Continuous threat exposure management (CTEM) is a formal program to manage cyber risk that allows organizations to enhance and optimize their overall cybersecurity posture. As outlined by Gartner, CTEM offers a cyclical approach to finding and mitigating threat exposure—which is the accessibility and exploitability of digital and physical assets—in an ongoing, proactive, and prioritized way.
CTEM does this by unifying traditional and emerging security elements for monitoring, detection and response, threat hunting and intelligence, vulnerability management (VM), forensics, analysis, and reporting. While some new elements may be needed to support a CTEM program, the approach seeks to increase the return on investment (ROI) of tools organizations already have in place to improve the readiness, response, resilience, and efficacy of security operations.
In this new blog series, we’ll set out to explore various aspects of a CTEM program, including what it is and how organizations can begin to implement a CTEM-based approach. In this installment, we’ll explore basic concepts about the program’s phases, related technologies, and potential benefits.
The Five Stages of a CTEM Program
The ongoing cycle of a CTEM program begins with scoping of security program goals and culminates with mobilization of resources to ensure mitigation—two powerful, collaborative activities that companies struggle with today. The five phases of the full program—scoping, discovery, prioritization, validation, and mobilization—take place continuously, but various events can trigger a cycle to begin at multiple phases.
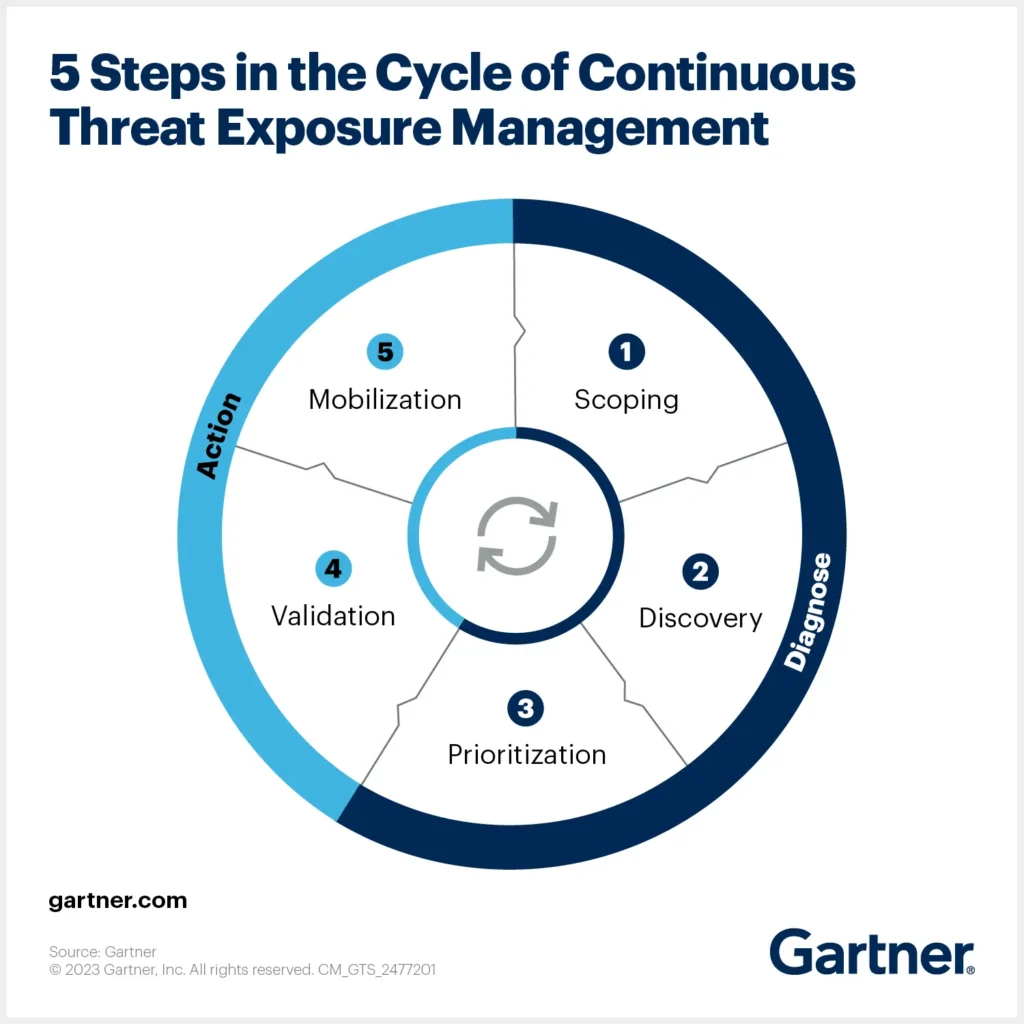
Phase I: Scoping to personalize CTEM objectives and parameters.
