
The SafeBreach Labs team is committed to conducting original research to uncover new threats and ensure our Hacker’s Playbook provides the most comprehensive collection of attacks. As part of this ongoing research, our team recently discovered vulnerabilities in various endpoint detection and response (EDR) products that allow adversaries to remotely erase critical files and databases without authentication that could lead to potential data loss, denial of service (DoS), and significant security risks. We believe the ten attack vectors we discovered are the tip of the iceberg and, since Microsoft Defender is embedded in multiple critical points in many cloud vendors, the impact of these vulnerabilities could be significant and far reaching.
We first presented this research at Black Hat USA 2023 and are sharing it with the broader security community in this post. Below, we will provide a high-level overview of the previous SafeBreach Labs research that served as the foundation for our latest discovery. We will then explain our research process that uncovered a method for remote deletion of both user and operating system (OS) files leveraging leading EDRs. Finally, we will highlight the vendor response and identify how SafeBreach is sharing this information with the broader security community to help organizations protect themselves.
Background
Our research journey began with a critical finding by one of our team members, Or Yair, who identified multiple zero-day vulnerabilities in several major EDRs in his Aikido Wiper Research presented at Black Hat Europe 2022. In this research, Or identified that it was possible to delete the wrong file by exploiting a time-of-check to time-of-use (TOC/TOU) vulnerability. This resulted in a total deletion of all users and OS files after a certain period.
Building on this initial discovery, we conducted a secondary research effort to identify vulnerabilities for remote deletion of critical files through the same EDR products. The central question we asked ourselves was:
Is it possible to trick EDRs into deleting legitimate files?
The Research Process
During our investigation, we successfully identified multiple attack vectors—including inserting minimal malicious signatures into web server logs, email clients, Windows event logs, and databases—that triggered EDR products to automatically delete files or databases without authentication, resulting in a DoS condition. Below, we provide a high-level overview of each of the steps in our research process that led to these discoveries.
Develop Minimal Signature to Trigger File Deletion
Our first goal was to find a minimal signature that triggered automatic deletion when appended to an empty file. To start, we focused on Microsoft Defender, which is the default EDR installed on hundreds of millions of Windows agents and servers. After a significant amount of trial and error, we were able to minimize a malicious file to a 15 character signature, mainly using non-alphanumeric characters, that successfully triggered Microsoft Defender to automatically delete a file’s content.
Locally Trigger File Deletion
Next, we used trial and error to identify the sections of a legitimate file where the malicious signature could be appended. We focused on non-executable files, since they are intended to be modified and more easily allowed us to insert our malicious signature. When we manually embedded the malicious signature into a non-executable file, we were able to locally trigger an automatic deletion of that file by Microsoft Defender.
Remotely Trigger File Deletion on Windows Server
To enable a remote attack, we needed a way for a privileged service to write our signature to a remote file. As one example, we used an HTTP request to send our malicious signature to a Windows-based web server, exploiting the user agent field in IIS logs to include our signature. This triggered Microsoft Defender, which was installed on the web server, to delete the log file.
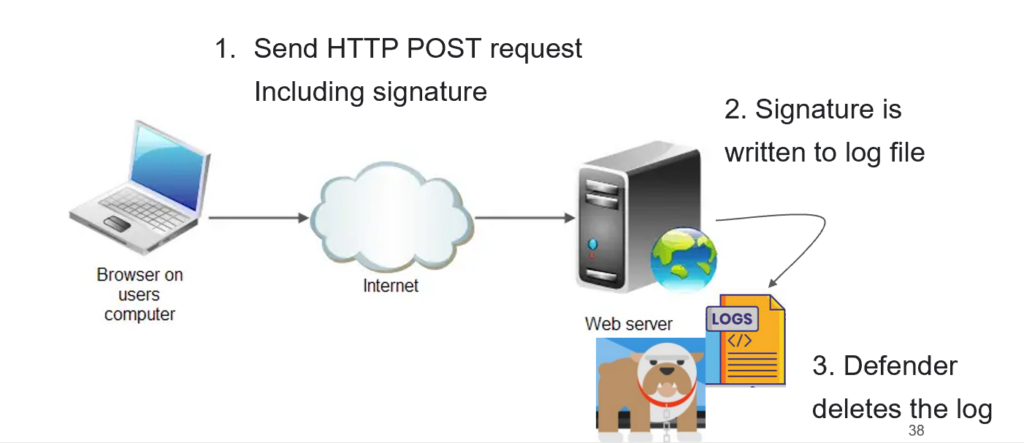
Remotely Trigger File Deletion on Linux Server
Since many web servers run on Linux, we wanted to explore this platform too. Linux servers typically do not have built-in EDR solutions, so we focused on triggering other EDR products commonly installed on Linux web servers. This included AVG, Avast, TrendMicro, CrowdStrike, Palo Alto Cortex XDR, SentinelOne, and Kaspersky.
We discovered that different EDR products exhibited varying behaviors. For example, AVG and Avast only scanned files with specific extensions, limiting the number of files that could be infected with our malicious signature. Another example was Trend Micro, which only worked if the signature was present at offset zero in the target file, reducing our attack possibilities. Additionally, EDR solutions that utilize machine learning algorithms, such as CrowdStrike, Falcon, Palo Alto Cortex XDR, and SentinelOne, were not vulnerable to our attack vector. Eventually, we found that Kaspersky Endpoint Detection and Response for Linux suited our needs perfectly. We were able to trigger both Kaspersky and Microsoft Defender with the same signature, making it an ideal signature for testing web servers.
