Of organizations experienced an OT/IoT security event in the past 12 months
%
Of industrial organizations only run an OT security assessment once a year or less
%
Year-over-year increase in ransomware attacks against industrial organizations
%

Protect Production Uptime
Continuously validate your security controls to safeguard your production processes from costly downtime caused by cyberattacks.
Unify IT/OT Security Testing & Remediation
Create a consolidated view of your IT/OT environment to quickly identify and remediate points of “spill-over” from one network to the other during an attack.


Confidently Support OT Digital Transformation
Ensure your operations, IT, and security teams utilize the same information to meet demands for both productivity and protection as your operational environment transforms.
Control Supply Chain Security Exposure
Gain greater visibility into your supply chain ecosystem to identify potential attack paths, prioritize vulnerabilities, and take mitigating action quickly.

Rediscover your defenses with a powerful BAS platform.
Watch our demo.
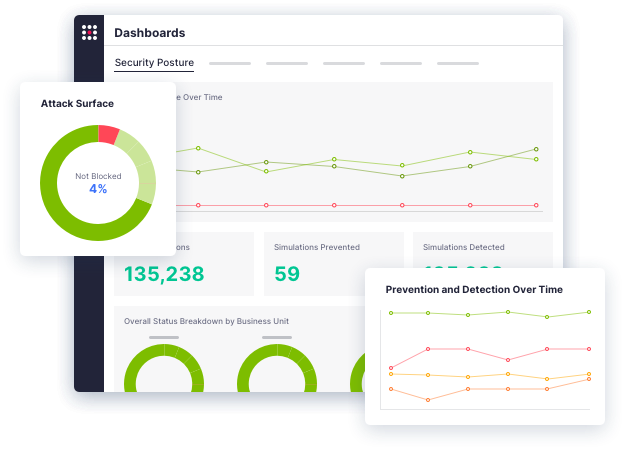
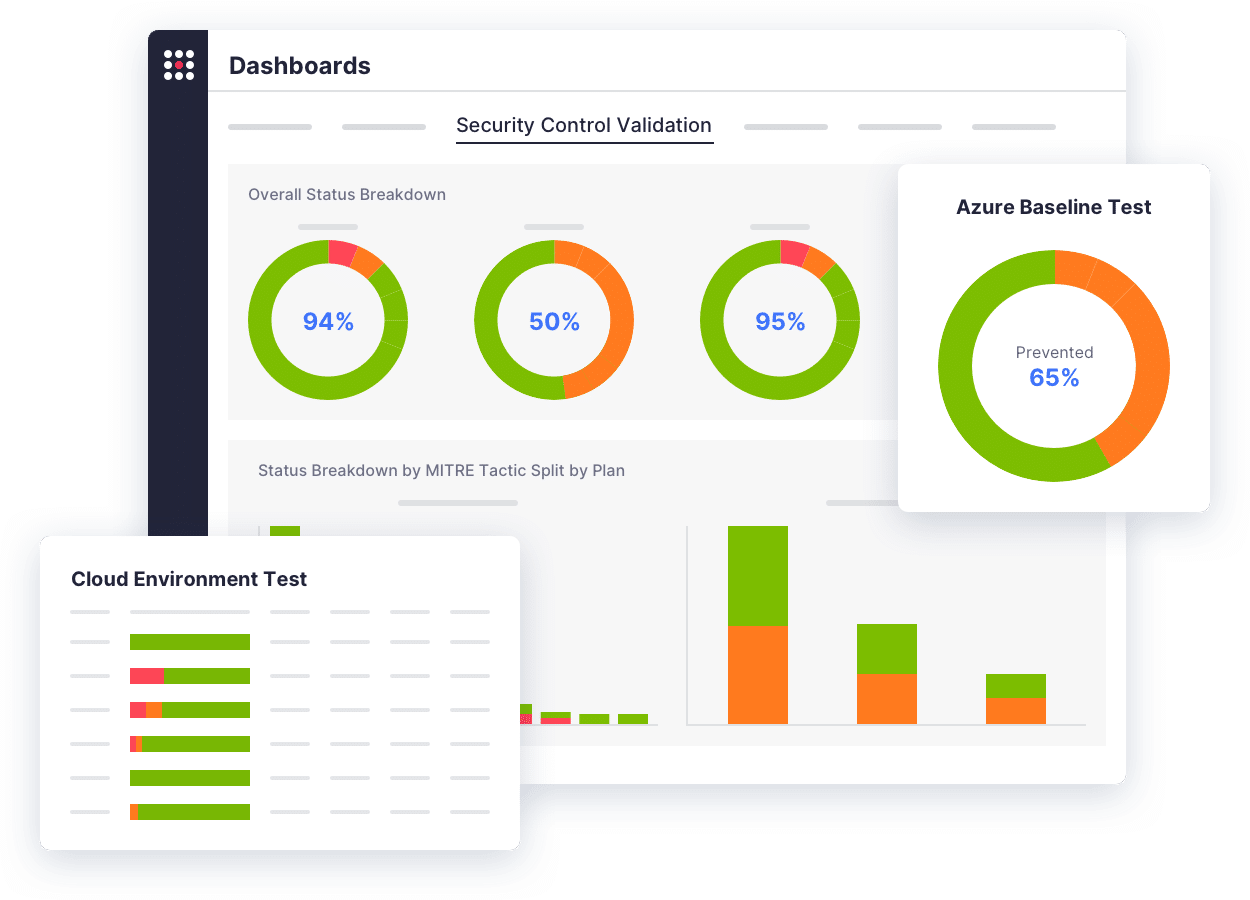
See how SafeBreach helps you justify your security investments, strengthen your defenses, and drive risk down with the industry’s most robust security control validation.
Watch our demo.
See how SafeBreach helps you justify your security investments, strengthen your defenses, and drive risk down with the industry’s most robust security control validation.
Validate security controls by running simulation techniques used by threat actors with hundreds of MITRE ATT&CK TTP attack scenarios and dozens of OT-specific attack techniques.
Proactively identify firewall rules gaps and mitigate the associated risk, while permitting legitimate inbound/outbound traffic.
Execute lateral movement, infiltration, and exfiltration simulations to test and secure segmentation and access control weaknesses between the IT and OT networks.