On February 24th, the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), the U.S. Cyber Command Cyber National Mission Force (CNMF), and the United Kingdom’s National Cyber Security Centre (NCSC-UK) issued an advisory that provided additional details about Iranian state-sponsored advanced persistent threat (APT) actor – MuddyWater conducting cyber espionage and other malicious cyber operations targeting a range of government and private-sector organizations across multiple verticals—including telecommunications, defense, local government, and oil and natural gas—in Asia, Africa, Europe, and North America (Note – this actor is also known as Earth Vetala, MERCURY, Static Kitten, Seedworm, and TEMP.Zagros). Details of the various tactics, techniques, and procedures (TTPs) are described in US-CERT Alert (AA22-055A) – Iranian Government-Sponsored Actors Conduct Cyber Operations Against Global Government and Commercial Networks.
The MuddyWater threat group is a subordinate element within the Iranian Ministry of Intelligence and Security (MOIS) and has conducted broad cyber campaigns to support MOIS objectives since approximately 2018. This group’s activities are primarily focused to provide stolen data and accesses to the Iranian government. According to the information available, this group is known to employ the following techniques to achieve its objectives:
- Use of Spearphishing – MuddyWater attempts to coax their targeted victim into downloading ZIP files, containing either an Excel file with a malicious macro that communicates with the actor’s C2 server or a PDF file that drops a malicious file to the victim’s network.
- Use of Side loaders and Obfuscation – MuddyWater actors also use techniques such as side-loading DLLs to trick legitimate programs into running malware and obfuscating PowerShell scripts to hide C2 functions.
- Use of Proprietary tools – the group has created several proprietary malware sets—including PowGoop, Small Sieve, Canopy/Starwhale, Mori, and POWERSTATS—for loading malware, backdoor access, persistence, and exfiltration.
- Use of Exploits – the group is known to exploit unpatched vulnerabilities including CVE-2020-1472 and CVE-2020-0688
NOTE – Several of the identified TTPs have been previously used by the MuddyWater and are already available in the SafeBreach Hacker’s Playbook™ and have now also been mapped to US-CERT Alert (AA22-055A). New TTPs have now been added as attacks to the playbook. We encourage you to test your preparedness against MuddyWater by running the attacks listed below.
7 newly developed playbook methods related to US-CERT AA22-055A (MuddyWater)
- #6919 Write a hidden powershell script to disk with a different extension
- #6920 Write MuddyWater (860f5c) malware to disk’,
- #6921 Transfer of MuddyWater (860f5c) malware over HTTP/S’,
- #6922 Transfer of MuddyWater (860f5c) malware over HTTP/S’,
- #6923 Email MuddyWater (860f5c) malware as a ZIP attachment’
- #6924 Email MuddyWater (860f5c) malware as a ZIP attachment’,
- #6925 Communication with a malicious Telegram chat bot using HTTPS
30 previously used attack methods already present in the Hacker’s Playbook:
- Host-Level Attacks
- #2221 Modify the Registry Run keys’
- #2222 Discover Remote Systems using PowerShell’
- #6127 Extract LSASS memory dump using PowerShell and ‘Rundll32’
- #2192 Collect Data from Local Shared Drives using System ‘Commands’
- #2611 Extract system date using PowerShell’
- #3830 Extract credentials using PwDump through PowerShell’
- #6809) Execute DLL by signed executable (igfxtray.exe)’
- #2266 Collect Google Chrome Bookmarks’
- #1693 Collect Windows system data using CMD’
- #6910 RDP Tunneling’
- #6411) Screen Capture (Windows)’
- #6246) Exploit ZeroLogon (CVE-2020-1472) (Windows)’
- #4966 Write MuddyWater (3769ea) malware to disk’
- #2344 Write a macro hidden in a dotm file to disk’
- #2153 Rundll32
- #2221 Modify the Registry Run keys’
- #3819 Windows Credentials Collection using LaZagne’
- #2608) PowerShell – Run Script File (csc build no powershell)’
- #1269) Creating Windows schedule task (schtasks)’
- #5308 Signed Binary Proxy Execution using CMSTP’
- #2173 Execute Code using Mshta’
- Infiltration Attacks
- #1290 Transfer of MS office exploit using CVE-2017-0199 over HTTP’
- #2218 Obfuscation of arbitrary commands using DDE (Dynamic ‘Data Exchange) inside RTF over HTTP/S’
- #4968 Transfer of MuddyWater (3769ea) malware over HTTP/S’
- #4970 Email MuddyWater (3769ea) malware as a ZIP attachment
- Lateral Movement Attacks
- #1220 Inject Mimikatz using PowerShell to Extract Credentials’
- #4967 Transfer of MuddyWater (3769ea) malware over HTTP/S’
- #4969 Email MuddyWater (3769ea) malware as a ZIP attachment’
- #5487 Exploit CVE-2020-1472 ZeroLogon
- #6579 Remote Code Execution via DCOM
What you should do now
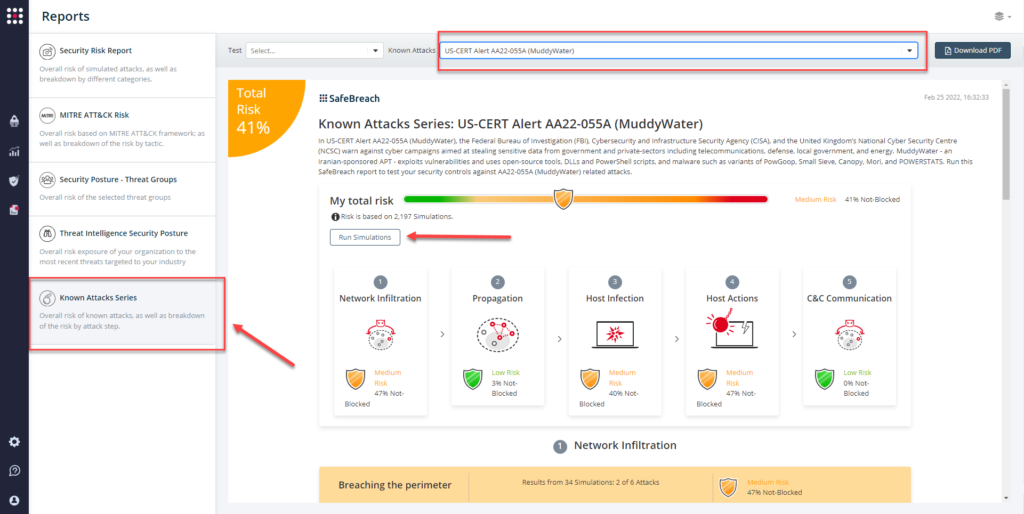
Attack methods related to US-CERT AA22-055A (MuddyWater) are already in the SafeBreach Hacker’s playbook and ready to run across your simulators. The Known Attack Series report has been also updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT AA22-055A (MuddyWater) report and select Run Simulations which will run all attack methods.
