On May 11th, the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) released an advisory highlighting the active malicious exploitation of CVE-2023-27350 in PaperCut MF and PaperCut NG software by a threat actors including one known as the Bl00dy Ransomware Gang. The US-CERT Alert (AA23-131A) Malicious Actors Exploit CVE-2023-27350 in PaperCut MF and NG includes detailed information about this investigation (along with attacker TTPs and IOCs).
According to the advisory, attackers began exploiting the vulnerability in mid-April 2023, which allows an unauthenticated actor to execute malicious code remotely without credentials. The FBI even highlighted that in May 2023, a threat actor known as the Bl00dy Ransomware Gang attempted to exploit vulnerable PaperCut servers in the Education facilities sub-vertical.
Technical Details about CVE-2023-27350
This vulnerability allows a remote actor to bypass authentication and conduct remote code execution on the following affected installations of PaperCut:
- Version 8.0.0 to 19.2.7
- Version 20.0.0 to 20.1.6
- Version 21.0.0 to 21.2.10
- Version 22.0.0 to 22.0.8
PaperCut servers vulnerable to CVE-2023-27350 implement improper access controls in the SetupCompleted Java class, allowing malicious actors to bypass user authentication and access the server as an administrator. After accessing the server, actors can leverage existing PaperCut software features for remote code execution (RCE).
According to the advisory, there are currently two publicly known proofs of concept (others may be developed) for achieving RCE in vulnerable PaperCut software:
- Using the print scripting interface to execute shell commands.
- Using the User/Group Sync interface to execute a living-off-the-land-style attack.
Threat researchers also noted that a wide range of post-exploitation activity is possible following initial access and compromise.
Important Note for SafeBreach Customers – Coverage for AA23-131A (Exploit CVE-2023-27350 in PaperCut MF and NG)
As soon as details were made available, the SafeBreach Labs teams updated the Hacker’s Playbook with new attacks identified in this US-CERT alert immediately. SafeBreach customers can run/ re-run the attacks listed below to ensure their environments are protected against this vulnerability.
