Criminals typically approach data theft with one goal in mind: to invest as little effort as possible in order to collect as much sensitive, money-generating user data as possible. Cryptocurrency wallets, banking credentials, extortion, and identity theft are just a few examples.
Towards this end, criminals can develop trojans and then build an infrastructure, including Command and Control (C2) servers, to infect victims, send commands to the malware, and store the exfiltrated data. This requires them to purchase a VPS and domain names for the C2 servers, renew them every year, and purchase a proxy to anonymize their activities. Alternatively, criminals can invest their efforts in attacking legitimate unprotected sites, like unpatched WordPress sites, and launch attacks from there. Finally, a more expensive option is for criminals to purchase malware-as-a-service (MaaS). Regardless of the option they select, this illegal activity can take time, requires money, and involves the risk of getting caught.
Instead, what if criminals were able to acquire large amounts of victims’ credentials without infecting any victim, without the need to build or purchase anything, and without the risk of getting caught? We recently set out to explore this topic and validate our theory that this type of “perfect crime” could be a new reality in cyber security.
In this blog, we’ll explain how we were able to obtain large amounts of sensitive data using Google’s VirusTotal service in combination with other known malware services and hacker forums. We will also outline the steps we’ve taken to mitigate the risk posed by the information we found, including notifying Google of these files and activities. Finally, we’ll address key steps you can take to protect yourself and your organization from this type of malicious activity.
Our Process
Our research began with VirusTotal, one of the most comprehensive malicious file storage services currently available. VirusTotal is owned by Google and provides a free service to upload suspicious files and check them using dozens of antivirus engines. It also provides extensive search capabilities for a licensed user, allowing them to query the VirusTotal dataset by a combination of dozens of queries: filetype, filename, submitted date and country and file content are just a few examples.
To test our theory, we developed the idea of “VirusTotal hacking,” based on the known method of “Google hacking.” With Google hacking, criminals use Google to search for vulnerable websites, IoTs, installed webshells, and sensitive data leaks. Because VirusTotal employs Google’s more advanced search APIs, we believed it had the potential to enable turbocharged Google hacking. Our goal was to identify the data a criminal could gather with a VirusTotal license, available for the small fee of €600.
After obtaining a VirusTotal license, we began by classifying the exfiltrated file names used by common malicious info stealers. Next, we used different VirusTotal APIs, including search, VT Graph, and Retrohunt, to search for those file names.
The results were huge. In just a few days, we were able to collect more than 1,000,000 credentials, exfiltrated by different types of malware and unencrypted cryptocurrency wallets. We also discovered a market that publishes a small amount of victims’ data for free as a teaser, with an additional site and Telegram channel that offers larger amounts of victims’ exfiltrated data for sale.
In the sections below, we provide in-depth information about how we leveraged known malware services, like RedLine Stealer, Azorult, Racoon Stealer, and Hawkeye, and known hacker forums, like DrDark and Snatch_Cloud, to uncover sensitive data that is readily available to criminals in VirusTotal.
RedLine Stealer
RedLine Stealer is a malware available for sale on underground forums as a standalone version or on a subscription basis. This malware uses browsers to harvest information like saved credentials, autocomplete data, and credit card information. It also takes a system inventory when running on a target machine that includes details like the username, location data, hardware configuration, and information regarding installed security software. More recent versions of RedLine added the ability to steal cryptocurrency. File transfer protocols (FTP) and instant message (IM) clients are also targeted by this family, and this malware has the ability to upload/download files, execute commands, and periodically send back information about the infected computer.
To start, we used VirusTotal Query to search for all binaries that were identified by at least one antivirus engine as RedLine malware: “engines:MSIL.Trojan-Stealer.Redline.B”. The query returned 800 results.
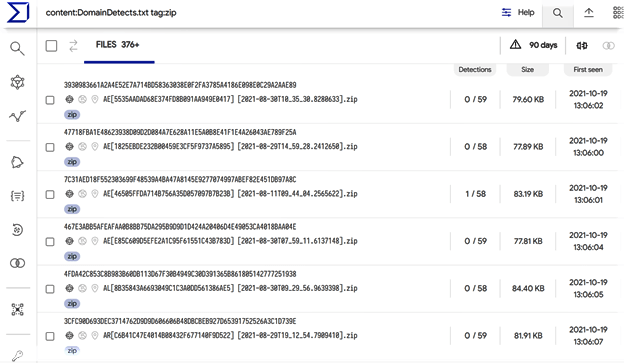
In addition, we searched for files named “DomainDetects.txt,” which is one of the filenames exfiltrated by RedLine Stealer. This query returned hundreds of exfiltrated files: “content:DomainDetects.txt tag:zip”. The exfiltrated zip files have a naming convention of country_code[victim_id][date].zip.
