- US-CERT Alert AA24-060A #StopRansomware: Phobos Ransomware
- US-CERT Alert AA24-060B Threat Actors Exploit Multiple Vulnerabilities in Ivanti Connect Secure and Policy Secure Gateways
This blog will share an overview of both threats and our coverage of these threats. As a SafeBreach customer, you will have access to all the attacks listed below and more to validate your organizational security controls against these advanced threats.

AA24-060A – Phobos Ransomware
This advisory was jointly released by the Federal Bureau of Investigation (FBI), CISA, and the Multi-State Information Sharing and Analysis Center (MS-ISAC) and highlights the IOCs and TTPs associated with the Phobos ransomware observed as recently as February 2024. Phobos is typically leveraged in a ransomware-as-a-service (RaaS) model by its affiliates who are typically known to target state, local, tribal, and territorial (SLTT) governments. By targeting municipal and county governments, emergency services, education, public healthcare, and other critical infrastructure entities, Phobos ransomware affiliates have successfully managed to extract ransom worth several million U.S. dollars.
According to the information currently available, Phobos ransomware is likely connected to numerous variants (including Elking, Eight, Devos, Backmydata, and Faust ransomware) due to similar TTPs observed in Phobos intrusions. Threat actors leveraging Phobos typically use it along with open-source tools like Smokeloader, Cobalt Strike, and Bloodhound due to these tools being easily available and their ability to work in a wide variety of network environments. Additional details about this threat can be seen below:
- Recon and Initial access – Threat actors gain initial access by leveraging phishing to drop malicious payloads or by leveraging internet protocol (IP) scanning tools, such as Angry IP Scanner (for vulnerable RDP connections). Once they discover a vulnerable RDP connection, they gain initial access through brute force. Threat actors then deploy remote access tools to establish a connection with the victim network. Alternatively, they can also use spoofed emails to send hidden malicious payloads via backdoor trojans. These malicious payloads can then be used to exfiltrate sensitive data from victim networks.
- Execution and Privilege Escalation – By running executables like 1saas.exe or cmd.exe, threat actors deploy additional payloads that already have elevated privileges enabled. Phobos operations feature a standard three-phase process to decrypt a payload that allows the threat actors to deploy additional destructive malware. In the first phase, by manipulating VirtualAlloc or VirtualProtect API functions, threat actors can inject code into running processes, allowing malware to evade network defenses. In the second phase, a stealth process is used to obfuscate command-and-control (C2) activity by producing requests to legitimate websites. The third phase allows threat actors to unpack a program-erase cycle from stored memory, which is then sent to be extracted from an SHA 256 hash as a payload.
- Persistence and Privilege Escalation – Phobos affiliates have been observed using Windows Startup folders and Run Registry Keys such as C:/Users\Admin\AppData\Local\directory to maintain persistence within compromised environments. Additionally, by leveraging built-in Windows API functions, they steal tokens, bypass access controls, and create new processes to escalate privileges by leveraging the SeDebugPrivilege process.
- Discovery and Credential Access – Phobos actors additionally use open-source tools such as Bloodhound and Sharphound to enumerate the active directory. Additionally, Mimikatz and NirSoft, as well as Remote Desktop Passview have also been used to export browser client credentials.
- Exfiltration – Phobos affiliates typically use WinSCP and Mega.io for file exfiltration. They install Mega.io and use it to export victim files directly to a cloud storage provider. The stolen data is typically archived as a .rar or a .zip file. Targeted and typically stolen documents include legal documentation, financial records, technical documents (including network architecture), and databases for commonly used password management software.
- Post-Exfil Impact – After the exfiltration phase is completed Phobos actors look for backups using vssadmin.exe and Windows Management Instrumentation command-line utility (WMIC) to discover and delete volume shadow copies in Windows environments. This prevents victims from recovering files after encryption has taken place.
- Extortion – Extortion typically occurs via email. Some affiliates have even used voice calls to contact victims and demand ransom. Threat actors are also known to use instant messenger tools such as ICQ, Jabber, and QQ to communicate with victims.
