On May 16th, Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and Australian Cyber Security Centre (ACSC) released an advisory highlighting the various malicious indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) being leveraged by the BianLian ransomware group. These TTPs and IOCs were gathered after a detailed joint investigation by the FBI and ACSC and are listed in US-CERT Alert (AA23-136A) – #StopRansomware: BianLian Ransomware Group.
According to the advisory, BianLian is a ransomware developer, deployer, and data extortion cybercriminal group that has targeted organizations in multiple U.S. critical infrastructure sectors since June 2022. The ransomware group has also targeted several entities in the Australian critical infrastructure sector. The group typically gains access to victim networks using legitimate remote desktop protocol (RDP) credentials. They have been observed using open-source tools and command-line scripting for discovery and credential harvesting. After exfiltrating victim data using the file transfer protocol (FTP), the BianLian ransomware threat actors extort money by threatening to release stolen victim data if payment is not made. The BianLian threat actors were originally using the double-extortion model, but as of January 2023 have switched to exfiltration-based extortion.
Technical Details about BianLian Ransomware
The FBI observed BianLian attacks on U.S. critical infrastructure entities starting in June 2022. In 2023, the threat actors were observed leveraging exfiltration-based extortion, warning their victims of financial, business, and legal ramifications if the ransom payment was not made. The FBI, CISA, and ACSC investigation also revealed the following technical details about the attack:
- Initial access – the threat actors leveraged compromised RDP credentials to gain access to victim networks.
- Command & Control – A custom Go backdoor is implanted for each victim allowing the threat actors to install remote management and access software, including TeamViewer, Atera Agent, SplashTop, AnyDesk—for continued persistence and command and control activities.
- Defense Evasion– PowerShell and Windows Command Shell were used to disable Windows Defender and Anti-Malware Scan Interface (AMSI). Threat actors were observed modifying Windows Registry disable tamper protection for Sophos SAVEnabled, SEDEenabled, and SAVService services, enabling them to uninstall these services.
- Discovery – A combination of complied tools, including Advanced Port Scanner, SoftPerfect Network Scanner, SharpShares, PingCastle were used to learn more about the victim environment.
- Credential Access – Valid user accounts were used for lateral movement through the network and pursue additional malicious activities, including credential harvesting and attempts to access an Active Directory domain database.
- Persistence and Lateral Movement – Valid PsExec and RDP credentials were used for lateral movement. Prior to using RDP, BianLian actors used Command Shell and native Windows tools to add user accounts to the local Remote Desktop Users group, modified the added account’s password, and modified Windows firewall rules to allow incoming RDP traffic.
- Exfiltration and Impact – Threat actors used PowerShell scripts to search for sensitive files and exfiltrate them for data extortion. If a victim refuses to pay the ransom demand, the BianLian group threatens to publish exfiltrated data to a leak site maintained on the Tor network. BianLian group engages in additional techniques to pressure the victim into paying the ransom; including printing the ransom note to printers on the compromised network.
Important Note for SafeBreach Customers – Coverage for AA23-136A (BianLian Ransomware)
As soon as details were made available, the SafeBreach Labs teams mapped existing attacks and added new attacks to the Hacker’s Playbook immediately. SafeBreach customers can run/ re-run the attacks listed below to ensure their environments are protected against this vulnerability.
