Level)
- #7595 – Transfer of IRGC (6d1a) malware over HTTP/S (Lateral Movement)
- #7596 – Transfer of IRGC (6d1a) malware over HTTP/S (Infiltration)
- #7597 – Email IRGC (6d1a) malware as a ZIP attachment (Lateral Movement)
- #7598 – Email IRGC (6d1a) malware as a ZIP attachment (Infiltration)
- #7599 – Pre-execution phase of IRGC (b00b) malware (Host-Level)
- #7600 – Write IRGC (b00b) malware to disk (Host-Level)
- #7601 – Transfer of IRGC (b00b) malware over HTTP/S (Lateral Movement)
- #7602 – Transfer of IRGC (b00b) malware over HTTP/S (Infiltration)
- #7603 – Email IRGC (b00b) malware as a ZIP attachment (Lateral Movement)
- #7604 – Email IRGC (b00b) malware as a ZIP attachment (Infiltration)
- FRP IOCs
- #7605 – Pre-execution phase of FRP_UPX (Windows) malware (Host-Level)
- #7606 – Write FRP_UPX (Windows) malware to disk (Host-Level)
- #7607 – Transfer of FRP_UPX (Windows) malware over HTTP/S (Lateral Movement)
- #7608 – Transfer of FRP_UPX (Windows) malware over HTTP/S (Infiltration)
- #7609 – Email FRP_UPX (Windows) malware as a ZIP attachment (Lateral Movement)
- #7610 – Email FRP_UPX (Windows) malware as a ZIP attachment (Infiltration)
- #7611 – Write FRP_UPX (Linux) malware to disk (Host-Level)
- #7612 – Transfer of FRP_UPX (Linux) malware over HTTP/S (Lateral Movement)
- #7613 – Transfer of FRP_UPX (Linux) malware over HTTP/S (Infiltration)
- #7614 – Email FRP_UPX (Linux) malware as a ZIP attachment (Lateral Movement)
- #7615 – Email FRP_UPX (Linux) malware as a ZIP attachment (Infiltration)
21 previously available playbook attacks for AA22-257A:
- Vulnerability Exploitation
- #5567 – Path Traversal of Fortigate VPN vulnerability CVE-2018-13379
- #6576 – Remote exploitation of Microsoft Exchange ProxyShell vulnerability CVE-2021-34473
- #6577 – Remote exploitation of Microsoft Exchange ProxyShell vulnerability CVE-2021-34523
- #6843 – Communication with a real malicious server exploiting CVE-2021-44228 (log4j) using LDAP
- #6844 – Communication with server vulnerable to CVE-2021-44228 (log4j) using HTTP/s
- #6856 – Obfuscated communication with server vulnerable to CVE-2021-44228 (log4j) using HTTP/s
- #6858 – Communication with server vulnerable to CVE-2021-45105 (log4j2) using HTTP/s
- #6860 – Communication with server vulnerable to CVE-2021-45046 (log4j) using HTTP/s
- #6861 – Remote exploitation of Apache Log4j vulnerability CVE-2021-44228
- #6903 – Malicious payloads of Apache Log4j 2 vulnerability
- Techniques
- #1269 – Creating Windows schedule task (schtasks)
- #2164 – Scheduled Task
- #2170 – Create Account (Windows)
- #2171 – Create Account (Linux)
- #2189 – Account Manipulation
- #2308 – Install Root CA
- #6127 – Extract LSASS memory dump using PowerShell and Rundll32
- #6473 – Agentless lateral movement via RDP
- #6909 – RDP Connection Between 2 Simulators
- #7045 – Create System Account (Linux)
- #7170 – Add a local administrator (Windows)
What You Should Do Now
Attack methods related to US-CERT Alert AA22-257A are ready to run across your simulators. The Known Attack Series report has been updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT Alert AA22-257A (IRGC) report and select Run Simulations which will run all attack methods.
