SafeBreach Labs has updated the Hacker’s Playbook™ with new attack methods for malware samples described in US-CERT Exploitation of Pulse Connect Secure Vulnerabilities which addresses multiple vulnerabilities successfully leveraged by two threat groups – APT5, a Chinese state-sponsored threat group and UNC2717, a yet unattributed group. Vulnerabilities in certain Ivanti Pulse Connect Secure products allow a remote authenticated threat actor to execute binary code via a server message block (SMB) or Pulse Secure Collaboration, granting them access to targets including several US and global government agencies, critical infrastructure entities, and other private sector organizations. Once access is established, the threat actors place webshells on the Pulse Connect Secure appliance to enable a wide variety of functions including authentication bypass, multi-factor authentication bypass, password logging, and persistence through patching.
Due to the prevalence of remote work during the COVID-19 pandemic, VPNs have been one of the most common attack vectors used in the last two years worldwide by attackers and threat groups. Whether your organization is using Ivanti Pulse Connect Secure products or other VPN solutions, we encourage you to use this opportunity to conduct an in-depth analysis of this attack surface.
Listen to the details of the attack from SafeBreach Labs’ Tomer Bar:
4 newly developed playbook methods related to AA21-110A
- #6128 – Remote exploitation of Pulse VPN vulnerability CVE-2021-22893
- #6129 – Communication with aa21-110a_HARDPULSE using HTTP
- #6130 – Remote exploitation of Pulse VPN vulnerability CVE-2020-8260
- #6131 – Communication with PULSECHECK using HTTP
25 existing playbook methods related to AA21-110A
- Exfiltration
- #110 – Covert data asset exfiltration using HTTP/s POST
- #106 – Covert data exfiltration using HTTP (GET)
- #107 – Covert data asset exfiltration using HTTP POST
- Host-Level
- #2445 – Indicator Removal on Host (Windows)
- #2355 – Modify the user’s PATH variable
- #1011 – Collect Linux System Information using bash Commands
- #1695 – Collect Linux System Data using Bash Scripts
- #2356 – Service Registry Permissions Weakness
- #2170 – Create Account (Windows)
- #2248 – Masquerading
- #1644 – Write to disk of SettingContent-ms hidden in docx
- #2357 – File System Permissions Weakness
- #2244 – Windows Management Instrumentation Event Subscription
- #2249 – Indicator Removal on Host (Linux)
- #2188 – Extract Process List using Windows Commands
- #1269 – Creating Windows schedule task (schtasks)
- #1357 – Create Cron scheduled task
- #2293 – Create and Start a Service
- #2189 – Account Manipulation
- #2171 – Create Account (Linux)
- #2164 – Scheduled Task
- #1693 – Collect Windows system data using CMD
- Infiltration
- #4271 – Remote exploitation of Pulse VPN vulnerability CVE-2019-11510
- #1642 – Obfuscation of SettingContent-ms inside docx over HTTP/S’
- Lateral Movement
- #214 – Scheduled task creation over SMB
What you should do now
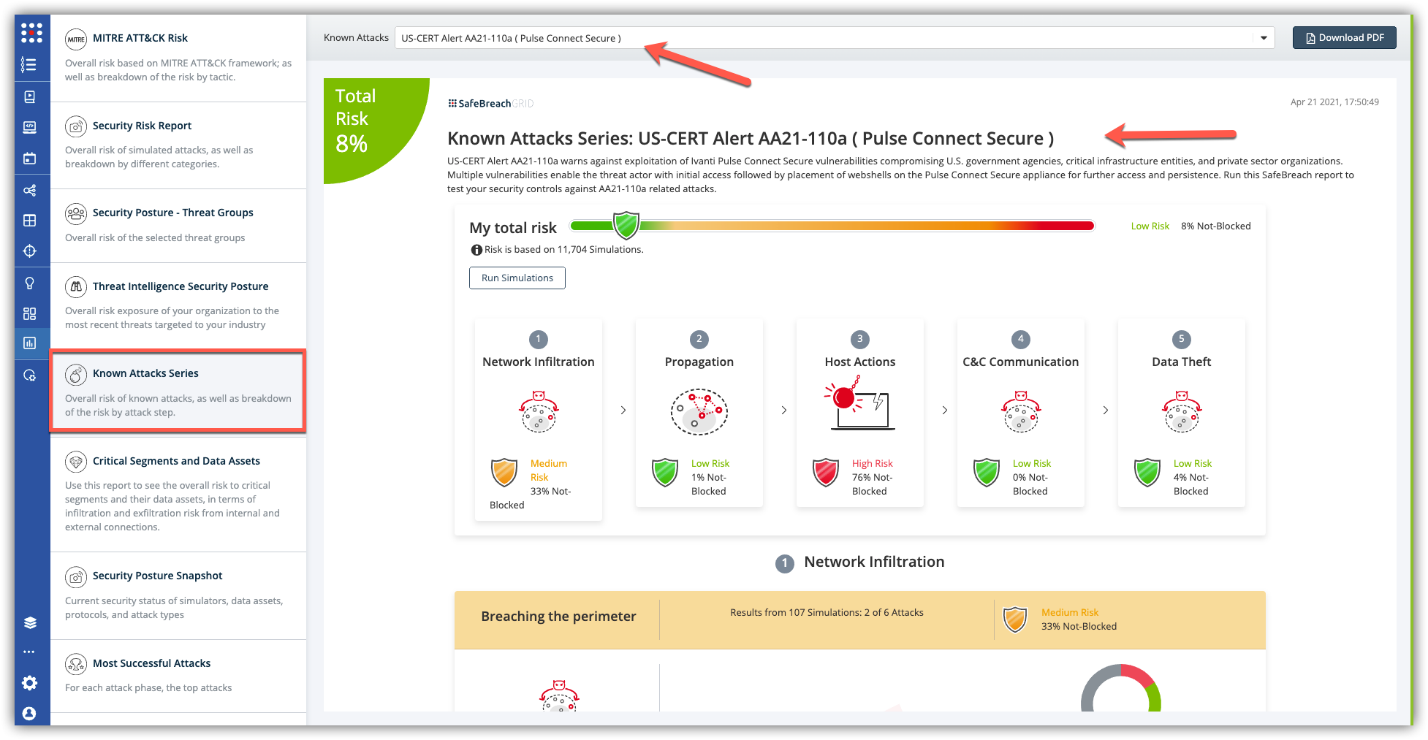
The new attack methods for US-CERT AA21-110A are already in the SafeBreach Hacker’s playbook and ready to be run across your simulators. The Known Attack Series report is updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT AA21-110A (Pulse Connect Secure) report and select Run Simulations which will run all attack methods.