
Today, due to customer demand and the rise of new products and services, financial service organizations (FSIs) of all sizes must be able to access a wide variety of digital resources quickly and efficiently. This places an enormous strain on their IT and security teams to ensure their cybersecurity defenses are impenetrable.
The financial industry continues to be targeted by cyberattacks. According to the 2022 VansonBourne report nearly all (94%) of surveyed FSIs faced some type of attack over the past 12 months.
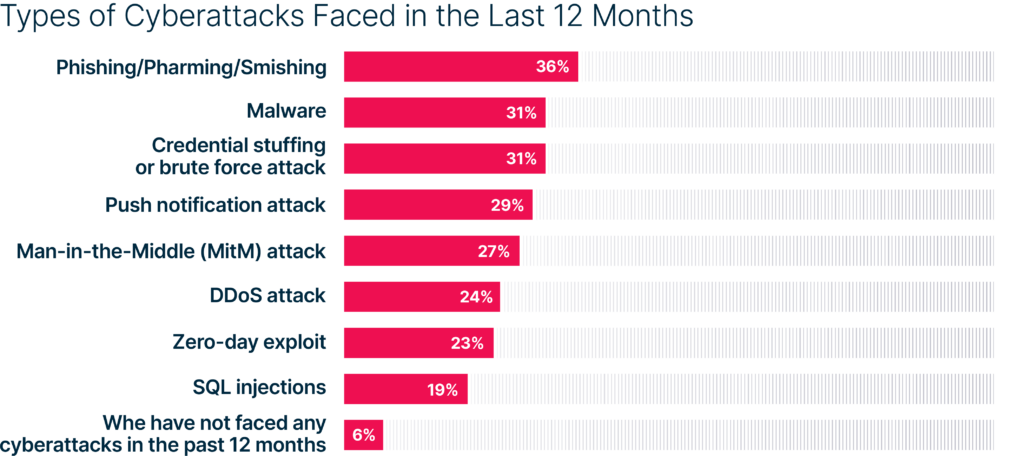
Insights from 500 IT security financial decision-makers (U.S., U.K., France. and Germany)
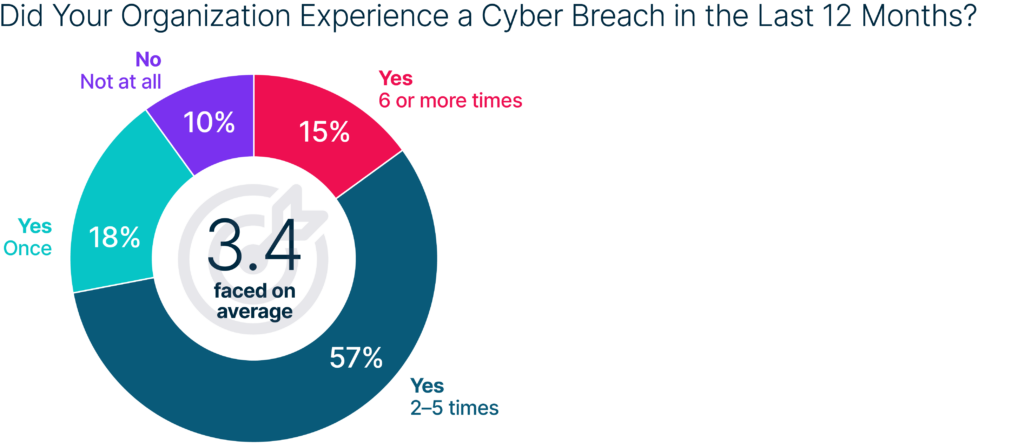
Moreover, of the financial companies that reported an attack, 90% acknowledge that they fell victim to a cyber breach over the past 12 months. Look at this another way, 85% of all FSIs experienced a known breach. Moreover, nearly three-quarters (72%) who experienced a breach did so multiple times—at an average of 3.4 breaches. This not only demonstrates the prevalence of attacks, but it also exposes the vulnerability of current security measures in place and the damage caused by reluctance or inability to make tangible changes.
Research by IBM X-Force also shows that 70% of the attacks on financial firms targeted banks, 16% targeted insurance companies, and 14% targeted other financial institutions in 2021. BCG’s report shows that financial services are 300 times more likely to be the victim of a cyberattack than other organizations.
Organizations in the finance sector are highly concerned about cyber threats. According to a survey conducted by the Conference of State Bank Supervisors (CSBS) in September 2021, cybersecurity risk was rated “extremely important” by more than 80% of bankers as the top internal risk—that’s more than double any other category of operational risk and more than the 60% reported the previous year.
