On October 13th, the Hillel Yaffe Medical Center in Hadera, Israel was targeted by a ransomware attack that affected its computer systems (medical devices were not affected). The medical center is a major hospital serving a population of nearly 500K residents. Based on the current information available, this attack has been attributed to a new threat actor DeepBlueMagic. The group is using a brand-new ransomware called DeepBlueMagic that was first discovered in the wild in August 2021. It is not known whether the ransomware attack was a terror attack or if it was financially motivated.
It is suspected that the group leveraged a vulnerability in the Pulse Connect Secure VPN to get access to the IT systems of the Hillel Yaffe Medical Center. Once inside the network, the ransomware leveraged a legitimate disk encryption tool (BestCrypt Volume Encryption by Jetico) to encrypt the system drives as well as the rescue file (used by the Jetico tool to recover a partition in case of damage). They were then able to leverage the recently discovered Hive Nightmare Vulnerability to steal information in the Security Account Manager (SAM) from the Windows Volume Shadow File. The threat actors then went on to delete the Volume Shadow File to prevent any data from being restored. Additionally, it also tried to leverage Active Directory to activate BitLocker encryption on all the endpoints in the medical center network.
NOTE – The SafeBreach Hacker’s Playbook has been updated to include the newly discovered tactics and techniques from this alert. We encourage you to test your preparedness against the DeepBlueMagic Ransomware by running the attacks listed below.
6 newly developed playbook methods related to DeepBlueMagic Ransomware
- #6637 – Write DeepBlueMagic_Ransomware to disk (Host-Level)
- #6638 – Transfer of DeepBlueMagic_Ransomware over HTTP/S (Lateral Movement)
- #6639 – Transfer of DeepBlueMagic_Ransomware over HTTP/S (Infiltration)
- #6640 – Email DeepBlueMagic_Ransomware as a ZIP attachment (Lateral Movement)
- #6641 – Email DeepBlueMagic_Ransomware as a ZIP attachment (Infiltration)
- #6642 – Exploit the Hive Nightmare Vulnerability (CVE-2021-36934)
It is worth noting that the SafeBreach Hacker’s Playbook™ already incorporates 4 attacks that leverage the identified TTPs including:
- #4271 – Remote exploitation of Pulse VPN vulnerability CVE-2019-11510
- #6128 – Remote exploitation of Pulse VPN vulnerability CVE-2021-22893
- #6130 – Remote exploitation of Pulse VPN vulnerability CVE-2020-8260
- #6372 – Modify Volume Shadow Copy (VSS)
What you should do now
The new and existing attack methods for IL-CERT Alert 1389 (DeepBlueMagic Ransom) are already in the SafeBreach Hacker’s playbook and ready to be run across your simulators. The Known Attack Series report is updated so you can run the specific attacks from this alert. From the Known Attack Series report, select the IL-CERT Alert 1389 (DeepBlueMagic Ransom) report and select Run Simulations which will run all attack methods.
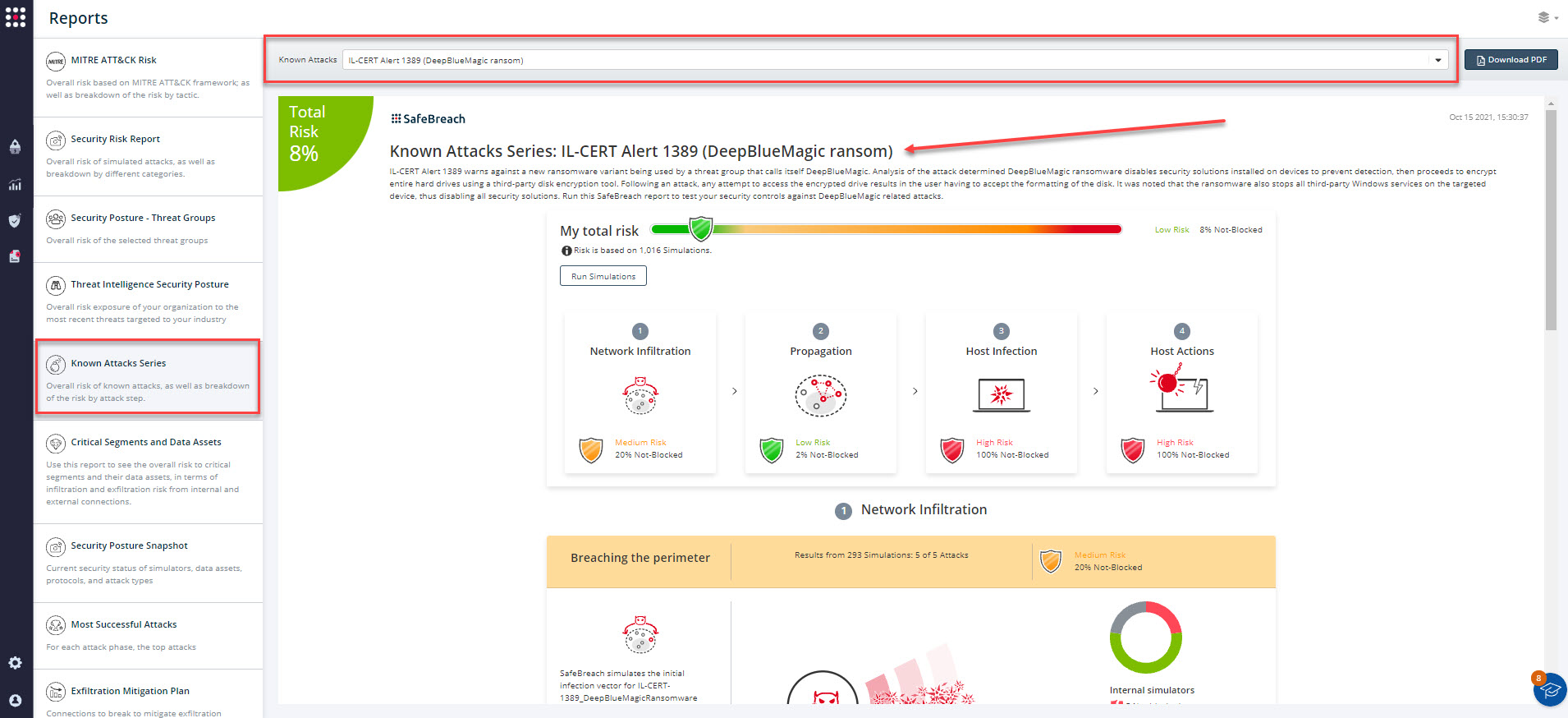
Additionally, you can also select all the attacks related to IL-CERT 1389 (DeepBlueMagic Ransomware), by going to the SafeBreach Playbook and filtering by Threat Name – IL-CERT Alert 1389 (DeepBlueMagic Ransom).