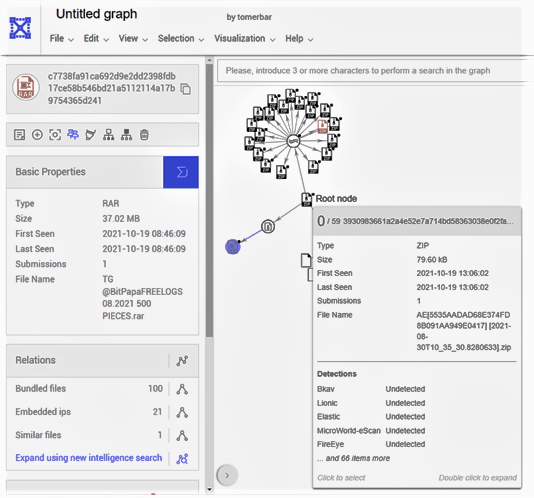
Next, we utilized VirusTotal Graph, a service for paying customers within VirusTotal that enables users to explore this huge dataset visually, discover threat commonalities, and understand the relationship between files, URLs, domains, IP addresses and other items encountered in an ongoing investigation. Pivoting intelligently over any of the malware artifacts in the graph will synthesize the findings into a threat map.
Using VirusTotal Graph, we found that the first zip file included in the search results above “3930983661a2a4e52e7a714bd58363038e0f2fa3785a4186e098e0c29a2aae89” was also included in a RAR file named “TG @BitPapaFREELOGS 08.2021 500 PIECES.rar”:
c7738fa91ca692d9e2dd2398fdb17ce58b546bd21a5112114a17b9754365d241
The RAR file contains exfiltrated data belonging to 500 victims, including 22,715 passwords to a variety of sites:

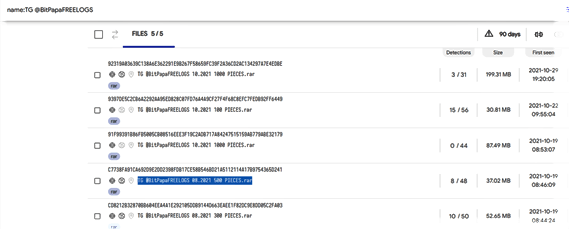
Looking at the format of the RAR file name—“TG @BitPapaFREELOGS 08.2021 500 PIECES.rar”—suggests that it was shared on purpose and not by automatic uploader or by mistake:
- “BitPapa” is the name of a cryptocurrency market site and also a Russian Telegram channel.
- “500 PIECES” is the number of victims.
We found additional results, including a file six times bigger (200 MB) with 46,952 passwords belonging to 1,000 victims when searching for similar file names. For example:
- Query: name:TG @BitPapaFREELOGSit
- We found file name “SHA256: b1473e737c7ee2849fec49b616f83f077d1a1f552e8d3139354ecb8b002da4a9” which contains 34 victims’ data, including credentials, documents and cryptocurrency from September 2021.
- The file included more than 800 passwords, 30 of which were for government-related URLs (e.g., more than 40 victims from the Ministry of Health). Below is an example of a RedLine exfiltrated password file:
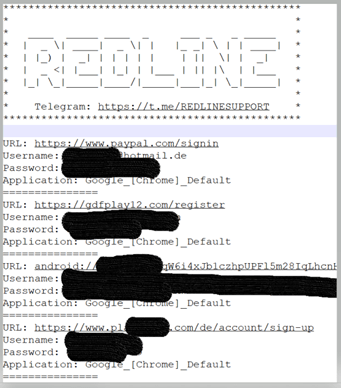
Azorult
Azorult is an information-stealing trojan and one of the most prevalent malware families. It harvests and exfiltrates credentials, browser-login data, cookies, history, chat sessions, cryptocurrency wallet files, and screen captures. It is commonly propagated via spam, either as an attachment or as a payload of a malicious document file.
