On May 24th, the National Security Agency (NSA), the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), the Canadian Centre for Cyber Security (CCCS), the New Zealand National Cyber Security Centre (NCSC-NZ), United Kingdom National Cyber Security Centre (NCSC-UK) and the Australian Cyber Security Centre (ACSC) along with their private sector partners recently discovered a cluster of activity of interest associated with a People’s Republic of China (PRC) state-sponsored cyber actor, also known as Volt Typhoon. The authoring agencies have released an advisory highlighting the various malicious indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) being leveraged by the Volt Typhoon group. These TTPs and IOCs are listed in US-CERT Alert (AA23-144A) – People’s Republic of China State-Sponsored Cyber Actor Living off the Land to Evade Detection.
According to the advisory, Volt Typhoon’s malicious activity affects networks across U.S. critical infrastructure sectors and the same TTPs and IOCs could be used to target critical infrastructure and other sectors across the world. One of the key defining features of this threat actor is its use of living-off-the-land techniques, which makes it inherently hard to detect with traditional EDR tools. Some of the tools being used by the threat actor are built-in tools, including wmic, ntdsutil, netsh, and PowerShell which are built-in network administration tools.
Important Note for SafeBreach Customers and Non-Customers
The advisory listed a wealth of information including valuable analysis and summary of the post-compromise tactics, techniques, and procedures (TTPs). By having access to the TTPs, we were enabled to build the attacks that support our customers.
That is why SafeBreach is the first and only breach and attack simulation (BAS) provider to develop attacks based on the actual TTPs and IOCs used by the Volt Typhoon group in under 24 hours and are making these available in our platform to test in your environment.
SafeBreach Customers – Understanding the severity of this attack and the previous few CERTs on critical infrastructure, we are offering additional support by offering a personalized 1:1 session with our research team to help you understand the evolving threat landscape as well as extending complimentary access to our SafeBreach-as-a-Service experts, to help you run these attacks. To access this offer, kindly reach out to your CSM or fill out our contact us form.
Non-Customers – We will run a customized, no-cost attack scenario based on actual Volt Typhoon behavior—to help you gain unparalleled visibility into how your security ecosystem responds at each stage of the defense process. Please complete this form.
Technical Details about the Volt Typhoon Attack
Microsoft Security first discovered this stealthy and malicious activity by Volt Typhoon, a nation-state-sponsored threat group heavily focused on espionage and information gathering. Their researchers have determined that this threat actor is pursuing the development of capabilities that could disrupt critical communications infrastructure between the United States and Asia region during future crises. The entities targeted during the current attack include those from the communications, manufacturing, utility, transportation, construction, maritime, government, information technology, and education sectors.
As the threat actors rely on stealth, they heavily leverage living-off-the-land techniques and issue command line directives to:
- Collect credential data from local and network systems
- Archive data and stage it for exfiltration
- Leverage stolen credentials to maintain persistence
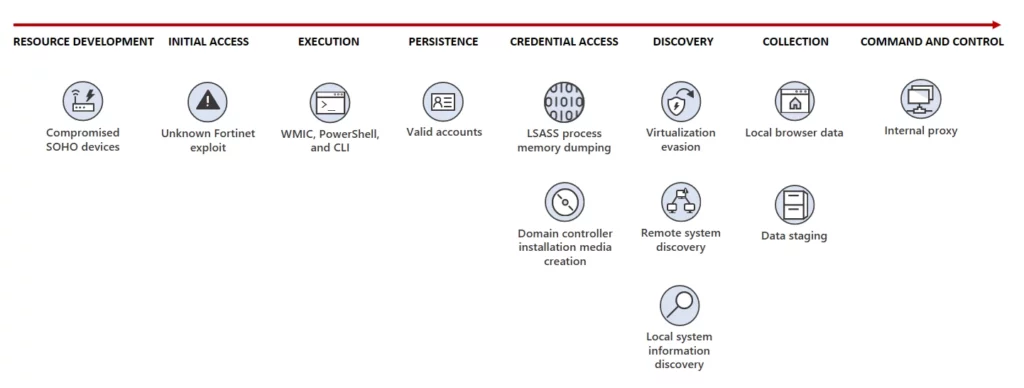
Image – Volt Typhoon attack diagram (Credit – Microsoft Security)
- Initial Access – The Volt Typhoon threat actors were observed gaining access to targeted organizations through internet-facing FortiGuard tools. Stolen credentials were then leveraged to authenticate to other devices on the network
- Post-Compromise Activity – Once Volt Typhoon gains access to a target environment, they begin conducting hands-on-keyboard activity via the command line. Some of these commands appear to be exploratory or experimental, as the operators adjust and repeat them multiple times.
