SafeBreach Labs has updated the Hacker’s Playbook™ with new attack methods for malware samples described in US-CERT AppleJeus: Analysis of North Korea’s Cryptocurrency Malware which is a spear phishing campaign that masquerades as a cryptocurrency trading company. As users install the trading company software it appears to be a legitimate application but in the background, another process called updater is installed and is designed to collect and exfiltrate data and bitcoins from the victim.
The North Korean threat groups are notorious for devastating attacks, including the infamous WannaCry attack in 2017 from Lazarus Group, the attack against Sony Pictures in 2014 in retaliation for ‘The Interview’ film by Guardians of Peace, and the Bangladesh Bank Heist in 2016 where \$81 million was stolen via the SWIFT network, among others. SafeBreach Labs has been tracking their progress and updating the SafeBreach Hacker’s Playbook throughout the years.
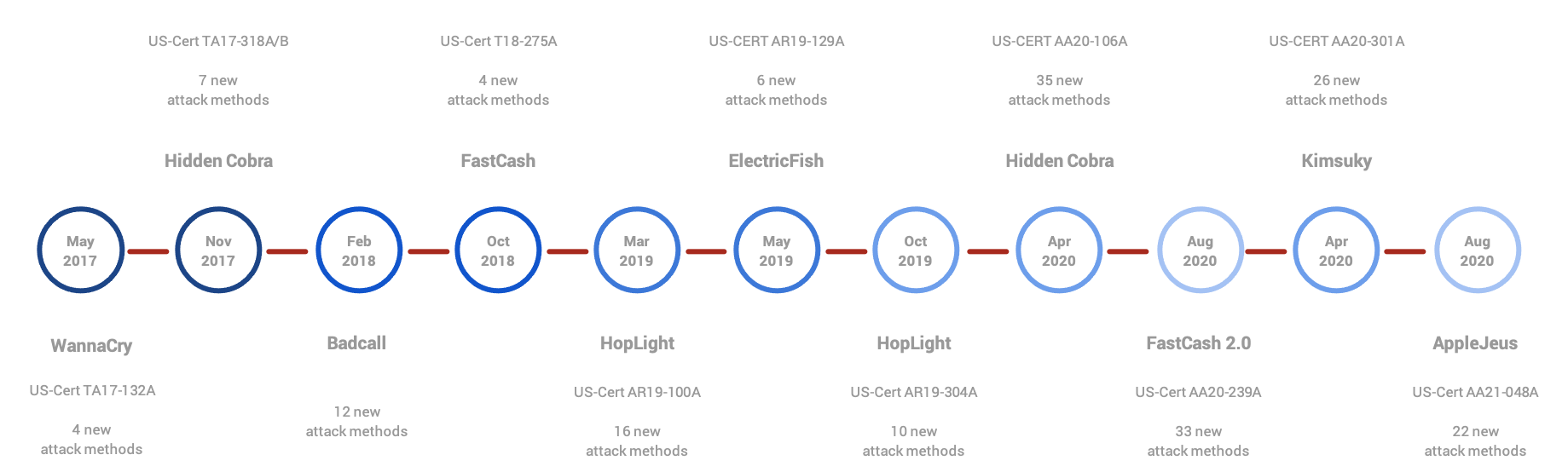
Here is an overview SafeBreach Hacker’s Playbook timeline based on US-Cert Alert updates only:
22 newly developed playbook methods related to AA21-048A:
#5948 – Write KupayWallet malware to disk (Host-Level)
#5949 – Transfer of KupayWallet malware over HTTP/S (Lateral Movement)
#5950 – Transfer of KupayWallet malware over HTTP/S (Infiltration)
#5951 – Email KupayWallet malware as a ZIP attachment (Lateral Movement)
#5952 – Email KupayWallet malware as a ZIP attachment (Infiltration)
#5954 – Write AppleJeus malware to disk (Host-Level)
#5955 – Transfer of AppleJeus malware over HTTP/S (Lateral Movement)
#5956 – Transfer of AppleJeus malware over HTTP/S (Infiltration)
#5957 – Email AppleJeus malware as a ZIP attachment (Lateral Movement)
#5958 – Email AppleJeus malware as a ZIP attachment (Infiltration)
#5959 – Write AppleJeus_osx malware to disk
#5960 – Transfer of AppleJeus_osx malware over HTTP/S (Lateral Movement)
#5961 – Transfer of AppleJeus_osx malware over HTTP/S (Infiltration)
#5962 – Email AppleJeus_osx malware as a ZIP attachment (Lateral Movement)
#5963 – Email AppleJeus_osx malware as a ZIP attachment (Infiltration)
#5945 – Communication with AppleJeus using HTTP (Infiltration)
#5965 – Write KupayWallet_osx malware to disk (Host-Level)
