On October 4, the Federal Bureau of Investigation (FBI), the National Security Agency (NSA), and the Cybersecurity and Infrastructure Security Agency (CISA) issued a joint advisory highlighting malicious cyber activity by unknown advanced persistent threat (APT) actors against a Defense Industrial Base (DIB) organization’s enterprise network. According to the information available, this attack started in 2021 when the APT actors successfully compromised the network defenses and gained access to the networks. They continued to have access to the network until mid-January 2022. Additional details about these threat actors and its associated tactics, techniques, and procedures (TTPs) are available in US-CERT Alert (AA22-277A) Impacket and Exfiltration Tool Used to Steal Sensitive Information from Defense Industrial Base Organization.
Additional Technical Details
According to the advisory, the threat actors used an open-source toolkit called Impacket to gain an initial foothold within the DIB’s enterprise network and further compromise it. They also leveraged a custom data exfiltration tool called CovalentStealer to steal sensitive information from the DIB networks. Below are additional details about the compromise and data theft:
- Some threat actors gained initial access to the DIB’s MS Exchange Server as early as January 2021. During this initial recon, they gathered information about the exchange environment and performed mailbox searches to locate sensitive data.
- In January and February 2021, they used a previously compromised admin account “Admin 1” to access the Exchange Web Services (EWS) API.
- During the same period, they used Windows Command Shell to interact with the DIB’s network. This Command Shell was also used to learn about the organization’s environment and to collect sensitive data for eventual exfiltration, including sensitive contract-related information from shared drives.
- Files were manually collected using the command line tool WinRAR, split into 3 MB chunks and stored within the debug directory.
- The APT actors also used Impacket—an open-source Python toolkit to attempt to move laterally to another system.
- In March 2021, they also exploited CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065 to install 17 China Chopper web shells on the Exchange Server. Later in March, APT actors installed HyperBro on the Exchange Server and two other systems.
- In April 2021, Impacket was used for network exploitation activities.
- From July through mid-October 2021, CovalentStealer, a custom exfiltration tool, was used to export the remaining sensitive files.
Important Note for SafeBreach Customers – Coverage for AA22-277A
As soon as details and IOCs for the DIB compromise were made available, corresponding new attacks were immediately added to the SafeBreach Hacker’s Playbook™ on October 5. It is important to note that some of the attack TTPs used by these threat actors were already available in the SafeBreach playbook. SafeBreach customers already had an existing level of protection against these threat actors if their security controls were validated against these known TTPs.