Remotely Trigger Database Deletion on Windows and Linux Servers
In our investigation, we discovered that the crown jewels of many organizations are not stored in files but rather in databases. These databases are commonly used to store sensitive and critical data. While users may not have direct privileges to insert queries into a remote database, websites often use databases in the backend, allowing users to submit data through forms or other means.
For instance, a website’s registration form might store user data in the database. This presents an opportunity for a remote attack to trigger Microsoft Defender to delete the entire production database without any authentication.
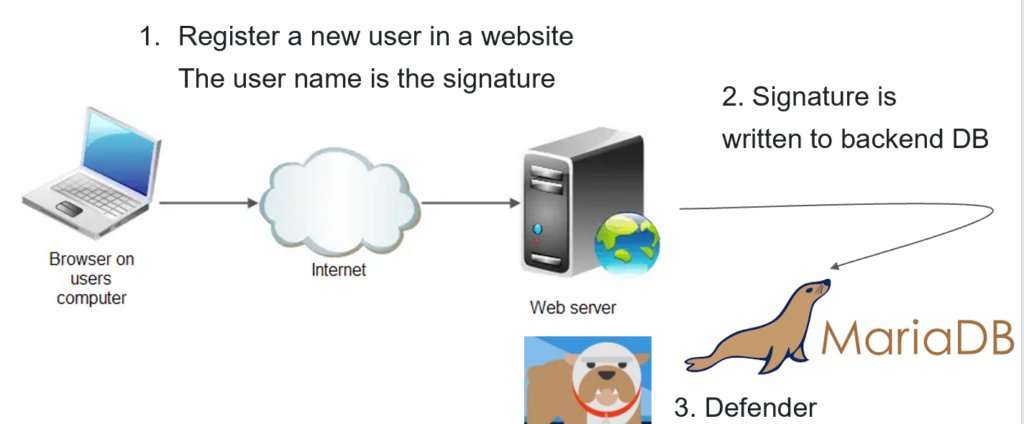
We tested the same attack on the most popular databases, including MySQL, MariaDB, Postgres, SQLite, and MongoDB, and it worked successfully on Windows systems and Linux systems with Kaspersky installed. This means that numerous major websites using these databases could potentially be vulnerable to remote deletion.
Vendor Response
After we notified Microsoft about the discovery of the vulnerability, CVE-2023-24860, they issued a fix in April. The patch fixed some of the attack vectors, including remote db deletion, but we were still able to achieve remote deletion in some of the attack vectors. We reported once again, and Microsoft decided that the remaining attack vectors were a moderate DoS and may be fixed at a later point.
Kaspersky did not release a patch; however, they indicated that they had planned improvements to mitigate the issues. Currently, all attack vectors are still possible.
Conclusion
The implications of this research are significant, as the findings show how attackers could remotely delete critical data and disrupt organizations’ operations without having direct access to their systems. To help mitigate the potential impact of these vulnerabilities, we have:
- Responsibly disclosed our research findings to the vendors of the EDR products we tested. As noted above, some patches have been released, although specific attack vectors remain unaddressed.
- Provided a research repository that includes tools that enable the verification of these vulnerabilities and serve as a basis for further research and development of new attack vectors.
- Shared our research openly with the broader security community here and at our recent Black Hat presentation to enable organizations to monitor their EDR configurations more vigilantly and stay informed about potential security updates to protect against such sophisticated attacks.
- Added original attack content to the SafeBreach platform that enables our customers to validate their EDR products against these vulnerabilities and significantly mitigate their risk.
It is important to note that while we have done our best to test the EDR products we had access to, it is not feasible for us to test every product on the market. By making this information available to the security community, we hope to minimize the ability of malicious actors to exploit these vulnerabilities and provide EDR vendors and users with the knowledge they need to take immediate action on their own.
We believe it is critical for all EDR vendors to proactively test their products against this type of vulnerability and, if necessary, develop a remediation plan to ensure they are protected. We would also strongly encourage individual organizations that currently utilize EDR products to consult with their vendors about these vulnerabilities and immediately install any software updates or patches they provide.
For more in-depth information about this research, please:
- Contact your customer success representative if you are a current SafeBreach customer
- Schedule a one-on-one discussion with a SafeBreach expert
- Contact Kesselring PR for media inquiries
About Our Researchers
Tomer Bar heads the SafeBreach Labs team. Tomer is a hands-on security researcher with over 20 years of unique cybersecurity experience. His main interests are vulnerability research, reverse engineering, and advanced persistent threat (APT) research. Among his recent discoveries are the PrintDemon vulnerabilities in the Windows Spooler mechanism, which were candidates in the best privilege escalation category of the Pwnie awards and several research studies on Iranian APT campaigns. He has presented his research at events around the world, including DEF CON (28-30), Black Hat USA, ReCon, Sector, Confidence, Security Fest, HackCon, and Troopers conferences.
Shmuel Cohen is a cybersecurity professional with a diverse background. After serving in the Israel Defense Force (IDF) for three years, he pursued a bachelor of science degree in computer science. He had the privilege of working at CheckPoint, where he developed software and worked as a malware security researcher. As his interest grew in vulnerability research, he joined the SafeBreach team, where he has been able to focus his energies on exploring and addressing vulnerabilities in cybersecurity.