Emerging Cyber Threats
To understand the severity of the cyber-related risk to the financial industry, you must first look at the global financial system and its unprecedented digital transformation accelerated by the pandemic. In addition, central banks around the globe are assessing the use of digital currencies and modernizing payment systems. In this time of transformation, cybersecurity is more crucial than ever.
Second, bad actors are taking advantage of this digital transformation and pose a great threat to the global financial system, financial stability, and confidence in the integrity of the financial industry.
Finance institutions are 300 times more likely than other sectors to be targeted by cyberattacks, and the costs of those attackers are higher than any other sector.
A Peek Behind the Curtain
Cyber criminals have become more daring and dangerous attacks are worrisome. Incidents that corrupt the integrity of financial data, records, algorithms, and transactions leave IT and security teams with few technical solutions to tackle such attacks. In addition, states and state-sponsored attackers have stolen billions of dollars from at least 38 countries in the past five years.
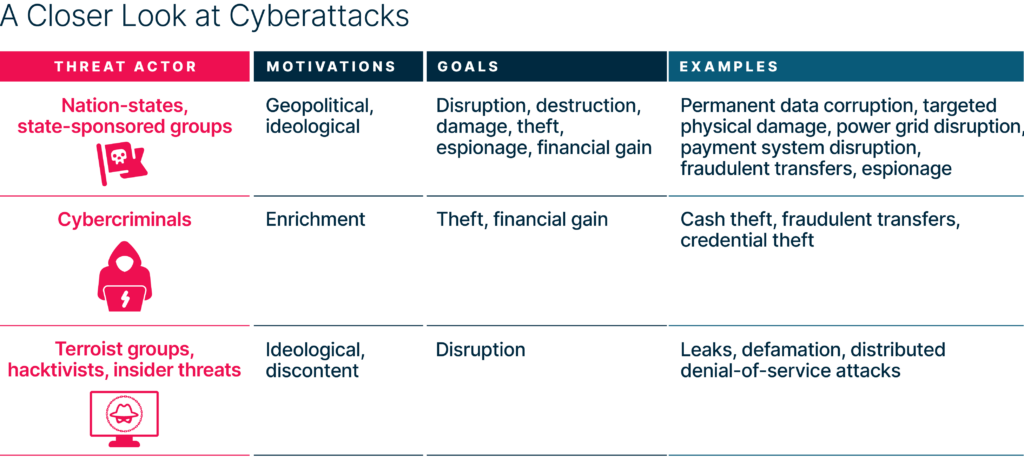
And let’s not forget this is truly a global problem. News headlines tend to focus only on high-income countries and high-profile attacks. But more attention needs to be paid to the growing number of attacks on softer targets in low- and lower-middle-income countries. These countries are pushing for greater financial inclusion, leading many to leapfrog to digital financial services like mobile payment systems. The October 2020 hack of Uganda’s largest mobile money networks, MTN and Airtel, for example, resulted in a major four-day disruption of service transactions and plunged the country’s telecoms and banking sectors into crisis.
2022 Most Prevalent Attack Types
1. Ransomware & Data Exfiltration
According to a recent report, the finance industry experienced a 1,318% increase in ransomware attacks in 2021. That’s hard to get your head around. Ransomware is not going away and continues to be the most widespread worldwide threat.
At the outset, ransomware prevented organizations from accessing their data by encrypting files in the infected systems and holding the decryption key for ransom to extort money. Victims pay a ransom fee to recover access to their encrypted data in this single extortion method.
The finance industry experienced a 1,318% increase in ransomware attacks in 2021.
Today, FSIs are much savvier and have adapted to file encryption attacks by improving their data backup procedures. So, there is no reason to pay the ransom if you can recover your data from backups. However, ransomware gangs responded by exfiltrating critical data before encrypting it and then threatening to leak or disclose it if the ransom is not paid.
According to the State of Ransomware 2020 report by Sophos, remediation costs double when a ransom is paid. And the threat of leaking this data on the dark web, and the resulting reputational damage, has forced many FSIs to comply with ransom demands, despite FBI recommendations not to do so.