11 newly added playbook methods for US-CERT Alert AA22-277A:
- HyperBro Malware
- (#7762) – Write HyperBro malware to disk (Host-Level)
- (#7763) – Transfer of HyperBro malware over HTTP/S (Lateral Movement)
- (#7764) – Transfer of HyperBro malware over HTTP/S (Infiltration)
- (#7765) – Email HyperBro malware as a ZIP attachment (Lateral Movement)
- (#7766) – Email HyperBro malware as a ZIP attachment (Infiltration)
- CovalentStealer Malware
- (#7767) – Pre-execution phase of CovalentStealer malware (Host-Level)
- (#7768) – Write CovalentStealer malware to disk (Host-Level)
- (#7769) – Transfer of CovalentStealer malware over HTTP/S (Lateral Movement)
- (#7770) – Transfer of CovalentStealer malware over HTTP/S (Infiltration)
- (#7771) – Email CovalentStealer malware as a ZIP attachment (Lateral Movement)
- (#7772) – Email CovalentStealer malware as a ZIP attachment (Infiltration)
81 previously available playbook attacks for AA22-277A:
- CVE-2021-26855
- (#6898) Exploitation of CVE-2021-26855 internal Exchange server (WAF)
- (#5983) Exploitation of CVE-2021-26855 external Exchange server
- (#5984) Exploitation of CVE-2021-26855 internal Exchange server
- MITRE ATT&CK Technique T1047 – Windows Management Instrumentation
- (#6364) Carbanak – System information and screenshot, collection, and exfiltration
- (#5672) Agentless lateral movement via WMI
- (#2250) Execute VBScript using XSL with wmic.exe
- (#6918) Execute remote VBScript using XSL with wmic.exe
- (#1527) Remote command execution by WMIC (information gathering)
- (#1528) Remote command execution by WMIC (remote download and execute)
- (#1529) Remote command execution by WMIC (persistence)
- (#1562) Remote command execution by WMIC (persistence)
- MITRE ATT&CK Technique T1569 – System Services
- (#6855) Execute task using launchctl and perform dynamic linker hijacking
- (#2348) Execute a binary using Launchctl
- (#2357) File system permissions weakness
- (#2293) Create and start a service
- (#904) Start the secondary logon service
- (#905) Start the remote registry service
- (#907) Start the Distributed COM service
- (#912) Start the SSDP discovery service
- MITRE ATT&CK Technique T1543 – Create or Modify System Process
- (#2294) Create Systemd service
- (#2293) Create and start a service
- (#1224) Create a persistent Linux service to facilitate a bind shell
- (#2347) Add a launch daemon
- (#2349) Add and execute a launch agent using launchctl
- MITRE ATT&CK Technique T1036.005 – Masquerading: Match Legitimate Name or Location
- (#2248) Masquerading
- MITRE ATT&CK Technique T1078 – Valid Accounts
- (#6473) Agentless lateral movement via RDP
- MITRE ATT&CK Technique T1497.001 – Virtualization/Sandbox Evasion: System Checks
