SafeBreach Labs has updated the Hacker’s Playbook™ with new attack methods for malware samples described in US-CERT North Korean Advanced Persistent Threat Focus: Kimsuky, which addresses a global intelligence-gathering mission in South Korea, Japan, and the United States. Kimsuky uses social engineering tactics, spearphishing, and watering hole attacks to exfiltrate foreign policy, national security issues related to the Korean peninsula, nuclear policy, and sanctions.
26 newly developed playbook methods related to AA20-301A:
Infiltration
- #5550 – Transfer of Kimsuky_loader malware over HTTP/S
- #5552 – Email Kimsuky_loader malware as a ZIP attachment
- #5555 – Transfer of Kimsukysecondstage malware over HTTP/S
- #5557 – Email Kimsukysecondstage malware as a ZIP attachment
- #5562 – Transfer of GREACE malware over HTTP/S
- #5564 – Email GREACE malware as a ZIP attachment
- #5565 – Communication with Kimsuky malware using HTTP
- #5566 – Communication with a real malicious Kimsuky malware server using HTTP/S
- #5571 – Communication with aa20-301a using HTTP
- #5575 – Transfer of Win7Elevate malware over HTTP/S
- #5577 – Email Win7Elevate malware as a ZIP attachment
Lateral movement
- #5549 – Transfer of Kimsuky_loader malware over HTTP/S
- #5551 – Email Kimsuky_loader malware as a ZIP attachment
- #5554 – Transfer of Kimsukysecondstage malware over HTTP/S
- #5556 – Email Kimsukysecondstage malware as a ZIP attachment
- #5561 – Transfer of GREACE malware over HTTP/S
- #5563 – Email GREACE malware as a ZIP attachment
- #5574 – Transfer of Win7Elevate malware over HTTP/S
- #5576 – Email Win7Elevate malware as a ZIP attachment
Host level
- #5547 – Pre-execution phase of Kimsuky_loader malware
- #5548 – Write Kimsuky_loader malware to disk
- #5553 – Write Kimsukysecondstage malware to disk
- #5558 – Pre-execution phase of GREACE malware