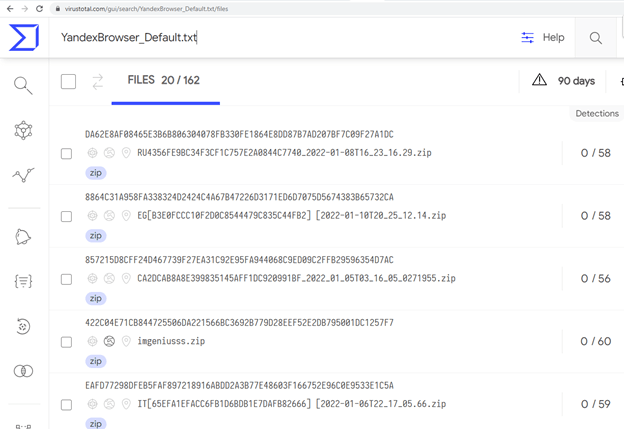
Using VirusTotal Query, we searched for “YandexBrowser_Default.txt”, which is one of the known exfiltrated file names. 162 results were returned:
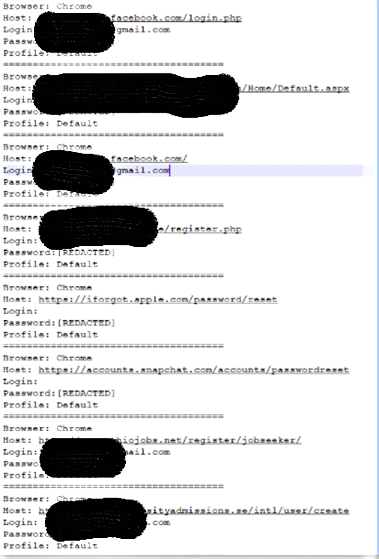
The first file includes CV files, credentials for Facebook, Apple, Snapchat, an Australian government account, and more sensitive information. Below is a sample of the file contents, with the passwords redacted:
Using VirusTotal Graph, we pivoted a single victim’s data from the zip file “75a2d5fa3c7d2defd71752bee1a938f8043b15a8d651e51ba1db31cb880f9666” for its parent zip archive.
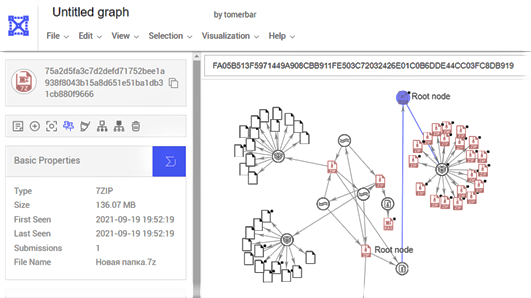
The archive file “Новая папка” from September 21, 2021, contains 1,000 victims’ data.
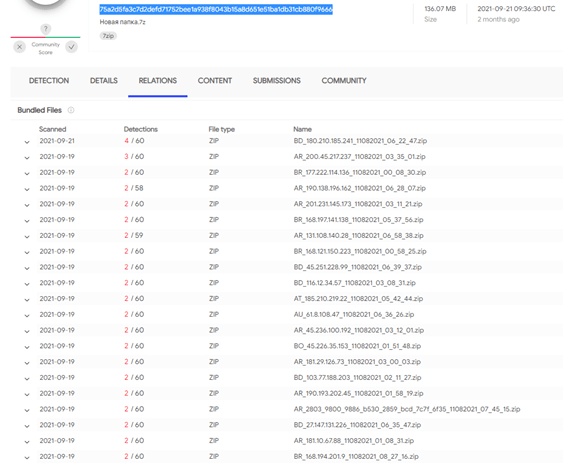
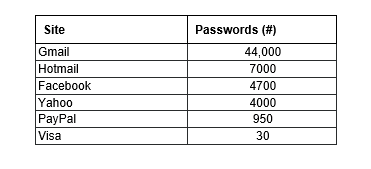
It includes 405 MB of exfiltrated data, including 136,000 passwords for a variety of systems:
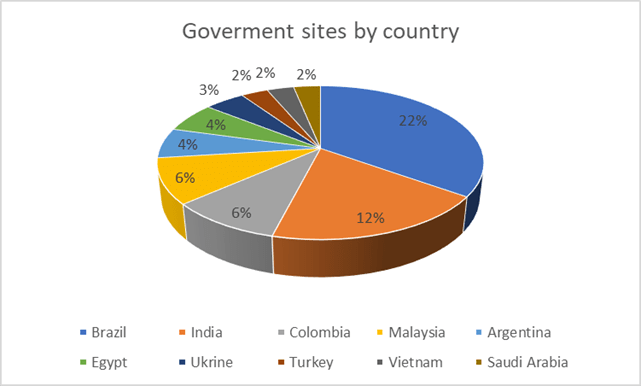
It included credentials for 1,300 government sites from 48 countries:
The file also included 30 tax-related sites like the IRS in the USA, UK, India, and other countries:
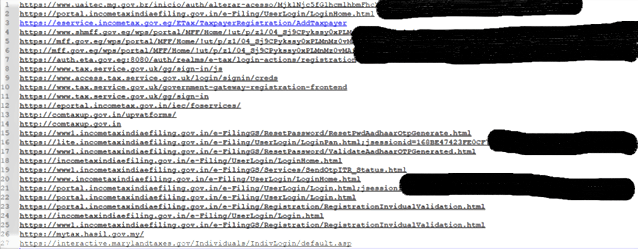
Using those credentials, an attacker would likely be able to steal even more sensitive data from sites such as:
- India’s Passport:
Racoon Stealer