#5966 – Transfer of KupayWallet_osx malware over HTTP/S (Lateral Movement)
#5967 – Transfer of KupayWallet_osx malware over HTTP/S (Infiltration)
#5968 – Email KupayWallet_osx malware as a ZIP attachment (Lateral Movement)
#5969 – Email KupayWallet_osx malware as a ZIP attachment (Infiltration)
#5971 – Communication with a real malicious AppleJeus server using HTTP/S (Infiltration)
30 existing playbook methods related to AA21-048A:
Infiltration
#109 – Covert data asset exfiltration using HTTP/s GET
#110 – Covert data asset exfiltration using HTTP/s POST
#106 – Covert data exfiltration using HTTP (GET)
#107 – Covert data asset exfiltration using HTTP POST
#125 – Covert data asset exfiltration over TLS
Host Level
#2339 – Execute AppleScript’,
#2164 – Scheduled Task’,
#1693 – Collect Windows system data using CMD’,
#1694 – Collect macOS system data using bash’,
#2293 – Create and Start a Service’,
#2124 – Hide a file – Windows’,
#2347 – Add a Launch Daemon’,
#2346 – Add a Login Item using AppleScript’,
#1269 – Creating Windows schedule task (schtasks)’,
#1699 – Edit the File Configuration so the File is Hidden (macOS)’]
Lateral Movement
#2173 – Execute Code using Mshta
#2245 – Indicator Removal on Host (Windows)
#1901 – Capture network packets using WinPcap (Windows)
#2208 – Extract Credentials using Get-GPPPassword (PowerShell)
#2221 – Modify the Registry Run keys
#2222 – Discover Remote Systems using PowerShell
#2389 – Add a Firewall Rule using netsh.exe
#794 – Extract Login Information using MimiKatz
#3820 – Extract credentials stored in a browser using WebBrowserPassView
#2267 – Add an exclusion to Windows Defender using PowerShell
#2191 – Change Default File Association
#2418 – Write babyshark malware to disk
#3118 – Pre-execution phase of babyshark malware
#2612 – Write to disk DOCX with Remote Template
#2293 – Create and Start a Service
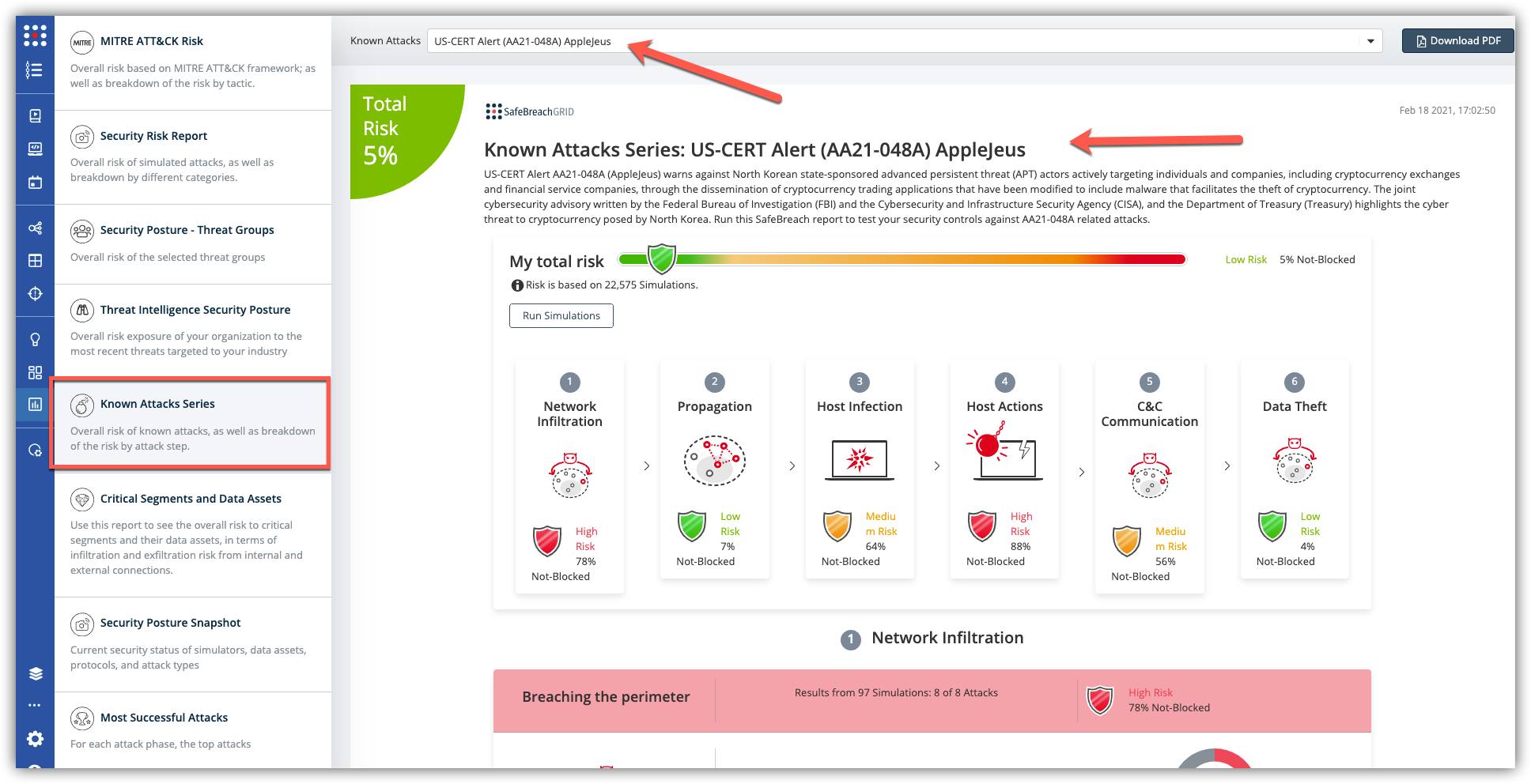
What you should do now
The new attack methods for US-CERT AA21-048A are already in the SafeBreach Hacker’s Playbook and ready to be run across your simulators. The Known Attack Series report is updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT Alert AA21-048A (AppleJeus) report and select Run Simulations which will run all the attack methods.