- (#2279) Virtualization/sandbox evasion
- (#7068) Execute virtualization evasion
- MITRE ATT&CK Technique T1562.001 – Impair Defenses: Disable or Modify Tools
- (#2267) Add an exclusion to Windows Defender using PowerShell
- (#2389) Modify firewall rules using netsh.exe
- (#5107) Stop a service using net stop command
- (#7043) Disable Cortex XDR using its default password (Windows)
- (#7044) Disable Cortex XDR using its default password (Linux)
- MITRE ATT&CK Technique T1574 – Hijack Execution Flow
- (#2355) Modify the user’s PATH variable
- (#2356) Service registry permissions weakness
- (#2357) File system permissions weakness
- (#3681) Execute a binary using LD_PRELOAD injection
- (#6809) Execute DLL by signed executable (igfxtray.exe)
- (#6855) Execute task using launchctl and perform dynamic linker hijacking
- (#6994) Search order hijacking
- (#7079) Path interception by unquoted path
- (#7143) Hijack execution flow via COR_PROFILER
- MITRE ATT&CK Technique T1033 – System Owner/User Discovery
- (#6853) Discover macOS user configurations
- (#2175) Discover Linux user configurations using Bash (Linux)
- (#1693) Collect Windows system data using CMD
- MITRE ATT&CK Technique T1049 – System Network Connections Discovery
- (#811) Discover Linux network configuration using Bash
- (#6872) Discover macOS network configuration using Bash
- (#1693) Collect Windows system data using CMD
- MITRE ATT&CK Technique T1057 – Process Discovery
- (#6871) Discover macOS processes using Bash scripts
- (#2188) Extract process list using Windows commands
- (#1695) Discover Linux processes using Bash scripts
- MITRE ATT&CK Technique T1082 – System Information Discovery
- (#6854) Discover macOS system information
- (#1011) Discover Linux system information using Bash commands
- MITRE ATT&CK Technique T1083 – File and Directory Discovery
- (#6132) Discover file system information using bash commands (Linux, macOS)
- MITRE ATT&CK Technique T1021.002 – Remote Services: SMB/Windows Admin Shares
- (#6483) Agentless lateral movement via SMB and RCE, using Token duplication
- (#6513) Agentless lateral movement via SMB and RCE, using Mimikatz
- (#6550) Agentless lateral movement via SMB and RCE, using Impersonated user
- (#5674) Agentless lateral movement via Remote PowerShell (WinRM)
- (#5673) Agentless lateral movement via Remote PowerShell (WMI)
- (#5672) Agentless lateral movement via WMI
- (#5671) Agentless lateral movement via Windows Remote Management
- (#5670) Agentless lateral movement via Remote Registry
- (#1339) Remote command execution by PSExec
- (#1338) Remote command execution by PSExec
- MITRE ATT&CK Technique T1039 – Data from Network Shared Drive
- (#242) SMB – Shares connections attempts
- (#241) SMB- ‘dir’ remote shell
- MITRE ATT&CK Technique T1095 – Non-Application Layer Protocol
- (#131) Data asset exfiltration over UDP
