On March 15th, the Federal Bureau of Investigation (FBI), Multi-State Information Sharing and Analysis Center (MS-ISAC), and the Cybersecurity and Infrastructure Security Agency (CISA) released an advisory highlighting the malicious cyber activities carried out by multiple threat actors (including an APT actor) that allowed them to exploit a .NET deserialization vulnerability (CVE-2019-18935) in Progress Telerik user interface (UI) for ASP.NET AJAX, located in a Federal Civilian Executive Branch (FCEB) agency’s Microsoft Internet Information Services (IIS) web server. Details of this investigation (along with attacker TTPs and IOCs) were made available via US-CERT Alert (AA23-074A) Threat Actors Exploit Progress Telerik Vulnerability in U.S. Government IIS Server
According to the advisory, threat actors began their campaign in November 2022. They successfully exploited the .NET deserialization vulnerability which granted them the ability to successfully execute remote code on the vulnerable web server. It is believed that the FCEB agency’s vulnerability scanner was set up to detect CVE-2019-18935, but failed to do so as the Telerik UI software was installed in a file path not usually scanned by the VM tool. Additionally, analysis suggests that the threat actors could have potentially exploited CVE-2019-18935 in conjunction with either CVE-2017-11357 or CVE-2017-11317.
Additional Technical Details
The investigation revealed that two primary threat actors – Threat Actor 1 (an unnamed APT actor) and Threat Actor 2 (XE group) actor conducted reconnaissance and scanning activities that correlate to the successful exploitation of CVE-2019-18935. Threat actors uploaded malicious DLL files (some masquerading as PNG image files) to the Windows Temp directory. These malicious files were then executed via the w3wp[.]exe process – a legitimate process running on IIS servers. CISA and authoring organizations confirmed that some malicious files dropped on the IIS server are consistent with a previously reported file naming convention that threat actors commonly use when exploiting CVE-2019-18935.
Threat analysts revealed that malicious artifacts were not available for analysis because the threat actors’ malware—that looks for and removes files with the .dll file extension—removed files from the Windows Temp directory. They also observed error messages being sent to the threat actors’ command and control (C2) server when existing permission restraints prevented the service account from executing the malicious DLLs and writing new files. Analysts did not observe evidence of privilege escalation or lateral movement.
Important Note for SafeBreach Customers – Coverage for AA23-074A
As soon as details and IOCs were made available, corresponding new attacks were immediately added to the SafeBreach Hacker’s Playbook™ on March 16th. SafeBreach customers can run the attacks listed below to ensure their environments are protected against this threat.
Newly added playbook methods for US-CERT Alert AA23-074A:
IOC-Based Attacks:
- #8707 – Write XEReverseShell dropper to disk
- #8709 – Transfer of XEReverseShell dropper over HTTP/S
- #8710 – Transfer of XEReverseShell dropper over HTTP/S
- #8711 – Email XEReverseShell dropper as a ZIP attachment
- #8712 – Email XEReverseShell dropper as a ZIP attachment
- #8713 – Write XEReverseShell backdoor to disk
- #8714 – Transfer of XEReverseShell backdoor over HTTP/S
- #8715 – Transfer of XEReverseShell backdoor over HTTP/S
- #8716 – Email XEReverseShell backdoor as a ZIP attachment
- #8717 – Email XEReverseShell backdoor as a ZIP attachment
- #8718 – Write XEReverseShell webshell to disk
- #8719 – Transfer of XEReverseShell webshell over HTTP/S
- #8720 – Transfer of XEReverseShell webshell over HTTP/S
- #8721 – Email XEReverseShell webshell as a ZIP attachment
- #8722 – Email XEReverseShell webshell as a ZIP attachment
Previously available playbook attacks for US-CERT Alert AA23-074A:
Behavioral Attacks
- #2248 – Masquerading (MITRE T1036.005)
- #2246 – 2246 – Hooking of GetSystemTime function using mavinject.exe with a custom DLL (MITRE T1055.001)
- #2302 – Modify the timestamp of a file using Powershell (MITRE T1070.006)
- #1693 – Collect Windows system data using CMD (MITRE T1016)
- #312 – Obfuscation of EXE inside Encrypted ZIP over HTTP/S protocol (MITRE T1105)
- #1263 – Data asset exfiltration over TCP (MITRE T1095)
What You Should Do Now
Several attack methods related to this US-CERT Alert were already present in the SafeBreach Hacker’s Playbook™. The playbook has now been updated with attacks that map to the new IOCs and TTPs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
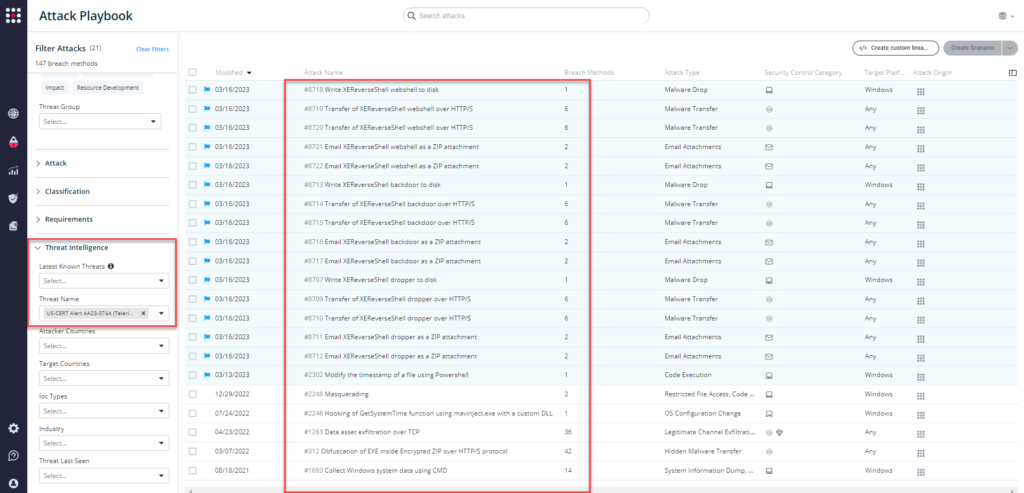
From the Attack Playbook, select and filter attacks related to AA23-074A (Telerik Vulnerability in IIS Server).