Raccoon Stealer is an information stealer that supports the theft of user credentials and data stored in web browsers, mail applications, cryptocurrency wallets, and Discord files. It is believed to originate in Russia, openly advertises itself as a malware-as-a-service (MaaS) on the dark web and is well-known in cybercriminal circles. It is also one of the most well-administered and well-managed malware services.
Using VirusTotal Query, we searched for “chrome_autofill.txt.” which is a known exfiltrated filename by Racoon. The query returned 69 results.
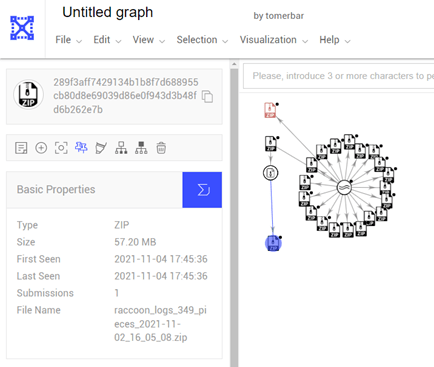
Using VirusTotal Graph, we can see that this text file is included in another zip, which is included in an even bigger ZIP file (57 MB) named “raccoon_logs_349_pieces_2021-11-02_16_05_08.zip.”
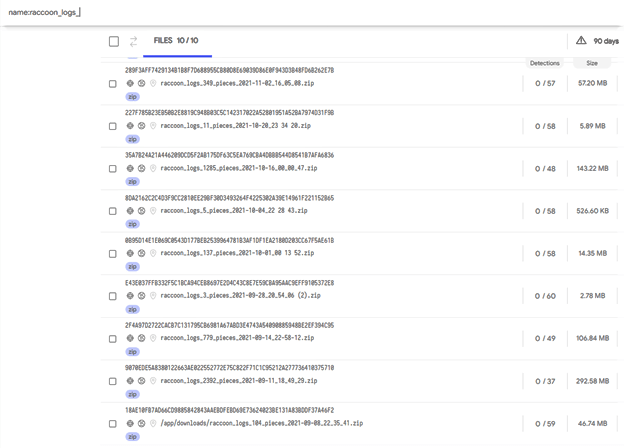
Searching for “name:raccoonlogs” (the misspelling is on purpose) provides ten results, including a file named “raccoon_logs_2392_pieces_2021-09-11_18_49_29.zip” that includes 2,392 victims.
Sha256: 9070ede5a8380122663ae022552772e75c822f71c1c95212a277736410375710
This file includes 96,000 passwords for a variety of services:
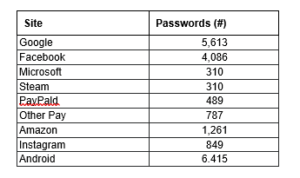
It also includes cryptocurrency wallets. For example, running the pywallet.py script reveals the private keys of the wallet:
pywallet.py –dumpwallet –wallet “.\DE 194.195.91.19 2021-09-11\wallets\BitcoinCore.dat”
This means that the private keys are encrypted.