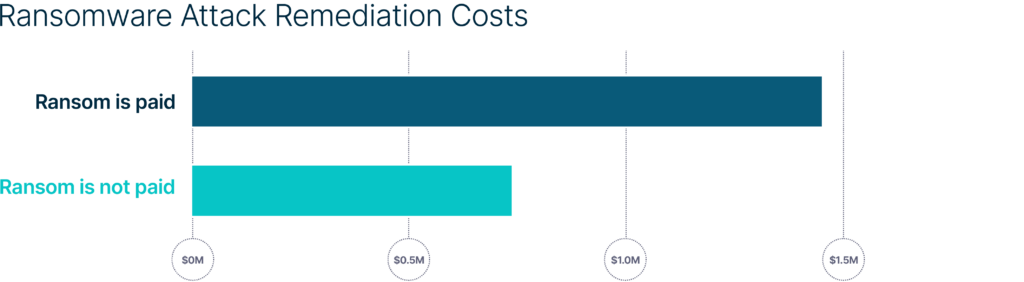
In addition to encryption and data exfiltration, cybercriminals utilize other extortion methods, such as threatening to disrupt operations or sell sensitive data to competitors. As such, in November 2021, the FBI warned that ransomware actors are very likely to target and leverage victim organizations through significant financial events such as mergers and acquisitions. Prior to launching an attack, ransomware attackers conduct research into publicly available information, such as the stock valuation of a victim and material nonpublic information. If victims do not pay the ransom on time, ransomware attackers threaten to expose this information, potentially giving rise to investor backlash publicly.
As a result of these new extortion methods, ransomware attacks have a massive impact on financial firms, including business downtime, revenue loss, reputation loss, data loss, and public release of sensitive information.
2. Phishing
Attackers used the phishing technique to gain initial access in 46% of attacks against the financial services sector in 2021.
Like ransomware-as-a-services (RaaS) for running a ransomware attack campaign, attackers are now paying an operator to run complete phishing campaigns or phishing-as-a-service (PhaaS) through a hosted solution. These campaigns may include spoofing, website hosting, phishing mail template creation, distribution of phishing emails, credential parsing, and overall orchestration.
46% of attacks against the financial services sector in 2021 used phishing techniques to gain initial access.
Cybercrime via phishing has become very accessible with ready-made PhaaS kits. An example of a PhaaS operation, BulletProofLink (also referred to as BulletProftLink or Anthrax) is utilized by a variety of threat groups in one-off or monthly subscription-based business models, providing a consistent revenue stream for its operators.
And phishing has become much more sophisticated, with research noting a 300% rise in phishing attacks targeting Chase Bank between May and August 2021, and similar campaigns targeting global financial giants Citibank and CapitalOne. The XBALTI phishing kits were designed to look and behave exactly like the Chase banking portal. According to the researchers, the phishing kits were very sophisticated and aimed to gather information other than email addresses and passwords, such as banking and credit card information, social security numbers, and home addresses.
3. Web Application Attacks
According to the State of the Internet/Security report for 2021, 6.3 billion web attacks worldwide were observed in 2020; 12% of them are in the financial services industry alone. The most common type of web attack targeting financial services was local file inclusion (52%), followed by SQL injection (33%) and cross-site scripting (9%).
Morgan Stanley, the American investment banking giant, announced a data breach on July 2, 2021, attributed to zero-day assaults on Accellion’s legacy file transfer appliance (FTA). The primary attack vector is a SQL injection vulnerability (CVE-2021-27101), which enables an unauthenticated user to execute remote commands on vulnerable Accellion FTA servers. By hacking into the Accellion FTA server of a third-party provider, Guidehous, attackers collected personal information belonging to Morgan Stanley’s clients.
6.3 billion web attacks worldwide were observed in 2020.
4. Vulnerability Exploitation Attacks
These types of attacks enable threat actors to gain access to target networks to perform additional operations with higher privileges. According to the IBM Security X-Force 2022 report, threat actors used vulnerability exploitation attacks as the initial access vector in one of three attacks against financial institutions in 2021.
Attackers will gain initial access to victim networks by exploiting multiple known vulnerabilities or gain access to target networks via zero-day vulnerabilities in high-profile attacks such as Kaseya MSP supply-chain ransomware attack campaign and Microsoft Exchange Server incidents (CVE-2021-26857, CVE-2021-26858, CVE-2021-27065, and CVE-2021-26855).
1 in 3 attacks against financial institutions used vulnerability exploitation attacks in 2021.
5. Nation-State/State-Sponsored Attacks & APTs
Three significant risks today to the financial industry include nation-state attacks carried out by foreign governments, state-sponsored attacks implemented by affiliated cybercriminal gangs, and advance persistent threats (APTs) launched by sophisticated ATP groups. The banking/financial sector experienced 37% of the most APT detections that occurred in Q3 2021.
