On February 16th, the Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), the Federal Bureau of Investigation (FBI) issued an advisory that provided additional details about targeted attacks by Russian state-sponsored threat actors on U.S cleared defense contractors (CDCs) and subcontractors. These attacks began in January 2020 and were still being observed in February 2022. The attacks on both small and large CDCs were aimed at acquiring sensitive, unclassified information, as well as CDC-proprietary and export-controlled technology. This stolen information provides significant insight into U.S. weapons platforms development and deployment timelines, vehicle specifications, and plans for communications infrastructure and information technology. Details of the various tactics, techniques, and procedures (TTPs) are described in US-CERT Alert (AA22-047A) – Russian State-Sponsored Cyber Actors Target Cleared Defense Contractor Networks to Obtain Sensitive U.S. Defense Information and Technology.
According to the information available, these state-sponsored threat actors leveraged access to the secure contractor/ sub-contractor networks to obtain sensitive data about U.S. defense and intelligence programs and capabilities. Compromised entities have included CDCs supporting the U.S. Army, U.S. Air Force, U.S. Navy, U.S. Space Force, and DoD and Intelligence programs. During the observed two-year period, threat actors maintained persistent access to multiple CDC networks, in some cases for at least six months. Whenever secure networks were successfully accessed, the FBI, NSA, and CISA noted regular and recurring exfiltration of emails and data.
The Russian threat actors were observed using the following Tactics, Techniques, and Procedures (TTPs) to breach secure defense contractor networks:
- Brute force techniques were used to identify valid credentials (for domain and admin M365 accounts) and gain initial foothold.
- Harvested admin credentials in conjunction with known vulnerabilities on public-facing applications like FortiGate VPN devices were then leveraged to escalate privileges and gain remote code execution (RCE) on exposed applications.
- After gaining initial access, threat actors sent legitimate looking spearphishing emails to unsuspecting victims to steal their user credentials.
- Stolen user credentials were then used to change permissions on enterprise applications, exfiltrate sensitive emails from user accounts, or gain access to other systems in the network (lateral movement).
NOTE – Since several of these identified TTPs have been previously used by the Russian threat actors, these were already included in the SafeBreach Hacker’s Playbook™ and have now also been mapped to US-CERT Alert (AA22-047A). Freshly discovered TTPs were also added as new attacks to the playbook. We encourage you to test your preparedness against the Russian state-sponsored threat groups by running the attacks listed below.
5 newly developed playbook methods related to US-CERT AA22-047A (Russian State-Sponsored Cyber Actors)
- #6913 – Write Koadic rootkit to disk (host-level)
- #6914 – Transfer of Koadic rootkit over HTTP/S (Lateral Movement)
- #6915 – Transfer of Koadic rootkit over HTTP/S (Infiltration)
- #6916 – Email Koadic rootkit as a ZIP attachment (Lateral Movement)
- #6917 – Email Koadic rootkit as a ZIP attachment (Infiltration)
As mentioned earlier Hacker’s Playbook already included many (13) of the tactics, techniques, and procedures (TTPs) previously used by the Russian threat actors. These attacks can be seen below:
- #2604 Transfer of fysbis malware over HTTP/S(Lateral Movement)
- #2605 Transfer of fysbis malware over HTTP/S (Infiltration)
- #2262 BBSwift – malware transfer and first communication – using TOR (Infiltration)
- #6807 Extract credentials from ntds.dit file using volume shadow copy (Host-level)
- #4135 Data Asset Exfiltration with the Email Attachment (Exfiltration)
- #6581 Discover domain computers using LDAP method (Host-level)
- #6580 Discover domain groups using LDAP method (Host-level)
- #6578 Discover domain users using LDAP method (Host-level)
- #2603 Write fysbis malware to disk (Host-level)
- #5567 Path Traversal of Fortigate VPN vulnerability CVE-2018-13379 (Infiltration)
- #794 Extract Login Information using MimiKatz (Host-level)
- #2606 Email fysbis malware as a ZIP attachment (Lateral movement)
- #2306 Domain Trust Discovery (Host-level)
What you should do now
The newly updated and existing attack methods for US-CERT AA22-047A (Russian State-Sponsored Cyber Actors) are already in the SafeBreach Hacker’s playbook and ready to be run across your simulators. The Known Attack Series report has been updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT AA22-047A (Russian State-Sponsored Cyber Actors) report and select Run Simulations which will run all attack methods.