But, other files were unencrypted, making them easier to be stolen by a criminal. For example:
pywallet.py –dumpwallet –wallet “.\JM 63.143.93.177 2021-09-11\wallets\CHOPPA CHOPPA.dat”
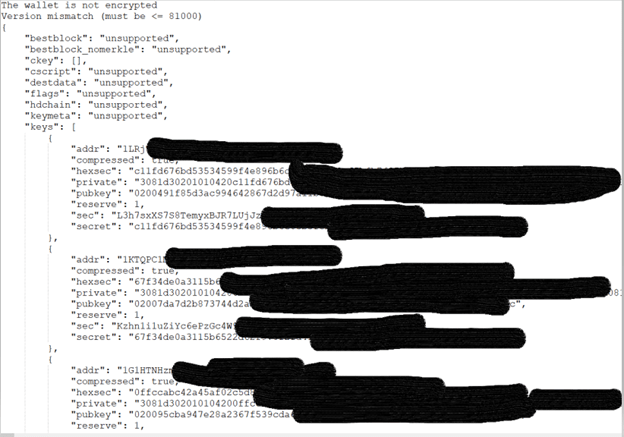
Possible Original Hacker identity – uploading a file to VirusTotal
There are two methods to upload a file to VirusTotal. One is free and open to all throughout the web interface without signing in. Another is via a logged-in user who is identified by an API key. Nine of the ten files above were uploaded using the Racoon Stealer web interface from different countries (probably using a proxy), but the last file was probably uploaded by the original hackers for publication of their “service” using API key 9c2cfa71.
![]()
This API key will be submitted to Google in a request to be banned.
Expanding the search to query for “logs.zip” tag:zip size:290000000+” returns six additional results, including a compressed file size of 556 MB with original file name “988.logs.zip” and original name:
US[C64C48406FF187D3C0D2B8B68B793AEB] [2021-10-03T20_58_19.7082173+03_00]
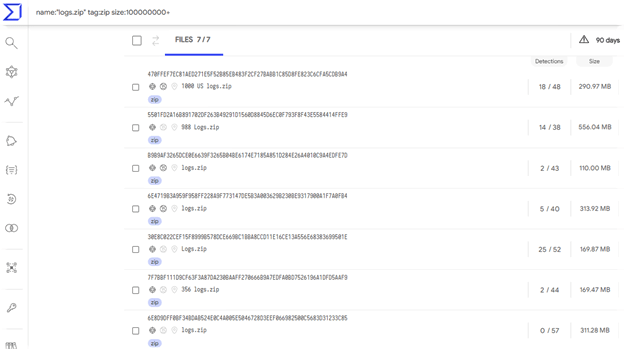
This file also included 988 RedLine malware victims. Each exfiltrated-files folder includes a text file, which reveals the original attacker group’s name: cbanke.
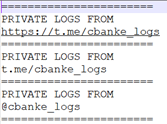
DrDark, a hacking forum used by the cbanke group, is even allowing the free download of victims’ files from a Google drive. The file name is “250 LOGS [TG @cbanke_logs].zip,” which correlates this site to the cbanke group. The file was uploaded on November 24, 2020, and includes a 287 MB ZIP file. We’ll investigate this further in the section below.
DrDark
DrDark is a known hacking forum that publicly declares its goal as follows:
“DrDark is a forum dedicated to making money on the Internet, various earning schemes, IT issues and much more. Also we share knowledge about carding forums, malware modifications, hacking, security, programming, cracking, among many other things”.
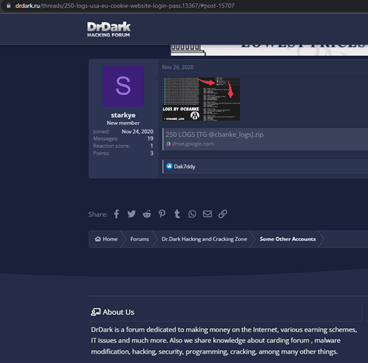
The file 250 LOGS [TG @cbanke_logs].zip, which again is included for free on DrDark, includes exfiltration data by Spyware.KpotStealer. For example: 028ec268176707aadc2cf8e65a28236cbed214f9fd65fc3346ee34e859e50057
The exfiltrated data includes the “KPOT” name and the malware indeed writes the same exfiltrated files.
