Introduction
According to the latest research by the Enterprise Security Group (ESG), 70% of organizations own more than ten security tools to manage their security posture. Despite this investment, security hygiene and posture management remains one of the least mature areas in cybersecurity. The increasing complexity of the modern security stack opens potential new opportunities for an attacker to breach the organization. But what really is security posture and why does it matter to security teams?
What is Security Posture?
NIST defines security posture in this way: “The security status of an enterprise’s networks, information, and systems based on information security resources (e.g., people, hardware, software, policies) and capabilities in place to manage the defense of the enterprise and to react as the situation changes.”
In simpler terms, security posture refers to an organization’s overall cybersecurity strength and how well it can detect, prevent, and respond to the ever-changing threat landscape. To have a strong security posture, security teams must be able to:
- Understand their attack surface, with effective, real-time visibility into security gaps and vulnerabilities.
- Track the current status and effectiveness of security controls that have been deployed.
- Prevent, detect, and remediate threats.
Effectively Defending Against the Known and the Unknown
An organization’s security posture is based on the status of all of an enterprise’s technology assets, including networks, information, and systems, which can be in the cloud or on-premises. Consequently, teams must be able to not only quantify what tools they own but also determine whether they are functioning as intended.
According to the IBM Cost of a Data Breach Report 2021, the average cost of a data breach in the United States was $9.05 million and it took an average of 287 days to identify and contain a security breach. In addition, while enterprises continue their rapid adoption of cloud services, many are unprepared for the risks. For example, the latest Verizon Data Breach Investigation Report found that, in 2020, 73% of cybersecurity incidents involved cloud assets. These statistics highlight how critical it is for security teams to dynamically adapt their organization’s security posture to rapidly changing attack surfaces, so they can eliminate the security gaps and vulnerabilities that can be easily exploited by a highly motivated attacker.
Why Does Security Posture Matter?
Security posture helps teams understand their level of readiness against threats. Today’s organizations own dozens of security controls, which are intended to protect assets against a range of threats. However, each of these security controls is susceptible to a wide range of attacks, presenting the determined threat actor with a practically unlimited number of ways to breach an organization.
This means that security teams face the arduous task of ensuring that each security control is configured correctly to detect threats and that it stays that way in the future. However, security configurations can often drift over time. Threat actors understand this and exploit it. By making minor modifications to an existing threat vector, they can easily bypass existing controls and gain access to an organization’s networks and assets. Given this dynamic attack surface, it is highly complex and difficult for security teams to ensure that existing security controls can effectively detect, prevent, or respond to attacks.
It is critical to understand that an organization’s security posture cannot be static. It must constantly change in response to the ever-evolving threat landscape.
How Can Breach and Attack Simulation Help?
According to Gartner “Breach and attack simulation (BAS) tools are emerging to provide continuous defensive posture assessments….”. Gartner also highlights that BAS tools enable security teams to:
- Test the efficacy of security controls and help prioritize future investments.
- Find likely paths that attackers can take to navigate through the organization and gain access to highly sensitive assets.
- Improve the maturity of defenses by testing the effectiveness of current detection capabilities and incident response playbooks.
This means that when security leaders include BAS tools as a part of their regular security assessments, they can help their teams identify gaps in their security posture more effectively and prioritize security initiatives more efficiently. BAS tools can speed up the assessment of new applications and critical infrastructure, using attack techniques that are likely to be used in the real world.
The SafeBreach BAS Platform
The SafeBreach BAS platform continuously executes advanced attacks against an organization’s security and cloud controls and does so in a safe and controlled manner. This enables security teams to test the efficacy of their controls and establish a baseline security posture. Gaps identified can be remediated to ensure that future attacks can be effectively detected, prevented, or remediated. SafeBreach provides continuous defensive posture assessments. Compared to point assessments like penetration testing, which tend to be carried out on an annual basis, this continuous approach offers significant improvements in visibility.
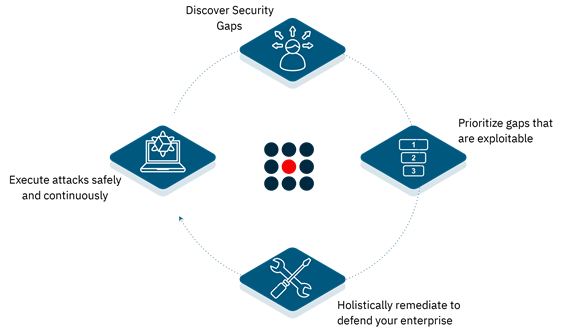
The SafeBreach platform empowers and optimizes security response by:
- Continuously validating the efficacy of cloud and on-premises security controls.
- Testing an organization’s security posture against emerging and known threats, discovering gaps before adversaries.
- Automating and prioritizing remediation efforts to help efficiently mitigate risk.
- Measuring and reporting on business risk, enabling security leaders to intelligently prioritize and justify security programs and projects.
Optimize and Evolve Organizational Security Posture with SafeBreach
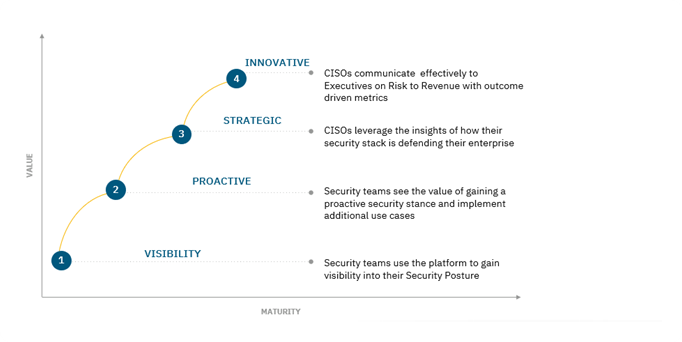
Your organization’s security and business risk priorities evolve over time. Your security posture must adapt and evolve accordingly. SafeBreach understands this and offers an adaptable and scalable BAS solution to meet your changing needs. SafeBreach can therefore be the optimal partner for your security team as it evolves your organization’s security posture.
Conclusion
It is critical to remember that the importance of being prepared for breaches grows with the constant evolutionary nature of costly cybersecurity attacks. The increasing complexity of the modern security stack only compounds this challenge as vulnerabilities in each security control open a potential new opportunity for an attacker to breach the organization. Please join Jon Oltsik, Senior Principal Analyst and Fellow at ESG, and Yotam Ben Ezra, VP of Products at SafeBreach on Thursday, Dec. 16th at 9am PT/ 12pm ET to understand how Breach and Attack Simulation tools can help organizations tackle the challenges of security posture management. Register here.