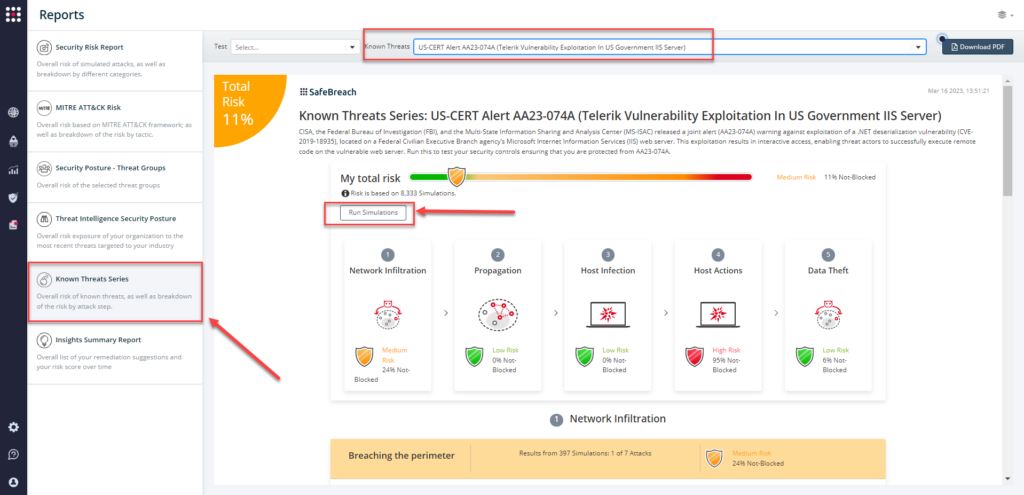
From the Known Attack Series report, select the AA23-074 (Telerik Vulnerability in IIS Server) report and select Run Simulations which will run all attack methods.
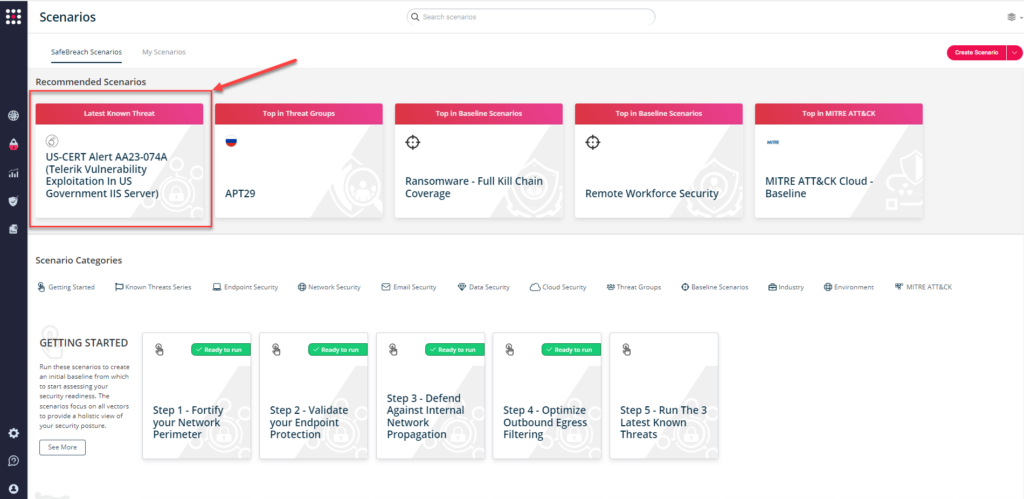
You can also go to “SafeBreach Scenarios” page and choose the AA23-074A (Telerik Vulnerability in IIS Server) scenario from the list of available scenarios.
NOTE: CISA, FBI, and MS-ISAC recommend continually validating your security program, at scale, in a production environment to ensure optimal performance against the MITRE ATT&CK techniques identified in this advisory:
- Upgrade all instances of Telerik UI ASP.NET AJAX to the latest version after appropriate testing.
- Prioritize remediation of vulnerabilities on internet-facing systems.
- Segment networks based on function.
- Keep all operating systems, software, and firmware up to date.
- Implement phishing-resistant multifactor authentication (MFA).
Additional Useful Resources
- Telerik: Exploiting .NET JavaScriptSerializer Deserialization (CVE-2019-18935)
- ACSC Advisory 2020-004
- Bishop Fox CVE-2019-18935: Remote Code Execution via Insecure Deserialization in Telerik UI
- Volexity Threat Research: XE Group
- GitHub: Proof-of-Concept Exploit for CVE-2019-18935
- Microsoft: Configure Logging in IIS
- GitHub: CVE-2019-18935