- Credential Access – Stolen credentials are dumped through the Local Security Authority Subsystem Service (LSASS). These credentials can be used to re-establish access to the compromised organization.
- Discovery – Threat actors were observed discovering system information, including file system types; drive names, size, and free space; running processes; and open networks.
- Collection – Volt Typhoon dumps information from local web browser applications and staging collected data in password-protected archives.
- Command and Control – Volt Typhoon accesses compromised systems by signing in with valid credentials or in some cases by creating proxies on the compromised systems to allow access. In rare cases, custom versions of open-source tools Impacket and Fast Reverse Proxy (FRP) to establish a C2 channel over proxy were also observed being used.
Important Note for SafeBreach Customers – Coverage for AA23-144A (Volt Typhoon)
As soon as details were made available, the SafeBreach Labs teams mapped existing attacks and added new attacks to the Hacker’s Playbook immediately. It is important to note that existing SafeBreach customers already had a certain degree of coverage against some of the behavioral attacks being leveraged by the Volt Typhoon group. Please run/ re-run the attacks listed below to ensure your environments are protected against this threat actor.
Existing and Updated Behavioral Attacks
- #264 – Remote Control using Meterpreter to Execute File Commands
- #6372 – Modify Volume Shadow Copy (VSS)
- #6817 – Extract credentials from ntds.dit file using volume shadow copy
- #6910 – RDP Tunneling
- #7169 – Dump the SAM database from the registry (Windows)
- #7172 – Spawn a hidden Powershell process
- #7222 – Password Spraying
- #7223 – NTDS.dit dump using ntdsutil
- #7554 – Clear Windows Event Logs
- #8309 – Collect credentials from KeePass password manager
- #8336 – Extract Credentials Using Invoke-WCMDump
- #1693 – Collect Windows system data using CMD
Newly Added IOC-Based Attacks
- Fast Reverse Proxy
- #8878 – Write Fast Reverse Proxy hacktool to disk
- #8879 – Pre-execution phase of Fast Reverse Proxy hacktool (Windows)
- #8880 – Transfer of Fast Reverse Proxy hacktool over HTTP/S
- #8881 – Transfer of Fast Reverse Proxy hacktool over HTTP/S