The user who uploaded this file, identified as Starkye in the DrDark forum, has 19 posts offering files with similar types of sensitive data:
And there are hundreds of other users offering similar files:
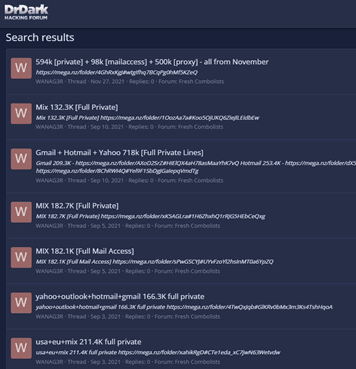
For example, a user identified as Wanag3R published 233 posts offering files with sensitive data— the type of credentials, amount, victims’ countries, etc., included in the files are outlined in the file names.
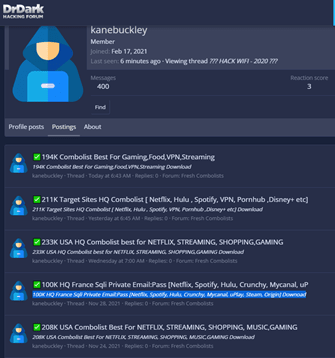
Another user, identified as kanebuckley, published 400 messages and specializes in stolen credentials for Netflix and gaming.
These activities are carried out on the regular web. There is no need for dark web access—these individuals are not hiding themselves.
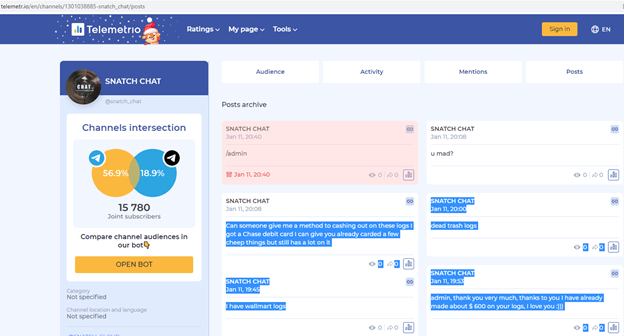
Snatch_Cloud Group
Using VirusTotal Query, we searched for “name:logs tag:zip” which is a known exfiltrated filename by Snatch_Cloud Group. Our query returned 1,000 results, one of which was a 265 MB file that was recently uploaded with an interesting file name:
“1000 US logs.zip.”
470FFEF7EC81AED271E5F52B85EB483F2CF27BABB1C85D8FE823C6CFA5CDB9A4
This is also a RedLine exfiltration. Each exfiltrated-files folder includes a text file:
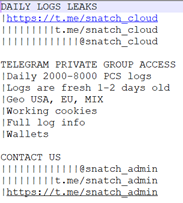
This site sells victims’ exfiltrated files, totaling 422,000 files between June and August 2021 and over 70,000 in September 2021 alone. That is an average of 2,000-8,000 daily PCS.
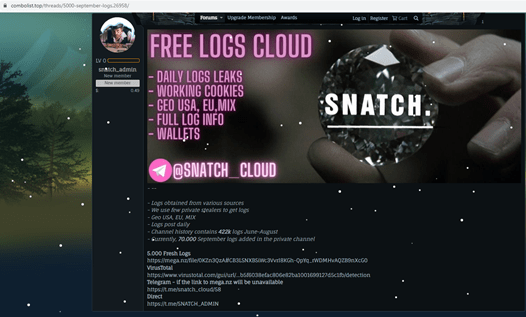
They provided a link to VirusTotal, which was uploaded from Russia and leads to https://mega.nz/file/0KZn3QzA, which requests a password to access the files. In the end, criminals don’t even need VirusTotal—they can purchase access to victims’ files directly.
The group’s Telegram site, which has approximately 500 participants, provides instructions about how to cash out money and displays messages from users thanking the administrator for all the money they have made.
HawkEye
HawKeye is a highly used keylogger that has been distributed since 2013. It is currently spread over phishing campaigns targeting businesses on a worldwide scale and is designed to steal credentials from numerous applications. It is sold by its development team on dark web markets and hacking forums.
Sometimes searching for already-exfiltrated files is not enough and a little more effort is needed. In this HawkEye example, we explore how criminals can search for malware, which uses simple protocols to exfiltrate the data. The credentials are exfiltrated using SMTP or FTP. The malware connects to the C2 FTP server using the username and password, so a criminal who has them can access them as if they were the original hacker.
