On March 16th, the Federal Bureau of Investigation (FBI), Multi-State Information Sharing and Analysis Center (MS-ISAC), and the Cybersecurity and Infrastructure Security Agency (CISA) released an advisory highlighting the known LockBit 3.0 IOCs and TTPs gathered through FBI investigations. Details of this investigation (along with attacker TTPs and IOCs) were made available via US-CERT Alert (AA23-075A) #StopRansomware: LockBit 3.0.
According to the advisory, the LockBit 3.0 (also known as LockBit Black) ransomware operations function as a Ransomware-as-a-Service (RaaS) model and is a continuation of previous versions of the ransomware, LockBit 2.0, and LockBit. Since January 2020, LockBit has functioned as an affiliate-based ransomware variant; affiliates deploying the LockBit RaaS use many varying TTPs and attack a wide range of businesses and critical infrastructure organizations, which can make effective computer network defense and mitigation challenging.
Additional Technical Details
LockBit 3.0/ LockBit Black is more modular and evasive than its predecessors and shares similarities with BlackMatter and Blackcat ransomware. LockBit 3.0 is configured upon compilation with many different options that determine the behavior of the ransomware. Upon the actual execution of the ransomware within a victim environment, various arguments can be supplied to further modify the behavior of the ransomware.
- LockBit 3.0 accepts additional arguments for specific operations in lateral movement and rebooting into Safe Mode.
- If a LockBit affiliate does not have access to passwordless LockBit 3.0 ransomware, then a password argument is mandatory during the execution of the ransomware. LockBit 3.0 affiliates failing to enter the correct password will be unable to execute the ransomware.
- By protecting the code in such a manner, LockBit 3.0 hinders malware detection and analysis with the code being inexecutable and unreadable in its encrypted form. Signature-based detections may fail to detect the LockBit 3.0 executable as the executable’s encrypted potion will vary based on the cryptographic key used for encryption while also generating a unique hash.
- LockBit 3.0 will only infect machines that do not have language settings matching a defined exclusion list. However, whether a system language is checked at runtime is determined by a configuration flag originally set at compilation time. Languages on the exclusion list include, but are not limited to, Romanian (Moldova), Arabic (Syria), and Tatar (Russia). If a language from the exclusion list is detected, LockBit 3.0 will stop execution without infecting the system.
During the investigation, LockBit 3.0 was observed following these steps to enter victim networks and execute malicious code:
- Initial Access – Affiliates deploying LockBit 3.0 ransomware gain initial access to victim networks via remote desktop protocol (RDP) exploitation, drive-by compromise, phishing campaigns, abuse of valid accounts, and exploitation of public-facing applications.
- Execution and Infection – LockBit 3.0 attempts to spread across a victim network by using a preconfigured list of credentials hardcoded at compilation time or a compromised local account with elevated privileges. LockBit 3.0 may also enable options for spreading via Group Policy Objects and PsExec using the Server Message Block (SMB) protocol when compiled. LockBit 3.0 attempts to encrypt data saved to any local or remote device but skips files associated with core system functions.
- Exfiltration – LockBit 3.0 affiliates use Stealbit, a custom exfiltration tool used previously with LockBit 2.0; rclone, an open-source command line cloud storage manager; and publicly available file sharing services, such as MEGA, to exfiltrate sensitive company data files prior to encryption. While rclone and many publicly available file-sharing services are primarily used for legitimate purposes, they can also be used by threat actors to aid in system compromise, network exploration, or data exfiltration. LockBit 3.0 affiliates often use other publicly available file-sharing services to exfiltrate data.
Important Note for SafeBreach Customers – Coverage for AA23-075A
As soon as details were made available, the SafeBreach Labs teams mapped existing Hacker’s Playbook attacks to this threat immediately. SafeBreach customers can run/ re-run the attacks listed below to ensure their environments are protected against this threat.
