
In our first post on using BAS in an operational technology (OT) environment, we provided an overview of a typical converged IT/OT network, the trends that were driving increased cyber risk for industrial asset owners, and a high-level discussion of how BAS can help provide better visibility and protection across the converged environment. In this update we’ll discuss the benefits BAS delivers in these use cases, and we’ll get into the details of where and how BAS fits into a combined IT/OT architecture using the Purdue model.
What is the Purdue Model?
The Purdue model is generally accepted as the standard for building an industrial control system (ICS) network architecture in a way that supports OT security, separating the layers of the network to maintain a hierarchical flow of data between them, and as such, reflects the baseline architecture requirements for many industrial control system frameworks such as API 1164, ISA/IEC 62443, and NIST 800-82.
Purdue illustrates how the typical elements of an ICS architecture interconnect, dividing them into six zones that contain business systems (the IT network) and industrial control systems (the OT network). Implemented correctly, it helps establish an “air gap” between ICS/OT and IT systems, isolating them so an organization can enforce effective access controls without hindering business. This being said, Purdue is not a one-size-fits-all prescription for OT network architecture. As with any network, every environment is going to have its own unique assortment of devices at each layer.
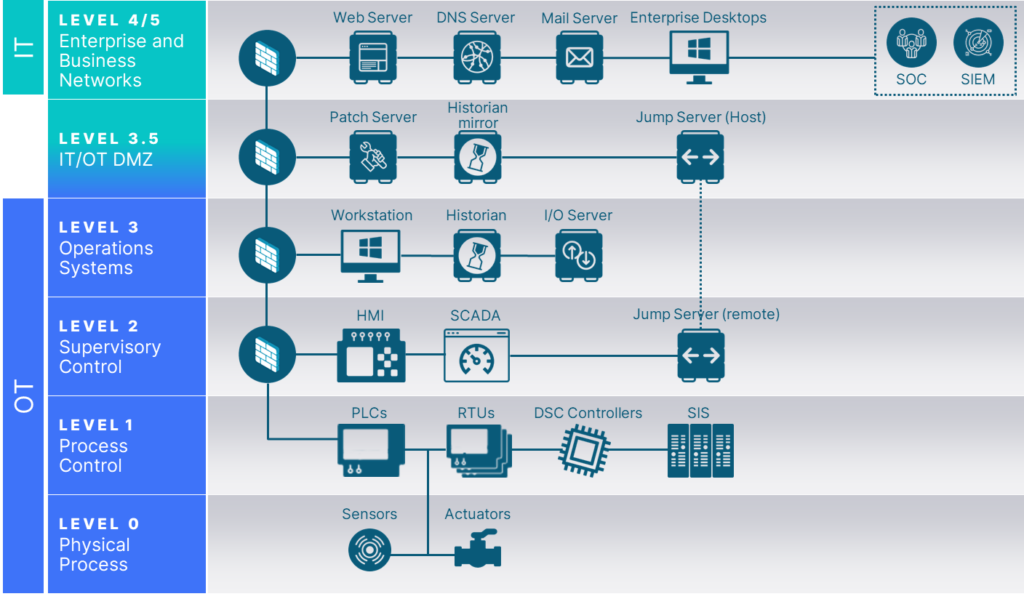
Figure 1: A basic Purdue model

The Levels of the Purdue Model
The Purdue model consists of six network levels, defined by the systems and technologies that reside in each. IT systems occupy the upper 2 levels, while OT systems occupy the lower 3 and a converged “demilitarized zone” resides between them. Let’s take a more detailed look at each:
Level 5/4: Enterprise and Business Networks
While separate in the traditional Purdue model, these two levels have been combined for simplicity in the basic model above, as together they make up the IT environment. Levels 4 and 5 are comprised of enterprise-wide services such as Active Directory, HR and document management systems, Customer Relationship Management (CRM) platforms, internal email, and the Security Operations Center (SOC). It also includes site-specific services such as Enterprise Resource Planning (ERP) which drive plant production schedules, material use, shipping, and inventory levels.
Devices in this level utilize standard IT hardware, cloud platforms, and off-the-shelf operating systems such as Windows and Linux.
