
Digital transformation has served to change many industries for the better in a post-pandemic world, but no more life changing than in the healthcare industry. Due to the weight of many stresses, we are seeing healthcare organizations extend beyond their clinical walls to power everything from pop-up clinics to telemedicine and driving the healthcare technology stack out to the edge.
Edge is experiencing unprecedented momentum among organizations around the world, despite concerns about its perceived risks. In fact, AT&T’s “Securing the Edge” report showed that 75% of survey respondents are planning, have partially, or have fully implemented an edge use case as of today. This same report also found that ransomware attacks (66.1%) targeted edge network servers and data as well as attacks against user/endpoint devices (65.5%).
We have seen healthcare adopt new edge approaches and technologies slowly moving away from traditional patient care solutions. Virtual care services surged during the pandemic and continue to help consumers reduce healthcare costs by providing care anytime and anywhere whether it be in an at-home setting or from a security device using a combination of video, mobile, cloud, and IoT technologies. According to a recent report on healthcare from Hewlett-Packard, 259,000 healthcare apps have been made available since 2017, including Doctor on Demand, which enables users to see a doctor for a video consultation, and Microsoft HealthVault, an app and online services that keeps users’ medical records secure and up to date. That number is estimated to grow to 635,000 by 2025.
In contrast, this new “anywhere” healthcare model has the highest perceived security risk within any industry, and the biggest impact should a cyberattack occur. New defenses will need to address the potentially increased attack surface, and issues of privacy and interoperability to determine how to ensure both the privacy and security of protected health information (PHI).
The good news is that as the industry moves toward a more modern model of integrated care, this heavy reliance on edge computing will push healthcare organizations to transform their cybersecurity practices to keep pace with innovation across the healthcare services continuum.
Edge Security in Healthcare – What Is It?
Edge is defined differently depending on who you talk to. Vendors are defining edge according to their technology stack, but this can make security decisions more complicated. Edge is very similar to when cloud first emerged, which was a historical shift in IT and security. Similarly, edge is doing the same as it moves computing from a centralized model to a decentralized model and away from data center consolidation toward distribution across the cloud. Edge moves the placement of infrastructure, applications, and workloads closer to where data is generated and consumed.
A proactive stance on security best serves the many healthcare organizations that are innovating at the edge. Former security decisions, or security controls based primarily on past practices, will no longer protect your organization. Healthcare data needs to be protected and shared in a safe way while remaining compliant with HIPAA, as well as local laws and regulations, yet breaks out of information silos to connect with other care providers. More simplified cybersecurity infrastructures are needed that are efficient, flexible, and scalable to enable a powerful and safe, patient-centric healthcare system.
Security Concerns & Considerations
Unfortunately, there is no one security strategy that can be deployed, and security teams need to be aware of all the security hazards that could impact the quality of care and the privacy implications of edge use computing.
Organizations should be aware of the security threats that edge deployment poses and build an ecosystem consisting of the right technology and partners that can help mitigate them. With the edge, healthcare cybersecurity teams must seek to improve their ability to address ransomware attacks that have negatively affected hospitals and clinics and other healthcare-related service organizations. As edge computing creates a much wider attack surface, different security controls need to be applied to safeguard data and other digital assets that reside outside of the hospital or providers’ locations.
We will explore three ways in which to test your security controls to help defend against potential attackers and safeguard your data and digital assets at the edge. The best approach is to try to anticipate cyber threats before they happen and to understand what defensive tools to employ to help prevent and combat attacks.
The top three cited attack vectors in the healthcare industry are:
- Ransomware due to social engineering attacks
- Attacks against associated cloud workloads
- Attacks against server/data within the network edge
Social Engineering Attacks
Social engineering remains the fastest growing security risk concern today. In a social engineering attack, criminals use “phishing” social skills and influence tactics to elicit information about an organization or its computer system. Whether a fictitious email from a friend or trusted source, or a legitimate company or individual trying to persuade you to share personal data, it just takes one quick click on a link to bait an unsuspecting user and expose your system to an attacker. There are many types of social engineering tactics, but phishing remains the most common and easiest way in which hackers infiltrate network systems.
When it comes to the edge, attackers will send phishing emails where URLs are redirected via an HTTP protocol in edge computing systems that are undetectable.
Some of the largest healthcare data breaches are due to unauthorized individuals gaining access to email systems after employees respond to phishing emails. MEDNAX Services Inc., a provider of revenue cycle management and other administrative services to its affiliated physician practices groups discovered that unauthorized individuals had gained access to its Microsoft Office 365-hosted email system after employees responded to phishing emails.
