The recent Cisco breach reminded us that no matter how much you spend on security, you can’t always control what might happen next. Cisco is a multi-billion-dollar consultancy and technology conglomerate, and cyber criminals gained access to their domain controllers through stolen employee credentials after hijacking the employee’s personal Google account containing credentials synced from their browser.
If the Cisco story tells us anything, it is that any company can be breached, and oftentimes it is through the simplest of breach methods.
The Good News: We All Can Learn & Even Prepare
Thank you, Cisco, for being responsible and not only communicating the breach but providing a thorough back-door analysis and summary of the post-compromise tactics, techniques, and procedures (TTPs). By having access to the TTPs, we were enabled to build the attacks that support our customers.
That is why SafeBreach is the first and only breach and attack simulation (BAS) provider to develop the actual breach methods used by the Cisco attackers and are making these available in our platform to test in your environment.
Today, through the end of August, we are helping our customers by offering unlimited licenses to deploy as many simulators as they wish to test against the Cisco attack breach methods—at no cost. We will also extend complimentary SafeBreach-as-a-Service, a fully managed software solution that combines platform licenses with ongoing strategy and support from our elite team of breach and attack experts to help you run these attacks.
And for those who are not SafeBreach customers, we will run a customized, no-cost attack scenario based on actual ransomware behavior—including MITRE ATT&CK TTPs of today’s most prolific ransomware gangs—to help you gain unparalleled visibility into how your security ecosystem responds at each stage of the defense process.
ICYMI: A Breakdown of What Happened in the Cisco Breach
The Cisco breach, which was outlined in this recent blog post, was initiated through social engineering when a Cisco employee’s credentials were compromised after an attacker gained control of a personal Google account. The attacker then pretended to be trusted organizations during phone calls with the employee and successfully persuaded the employee to accept a multifactor push authentication notification to their device. That allowed the hacker to gain access to Cisco’s network using the employee’s credentials.
The attacker convinced the Cisco employee to accept multi-factor authentication (MFA) push notifications through MFA fatigue and a series of sophisticated voice phishing attacks initiated by the Yanluowang gang that impersonated trusted support organizations.
MFA fatigue is an attack tactic where threat actors send a constant stream of multi-factor authentication requests to annoy a target in the hopes that they will finally accept one to stop them from being generated. The threat actors finally tricked the victim into accepting one of the MFA notifications and gained access to the VPN in the context of the targeted user.
Once they gained a foothold on the company’s corporate network, the attack operators spread laterally into the Citrix environment, compromising a series of Citrix servers, and eventually obtained privileged access to a domain controller. Even though this was the result of social engineering, BAS providers are particularly well-suited to validate security controls across an array of TTPs by running breach and attack simulations.
It Might Have Been a Nation-State Attack, but the Technique Is One We All Know
The breach was conducted by an adversary that has been previously identified as an initial access broker (IAB) with ties to the UNC2447 cybercrime gain, Lapsus$ threat actor group, and Yanluowang ransomware operators.
Based upon artifacts obtained, TTPs identified, infrastructure used, and a thorough analysis of the backdoor utilized in this breach, it was assessed with moderate to high confidence that the attack was conducted by an adversary that had been previously identified as an initial access broker (IAB) with ties to both UNC2447 and Lapsus$.
UNC2447 is a financially motivated threat actor with a nexus to Russia that has been previously observed conducting ransomware attacks and leveraging a technique known as “double extortion,” in which data is exfiltrated prior to ransomware deployment to coerce victims into paying ransom demands. Prior reporting indicates that UNC2447 has been observed operating a variety of ransomware, including FIVEHANDS, HELLOKITTY, and more.
How Simple Were The TTPs Used – Simple Can Often Be Complex
- Backdoor/ C2 Servers – The first payload was a simple backdoor that takes commands from a command and control (C2) server and executes them on the end system via the Windows Command Processor. The commands are sent in JSON blobs and are standard for a backdoor. There is a “DELETE SELF” command that removes the backdoor from the system completely. Another command, “WIPE,” instructs the backdoor to remove the last executed command from memory with the intent of negatively impacting forensic analysis on any impacted hosts.
- Malware – The malware also communicated with the C2 server via HTTP GET. Following the initial request from the infected system, the C2 server responds with a SHA256 hash. The malware also creates a file called “bdata.ini” in the malware’s current working directory that contains a value derived from the volume serial number present on the infected system. In instances where this backdoor was executed, the malware was observed running from a directory location.