Level 3.5: IT/OT Demilitarized Zone (DMZ)
Whereas the DMZ located in IT networks is responsible for separating the corporate network from the Internet, the DMZ located in OT networks is responsible for isolating the industrial network from the corporate network. As demands for business data from the OT side have increased, and vice versa, administrators have had to connect these two levels through DMZs.
Devices at this layer are also running standard IT hardware, cloud, and software.
Level 3: Operations Systems
This level contains monitoring, supervisory, and operational support to manage production workflows on the shop floor. These include engineering and operations workstations running manufacturing operations management/manufacturing execution systems (MOMS/MES), data historians to store and analyze operational process data.
This layer is typically comprised of specialized operations management applications running on standard IT, cloud and mobile hardware and OSs.
Level 2: Supervisory Systems
Level 2 contains supervisory control and data acquisition (SCADA) systems which control groups of processes based on function, type, or risk. This level also includes the human-machine interface (HMI) devices through which an operator interacts with a controller.
This layer is typically comprised of industrialized IT or mobile hardware running specialized applications on standard cloud or OS platforms.
Level 1: Process Control Systems
The process control level contains devices such as distributed control systems (DCS), programmable logic controllers (PLC), and remote terminal units (RTU), and safety systems which monitor and send commands to the physical devices that execute operational processes.
Hardware and operating systems at this level is much more specialized. Proprietary hardware and software are typical, and these can be much more sensitive to software updates and change.
Level 0: Physical Process Devices
This bottom level includes all the devices that execute operational processes. These can include actuators, valves, and pumps, as well as IIoT devices such as cameras and motion sensors.
These devices are typically specialized for their specific task and are designed to accept instructions and send data using protocols such as Fieldbus.
Lack of OT Visibility is a Major Challenge for Security Teams
As we said in part one of our IT/OT blog series, most OT attacks begin by compromising the IT network. As such, it is critical in any OT security strategy to think of the IT and OT networks as two pieces of the same puzzle. They must address not only the vulnerabilities within the OT environment itself, but also the ways in which adversaries might compromise and traverse the IT network to gather information and gain lateral access to deeper OT control and safety systems.
Historically, operations teams have managed all OT assets due to concerns that software updates and configuration changes could put uptime and productivity at risk. So, security teams have had poor visibility into the OT environment and could not implement or update appropriate security controls.
As digital transformation has broken down IT-OT barriers, many industrial enterprises now have deeply integrated IT/OT environments and security teams now responsible for managing cyber risk across this extended network.
Let’s look now at how BAS can help security teams take a holistic view of assessing and validating security controls across this combined environment.
Increasing IT/OT Resilience with BAS
By simulating real-world attacks across your extended OT/IT network, a BAS platform can help validate security controls, identify vulnerable attack paths, and assist the Security and Ops teams with prioritizing and expediting remediation.
BAS platforms run attack scenarios without putting the OT network at risk of disruption by running simulations on clones of production systems. Simulations can be run as often as the user desires to identify drift and test against new attack methods. This is particularly relevant for OT asset owners, as a recent KPMG survey indicated 80% of industrial organizations only run an ICS security assessment once per year or less.
Going back to our Purdue model, below we’ve overlayed the architecture with locations the SafeBreach BAS platform would be deployed (all environments are different, so this is just a general example).
At levels 4/5, we’re deploying attack simulators out to typical enterprise desktops, laptops and servers. And the content server and external attacker are deployed in the SOC. At this level SafeBreach’s simulated attacks validate endpoint security controls, firewall detection rules, access-control list (ACL) rules, and verify events are being logged by the SIEM.
It’s important to note that the attack simulations at this level and every level below never put sensitive data or system integrity at risk. SafeBreach’s simulators only run attack simulations on and between simulators, never on the actual production system.
At the IT/OT DMZ (Level 3.5) the simulators are testing the firewall that regulates access to this level as well as validating the controls of the jump host (probably Linux-based) to ensure remote access to the lower OT levels is secure.