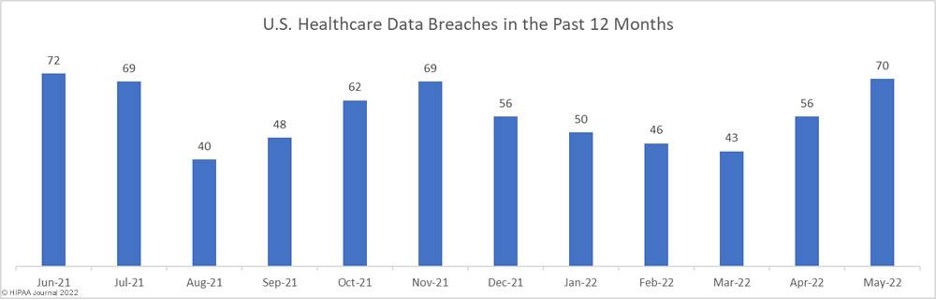
According to the HIPAA Journal, the organization that tracks and reports on data breaches in healthcare, May 2022 saw a 25% increase in data breaches of 500 or more records. Seventy data breaches were reported to the Department of Health and Human Services’ Office for Civil Rights (OCR) in May 2022, which is the highest monthly total this year and well above the 12-month average of 56.75 data breaches per month. This level of reported data breaches has not been seen since June 2021.
Spearphishing attacks can be prevented by taking a layered approach. To minimize the potential impact of phishing, implementation of strong security controls can reduce the chances for these types of emails getting into the hands of unsuspecting users while employee awareness training can highlight “phishing” tactics used by malicious actors to compromise companies. In addition, red and blue teams can evaluate their unique attack surface by using tools to mimic attacks that malicious social engineers use to breach your company, to validate the efficacy of security controls, and identify potential vulnerabilities and attack pathways.
Cloud Applications Security
Hybrid and multi-cloud solutions from major players like Amazon Web Services (AWS), Google Cloud, Microsoft Azure, VMware, and IBM are extending the cloud experience to edge locations with the pledge of a consistent application and operations experience. Off-the-shelf edge applications and marketplaces are readily available due to initiatives from the Google ecosystem comprised of 200 applications from 30 independent software vendors, and similar efforts by IBM and AWS producing “all in one” pricing models, all indicating how cloud-style utilization is affecting the edge.
Edge computing makes cloud and cloud workload security a big part of the equation, introducing security risks and shared security responsibility. While some cloud service providers may be responsible for the security of the infrastructure, most organizations will be held responsible for workload protection and security of their data, applications running within that infrastructure as well as access management.
Applications comprise many workloads (virtual machines [VMs], containers, serverless functions, databases, etc.). To effectively secure an organization’s cloud deployment, it is important to secure the infrastructure itself and every level of the workloads that are hosted on it. Each of these workloads must be properly configured individually and secured as well. There are many common threats in workload protection such as:
- Application security – The application is the #1 infiltration method for attackers when it comes to workloads. As a majority of applications are internet facing, application vulnerabilities and misconfigurations are susceptible to attacks.
- Workload infrastructure and network security – Whether workloads run on virtual machines or containers, once an attacker has an initial foothold, it is the resilience of the infrastructure and network configuration which may prevent the bad actor from further intrusion or getting to valuable resources and data.
- Cloud native services and control APIs – In the world of distributed applications and infrastructure, utilizing IaaS and PaaS, the cloud APIs represent a new attack surface which will be accessible to an attacker who obtains user/machine credentials granting himself access directly to valuable data and critical business services.
Before deploying a workload in the cloud, it must be properly configured. Configuration errors can introduce security gaps that can be exploited by an attacker. Applications can contain vulnerabilities that can be exploited either in the code that was used in development or imported from other third-party code. Applications should be regularly tested against the latest TTPs and mitigated quickly.
The more you gain visibility over your cloud ecosystem, the sooner you will be able to detect potential threats. A big picture of your workloads starts with how the applications are secured including the app and the APIs. Once you identify how the applications are secured, examine the workloads that make up the applications. Ensure that they are properly configured and that the visibility and controls are in place to identify any malicious or suspicious activities at the workload level. Applications should be operating in least privilege mode and running with the minimum level of authorizations necessary to perform.
Validating security controls through automation tools can help detect vulnerabilities associated with application workloads and eliminate threats before they become significant. Testing early and during runtime can also provide better cloud workload protection for your organization to help prevent suspicious activity and the likelihood of an attack.
Attacks Against Data within the Network Edge
For many security teams, securing the data center has comprised of firewalls, two-factor authentication, vulnerability monitoring, and role-based access control (RBAC) methods. But with edge deployments, security teams need to protect these new deployments, which adds more pressure as the attack surface now extends beyond the data center.
Traditionally, an organization’s most valuable data was confined within the data center. Security teams could easily monitor and control the movement of data in and out of the data center. And, if there was a data breach, teams could evaluate how the data was stolen and what data was taken in the attack. Edge deployments complicate this because they move the data collection and management of an organization’s valuable information outside the boundaries of the data center.
Edge deployment is all about data. Securing, collecting, and processing raw data at the point it is generated and using it to make intelligent business decisions within the organization.
Data, when moving from source to destination, is data in motion. Data stored on a disk in a database is data at rest. For edge deployments, there is typically a constant flow of data from the end user device or sensor. Both data in motion and data at rest are at risk by cyber criminals and protecting it can be challenging.
