Introduction
SafeBreach Labs discovered a vulnerability in Avira Antivirus 2019 software.
In this post, we will demonstrate how the CVE-2019-17449 vulnerability could have been used in order to achieve defense evasion, persistence and privilege escalation by loading an arbitrary unsigned DLL into multiple signed processes that run as NT AUTHORITY\SYSTEM.
Note: In order to exploit this vulnerability the attacker needs to have Administrator privileges.

Avira Antivirus
Avira Antivirus is an antivirus program which is developed and distributed by Avira Operations GmbH & Co. KG. It has multiple editions (Free, Pro, Internet Security, Prime, Business Edition).
Vulnerability Discovery
In our exploration, we targeted the Avira ServiceHost service which is the Avira Launcher service.
In addition to the fact that it is a signed process that runs as NT AUTHORITY\SYSTEM, this service was interesting because the Avira Launcher is the first part of the program which is installed right after the user double-clicks on the Installer (without a prompt) so we thought it should be popular.
When started, Avira.ServiceHost.exe tries to load the missing Wintrust.dll library from its own directory:
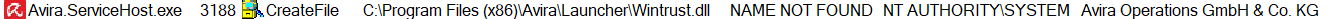
Usually, AV products restrict any modification (such as writing, adding or modifying files) to their folders by using a mini-filter driver which enforces a read-only policy on all users (including Administrator).
Despite this fact, we tried to implant a DLL, thinking “Who knows, it might even work…”.
PoC Demonstration
In order to test this vulnerability, we compiled an x86 arbitrary DLL which writes the following to the filename of a txt file:
- The name of the process which loaded it
- The username which executed it
- The name of the DLL file
We then placed it in the following path and restarted the computer:
C:\Program Files (x86)\Avira\Launcher\Wintrust.dll

We were able to load an arbitrary DLL and execute our code within Avira.ServiceHost.exe which was signed by “Avira Operations GmbH & Co. KG” and run as NT AUTHORITY\SYSTEM.
Note: We were also able to do the same with the following Avira services:
- Avira System Speedup
- Avira Software Updater
- Avira Optimizer Host
Root Cause Analysis
In order to analyze this one, we used dnSpy, because the vulnerable executable is based on .NET.
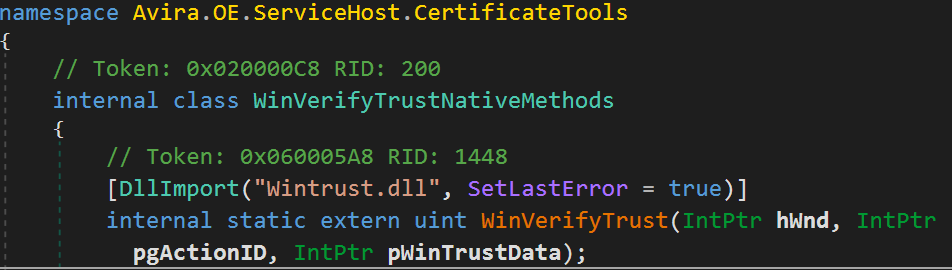
In order to verify the certificate of different binaries (for example, to load only trusted libraries), the Avira.ServiceHost.exe process uses the WinVerifyTrust WinAPI function.
It uses the DllImport attribute to load the Wintrust.dll unmanaged DLL:
Note: As we mentioned before, we have seen other components of the Antivirus software which use this code as well.
Because the code doesn’t contain the exact path of the Wintrust.dll, it will try to look for the library first in the CWD of the application.
There are two root causes for these vulnerabilities:
- No digital certificate validation is made against this specific binary. The program does validate whether different DLL files which it is loading are signed, but when it imports the Wintrust.dll library, it doesn’t validate it (because it relies on the WinVerifyTrust function which is inside the DLL and is not loaded yet). Therefore, it can load an arbitrary unsigned DLL.
- The AV has no self-protection for the Launcher folder.
As I mentioned before, different AVs protect their own folders from this kind of attack using a mini-filter filesystem driver which restricts any change to the directory of the AV.
Avira Antivirus currently doesn’t have this mechanism enabled on the “Launcher”, so attackers can implant arbitrary DLLs in the product’s folder.
Potential Malicious Uses and Impact
Below we show three possible ways that an attacker can leverage these vulnerabilities which we discovered and documented above.
Self-Defense Bypass
An antivirus application typically has a self-defense mechanism which prevents an attacker from tampering with its processes and files. Part of the mechanism is to use a mini-filter driver in order to monitor and prevent any changes to the directories of the antivirus application, so an attacker could not implant an arbitrary DLL, for example.
The vulnerability allows an attacker to bypass this part of the mechanism and load an arbitrary DLL into the antivirus process, because the self-defense mechanism is not enforced in the “Launcher” directory.
Signed Execution, Whitelisting Bypass
The vulnerability give attackers the ability to load and execute malicious payloads within the context of Avira signed processes. This ability might be abused by an attacker for different purposes such as execution and evasion, for example: Application Whitelisting Bypass.
Persistence Mechanism
The vulnerability gives an attacker the ability to load and execute malicious payloads in a persistent way, each time the services are loaded. That means that once the attacker drops a malicious DLL, the services will load the malicious code each time it is restarted.
Affected Products and Versions
- Avira Launcher – Versions below 1.2.137
- Avira Software Updater – Versions below 2.0.6.21094
Timeline
July 22nd, 2019 – SafeBreach reported a vulnerability to Avira.
Aug 16th, 2019 – Avira asked for clarifications about the vulnerability.
Aug 19th, 2019 – SafeBreach sent clarifications.
Aug 27th, 2019 – Avira said they will address this issue in future updates.
Sep 18th, 2019 – Avira said that they fixed the issue in the Launcher version 1.2.137.
Sep 19th, 2019 – SafeBreach asked Avira for a CVE-ID.
Sep 24th, 2019 – The vendor did not agree to provide a CVE-ID, claiming the fixed vulnerability was a security improvement.
Oct 9th, 2019 – Avira said they would publish release notes (without crediting SafeBreach for discovering the vulnerability).
Oct 10th, 2019 – SafeBreach asked MITRE to issue a CVE-ID.
Oct 10th, 2019 – MITRE issued CVE-2019-17449.
SafeBreach would like to thank MITRE for their prompt assistance and for assigning the CVE.
