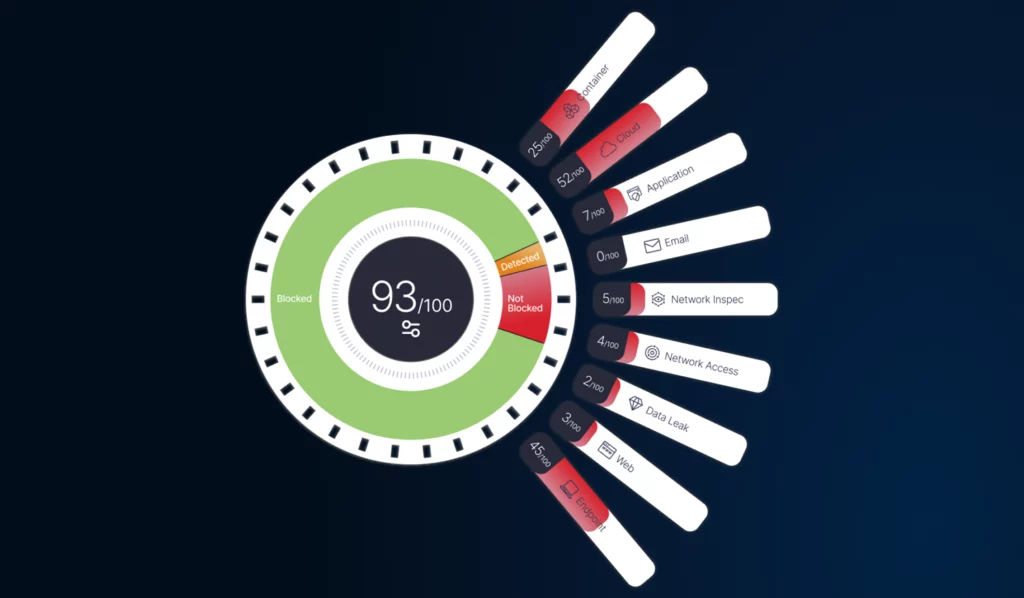
Configure Wisely
%
Protection-Coverage Improvement
Operate Efficiently
%
Savings on Red Team Exercises
Risk Less
%
Risk-Posture Reduction
Discover the SafeBreach Difference

The Only True Enterprise-Ready Platform
From out of the box scenarios to customization, we offer the speed, scale and stability to support you through business transformation.

Redefining Actionable Intelligence
Our world-renowned research team actively ensures SafeBreach has coverage for relevant attacks. We’ve built the largest attack playbook, backed by a 24-hr SLA for adding newly identified attacks from US-CERT and critical alerts.

Fastest Time to Value
We are the only BAS company offering high touch support, training and services, allowing you to optimize your threat management program and get results 24x faster.
Resources to Help You Plan For the Unknown
Because you don’t know what you don’t know. Until you do.

“Just because we have controls in place doesn’t mean they’re working, and our security posture is changing all the time. A mistaken configuration change in a VPN service could open up a new vulnerability at any time. That’s why it’s so vital to continuously validate our tools and overall security posture.”
– CISO, Fortune 500 Healthcare Provider