Existing Behavioral Attacks
- #7172 – Spawn a hidden Powershell process
- #7221 – Proxy execution – Msiexec
Newly Added IOC-Based Attacks
- #8814 – Write TrueBot downloader to disk
- #8815 – Transfer of TrueBot downloader over HTTP/S
- #8816 – Transfer of TrueBot downloader over HTTP/S
- #8817 – Email TrueBot downloader as a ZIP attachment
- #8818 – Email TrueBot downloader as a ZIP attachment
- #8819 – Write Cobalt Strike Beacon hacktool to disk
- #8820 – Transfer of Cobalt Strike Beacon hacktool over HTTP/S
- #8821 – Transfer of Cobalt Strike Beacon hacktool over HTTP/S
- #8822 – Email Cobalt Strike Beacon hacktool as a ZIP attachment
- #8823 – Email Cobalt Strike Beacon hacktool as a ZIP attachment
- #8824 – Communication with Bl00dy Gang Ransomware using HTTP
What You Should Do Now
The playbook has been updated with attacks that map to the IOCs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
From the Attack Playbook, select and filter attacks related to US-CERT Alert AA23-131A. Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
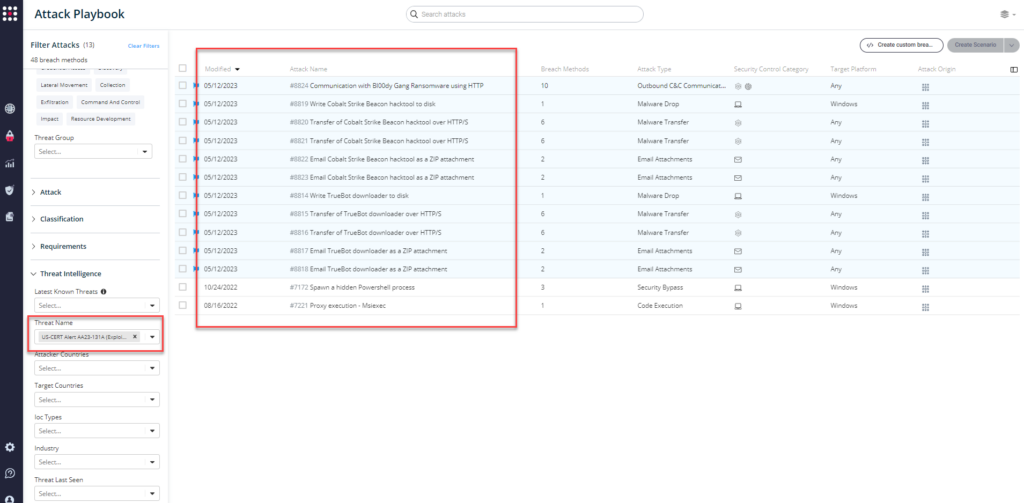
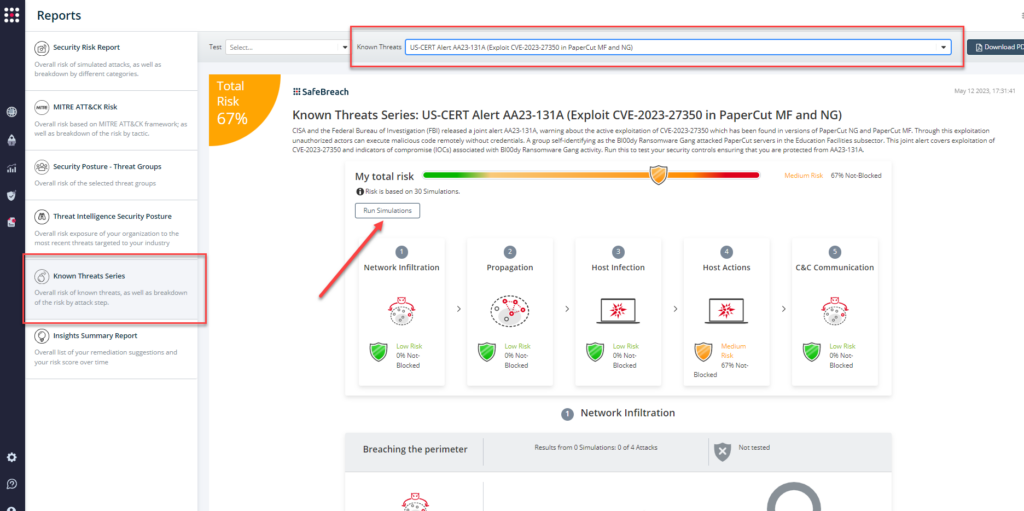
From the Known Attack Series report, select the AA23-131A (Exploit CVE-2023-27350 in PaperCut MF and NG) report and select Run Simulations which will run all attack methods.
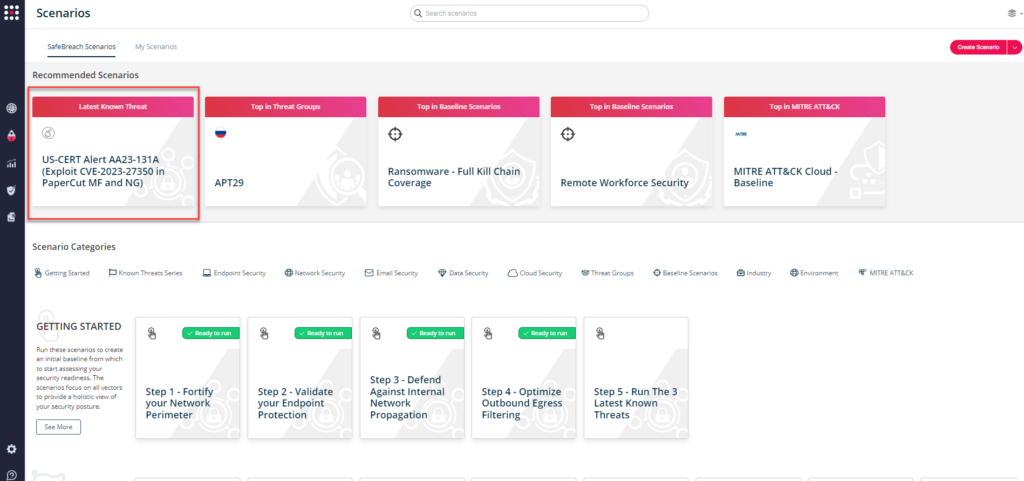
You can also go to “SafeBreach Scenarios” page and choose the AA23-131A (Exploit CVE-2023-27350 in PaperCut MF and NG) scenario from the list of available scenarios.
NOTE: CISA recommends continually validating your security program, at scale, in a production environment to ensure optimal performance against growing threat of advanced cyber threats. Additional recommendations include:
- Upgrade PaperCut to the latest version
- If unable to immediately patch, ensure vulnerable PaperCut servers are not accessible over the internet
- Follow best cybersecurity practices in your production and enterprise environments, including mandating phishing-resistant multifactor authentication (MFA) for all staff and for all services
- For detailed information about mitigations and incident response, please refer to the full advisory