- #8882 – Email Fast Reverse Proxy hacktool as a ZIP attachment
- #8883 – Email Fast Reverse Proxy hacktool as a ZIP attachment
- RemoteExec
- #8884 – Write RemoteExec trojan to disk
- #8885 – Pre-execution phase of RemoteExec trojan (Windows)
- #8886 – Transfer of RemoteExec trojan over HTTP/S
- #8887 – Transfer of RemoteExec trojan over HTTP/S
- #8888 – Email RemoteExec trojan as a ZIP attachment
- #8889 – Email RemoteExec trojan as a ZIP attachment
Newly Added Behavioral Attacks
- #8890 – Dump Active Directory data using ldifde
What You Should Do Now
The playbook has been updated with attacks that map to the IOCs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
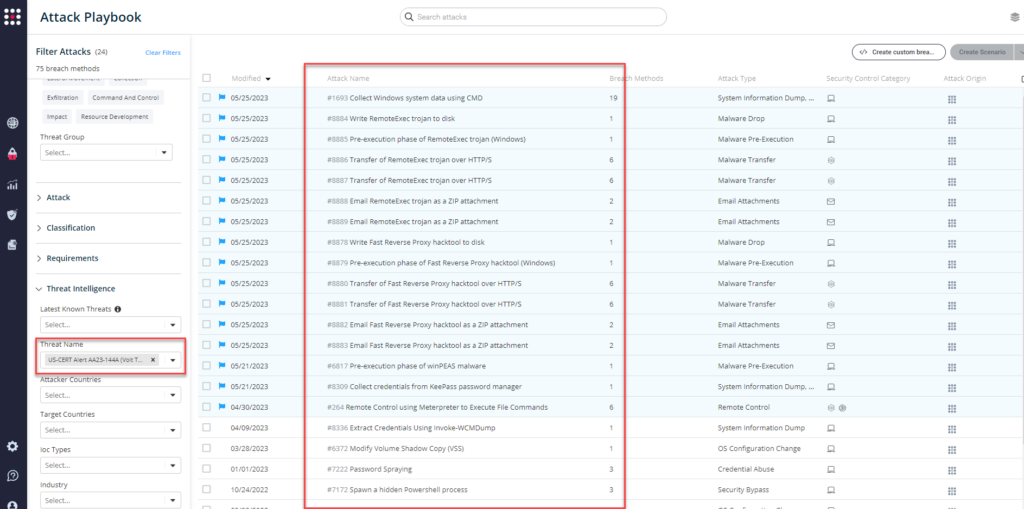
From the Attack Playbook, select and filter attacks related to US-CERT Alert AA23-144A. Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
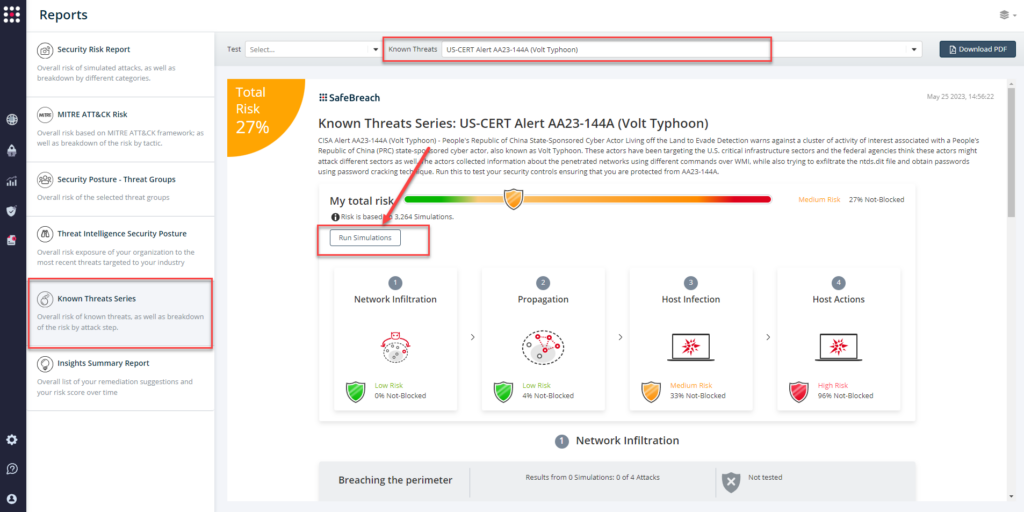
From the Known Attack Series report, select the AA23-144A (Volt Typhoon) report and select Run Simulations which will run all attack methods.
You can also go to “SafeBreach Scenarios” page and choose the AA23-144A (Volt Typhoon) scenario from the list of available scenarios.
NOTE: CISA recommends continually validating your security program, at scale, in a production environment to ensure optimal performance against the growing threat of advanced cyber threats. Additional recommendations include:
- Defenders should harden domain controllers and monitor event logs for ntdsutil.exe and similar process creations.
- Administrators should limit port proxy usage within environments and only enable them for the period of time in which they are required.
- Defenders should investigate unusual IP addresses and ports in command lines, registry entries, and firewall logs to identify other hosts that are potentially involved in actor actions.
- Defenders should review perimeter firewall configurations for unauthorized changes and/or entries that may permit external connections to internal hosts.
- Defenders should also look for abnormal account activity, such as logons outside of normal working hours and impossible time-and-distance logons.
- For detailed information about mitigations and incident response, please refer to the full advisory