These very organized groups collaborate and share attack tactics, techniques, procedures (TTPs), tools, and resources to compromise FSIs, resulting in an increase in cyberattacks. Nation-state attacks reflect current geopolitical tensions, resulting in a renewed increase in attacks against governments, militaries, and the business sector, according to the Navigating Cyber 2022 report of the Financial Services Information Sharing and Analysis Center (FS-ISAC).
The banking/financial sector experienced 37% of the most APT detections that occurred in Q3 2021.
6. Insider Threats
Financial services is the industry leader, experiencing 16% of insider threats. Many security incidents are attributed to insider threats posed by current or recently departed employees and unknowing staff errors. According to a 2020 study, insider attacks are becoming more prevalent, more difficult to detect, and more harmful.
Insiders can cause major disruption to operations and critical data loss, whether unintentional or purposeful. For example, a New York credit union suffered a data breach caused by an insider in September 2021. After being fired, a former employee was able to go into corporate systems and erase 21.3 GB of company data and files within forty minutes. IBM’s Cost of a Data Breach Report 2021 shows that malicious insiders are the third costliest attack type. According to the same report, a breach caused by a malicious insider took 23 days to identify and 75 days to contain.
Financial services is the industry leader experiencing 16% of insider threats.
How SafeBreach Can Help
Continuous security validation powered by SafeBreach’s breach and attack simulation (BAS) platform offers a safe-by-design approach to reach designated assets to validate control efficacy against known attacker TTPs and indicators of compromise (IOCs) for select high- and low-value assets. Simulated attacks in a planned IT architecture validate the efficacy of security controls to identify and prioritize the most critical threats and uncover all possible attack paths to improve detection efficacy.
SafeBreach provides validation of the controls in your entire security ecosystem with unmatched visibility into how your ecosystem will respond at each stage of the defense process.
Endpoint Protection Is a Critical Component of Data Exfiltration Prevention
Because data exfiltration focuses on retrieving, transferring, and copying data on endpoints, and endpoints have historically provided one of the easiest access points for hackers, financial institutions must look to comprehensive security control validation solutions to identify endpoint weaknesses to defend against threats such as data exfiltration.
Data exfiltration seems like an easily preventable process, but the advanced attacks that occur regularly in the modern threat landscape require an approach to validate controls across the full kill chain and entire security ecosystem that adequately identifies weaknesses at every endpoint that exists within your network.
Security Control Validation of Endpoints
The best way to assess the efficacy of your endpoint security is by using MITRE ATT&CK simulation techniques used by threat actors to validate security controls at the designated endpoint. The SafeBreach platform can perform the following to validate security control of your endpoints:
- Finance-Specific Top 16 MITRE TTPs Attack Scenarios: SafeBreach offers finance-specific attack scenarios that leverage the MITRE ATT&CK framework, including the Top 16 MITRE TTPs as well as full MITRE coverage scenarios of real-world attacks that have occurred in the financial industry.
- Lateral Movement Simulations: Run lateral movement attack simulations in your network to identify techniques attackers use to gain access and escalate privileges for execution. Using ATT&CK simulations from threat groups to test endpoint security against these attack vectors allows you to see how well your platform performs against actual attacks, providing insights to optimize and mitigate security weaknesses.
Data Exfiltration Is Preventable
Data exfiltration often relies on social engineering techniques to gain access to protected company networks. However, it’s quite difficult to adequately block the download of these malicious applications without restricting access to applications your users need. To effectively compromise an endpoint, however, malware must be able to communicate externally with a command or control server or endpoint DLP controls to receive instructions or exfiltrate data. Identifying weaknesses in these security controls to assess the ability of an attacker to exfiltrate data out of your organization can help prevent this unauthorized communication and is a viable method for preventing data exfiltration.
Security Control Validation of Network Perimeter
Network borders have multiple layers and looking at the policy for network border filtering is important to permit the flow of legitimate traffic, while closing security gaps in the network perimeter without impacting business operations. When it comes to network traffic, identifying and blocking potential cyberattacks is crucial. The SafeBreach platform can help validate network security controls at your network border in the following ways:
- Validate All Layers of Network: Continuous validation of the efficacy of your security controls at all layers of your network independently and at each stage of the defense process. Validating security controls and identifying gaps with firewall rules will allow you to address these weaknesses proactively and mitigate the associated risk.
