%
Organizations recently surveyed experienced an OT/IoT security event in the prior 12 months.
%
Industrial organizations only run an OT security assessment once/year or less.
Engineering workstations, HMIs, and operations servers (all running a commercial OS such as Windows or Linux) are the top 3 control system components at greatest risk for compromise in an OT attack.
Breach and attack simulation sheds light on 99% of your OT exposure: discover the SafeBreach difference

Post Production Uptime
Continuously validate your security controls to safeguard your production processes from costly downtime caused by cyberattacks.

Unify IT / OT Security Testing and Remediation
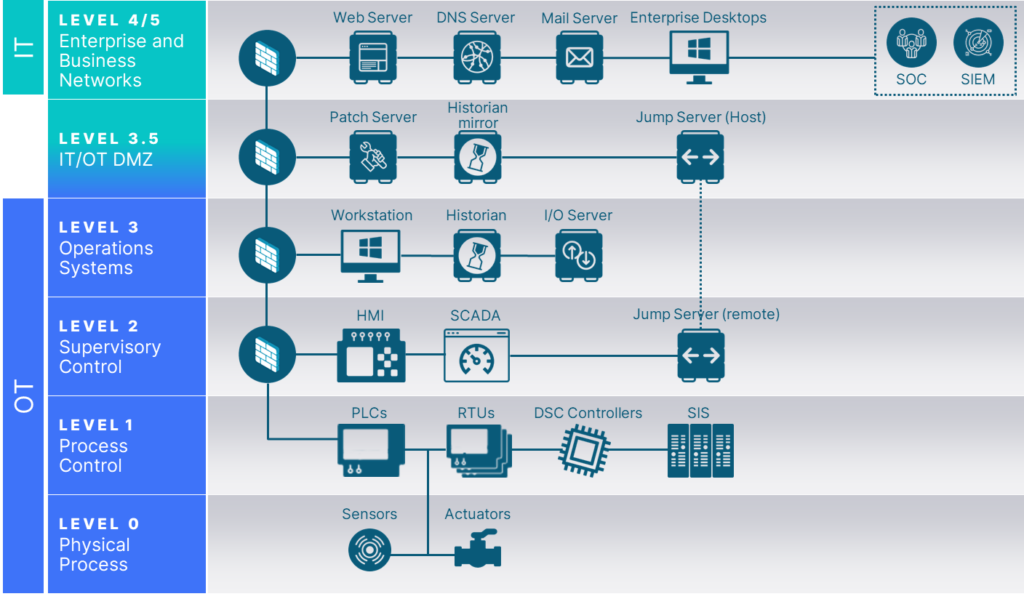
Create a consolidated view of your IT/OT environment to quickly identify and remediate points of “spill-over” from one network to the other during an attack.

Confidently Support OT Digital Transformation
Ensure your operations, IT, and security teams utilize the same information to meet demands for both productivity and protection as your operational environment transforms.
Resources to Help You Plan For the Unknown
Because you don’t know what you don’t know. Until you do.

“Tools like SafeBreach provide a continuous picture of how well you’re protecting yourself. Vulnerability scanners miss the mark, penetration testing doesn’t go far enough, and compliance tools only provide an isolated, often subjective snapshot of your security posture. SafeBreach, however, provides continuous insight while accurately replicating real-world attack scenarios. ”
– Tal Arad
CISO & Head of Technology, Carlsberg