On levels 2 and 3, we are now solidly in the OT network. When thinking about OT network endpoints, many people think of the specialized assets such as PLC and RTU units that are directly controlling production processes. But even in the OT environment, the assets often at greatest risk of compromise are the engineering workstations and HMIs which are likely running either a Windows or Linux environment. It is critical to include these assets in the attack simulation as OT endpoints often have different security controls and configurations than endpoints on the IT network.
But this must be done in a way that does not put the availability of the workstation or HMI at risk. Installing a simulator on any production system wouldn’t be acceptable to the Operations team that are reliant on these systems. You’ll notice we’ve introduced workstation and HMI clones on levels 3 and 2 below and would run the simulator from the clone. So the production system is untouched, but we still get an accurate assessment of its security controls. In this example, we would attempt to go from jump server to HMI clone, or HMI clone to engineering workstation clone.
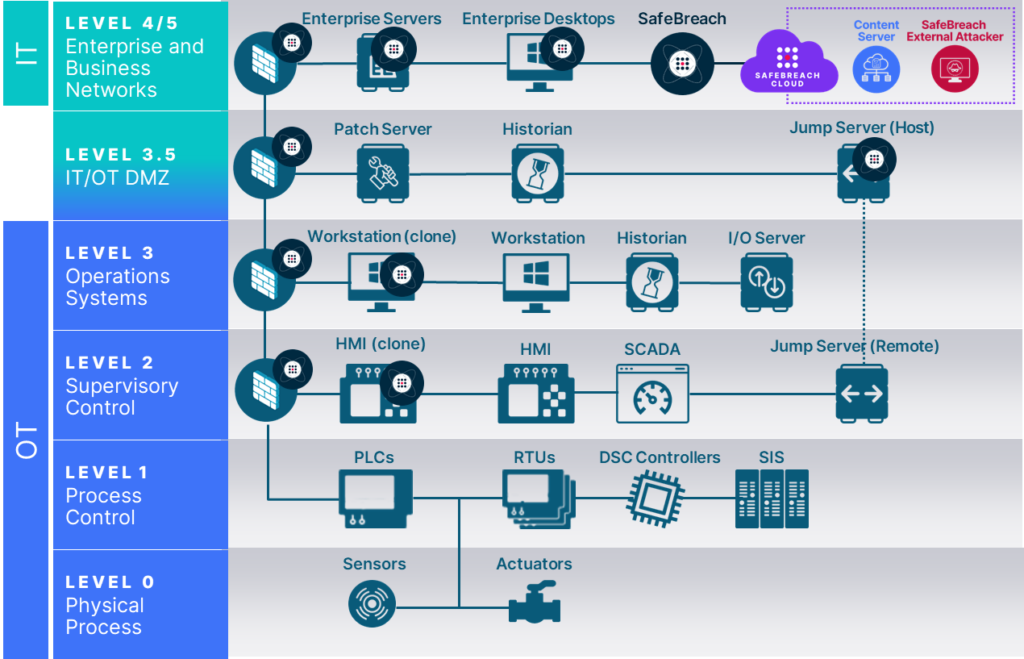
Unifying IT and OT Security with BAS
Breach and attack simulation is one of the most effective tools to assess and validate the security controls across a combined IT and OT environment.
Confidently Support OT Digital Transformation
Ensure your operations IT and security teams are working together, from the same information, to meet the demands for both productivity and protection as your operational environment transforms.
A Holistic Approach to Security Validation, Remediation and Reporting Across OT & IT
Create a consolidated view of your OT and IT security environment, to quickly identify and remediate weaknesses and vulnerable points of “spill-over” from one network to the other during an attack.
Increase Confidence with Stakeholders
Share automated reporting with key stakeholders to clearly communicate risk within the organization and ensure security investments are prioritized.
Secure the Entire Stack
Automate the execution of multi-stage attacks across the entire cloud stack, including end-user devices, networks, cloud services, and applications.
Manage Supply-Chain Security Risk
Before working with third-party suppliers, precisely assess their cybersecurity posture to understand the potential risks they may bring to your environment.
To learn more about breach and attack simulation and how SafeBreach can help provide better visibility and protection in your integrated IT/OT environment, we invite you to schedule a demo.
