On June 23rd, the Cybersecurity and Infrastructure Security Agency (CISA) and the United States Coast Guard Cyber Command (CGCYBER) issued a joint advisory highlighting the ongoing exploitation of CVE-2021-44228 (Log4Shell) by several threat actors, including state-sponsored Advanced Persistent Threat (APT) groups. These actors are exploiting CVE-2021-44228 on VMware Horizon® and Unified Access Gateway (UAG) servers to obtain initial access to organizations that did not apply available patches or workarounds. Additional details about this group and its associated tactics, techniques, and procedures (TTPs) are available in US-CERT Alert (AA22-174A) Malicious Cyber Actors Continue to Exploit Log4Shell in VMware Horizon Systems.
According to the information released, multiple threat actors have continued to exploit Log4Shell on unpatched, public-facing VMware Horizon and UAG servers since December 2021. These threat actors implanted loader malware on compromised systems with embedded executables enabling remote command and control (C2). In one confirmed compromise, these APT actors were able to move laterally inside the network, gain access to a disaster recovery network, and collect and exfiltrate sensitive data.
Additional Details of the CISA/CGCYBER Investigation
Log4j is maintained by the Apache Software Foundation (ASF) but the open-source component is used in a broad array of software on devices from many other vendors, including VMware, Cisco, IBM, and Oracle. The Log4Shell vulnerability was considered difficult to patch due to the range of end-user organizations, device manufacturers, and services affected by it.
After the vulnerability and its seriousness were first discovered in December 2021, CISA and CGCYBER conducted investigations at victim networks that showed attackers were using the vulnerability for more than installing “cryptojackers” or CPU-abusing crypto-mining malware.
At one of the victims using a vulnerable version of VMware Horizon, the attackers had installed malware impersonating Microsoft’s software for admins. At a second victim, the attackers first gained access to the VMware Horizon server and then used the Windows Remote Desktop Protocol (RDP) to gain access to hosts in the target’s production environment, including a security management server, a certificate server, a database containing sensitive law enforcement data, and a mail relay server. The attackers at the second victim site also used RDP to access the disaster recovery network. According to CISA, the threat actors gained credentials for multiple accounts, including admin accounts.
IMPORTANT NOTE for SafeBreach Customers – Coverage for AA22-174A
As soon as details and IOCs for the ongoing exploitation of the Log4Shell vulnerability were made available, corresponding attacks were immediately added to the SafeBreach Hacker’s Playbook™ on June 24th. Additionally, since threat actors have been leveraging the Log4Shell vulnerability to gain unauthorized access since December 2021, we recommend SafeBreach customers test their preparedness by running the newly discovered attacks and those previously covered in US-CERT AA21-356A.
12 newly added playbook methods for AA22-174A:
- #7153 – Pre-execution phase of XMRIG Cryptominer malware (Host-Level)
- #7154 – Write XMRIG Cryptominer malware to disk (Host-Level)
- #7155 – Transfer of XMRIG Cryptominer malware over HTTP/S (Lateral Movement)
- #7156 – Transfer of XMRIG Cryptominer malware over HTTP/S (Infiltration)
- #7157 – Email XMRIG Cryptominer malware as a ZIP attachment (Lateral Movement)
- #7158 – Email XMRIG Cryptominer malware as a ZIP attachment (Infiltration)
- #7159 – Pre-execution phase of XMRIG Cryptominer-2 malware (Host-Level)
- #7160 – Write XMRIG Cryptominer-2 malware to disk (Host-Level)
- #7161 – Transfer of XMRIG Cryptominer-2 malware over HTTP/S (Lateral Movement)
- #7162 – Transfer of XMRIG Cryptominer-2 malware over HTTP/S (Infiltration)
- #7163 – Email XMRIG Cryptominer-2 malware as a ZIP attachment (Lateral Movement)
- #7164 – Email XMRIG Cryptominer-2 malware as a ZIP attachment (Infiltration)
11 previously available playbook attacks for Log4Shell Vulnerability:
- #6861 – Remote exploitation of Apache Log4j vulnerability CVE-2021-44228
- #6844 – Communication with server vulnerable to CVE-2021-44228 (log4j) using HTTP/s
- #6856 – Obfuscated communication with server vulnerable to CVE-2021-44228 (log4j) using
- #6858 – Communication with server vulnerable to CVE-2021-45105 (log4j2) using HTTP/s
- #6860 – Communication with server vulnerable to CVE-2021-45046 (log4j) using HTTP/s
- #6909 – RDP Connection Between 2 Simulators
- #6845 – Remote exploitation of Apache Log4j vulnerability CVE-2021-44228
- #6857 – Obfuscated remote exploitation of Apache Log4j vulnerability CVE-2021-44228
- #6843 – Communication with a real malicious server exploiting CVE-2021-44228 (log4j) using
- #6473 – Agentless lateral movement via RDP
- #109 – Covert data asset exfiltration using HTTP/s GET
What you should do now
Attack methods related to US-CERT Alert AA22-174A are ready to run across your simulators. The Known Attack Series report has been updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT Alert AA22-174A (Exploit Log4Shell in VMware Horizon Systems) report and select Run Simulations which will run all attack methods.