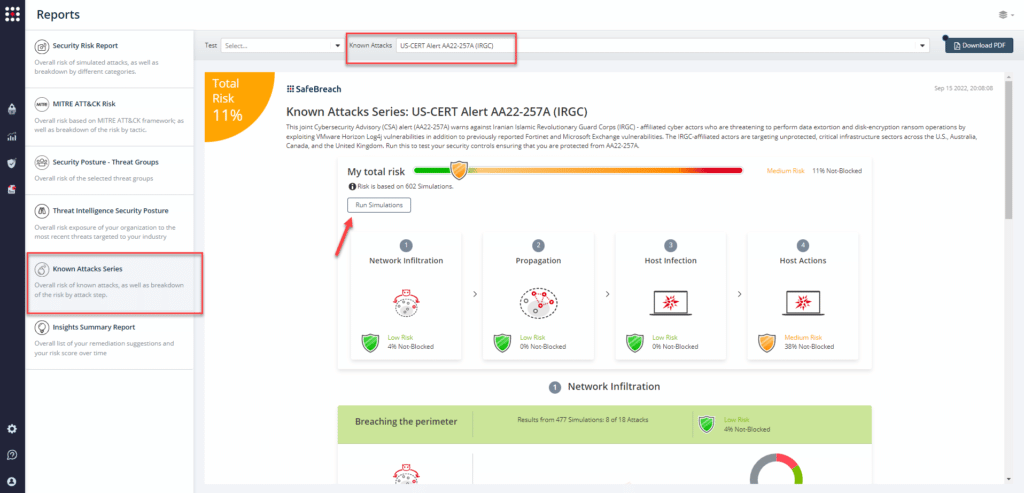
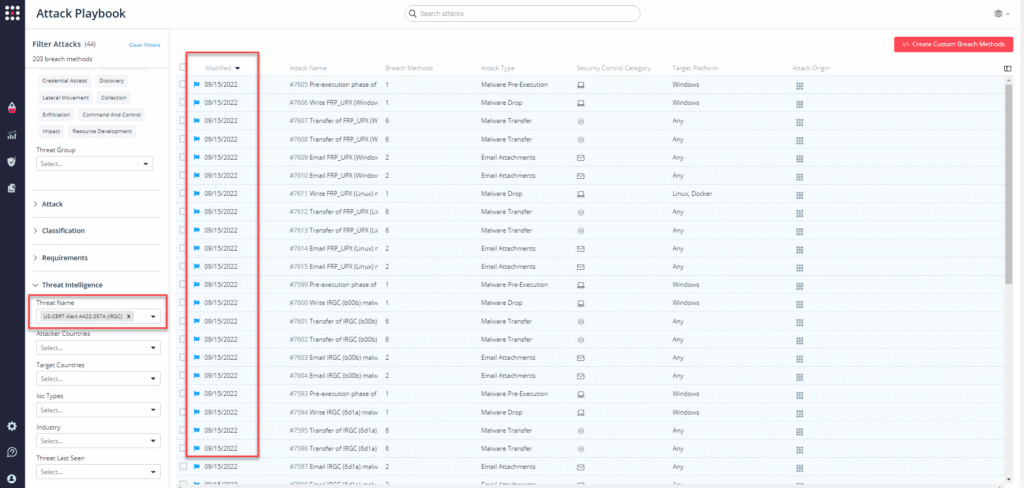
You can also select all the attacks related to US-CERT Alert AA22-257A by going to the SafeBreach Playbook and filtering by Threat Name – US-CERT Alert AA22-257A (IRGC)
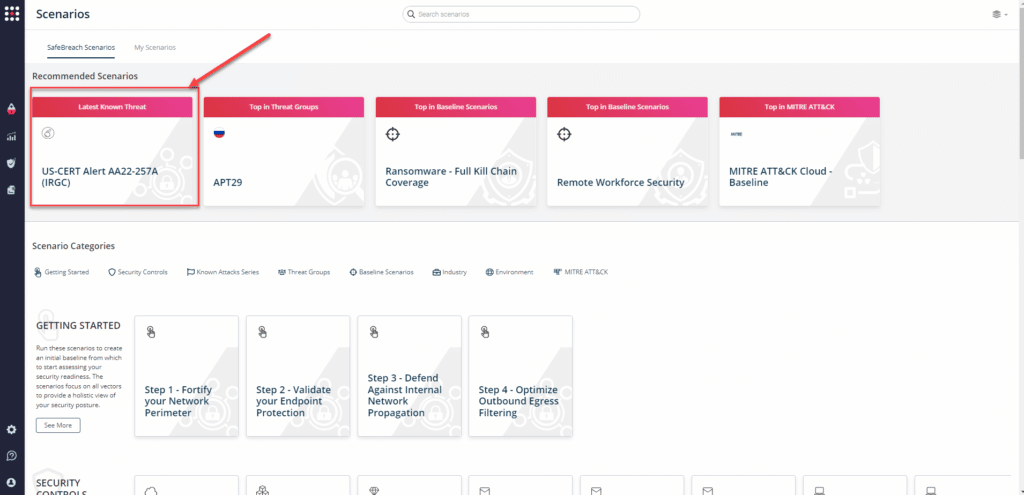
or you can go to “SafeBreach Scenarios” page and choose the US-CERT Alert AA22-257A (IRGC) scenario from the list of available scenarios.
NOTE – The following actions have been recommended to mitigate any threat arising from IRGC-affiliated threat actors:
- Keep systems and software updated and prioritize remediating known exploited vulnerabilities.
- Enforce MFA.
- Make offline backups of your data.
- Additional recommendations can be seen in the “Mitigations” section here.