Web Filtering Is Important
Web filtering provides your organization with the ability to control the locations where users are browsing, which is important for malware protection, data security, regulatory compliance, and policy enforcement.
- Malware Protection: Phishing and other malicious sites can be used to deliver malware and other dangerous content to users’ computers. Web filtering makes it possible for an organization to block access to websites that pose a threat to your company and user security.
- Data Security: C2 communications by compromised user machines used to receive commands, download further malware, and possibly exfiltrate data.
- Regulatory Compliance: Companies are responsible for complying with a growing number of data protection regulations, which mandate that they protect certain types of data from unauthorized access. With web filtering, an organization can manage access to sites that are likely to try to steal protected data and ones that may be used intentionally or unintentionally to leak data (such as social media or personal cloud storage).
- Policy Enforcement: Web filtering enables an organization to enforce corporate policies for web usage. All types of web filtering can be used to block inappropriate use of corporate resources, such as visiting sites containing explicit content.
SafeBreach Web Filtering
The SafeBreach platform can protect users in your organization from browsing malicious sites and from communicating with command and control (C2) sites. By running attack simulations specific to finance we can validate some of the top security controls related to web filtering, which may include:
- C2 communication
- Web shell downloads
- Malware downloads
Email Breach-and-Attack Simulations
The SafeBreach platform can help protect your organization from phishing, spearphishing, malicious attachments, and other email attacks that could lead to costly data breaches or ransomware attacks. Red-team phishing simulations can help your security team understand how well-prepared your organization is to handle phishing attack attempts, giving them tangible experience and preparing the team with proper response techniques should some type of social engineering attack occur.
SafeBreach will validate your email security controls at the first layer to reduce the impact of a social engineering attack and the chances of an unsuspecting user opening a phishing email, for example, that may compromise the company.
SafeBreach Studio Attack Scenarios
The SafeBreach platform is comprised of over 25,000 individual attack methods, and scenarios are tagged by industry and attack type using the Top 16 TTP MITRE ATT&CK workflows. The SafeBreach platform offers the ability to:
- Choose from 6,000 phishing and spearphishing attack scenarios based on malware or malicious links delivered via email and common use cases such as fake promotions (especially since the pandemic), or password resets due to unauthorized login attempts.
- Control what attacks to run and when, including associated parameters, sequencing steps, and the simulators desired to execute your scenarios.
- Analyze your individual red and blue team test results of attacks and gain an overview of the simulation details, parameters, and goals all mapped to MITRE ATT&CK, an individual threat group, industry, or NIST control mapping.
What Should IT & Security Leaders Do?
- Understand your overall company risk
The first step is to ensure that IT and security teams understand their overall company risk and can identify security gaps to ask for a defendable budget that will improve security operations.
- Be aware of the most significant threat vectors
Next, understand the most significant threat vectors and prioritize your cybersecurity objectives to create a relevant cybersecurity plan that can prove your security program’s effectiveness.
- Include security tools that can integrate into your ecosystem
Ensure your cybersecurity defense includes tools that easily integrate into your ecosystem and can continuously measure the effectiveness of your overall IT security infrastructure against real-world cyberattacks to stay ahead of threat actors.
- Adopt a security control validation approach
Improve defenses by adopting a security control validation approach that can validate the efficacy of your security controls by identifying weaknesses and prioritizing mitigation or determining whether current controls can successfully defend against a cyberattack.
- Identifying environmental drift
Use automated and ongoing monitoring to identify and address environmental drift introduced by misconfigurations, accidental restores of vulnerable system versions, or controls that fall offline.
- Flexible reporting relevant to stakeholders
This leads to the need for a flexible reporting mechanism that integrates easily into your existing framework to provide important data and dashboards and actionable intelligence that can be communicated across different stakeholders and in executive reports.
Financial Change, Attackers’ Gain
FSIs often have some of the most comprehensive and mature security controls in all the industry sectors, and it goes without saying that the rewards are high for criminals who seek to gain direct access to your network and valued customer data. Therefore, the importance of effective tools that can easily integrate into the ecosystem across the control validation process is key to the success of a security program.
As FSIs update their IT and security technology and programs, managing the growing attack surface will continue to become more complex and dispersed, both on-premises and in the cloud. New business initiatives and digital transformation to help drive new revenue will pose new threats as well. The SafeBreach solution is a direct response to a more integrated approach to validating security controls and prioritizing potential threats, while continually refining your security posture.