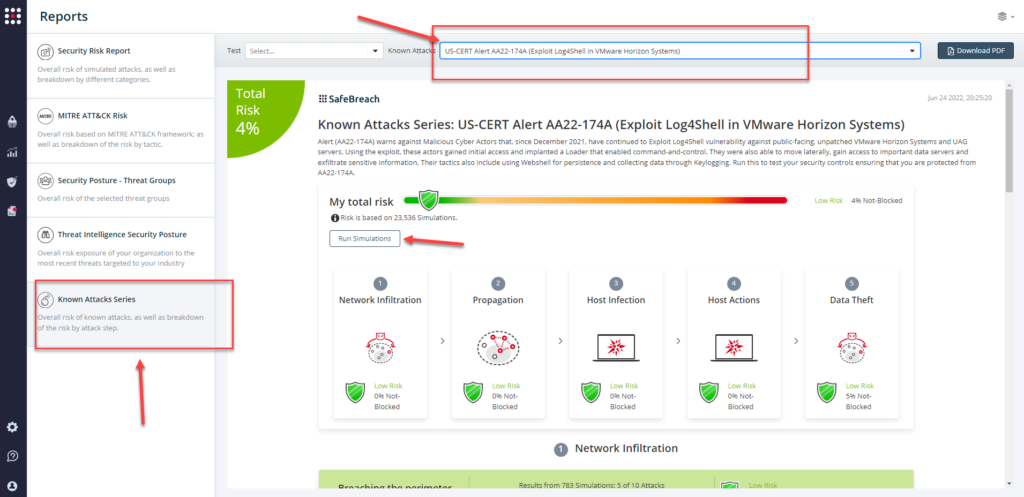
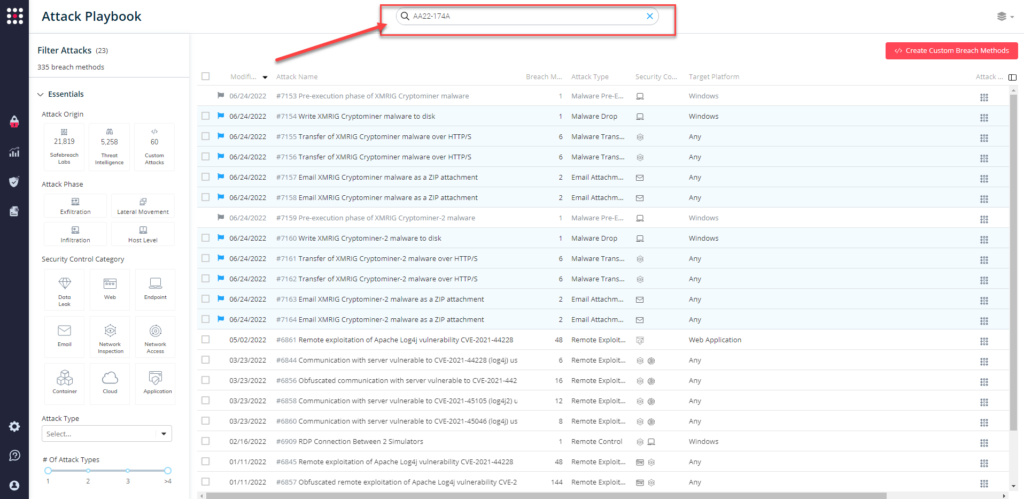
You can also select all the attacks related to US-CERT Alert AA22-174A by going to the SafeBreach Playbook and filtering by Threat Name – US-CERT Alert AA22-174A (Exploit Log4Shell in VMware Horizon Systems)
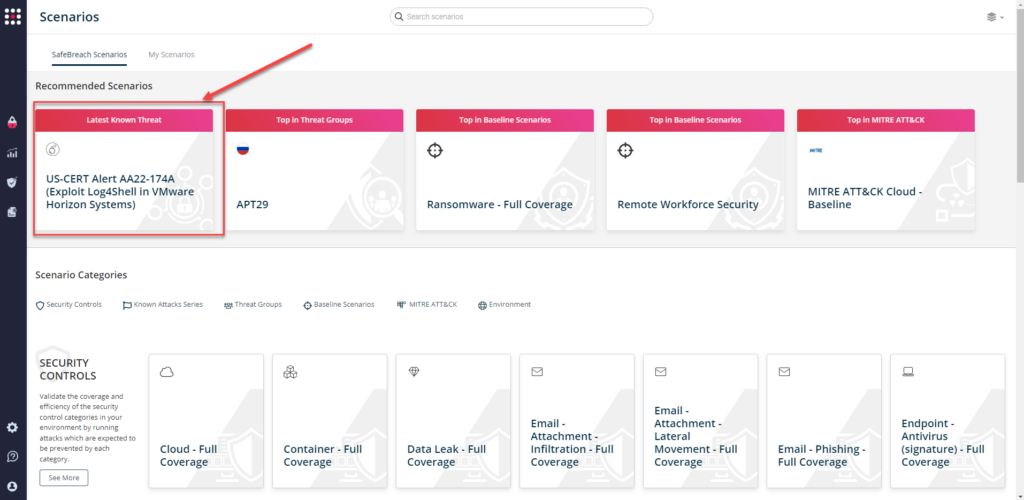
or you can go to “SafeBreach Scenarios” page and choose the US-CERT Alert AA22-174A (Exploit Log4Shell in VMware Horizon Systems) scenario from the list of available scenarios.
NOTE – The following actions have been recommended by CISA and CGCYBER to mitigate any threat to your unpatched VMware Horizon/UAG systems:
- Install fixed builds, updating all affected VMware Horizon and UAG systems to the latest versions. If updates or workarounds were not promptly applied following VMware’s release of updates for Log4Shell in December 2021, treat all affected VMware systems as compromised.
- Minimize the internet-facing attack surface by hosting essential services on a segregated demilitarized (DMZ) zone, ensuring strict network perimeter access controls, and implementing regularly updated web application firewalls (WAFs) in front of public-facing services