- (#1263) Data asset exfiltration over TCP
- MITRE ATT&CK Technique T1105 – Ingress Tool Transfer
- (#312) Obfuscation of EXE inside Encrypted ZIP over HTTP/S protocol
- MITRE ATT&CK Technique T1090 – Proxy
- (#7046) Communication via TOR (Windows)
- MITRE ATT&CK Technique T1029 – Schedule Transfer
- (#106) Covert data exfiltration using HTTP (GET)
- Existing IOCs of China Chopper Malware
- (#3320) Email china chopper malware as a ZIP attachment
- (#3319) Email china chopper malware as a ZIP attachment
- (#3318) Transfer of china chopper malware over HTTP/S
- (#3317) Transfer of china chopper malware over HTTP/S
- (#3316) Write china chopper malware to disk
- (#3315) Pre-execution phase of china chopper malware
- (#177) CHINA CHOPPER install
- (#176) Remote control using the China Chopper Web Shell
- (#1689) Write China Chopper to Disk
- (#1051) Remote Control using China Chopper
- Existing IOCs of HyperBro Malware
- (#2703) Email HyperBro malware as a ZIP attachment
- (#2704) Email HyperBro malware as a ZIP attachment
- (#2701) Transfer of HyperBro malware over HTTP/S
- (#2700) Transfer of HyperBro malware over HTTP/S
- (#2699) Write HyperBro malware to disk
What You Should Do Now
Attack methods related to US-CERT Alert AA22-277A are ready to run across your simulators. The Known Attack Series report has been updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT Alert AA22-277A (Attack against Defense Industrial Base Organization) report and select Run Simulations, which will run all attack methods.
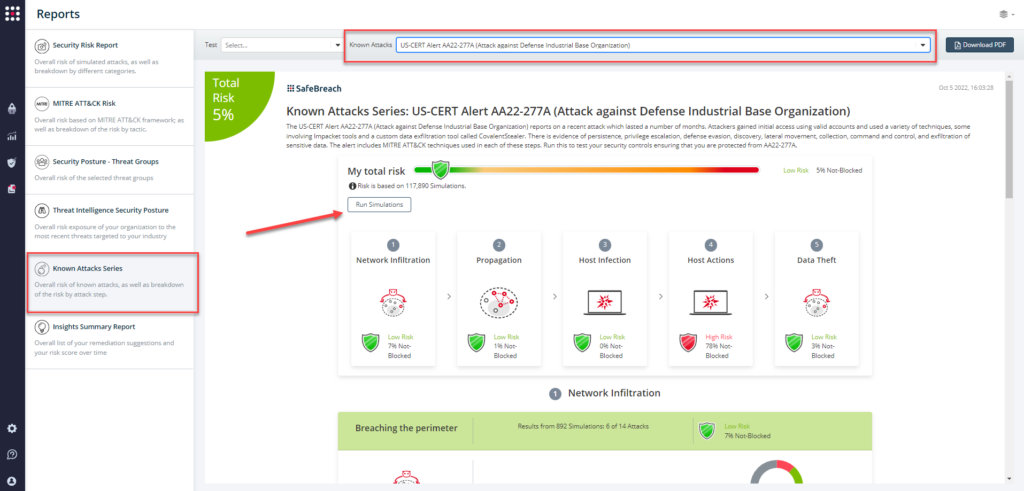
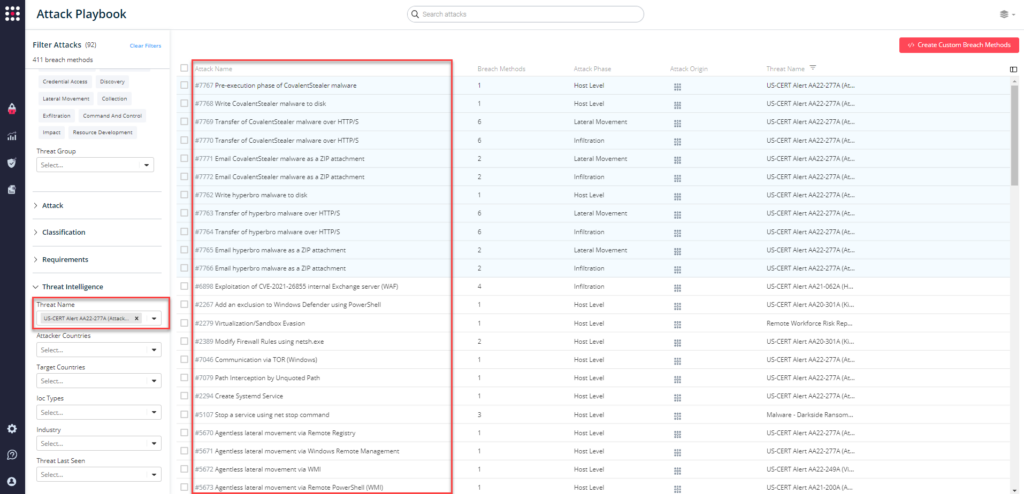
You can also select all the attacks related to US-CERT Alert AA22-277A by going to the SafeBreach playbook and filtering by Threat Name – US-CERT Alert AA22-277A (Attack against Defense Industrial Base Organization).
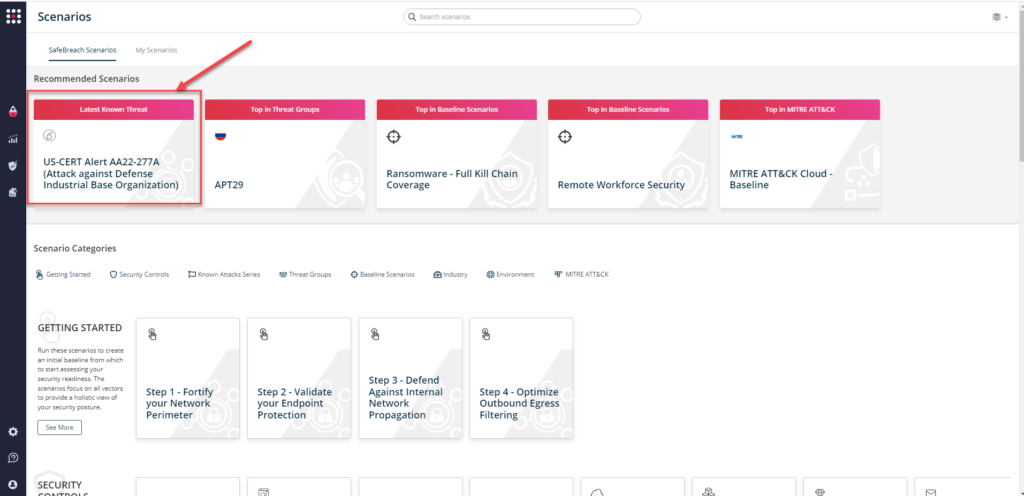
You can also go to the “SafeBreach Scenarios” page and choose the US-CERT Alert AA22-277A (Attack against Defense Industrial Base Organization) scenario from the list of available scenarios.
NOTE: The following actions have been recommended by CISA, the NSA, and the FBI to mitigate any threat arising from these threat actors:
- Validate security controls. CISA, the NSA, and the FBI recommend exercising, testing, and validating your organization’s security program against threat behaviors mapped to the MITRE ATT&CK for enterprise framework in this advisory. CISA, the NSA, and the FBI recommend continuously testing your existing security controls inventory to assess how they perform against the ATT&CK techniques described in this advisory.
- Enforce multi-factor authentication (MFA) on all user accounts.
- Implement network segmentation to separate network segments based on role and functionality.
- Update software, including operating systems, applications, and firmware, on network assets.
- Audit account usage.
- Consider additional mitigations noted here.