Existing Behavioral Attacks
Valid Accounts (T1078)
- #6473 Agentless lateral movement via RDP
- #7168 Enable a default account and add it to a Localgroup (Windows)
Drive-by Compromise (T1189)
- #6479 Simulate the SocGholish dropper with pre-execution of malicious malware
Boot or Logon Autostart Execution (T1547)
- #8323 Register security support provider (Windows)
- #2220 Modify a Shortcut using VBScript
- #2632 Edit the Authentication Package DLL Registry Key
- #2221 Modify the Registry Run keys
- #6990 Edit the ‘Active Setup’ Registry Key
- #6995 Register executable to Winlogon Helper DLL
- #7001 Install a print processor
- #2241 Time providers
- #2630 Edit the Port Monitor Registry Key
Obfuscated Files or Information (T1027)
- The report did not mention specific method, thus most of SafeBreach’s existing exfiltration attacks may be valuable
Indicator Removal: File Deletion (T1070.004)
- #2244 Windows Management Instrumentation Event Subscription
OS Credential Dumping: LSASS Memory (T1003.001)
- #1220 Inject Mimikatz using PowerShell to Extract Credentials
- #3819 Windows Credentials Collection using LaZagne
- #3829 Run obfuscated Mimikatz on host
- #794 Extract Login Information using MimiKatz
System Information Discovery (T1082)
- #6364 Carbanak – System information and screenshot, collection, and exfiltration
System Location Discovery: System Language Discovery (T1614.001)
- #6805 Discover System Language (Windows)
Remote Services: Remote Desktop Protocol (T1021.001)
- #6473 Agentless lateral movement via RDP
- #6910 RDP Tunneling
- #6909 RDP Connection Between 2 Simulators
- #192 Brute force attack over RDP protocol
Data Destruction (T1485)
- #2278 Data Destruction
Service Stop (T1489)
- #5107 Stop a service using net stop command
Inhibit System Recovery (T1490)
- #6372 Modify Volume Shadow Copy (VSS)
Defacement (T1491.001)
- #7000 Change the desktop wallpaper (Windows)
Existing IOC-Based Attacks
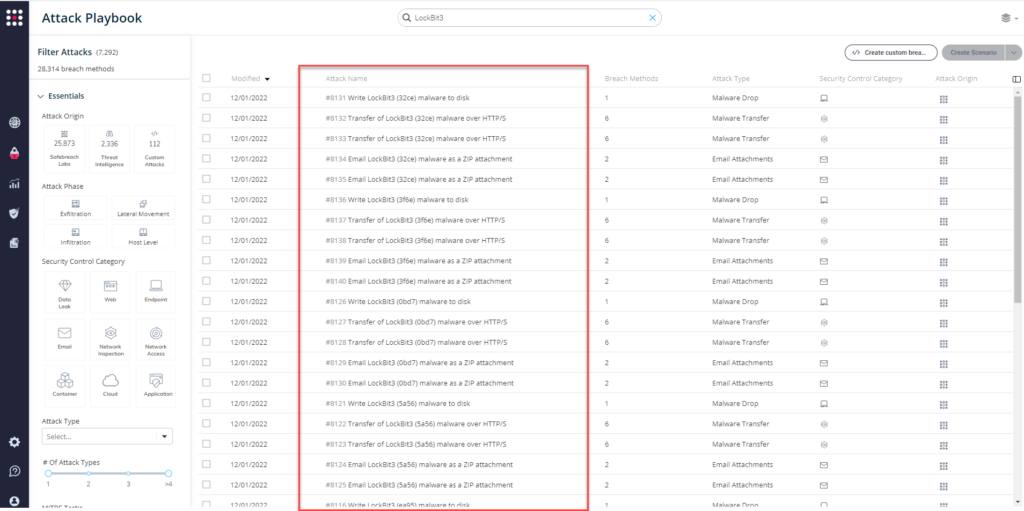
- #8101 – Write LockBit3 (62db) malware to disk
- #8102 – Transfer of LockBit3 (62db) malware over HTTP/S
- #8103 – Transfer of LockBit3 (62db) malware over HTTP/S
- #8104 – Email LockBit3 (62db) malware as a ZIP attachment
- #8105 – Email LockBit3 (62db) malware as a ZIP attachment
- #8106 – Write LockBit3 (da37) malware to disk
- #8107 – Transfer of LockBit3 (da37) malware over HTTP/S
- #8108 – Transfer of LockBit3 (da37) malware over HTTP/S
- #8109 – Email LockBit3 (da37) malware as a ZIP attachment
- #8110 – Email LockBit3 (da37) malware as a ZIP attachment
- #8111 – Write LockBit3 (ab92) malware to disk
- #8112 – Transfer of LockBit3 (ab92) malware over HTTP/S
- #8113 – Transfer of LockBit3 (ab92) malware over HTTP/S
- #8114 – Email LockBit3 (ab92) malware as a ZIP attachment