AA24-060B – Ivanti Connect Secure and Pulse Secure Gateways
This advisory was jointly released by CISA and several partners, including the FBI, MS-ISAC, Australian Cybersecurity Center (ACSC), United Kingdom Cybersecurity Center (NCSC-UK), Canadian Center for Cyber Security, New Zealand Cyber Security Center (NCSC-NZ), and CERT-NZ. The advisory primarily deals with the ability of threat actors to deceive Ivanti’s internal and external Integrity Checker Tool (ICT) and evade detection.
According to the advisory, threat actors are actively exploiting CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893, allowing them to target and bypass Ivanti Connect Secure and Ivanti Policy Secure gateways. These vulnerabilities impact all supported versions (9.x and 22.x) and can be used in a chain of exploits to enable malicious cyber threat actors to bypass authentication, craft malicious requests, and execute arbitrary commands with elevated privileges. Investigations have revealed that Ivanti ICT is not enough to detect compromise and motivated threat actors can easily gain root-level persistence. Technical details of this threat can be found below:
- In early January 2024, it was discovered that two vulnerabilities (CVE-2023-46805 and CVE-2024-21887) in Ivanti Connect Secure and Policy Secure gateways were being chained to execute unauthorized remote code execution (RCE).
- Threat actors were able to exploit vulnerabilities to implant web shells, including GLASSTOKEN and GIFTEDVISITOR, on internal and external-facing web servers. Once successfully deployed, these web shells are used to execute commands on compromised devices.
- Once Ivanti provided initial guidance on how to mitigate these vulnerabilities, threat actors developed a way to bypass those mitigations to deploy BUSHWALK, LIGHTWIRE, and CHAINLINE web shell variants.
- Post-compromise, the actors moved laterally into domain environments and have been observed leveraging tools that are native to the Ivanti appliances—such as freerdp, ssh, telnet, and nmap libraries—to expand their access to the domain environment. The result, in some cases, was a full domain compromise.
- Detailed post-compromise analysis revealed that threat actors were able to clean up their efforts by overwriting files, time-stomping files, and re-mounting the runtime partition to return the appliance to a “clean state.”
Important Note for SafeBreach Customers – Coverage for US-CERT AA24-060A and AA24-060B
As soon as details were made available, the SafeBreach Labs teams added new attacks based on the advisory and mapped existing attacks in the Hacker’s Playbook to these US-CERT alerts, immediately. It is important to note that existing SafeBreach customers already had a good level of coverage against the IOCs and TTPs identified in the advisories. Please run/re-run the attacks listed below to ensure your environments are protected against these TTPs.
Existing Playbook Attacks Related to AA24-060A
- #192 – Brute force attack over RDP protocol (lateral movement)
- #794 – Extract Login Information using MimiKatz (host level)
- #911 – Add SE_DEBUG_NAME privilege (host level)
- #2173 – Execute Code using Mshta
- #1693 – Collect Windows system data using CMD (host level)
- #2188 – Extract Process List using Windows Commands (host level)