Existing Behavioral Attacks
- #7327 Execute the BianLian Ransomware on user files
- #7168 Enable a default account and add it to a Localgroup (Windows)
- #6473 Agentless lateral movement via RDP
- #1269 Creating Windows schedule task (schtasks.exe)
- #2164 Scheduled Task
- #2189 Account Manipulation
- #7170 Add a local administrator (Windows)
- #5670 Agentless lateral movement via Remote Registry
- #803 Enable Administrator Shares
- #905 Start the remote registry service
- #7144 Unregister anti malware scanning interface providers
- #7834 Add Exclusions to Windows Defender
- #7835 Disable Windows Defender from Registry
- #2267 Add an exclusion to Windows Defender using PowerShell
- #2389 Modify Firewall Rules using netsh.exe
- #3829 Run obfuscated Mimikatz on host
- #794 Extract Login Information using MimiKatz
- #1220 Inject Mimikatz using PowerShell to Extract Credentials
- #6127 Extract LSASS memory dump using PowerShell and Rundll32
- #8370 In memory credential extraction via MiniDumpWriteDump
- #8371 In memory credential extraction via MiniDumpWriteDump and handle hijacking
- #8372 Credential extraction via Pypykatz
- #7223 NTDS.dit dump using ntdsutil
- #6807 Extract credentials from ntds.dit file using volume shadow copy
- #2208 Extract Credentials using Get-GPPPassword (PowerShell)
- #2174 Extract users and groups using net.exe (Windows)
- #6578 Discover domain users using LDAP method
- #2306 Domain Trust Discovery
- #2335 Collect and Enumerate Domain Controller Shares using PowerView (PowerShell)
- #2336 Collect and Enumerate Domain Computers Shares using PowerView (PowerShell)
- #2192 Collect Data from Local Shared Drives using System Commands
- #2222 Discover Remote Systems using PowerShell
- #1693 Collect Windows system data using CMD
- #192 Brute force attack over RDP protocol
- #6909 RDP Connection Between 2 Simulators
- #6985 Clipboard data collection (Windows)
- #103 Data asset exfiltration using FTP STOR (ASCII)
- #104 Data asset exfiltration using FTP STOR (Binary)
Existing IOC-Based Attacks
- #7571 Pre-execution phase of BianLian Ransomware
- #7572 Write BianLian Ransomware to disk
- #7573 Transfer of BianLian Ransomware over HTTP/S
- #7574 Transfer of BianLian Ransomware over HTTP/S