Although data is the most valuable asset in an edge deployment, it is no longer the sole motivator. By gaining access to networks or systems, these bad actors don’t want to just steal data but attain the bigger goal of disrupting operations.
Today’s networks are more intricate than ever, especially with edge deployments and techniques like Software Define Wide Area Networks (SD-WAN). Network attacks at the edge are very similar to those against a data center. However, edge deployments bring complexity and scale of the networks and the devices that connect into them. Networks can consist of millions of sensors or devices and gateways, and a single misconfigured device could provide that one access point attackers are seeking.
Technology to protect against these network attacks and edge access should consist of automated tools that can consistently validate security controls and policy-driven network configuration. Organizations that implement a zero-trust architecture and leverage the principle of least privilege to protect their networks can also be used to protect edge access to enterprise data or cloud services and mitigate network vulnerabilities.
How SafeBreach Can Help Protect the Edge
SafeBreach continuous security validation powered by our breach and attack simulation (BAS) platform offers a safe-by-design approach to reach designated assets to validate security control efficacy against known indicators of compromise (IOCs) for select high and low-value-assets. Simulated attacks in a planned IT architecture validates the efficacy of security controls to identify and prioritize the most critical threats and uncover all possible attack paths to improve detection efficacy.
SafeBreach provides validation of the controls in your entire security ecosystem with unmatched visibility into how your ecosystem will respond at each stage of the defense process. We offer solutions that can help healthcare organizations secure the edge.
Let’s Go Phishing – How to Avoid These Attacks Through Attack Simulation
Our BAS platform can help protect your organization from phishing attacks that could lead to costly data breaches or ransomware attacks. Red-team phishing simulations can help your security team understand how well-prepared your organization is to handle phishing attack attempts, giving them tangible experience and preparing the team with proper response techniques should a phishing attack occur.
SafeBreach will validate your email security controls at the first layer to reduce the impact of phishing and the chances of an unsuspecting user opening a phishing email that may compromise the company.
SafeBreach Phishing Simulations
The SafeBreach platform is comprised of over 25,000 individual attack methods and scenarios are tagged by industry and attack type using the Top 16 TTP MITRE ATT&CK workflows. The SafeBreach platform offers the ability to:
- Choose from 6,000 phishing and spearphishing attack scenarios based on malware or malicious links delivered via email and common use cases such as fake promotions (especially since the pandemic), or password resets due to unauthorized login attempts.
- You control what attacks to run and when, including associated parameters, sequencing steps, and the simulators desired to execute your scenarios.
- Easily generate phishing attack scenarios to understand how your organization is positioned against phishing threats which may be unique to you and your infrastructure.
- Your red and blue teams can analyze your individual test results of attacks and gain an overview of the simulation details, parameters, and goals all mapped to MITRE ATT&CK, an individual threat group, industry or NIST control mapping.
Security Control Validation of Application Workloads
The SafeBreach platform offers an advanced, hybrid, multi-cloud solution to validate security controls in your cloud ecosystem to provide critical information that will help you keep track of the risk associated with off-the-shelf edge applications and/or open-source dependencies your applications are built on. Continuous security validation can provide this information, ensuring you have the most up-to-date and accurate picture of your cloud vulnerabilities at edge locations.
Security Control Validation of Cloud Ecosystems
Whether it’s your native application security, runtime protection for your workloads, critical application dependencies for container security, or API governance and identity management in the control plane, SafeBreach provides continuous security validation for the full cloud kill chain in your cloud ecosystem.
We understand the risk associated with applications security, and we test your readiness in the cloud with real adversary behaviors to train your cloud immune system.
Lateral Attack Simulations at the Network Edge
The SafeBreach platform runs lateral movement simulations to identify locations of edge access and control weaknesses within the networks. We validate security controls and policy-driven network configuration to help protect edge access to enterprise data or cloud services.
Performing these types of simulations at different times during production operations, and across different edge locations, allows your organization to gain a much greater view of potential attack paths at the edge and to prioritize mitigation of these vulnerabilities without disruption to business operations.
Lateral movement simulations challenge internal networks against different TTPs and persistent threat methodologies used by attackers to gain edge access, escalate privileges, and breach additional systems on a network after the initial compromise of a single system.
Balancing on the Edge
As cloud computing and edge deployments gain traction, healthcare organizations will need to balance network and security controls with flexible architectures that can ensure security in the most complex hybrid scenarios. Given the attention over this expanding attack surface, healthcare organizations are making significant investments in the growing importance of shared responsibility models in the age of edge compute for networks and devices.
Keeping patient care confidential and compliant no matter where the data flows carry a heavier reliance on edge computing resulting in healthcare organizations transforming their cybersecurity controls and practices. Those who successfully balance the need to safely extend health services beyond clinical walls, while driving their healthcare technology stack out to the edge, understand the need to invest in a future that protects and safeguards their digital assets—all the way to the edge.
Want to learn more about SafeBreach, the leader in continuous security validation and breach and attack simulation? Request a demo with one of our cybersecurity experts today.