- #2221 – Modify the Registry Run keys (host level)
- #6372 – Modify Volume Shadow Copy (VSS) (host level)
- #2273 – Pass the Hash over SMB using Mimikatz (lateral movement)
- #2389 – Modify Firewall Rules using netsh.exe (host level)
- #3829 – Run obfuscated Mimikatz on host (host level)
- #5833 – Extract Login Information using MimiKatz DCSync (host level)
- #6473 – Agentless lateral movement via RDP (host level)
- #6578 – Discover domain users using LDAP method (host level)
- #6802 – Credential harvesting using Mimikatz DCSync with user credentials (host level)
- #7169 – Dump the SAM database from the registry (Windows) (host level)
- #7220 – Process Injection – Thread Execution Hijacking (host level)
- #8359 – Process Injection – Asynchronous Procedure Calls (host level)
- #9456 – Extract SAM credentials from registry (host level)
NEW Playbook Attacks Related to AA24-060A
- #9543 – Write Phobos (7069ed) ransomware to disk
- #9544 – Pre-execution phase of Phobos (7069ed) ransomware (Windows)
- #9545 – Transfer of Phobos (7069ed) ransomware over HTTP/S
- #9546 – Transfer of Phobos (7069ed) ransomware over HTTP/S
- #9547 – Email Phobos (7069ed) ransomware as a compressed attachment
Existing Playbook Attacks Related to AA24-060B
- #1693 – Collect Windows system data using CMD (host level)
- #2206 – Extract Security Packages using PowerShell (host level)
- #2267 – Add an exclusion to Windows Defender using PowerShell (host level)
- #228 – R57 Run Shell Command (lateral movement)
- #2611 – Extract system date using PowerShell (host level)
- #3671 – Edit System Permissions when Remounting Docker OS (host level)
- #3830 – Extract credentials using PwDump through PowerShell (infiltration)
- #5307 – Event Triggered Execution using PowerShell Profile (host level)
- #5674 – Agentless lateral movement via Remote PowerShell (WinRM) (host level)
- #6127 – Extract LSASS memory dump using PowerShell and Rundll32 (host level)
- #6473 – Agentless lateral movement via RDP (host level)
- #7168 – Enable a default account and add it to a Localgroup (Windows) (host level)
- #8004 – Capture Screen using Powershell (host level)
NEW Playbook Attacks Related to AA24-060B
- #9549 – Write LIGHTWIRE web shell (824ecb) infostealer to disk
- #9550 – Transfer of LIGHTWIRE web shell (824ecb) infostealer over HTTP/S
- #9551 – Transfer of LIGHTWIRE web shell (824ecb) infostealer over HTTP/S
- #9552 – Email LIGHTWIRE web shell (824ecb) infostealer as a compressed attachment
- #9553 – Email LIGHTWIRE web shell (824ecb) infostealer as a compressed attachment
- #9554 – Write WARPWIRE credential harvester (1e9dea) infostealer to disk
- #9555 – Transfer of WARPWIRE credential harvester (1e9dea) infostealer over HTTP/S
- #9556 – Transfer of WARPWIRE credential harvester (1e9dea) infostealer over HTTP/S
- #9557 – Email WARPWIRE credential harvester (1e9dea) infostealer as a compressed attachment
- #9558- Email WARPWIRE credential harvester (1e9dea) infostealer as a compressed attachment
What You Should Do Now
SafeBreach customers can now validate their security controls against these TTPs in multiple ways.
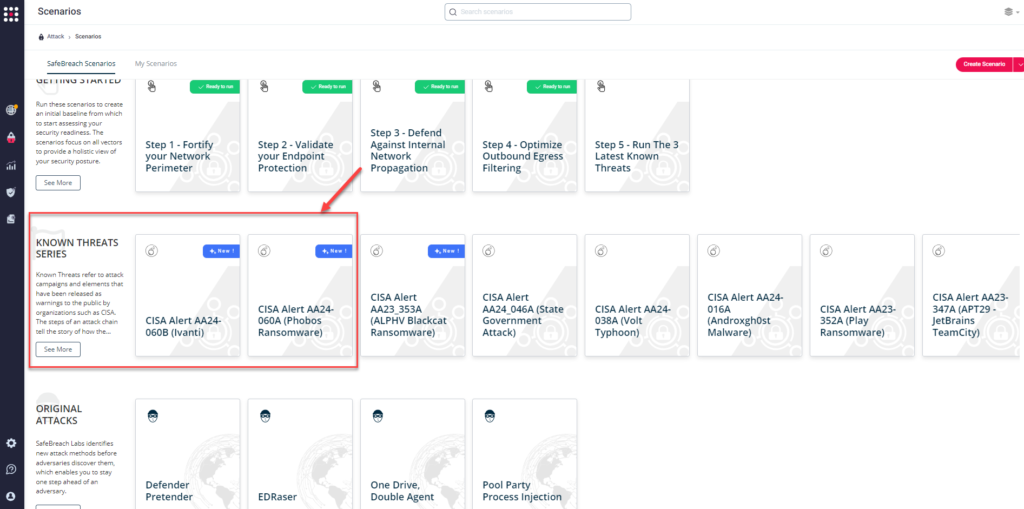
Method 1 – You can go to the “SafeBreach Scenarios” page and choose the AA24-060A (Phobos Ransomware) or AA24-060B (Ivanti) scenario from the list of available scenarios.