The first stage of scoping charts the course for your CTEM journey by defining which systems and assets should be included and which take priority based on your company’s business objectives and threat environments. This means identifying both your organization’s “crown jewel” assets and those facing the greatest risk of attack, then correlating the two perspectives so you can prioritize.
At a minimum, scoping should encompass four broad categories of security threats:
- Unintentional external threats originating from third-party partners, human error, negligence, or accidental acts
- Unintentional internal threats created by human error, negligence, or accidental actions
- Malicious external threats from hackers, hacktivists, criminal syndicates, or nation-states
- Malicious internal threats from rogue employees or third parties who commit data theft for financial gain
What are your business’s top security objectives?
Infrastructure: What resources must be protected to ensure business continuity?
Assets: What are the organization’s critical digital assets?
Compliance: What rules and regulations must you be in compliance with?
Brand: What must be protected to ensure your brand’s reputation?
Your company’s security strategy needs to identify and reflect which of these threat categories are most relevant and which assets might be impacted if a given threat succeeds. Quantifying risk and gaps in coverage helps to prioritize which assets the CTEM program should address and which teams must come together to define an approach and metrics for demonstrating success to stakeholders as the program unfolds.
Companies may find it useful to engage a trusted cybersecurity partner to provide guidance and help define the parameters for your CTEM program during the scoping phase. Once that’s complete, you can move on to identify, rank, and remediate threat exposures.
Phase II: Discovery to uncover end-to-end risk.
During discovery, organizations identify potential vulnerabilities within the systems and assets marked for inclusion in the CTEM program. IT, security, and business leaders should collaborate to review assets identified during the scoping phase and assess their vulnerability to risk from a variety of threats.
Discovery includes the obvious—pinpointing exposure from unpatched vulnerabilities—along with uncovering risk from external digital elements like those found during automated attack surface management (ASM) scans. Threats might include:
- Exposed or cyber-squatted domains
- Expired certificates
- Weak credentials
- Social media accounts
- Publicly exposed code repositories
- Misconfigurations
- Overly permissive identities
- Third-parties
- Shadow IT
Here again, the view of risk created during discovery combines what enterprise defenders can see—vulnerabilities and misconfigured assets and security controls—with the attacker’s view of your attack surface to drive evidence-based decisions in the next phase. The process might include a variety of tools and technologies, such as ASM, external ASM (EASM), digital risk protection, and what Gartner calls “dark and deep web sources” to identify and contextualize potential threats.
Phase III: Prioritization to maximize defense.
The goal of threat and exposure management should not be to find and fill every gap—which proves impossible—but to clarify which issues to fix first. CTEM applies a pragmatic, systematic approach to continuously refine priorities based on urgency, severity, availability of compensating controls, and above all, the value of assets being targeted.
The prioritization phase should quantify critical aspects of risk, including:
- How and how fast attackers might leverage exposure to move laterally through your network toward high-value assets. For example, you may ask:
- How long will it take for threat actors to reach the organization’s crown jewels?
- How and how quickly security controls and personnel might detect and mitigate attacks. For example, you may ask:
- How quickly can you detect and stop lateral movement?
- What can be done to keep time on the side of defenders?
- Which vulnerabilities pose the greatest risk to the business. For example, you may ask:
- Which vulnerabilities need to be patched right away?
- Which can take lower priority?
Which assets stand the greatest chance of being exploited by an adversary?
Do you have controls in place to protect these assets?
The assessments conducted during the prioritization stage equip defenders to quickly resolve “low-hanging fruit” issues such as risk from excessive permissions, vulnerabilities, and exposed cloud storage before moving on to more nuanced, sophisticated attacker behaviors.
The ability to prioritize in real time means the difference between working hard and working smart, so all security controls and workflows should be evaluated in terms of whether they speed or slow the process of correlating and contextualizing threat data.
Through 2026, non-patchable attack surfaces will grow from less than 10% to more than half of the enterprise’s total exposure, reducing the remediation practices.
– Gartner
Phase IV: Validation to move forward with confidence.