- #8115 – Email LockBit3 (ab92) malware as a ZIP attachment
- #8116 – Write LockBit3 (ea95) malware to disk
- #8117 – Transfer of LockBit3 (ea95) malware over HTTP/S
- #8118 – Transfer of LockBit3 (ea95) malware over HTTP/S
- #8119 – Email LockBit3 (ea95) malware as a ZIP attachment
- #8120 – Email LockBit3 (ea95) malware as a ZIP attachment
- #8121 – Write LockBit3 (5a56) malware to disk
- #8122 – Transfer of LockBit3 (5a56) malware over HTTP/S
- #8123 – Transfer of LockBit3 (5a56) malware over HTTP/S
- #8124 – Email LockBit3 (5a56) malware as a ZIP attachment
- #8125 – Email LockBit3 (5a56) malware as a ZIP attachment
- #8126 – Write LockBit3 (0bd7) malware to disk
- #8127 – Transfer of LockBit3 (0bd7) malware over HTTP/S
- #8128 – Transfer of LockBit3 (0bd7) malware over HTTP/S
- #8129 – Email LockBit3 (0bd7) malware as a ZIP attachment
- #8130 – Email LockBit3 (0bd7) malware as a ZIP attachment
- #8131 – Write LockBit3 (32ce) malware to disk
- #8132 – Transfer of LockBit3 (32ce) malware over HTTP/S
- #8133 – Transfer of LockBit3 (32ce) malware over HTTP/S
- #8134 – Email LockBit3 (32ce) malware as a ZIP attachment
- #8135 – Email LockBit3 (32ce) malware as a ZIP attachment
- #8136 – Write LockBit3 (3f6e) malware to disk
- #8137 – Transfer of LockBit3 (3f6e) malware over HTTP/S
- #8138 – Transfer of LockBit3 (3f6e) malware over HTTP/S
- #8139 – Email LockBit3 (3f6e) malware as a ZIP attachment
- #8140 – Email LockBit3 (3f6e) malware as a ZIP attachment
What You Should Do Now
No new malware hashes were released with this US-CERT Alert. However, the SafeBreach Hacker’s Playbook™ does include comprehensive coverage of all previously known LockBit 3.0 IOCs. This means that existing SafeBreach customers do have a good amount of coverage against this ransomware variant.
From the Attack Playbook, select and filter attacks related to LockBit 3.0. Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
NOTE: CISA, FBI, and MS-ISAC recommend continually validating your security program, at scale, in a production environment to ensure optimal performance against the growing threat of ransomware:
- Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers.
- Require all accounts with password logins.
- Segment networks based on function.
- Identify, detect, and investigate abnormal activity and potential traversal of the indicated ransomware with a networking monitoring tool.
- Implement phishing-resistant multifactor authentication (MFA).
Additional Useful Resources
- SafeBreach’s complimentary RansomwareRx assessment.
- Stopransomware.gov is a whole-of-government approach that gives one central location for ransomware resources and alerts.
- Resource to mitigate a ransomware attack: CISA-Multi-State Information Sharing and Analysis Center (MS-ISAC) Joint Ransomware Guide.