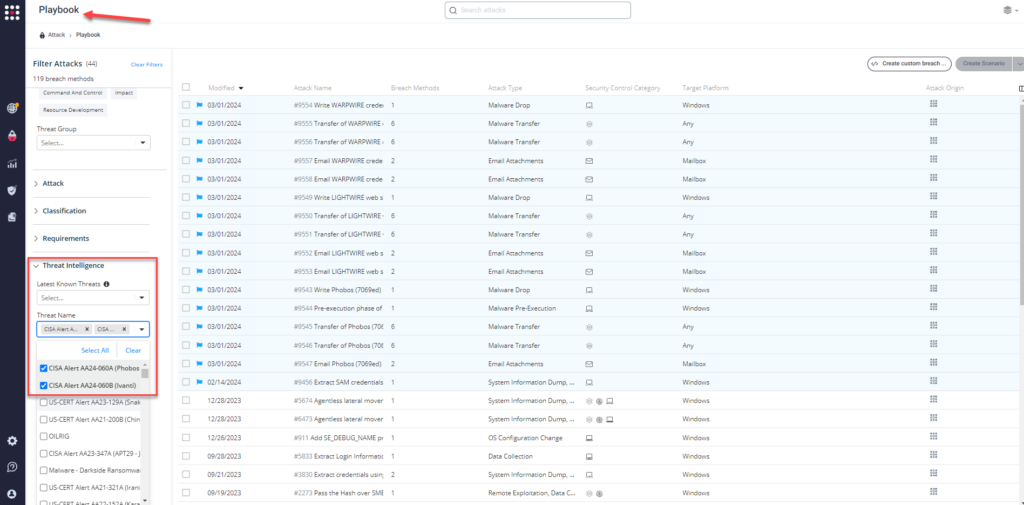
Method 2 – From the Attack Playbook, select and filter attacks related to US-CERT Alert AA24-060A (Phobos Ransomware) or US-CERT Alert AA24-060B (Ivanti). Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
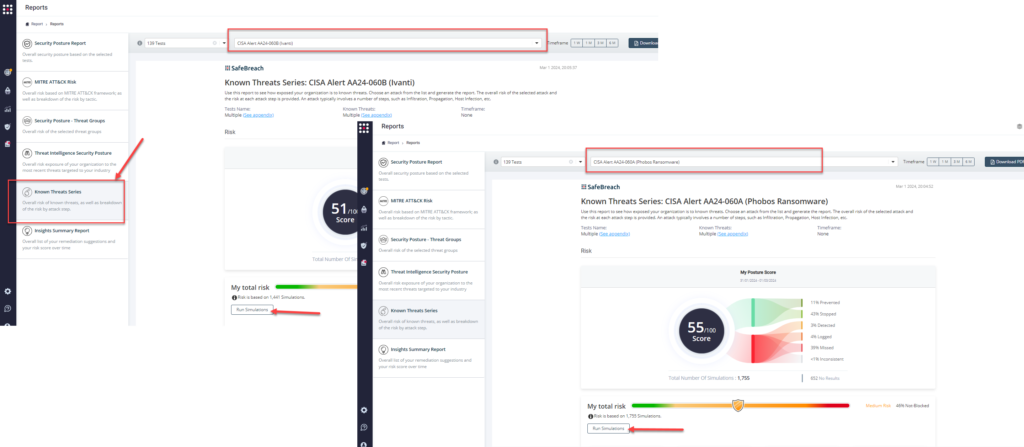
Method 3 – From the Known Attack Series report, select the US-CERT Alert AA24-060A (Phobos Ransomware) or US-CERT Alert AA24-060B (Ivanti) report and select Run Simulations, which will run all attack methods.
NOTE – CISA recommends continually validating your security program, at scale, in a production environment to ensure optimal performance against growing threat of advanced cyber threats. Additional recommendations can be seen in each of the advisories (linked below):
- AA24-060A (Phobos Ransomware) – For detailed information about mitigations and incident response, please refer to the full advisory.
- AA24-060A (Ivanti) – For detailed information about mitigations and incident response, please refer to the full advisory.