- #7575 Email BianLian Ransomware as a ZIP attachment
- #7576 Email BianLian Ransomware as a ZIP attachment
Newly Added IOC-Based Attacks
- #8825 – Write BianLian backdoor to disk
- #8826 – Pre-execution phase of BianLian backdoor (Windows)
- #8827 – Transfer of BianLian backdoor over HTTP/S
- #8828 – Transfer of BianLian backdoor over HTTP/S
- #8829 – Email BianLian backdoor as a ZIP attachment
- #8830 – Email BianLian backdoor as a ZIP attachment
- #8831 – Write BianLian ransomware to disk
- #8832 – Pre-execution phase of BianLian ransomware (Windows)
- #8833 – Transfer of BianLian ransomware over HTTP/S
- #8834 – Transfer of BianLian ransomware over HTTP/S
- #8835 – Email BianLian ransomware as a ZIP attachment
- #8836 – Email BianLian ransomware as a ZIP attachment
What You Should Do Now
The playbook has been updated with attacks that map to the IOCs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
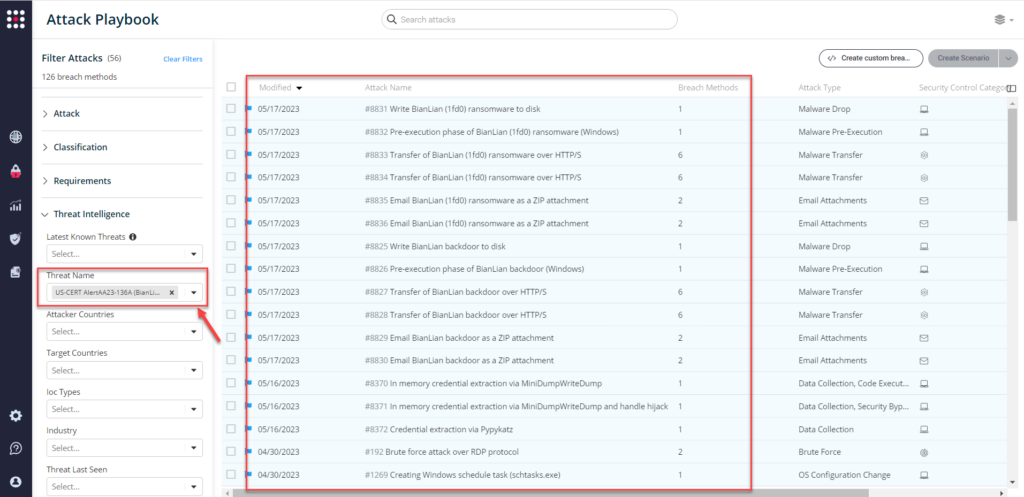
From the Attack Playbook, select and filter attacks related to US-CERT Alert AA23-136A. Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
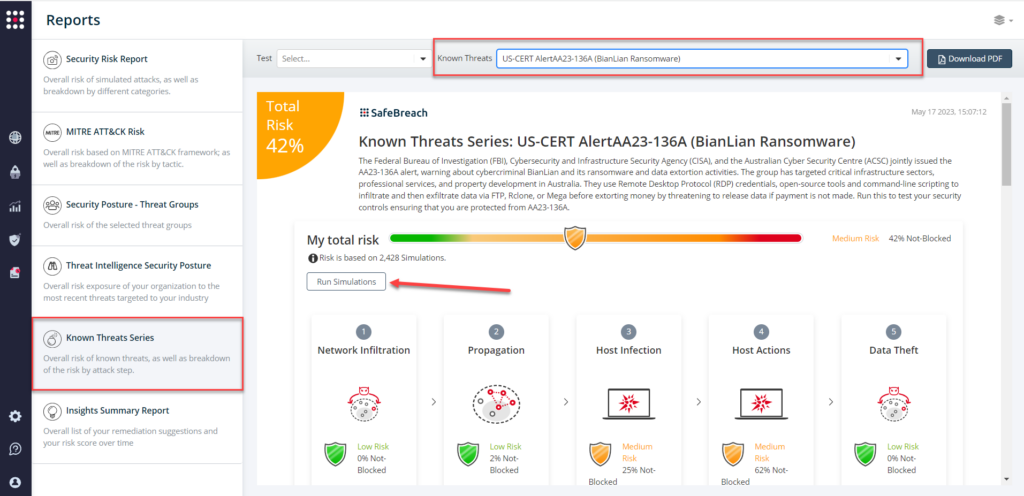
From the Known Attack Series report, select the AA23-136A (BianLian Ransomware) report and select Run Simulations which will run all attack methods.
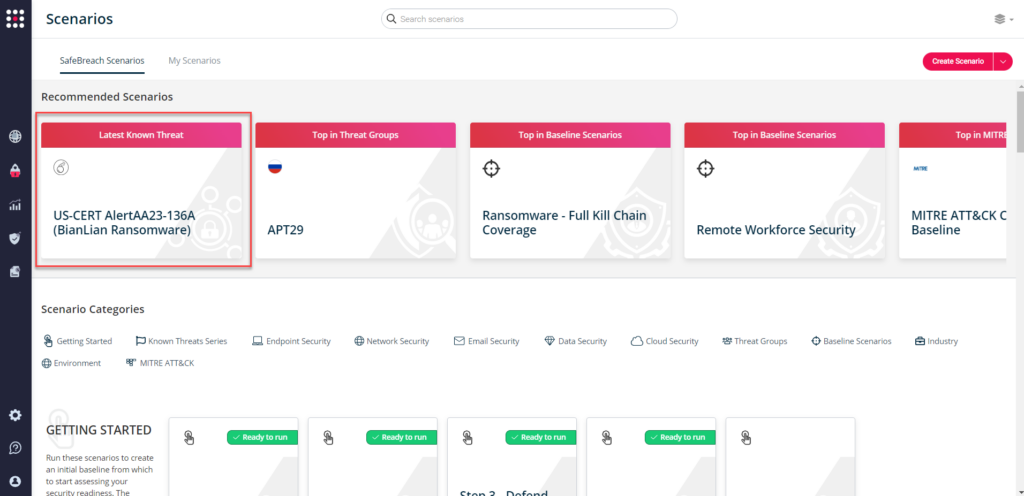
You can also go to “SafeBreach Scenarios” page and choose the AA23-136A (BianLian Ransomware) scenario from the list of available scenarios.
NOTE: CISA recommends continually validating your security program, at scale, in a production environment to ensure optimal performance against growing threat of advanced cyber threats. Additional recommendations include:
- Implement application controls to manage and control execution of software.
- Strictly limit the use of RDP and other remote desktop services.
- Disable command-line and scripting activities and permissions.
- Update Windows PowerShell or PowerShell Core to the latest version and uninstall all earlier PowerShell versions.
- Implement time-based access for accounts set at the admin level and higher.
- For detailed information about mitigations and incident response, please refer to the full advisory