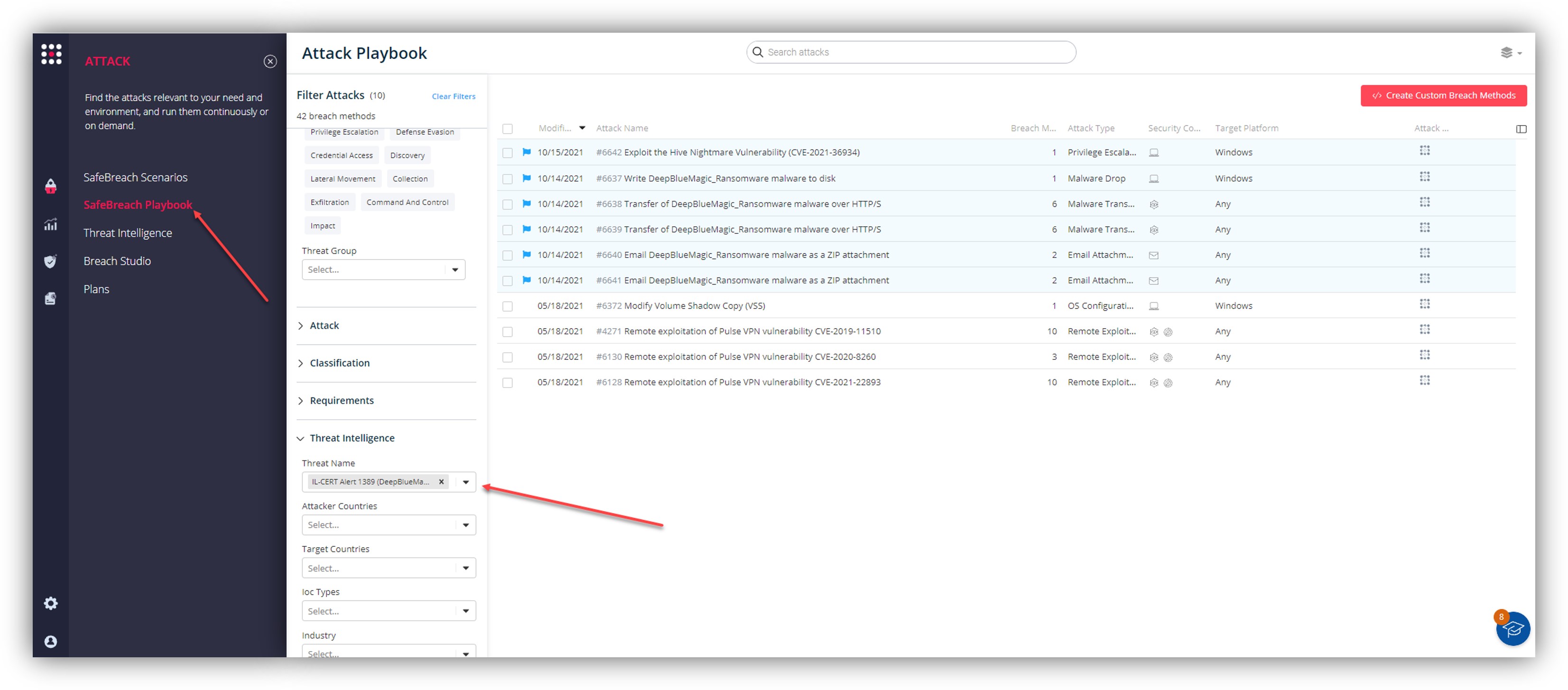
Additionally, the following steps are recommended to secure your organization against the DeepBlueMagic Ransomware:
- Use an EDR/AV solution to scan your environment for any identified TTPs
- Update your endpoints running Windows 10/11 with the latest security patches
- Update your Email servers and VPN solutions with the latest available security patches
- Update your passwords to prevent unauthorized access via stolen credential files