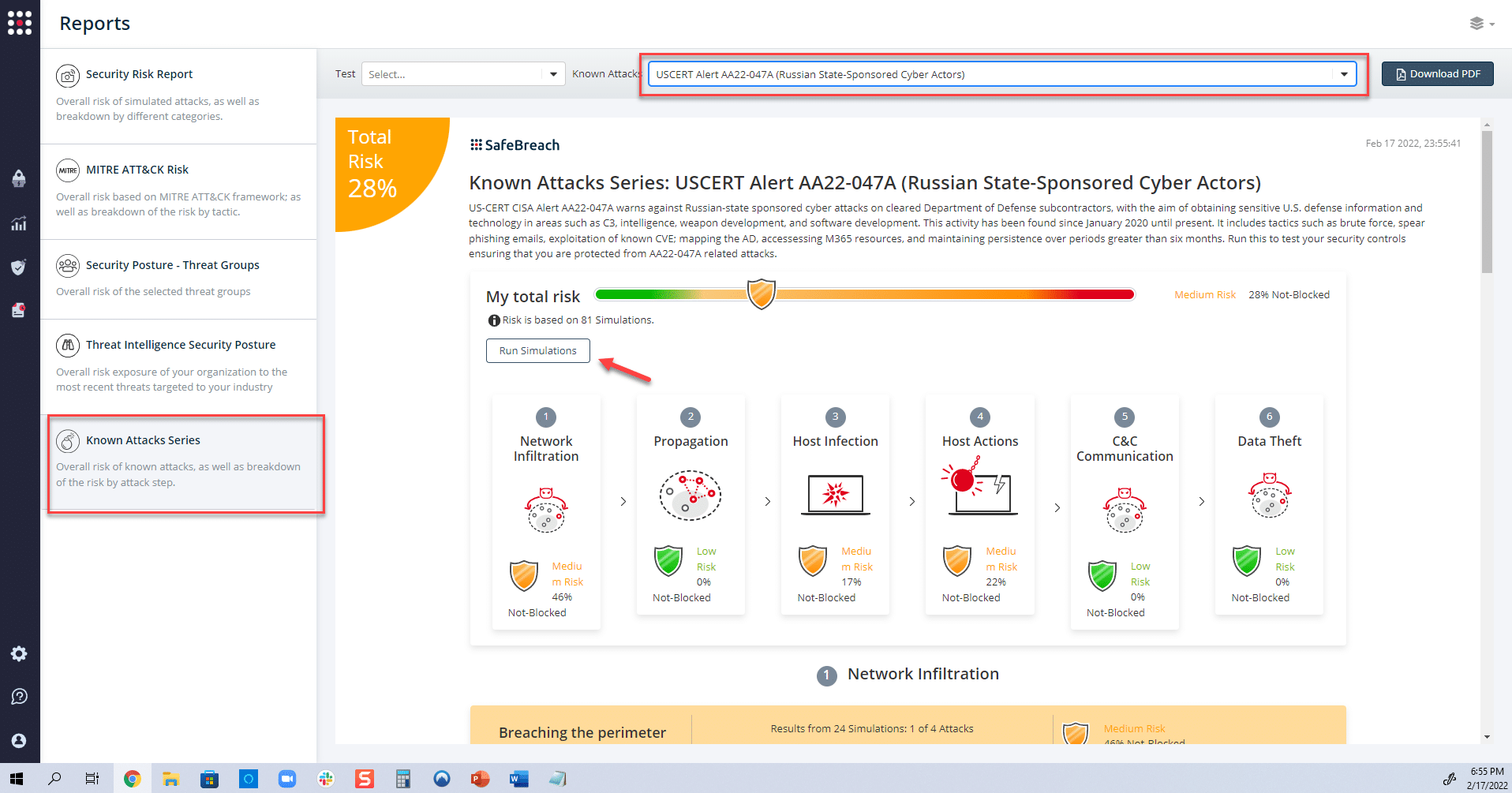
You can also select all the attacks related to US-CERT AA22-047A (Russian State-Sponsored Cyber Actors), by going to the SafeBreach Playbook and filtering by Threat Name – US-CERT AA22-047A (Russian State-Sponsored Cyber Actors).