- #5560 – Write GREACE malware to disk
- #5572 – Pre-execution phase of Win7Elevate malware
- #5573 – Write Win7Elevate malware to disk
24 existing playbook methods related to AA20-301A:
Infiltration
- #3830 – Extract credentials using PwDump through PowerShell
- #2420 – Transfer of babyshark malware over HTTP/S
- #2422 – Email babyshark malware as a ZIP attachment
- #5532 – Email malicious Microsoft Word macro as a ZIP attachment
Lateral movement
- #1220 – Fileless Mimikatz injection using PowerShell
- #2273 – Pass the Hash over SMB using Mimikatz
- #2419 – Transfer of babyshark malware over HTTP/S
- #2421 – Email babyshark malware as a ZIP attachment
- #161 – Malicious EXE File Inside a Macro of a Word File
Host level
- #2173 – Execute Code using Mshta
- #2245 – Indicator Removal on Host (Windows)
- #1901 – Capture network packets using WinPcap (Windows)
- #2208 – Extract Credentials using Get-GPPPassword (PowerShell)
- #2221 – Modify the Registry Run keys
- #2222 – Discover Remote Systems using PowerShell
- #2389 – Add a Firewall Rule using netsh.exe
- #794 – Extract Login Information using MimiKatz
- #3820 – Extract credentials stored in a browser using WebBrowserPassView
- #2267 – Add an exclusion to Windows Defender using PowerShell
- #2191 – Change Default File Association
- #2418 – Write babyshark malware to disk
- #3118 – Pre-execution phase of babyshark malware
- #2612 – Write to disk DOCX with Remote Template
- #2293 – Create and Start a Service
What you should do now
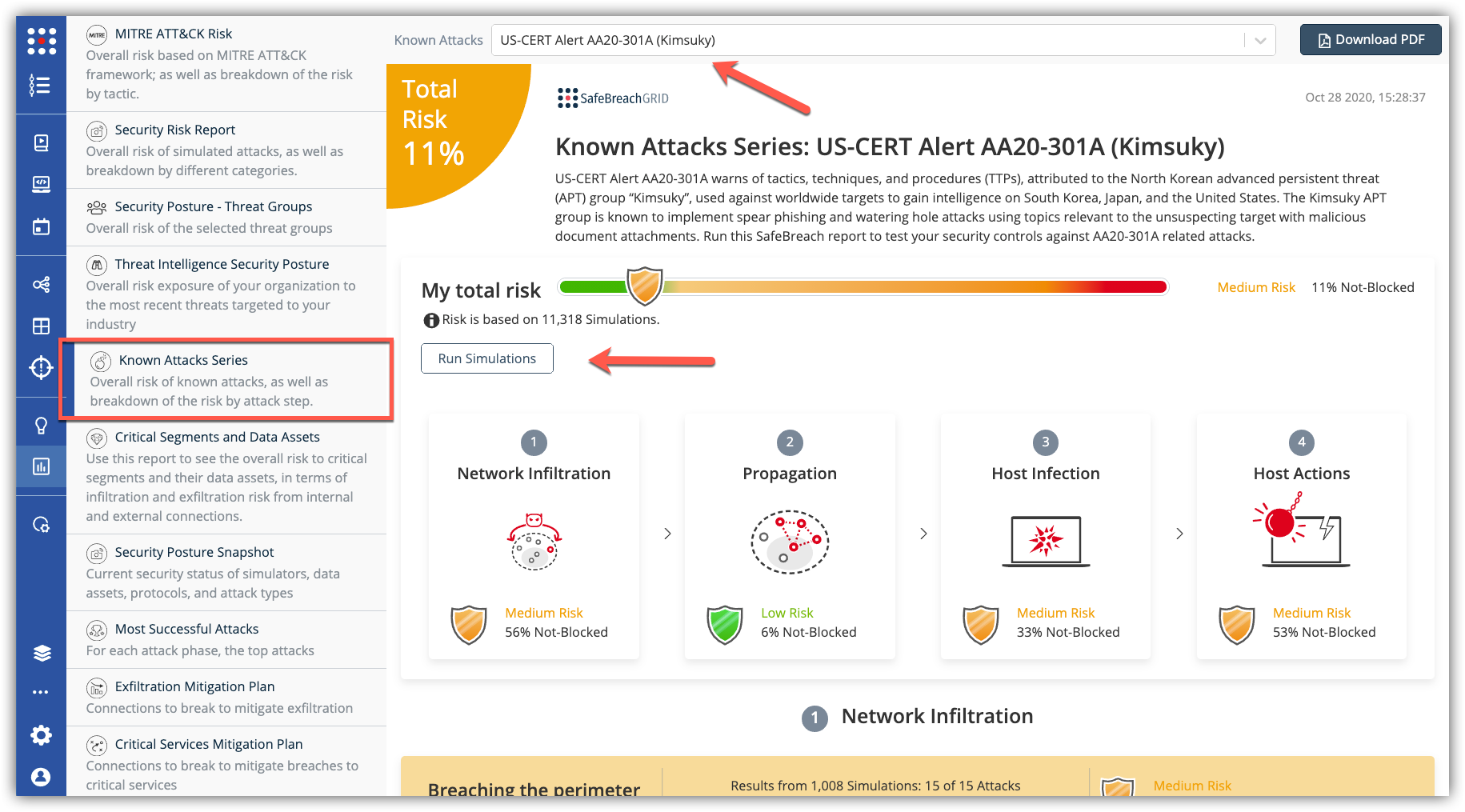
The new attack methods for US-CERT AA20-301A are already in the SafeBreach Hacker’s Playbook and ready to be run across your simulators. The Known Attack Series report is being updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT Alert AA20-301A (Kimsuky) report and select Run Simulations which will run all the attack methods.