The attacker was frequently observed staging tooling in directory locations under the public user profile on systems from which they were operating.
Based upon analysis of C2 infrastructure associated with this backdoor, Cisco assessed that the C2 server was set up specifically for this attack.
According to the Cisco blog, some of the other TTPs used:
- Vishing and MFA Push Notifications – After obtaining the user’s credentials, the attacker attempted to bypass MFA using a variety of techniques, including voice phishing (aka “vishing”) and MFA fatigue, the process of sending a high volume of push requests to the target’s mobile device until the user accepts, either accidentally or simply to attempt to silence the repeated push notifications they are receiving.
- New devices for MFA and authentication to VPN – Once the attacker had obtained initial access, they enrolled a series of new devices for MFA and authenticated successfully to the Cisco VPN. The attacker then escalated to administrative privileges, allowing them to login to multiple systems, which alerted the Cisco Security Incident Response Team (CSIRT), who subsequently responded to the incident. The actor in question dropped a variety of tools, including remote access tools like LogMeIn and TeamViewer, offensive security tools such as Cobalt Strike, PowerSploit, Mimikatz, and Impacket, and added their own backdoor accounts and persistence mechanisms.
- Lateral movement via built-in Windows utilities – Once on a system, the threat actor began to enumerate the environment, using common built-in Windows utilities to identify the user and group membership configuration of the system, hostname, and identify the context of the user account under which they were operating.
- Compromised user account for lateral movement to domain controllers – After establishing access to the VPN, the attacker then began to use the compromised user account to log on to a large number of systems before beginning to move laterally into the environment. They moved into the Citrix environment, compromising a series of Citrix servers, and eventually obtained privileged access to domain controllers.
- Creation of administrator user using Windows commands – After obtaining access to credential databases, the adversary created an administrative user called “z” on the system using the built-in Windows “net.exe” commands. This account was then added to the local Administrators group. The threat actor changed the password of existing local user accounts with the creation of the “z” account by this actor which has been observed in previous engagements prior to the Russian invasion of Ukraine.
- Further lateral movement to access directory services and obtain additional credentials – The ‘z’ account was then used in some cases to execute additional utilities, such as adfind or secretsdump, to attempt to enumerate the directory services environment and obtain additional credentials. Additionally, the threat actor was observed attempting to extract registry information, including the SAM database on compromised windows hosts.
- Leveraging Remote Desktop Protocol – To move files between systems within the environment, the threat actor often leveraged remote desktop protocol (RDP) and Citrix and modifyi the host-based firewall configurations to enable RDP access to systems.
- Leverage Windows logon bypass techniques – The attacker frequently leveraged Windows logon bypass techniques to maintain the ability to access systems in the environment with elevated privileges. This enabled the attacker to leverage the accessibility features present on the Windows logon screen to spawn a SYSTEM level command prompt, granting them complete control of the systems.
After obtaining initial access, the threat actor conducted a variety of activities to maintain access, minimize forensic artifacts, and increase their level of access to systems within the environment. Ultimately, Cisco detected and evicted the attackers from its environment, but they continued trying to regain access over the following weeks.
To help network admins and security professionals detect the malware used in the attack, Cisco created two new ClamAV detections for the backdoor and a Windows exploit used for privilege elevation.
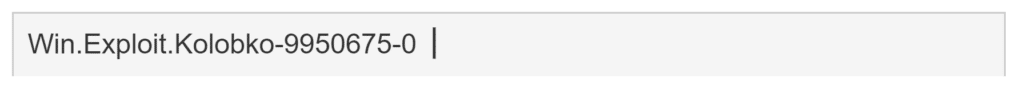

While Cisco provided some information on the backdoor and how it was used to remotely execute commands, their writeup does not mention any info on the exploit executable that was discovered.
However, according to detections on VirusTotal, the exploit is for CVE-2022-24521, a Windows Common Log File System Driver Elevation of Privilege vulnerability, reported by the NSA and CrowdStrike to Microsoft and patched in April 2022.
Test the Cisco Breach Methods in Your Environment Today
Over the next few days, we will continue to keep you updated. In the meantime, SafeBreach customers can run these attacks in their system and/or reach out to customer support for assistance on which attacks to run.
If all companies were as responsible as Cisco, instead of making empty statements to the media, these types of shared data would advance our industry to help meet the increasing threat landscape we find ourselves in today.