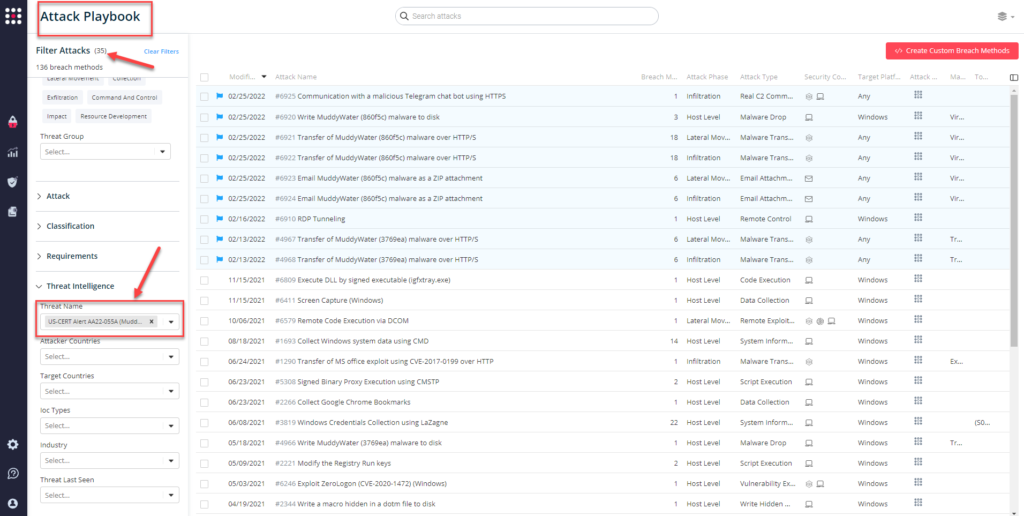
You can also select all the attacks related to US-CERT AA22-055A (MuddyWater), by going to the SafeBreach Playbook and filtering by Threat Name – US-CERT AA22-055A (MuddyWater).
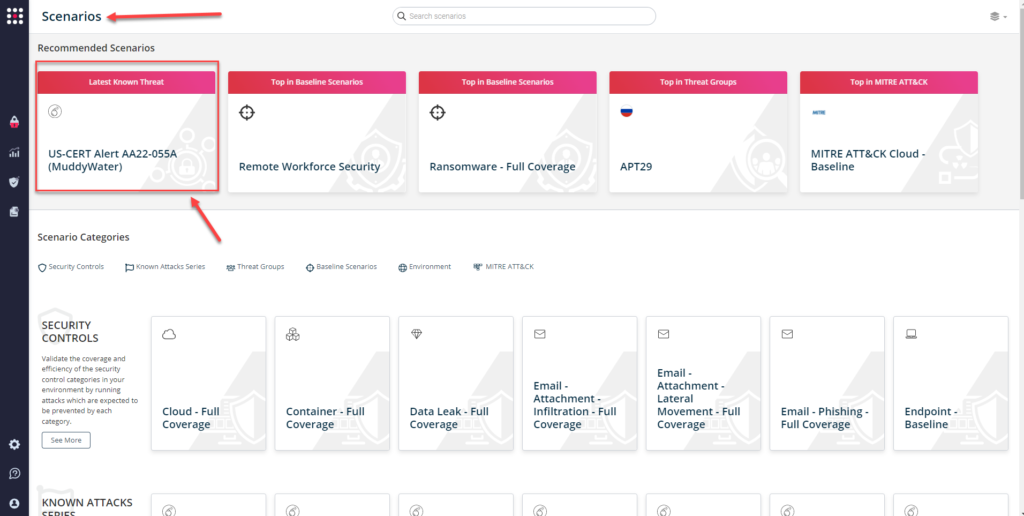
or you can go to the “SafeBreach Scenarios” page and choose the USCERT Alert AA22-055A (MuddyWater) scenario from the list of available scenarios.
NOTE – FBI, CISA, CNMF, NCSC-UK, and the National Security Agency (NSA) recommend organizations apply the mitigations in this advisory and review the following resources for additional information.:
- Malware Analysis Report – MAR-10369127-1.v1: MuddyWater
- IOCs – AA22-052A.stix and MAR-10369127-1.v1.stix
- CISA’s webpage – Iran Cyber Threat Overview and Advisories
- NCSC-UK MAR – Small Sieve
- CNMF’s press release – Iranian intel cyber suite of malware uses open-source tools