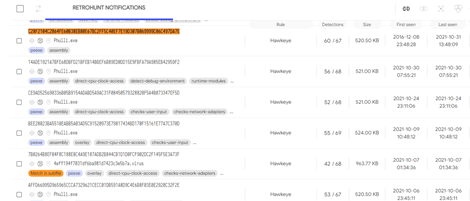
Using Retrohunt, a service provided within VirusTotal, anyone can search for all binaries that match a YARA rule signature in the last 90 days. We added a YARA rule to detect all HawkEye malware binaries (any attacker could use the YARA rule provided by VirusTotal, which includes 12000 shared rules):

The Retrohunt search returned 82 results in the last 90 days and an additional 265 beyond 90 days, which required a paid license to access.
Let’s look at one of them:
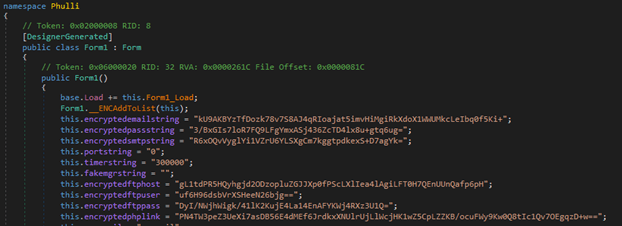
Using Dnspy to decompile revealed the following encrypted setting:
An attacker could decrypt this without writing any code using .Net Fiddle, an online environment that allows you to write, test, and share code.
By copying the encrypted strings to the template code and hitting run, it’s possible to get the FTP host, username, and password.
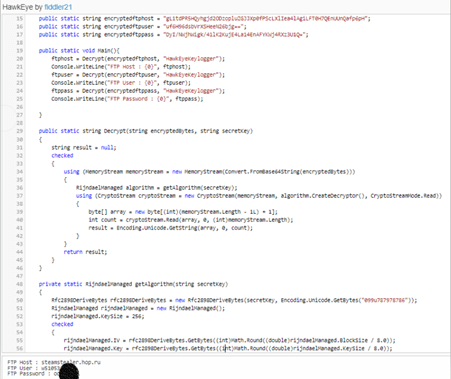
At this point, an attacker would be able to use the original attacker’s credentials and download all the victim’s exfiltrated data. In this example, 200 victims could have been hit.
Conclusion
In this article, we proved that the “VirusTotal hacking” method works at scale. A criminal who uses this method can gather an almost unlimited number of credentials and other user-sensitive data with very little effort in a short period of time using an infection-free approach. We called it the perfect cyber crime, not just due to the fact that there is no risk and the effort is very low, but also due to the inability of victims to protect themselves from this type of activity. After victims are hacked by the original hacker, most have little visibility into what sensitive information is uploaded and stored in VirusTotal and other forums.
The goal of releasing this post was to raise awareness about this issue, encourage the vendors of such repositories to help mitigate these types of activities, and decrease the overall risk posture. Below are the steps we have taken to achieve this goal:
- We informed Google in advance about our findings and requested that they remove the files from VirusTotal. After a month, we got this response from Google:
“Thanks for the samples reported and the recommendations, but unfortunately eight reported files are still available.” - Additionally, we provided the following recommendations to Google:
- Periodically search and remove files with sensitive user data and ban API keys that upload those files.
- Add an algorithm that disallows uploads of files with sensitive data that contain cleartext or encrypted files with the decryption password attached textually or by image.
- We also recommend that law enforcement consider tactics to address illegal forums and marketplaces where criminals sell and buy sensitive information.
- Regarding the last method of using malware that connects to C2 servers in unsecured protocols, we recommend that vendors cooperate with hosting companies to sinkhole or terminate affected C2 servers.
While mitigation efforts for the “VirusTotal hacking” method must primarily be completed by the vendors of repositories like VirusTotal, there are key steps every organization can take to prevent their information from being compromised, including:
- Implementing multi-factor authentication.
- Using strong, unique passwords that are changed periodically.
- Implementing network segmentation and traffic filtering.
- Scanning for vulnerabilities and keeping software updated.
- Removing unnecessary applications and applying controls.
- Implementing endpoint detection response (EDR) and data loss prevention (DLP) tools.
- Limiting access to resources over the network, especially by restricting remote desktop protocol (RDP).