SafeBreach Labs has updated the SafeBreach Hacker’s Playbook™ with new attack methods for malware samples described in US-CERT Active Exploitation of SolarWinds Software, which addresses a widespread sophisticated supply chain attack of SolarWinds Orion software.
The Russian state-sponsored attackers were able to deploy malware to U.S. Government agencies, as well as numerous public and private sector organizations in multiple countries, by breaching SolarWinds. The hackers stole the SolarWinds digital certificate which opened the door for deploying malware across multiple entities.
The full extent of the attack is still being uncovered. If you have SolarWinds Orion software it is imperative that you investigate to determine if your organization has been attacked. The SafeBreach updated playbook methods will help you assess the possibility of the attack and help you improve your security defenses to prevent attacks that leverage SUNBURST and SUPERNOVA malware campaigns.
Listen to the details of the attack from SafeBreach Labs’ Tomer Bar:
13 newly developed playbook methods:
Infiltration
- #5689 – Transfer of SUNBURST malware over HTTP/S (Infiltration)
- #5691 – Email SUNBURST malware as a ZIP attachment (Infiltration)
- #5692 – Communication with SUNBURST using HTTP (Infiltration)
- #5693 – Communication with a real malicious SUNBURST server using HTTP/S (Infiltration)
- #5738 – Transfer of SUPERNOVA_Webshell malware over HTTP/S (Infiltration)
- #5740 – Email SUPERNOVA_Webshell malware as a ZIP attachment (Infiltration)
Host Level
- #5687 – Write SUNBURST malware to disk (Host-Level)
- #5736 – Write SUPERNOVA_Webshell malware to disk (Host-Level)
Lateral Movement
- #5688 – Transfer of SUNBURST malware over HTTP/S (Lateral Movement)
- #5690 – Email SUNBURST malware as a ZIP attachment (Lateral Movement)
- #5735 – Resolution of domains connected to SUNBURST malware
- #5737 – Transfer of SUPERNOVA_Webshell malware over HTTP/S (Lateral Movement)
- #5739 – Email SUPERNOVA_Webshell malware as a ZIP attachment (Lateral Movement)
8 existing playbook methods:
Exfiltration
- #109 – Covert data asset exfiltration using HTTP/s GET
- #110 – Covert data asset exfiltration using HTTP/s POST
- #106 – Covert data exfiltration using HTTP (GET)
Host Level
- #1693 – Collect Windows system data using CMD
- #2244 – Windows Management Instrumentation Event Subscription
- #2293 – Create and Start a Service
- #2188 – Extract Process List using Windows Commands
- #2194 – Extract Credentials from the Registry using System Commands
What you should do now
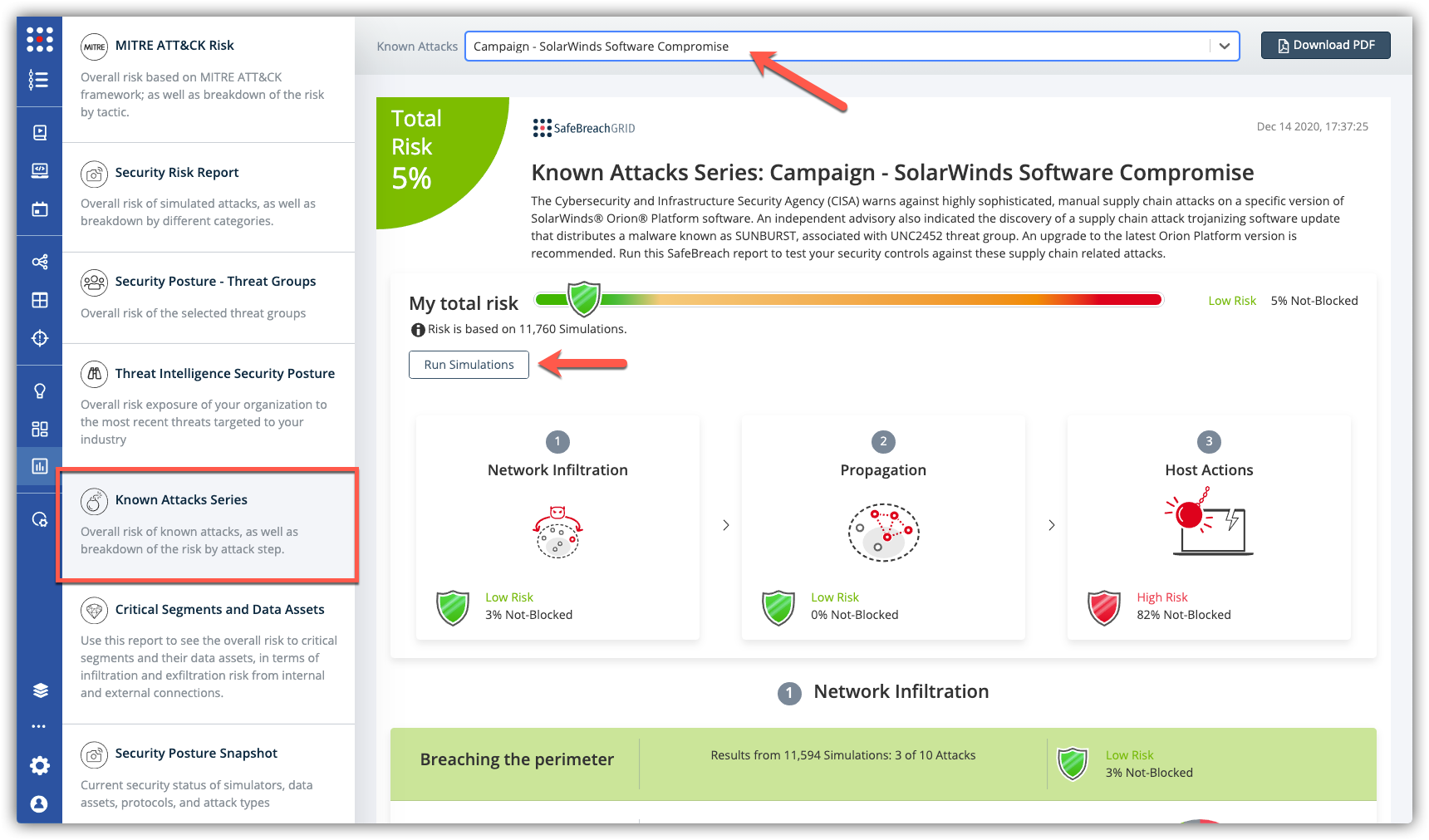
The new attack methods for US-CERT Active Exploitation of SolarWinds Software are already in the SafeBreach Hacker’s Playbook and ready to be run across your simulators. The Known Attack Series report is being updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the Campaign – SolarWinds Software Compromise and select Run Simulations which will run all the attack methods.