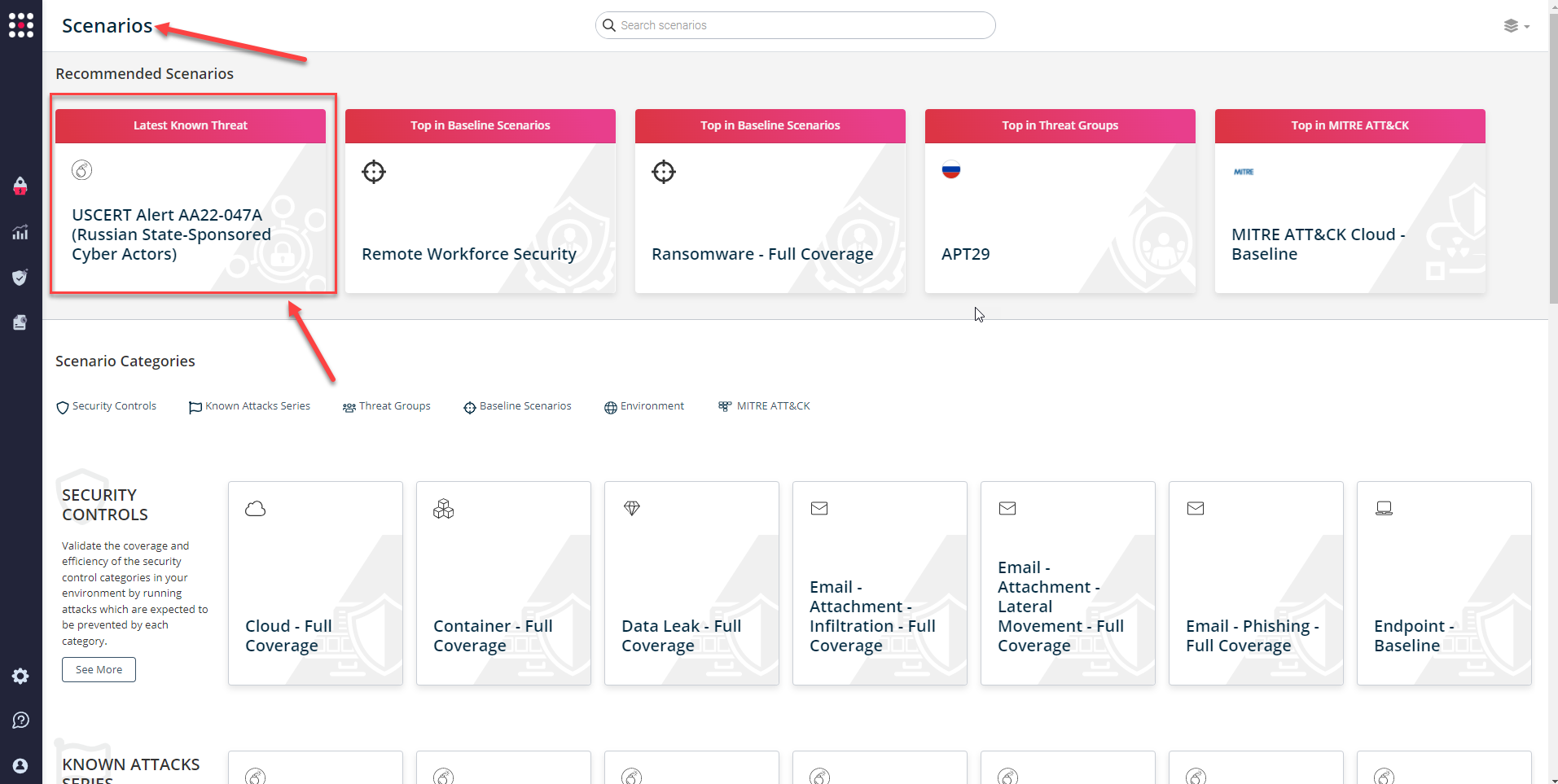
or you can go to “SafeBreach Scenarios” page and choose the USCERT Alert AA22-047A (Russian State-Sponsored Cyber Actors) scenario from the list of available scenarios.
NOTE – CISA, FBI, and the NSA also recommend the following mitigations to secure your organization against Russian state-sponsored malicious cyber activity:
- Enforce multifactor authentication.
- Enforce strong, unique passwords.
- Enable M365 Unified Audit Logs.
- Implement endpoint detection and response tools.