Once you’ve established clear priorities, the next step is to validate your security posture by testing the processes, procedures, and controls you have in place to gauge whether they can stop foreseeable threats. Gartner recognizes the need for continuous assessment within the CTEM cycle to:
- Show how potential attackers might exploit identified exposures
- Measure how well monitoring and control systems react to block threats and mitigate exposure
- Verify suggested treatments to improve security efficacy without disrupting operations
- Validate your improved security posture after remediation
There are a number of security validation methods available on the market today, but each has different uses and functions. And, not all of them are appropriate in every IT environment. Validation modalities used within a CTEM program might include:
- Attack and external attack surface management (ASM, EASM)
- Digital risk protection service (DRPS)
- Vulnerability Assessment (VA) and prioritization technology (VPT)
- Breach and attack simulation (BAS)
- Penetration testing (pen testing) and testing as a service (PTaaS)
- Automated pen testing and red team exercises
Reliable, comprehensive validation also guides and justifies investment strategies. Experts can recreate real-world events and threats such as phishing campaigns and business email compromise (BEC) to see how employees react and whether expanding your coverage, skillset, or education programs might add value. This might include scanning and updating your infrastructure and training your team using a mix of automated tools and analyst expertise.
Last but not least, validation of perceived threat paths, vulnerabilities, and security control effectiveness increases security leaders’ confidence in strategies for improving threat hunting, response, forensics, and other vital ongoing activities.
Phase V: Mobilization with collaboration across the organization.
Even when you know what to do, improving your security posture requires a sustained, cross-functional effort. Mobilization relies on collaboration and clear communication to achieve the ultimate objective of CTEM: reduced exposure to foreseeable threats. According to Gartner, “Through 2025, security leaders who implement cross-team mobilization as part of their exposure management program will gain 50% more security optimization than those only prioritizing automated remediation.”
Security and risk management leaders responsible for managing today’s and tomorrow’s enterprise exposure to threats should embrace a security posture validation approach to augment their prioritization workflow and enhance cybersecurity readiness.
– Gartner
During this stage (and in an ongoing manner), security teams should keep software up-to-date, conduct all scheduled security scans, and continue to train employees in the latest best practices. Ongoing validation—and the reports it provides—makes the process move faster by illuminating gaps and enabling better communication to ensure cross-functional teams are aligned on the response processes and in what cases they should be triggered. As the CTEM cycle renews, testing shows and helps prioritize new areas needing attention in the next phase of building the program.
The Benefits of CTEM
By 2026, organizations prioritizing their security investments based on a continuous exposure management program will be three times less likely to suffer from a breach.
– Gartner
According to Gartner, organizations that adopt a CTEM-based approach to their security program stand to benefit from enhanced security posture and fewer breaches. However, Gartner also notes that those organizations must be prepared for a multi-year implementation initiative that should be approached in stages to build a cohesive program versus another point tool or platform.
Fortunately, there are benefits at each stage in the implementation process that organizations will begin to experience, including:
- Faster, more secure digitalization and adoption of software-as-a-service (SaaS)/cloud services
- Secure remote and hybrid work
- Easier cyber due diligence around mergers and acquisitions (M&A)
- Improved response times and mean time to repair (MTTR)
- Evidence- and risk-based operations
- Reduced third-party risk
- Validation of current and future investments
Generally speaking, better security stems from the ability to have greater insight that makes it easier to decide on the right course of action moving forward. CTEM creates a force multiplier by combining and bridging the gaps between disparate perspectives:
- The attackers’ and defenders’ view of risk. Which threats do your security teams see? What external-facing exposure can attackers see? Which side has the advantage?
- A view of known and unknown threat exposures. CTEM correlates a “heads-up” on zero-day threats with global intelligence on known but as-yet-unpatched vulnerabilities—adversaries’ favorite “low-hanging fruit” to exploit.
- A view of patchable and non-patchable exposure. “Non-patchable” includes the sharp rise in third-party ecosystems originating beyond your IT team’s visibility or control.
Each phase of the cycle should include validating goals and progress to drive collaboration across security, infrastructure and operations (I&O) teams, application architects, and business leaders.
The “Big Picture” Role of Validation within a CTEM Program
A CTEM program produces the evidence needed to demonstrate to senior management that mitigating and anticipating risk is an uphill battle—and a never-ending job—that is extensive, but worth it. Continuous, automated testing—like that enabled by BAS solutions—enables organizations to leverage the tactics, techniques, and procedures (TTPs) used by malicious actors to recreate and model complete, realistic attack scenarios against their assets and infrastructure.
How? We’ll dive into the details in our next blog, “The Key Word is Continuous,” which describes the role of validation in detail and shows how BAS, pen testing, red/purple team exercises, and other assessments work together to drive and improve your CTEM program and security posture.
Ready to learn more about how BAS can play an important role in your CTEM program now? Connect with a SafeBreach cybersecurity expert today.

