On December 18th, the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC) issued an urgent advisory to highlight the ongoing malicious activities being conducted by the Play ransomware group. Detailed information about these activities and the associated indicators of compromise (IOCs) and the various tactics, techniques, and procedures (TTPs) is listed in US-CERT Alert AA23-352A – #StopRansomware: Play Ransomware.
According to the advisory, the Play (also known as Playcrypt) ransomware threat actors have been actively targeting critical infrastructure entities in North America, South America, and Europe since June 2022. The ongoing FBI investigation has revealed that as of October 2023, approximately 300 organizations/ businesses have been impacted by this threat group. Additionally, according to the ACSC, the Play ransomware group first targeted Australian entities in April 2023 and the latest incident was seen in November 2023.
Authorities believe that the Play ransomware group is a very close-knit group that is purposefully designed to “guarantee the secrecy of deals”. Threat actors leveraging Play ransomware employ the double-extortion strategy where they not only encrypt victim systems but also steal and exfiltrate data before performing this encryption. Their ransom notes do not include any ransom demand or payment instructions, but victims are asked to contact the threat group via an email address provided in the ransom note.
Technical Details
The Play ransomware group first emerged in 2022 and has been actively targeting organizations across the world including those in the United States, Brazil, Argentina, Germany, Belgium, and Switzerland. It has been suspected that this group may have ties to other Russian APT groups as a lot of their encryption techniques are very similar to those leveraged by ransomware groups like Hive and Nokoyawa. Their name is derived from their use of the “.play” extension used by them to rename encrypted files and them leaving a message containing the word “PLAY”. Based on the information available from the advisory and other sources, here are some of the technical details of the attack:
- Gaining Initial Access – The Play group often gains initial access to victim networks by abusing valid accounts and exploiting public-facing applications, especially exploiting vulnerabilities in FortiOS (CVE-2018-13379 and CVE-2020-12812) and Microsoft Exchange (ProxyNotShell CVE-2022-41040 and CVE-2022-41082). They have also been observed using external facing services like remote desktop (RDP) and virtual private networks (VPN) to gain initial access to target networks.
- Performing Discovery and Evading Defenses – The threat actors have been observed using tools like AdFind to run multiple Active Directory queries and an information-stealing tool, Grixba to enumerate network information. They are known to also use tools like GMER, IOBit, and PowerTool to disable deployed AV tools and remove log files. They have also been observed using PowerShell scripts to target and disable Microsoft Defender.
- Moving Laterally and Privilege Escalation – The use of command and control (C2) tools like Cobalt Strike, PsExec, and SystemBC to facilitate lateral movement and execute files is a known tactic of the Play ransomware group. Once they establish their presence on victim networks, they are known to hunt for unsecured user credentials and use the Mimikatz credential dumper to gain domain administrator access. They also use Windows Privilege Escalation Awesome Scripts (WinPEAS) to find further ways to escalate their privileges.
- File Encryption and Sensitive Data Exfiltration – Play ransomware actors often split stolen data into smaller segments and compress them using tools like WinRAR. They then use WinSCP to transfer data from a compromised network to actor-controlled accounts. Post-exfiltration, files are encrypted with AES-RSA hybrid encryption and a “.play” extension is added to file names and a ransom note titled “ReadMe[.]txt” is placed in the C: directory.
- Use of Double Extortion – Play threat actors actively leverage the “Double Extortion” model – they first exfiltrate sensitive data and then leave behind encrypted files. They expect victims to pay ransom in cryptocurrency and if a victim refuses to pay the ransom, the Play threat actors threaten to publish stolen data on the dark web.
Important Note for SafeBreach Customers – Coverage for AA23-352A (Play Ransomware)
As soon as details were made available, the SafeBreach Labs teams mapped existing attacks and added new attacks to the Hacker’s Playbook immediately. It is important to note that existing SafeBreach customers were already protected against a lot of the behavioral and IOC-based attacks commonly used by the Play ransomware gang and identified in the advisory. Please run/ re-run the attacks listed below to ensure your environments are protected against this malware variant.
NEW IOC-Based Attacks Related to CERT Alert
- Play Ransomware
- #9426 – Write Play (ccae57) ransomware to disk
- #9427 – Pre-execution phase of Play (ccae57) ransomware (Windows)
- #9428 – Transfer of Play (ccae57) ransomware over HTTP/S
- #9429 – Transfer of Play (ccae57) ransomware over HTTP/S
- #9430 – Email Play (ccae57) ransomware as a compressed attachment
- #9431 – Email Play (ccae57) ransomware as a compressed attachment
- #9420 – Write Play (data gathering tool) (465deb) ransomware to disk
- #9421 – Pre-execution phase of Play (data gathering tool) (465deb) ransomware (Windows)
- #9422 – Transfer of Play (data gathering tool) (465deb) ransomware over HTTP/S
- #9423 – Transfer of Play (data gathering tool) (465deb) ransomware over HTTP/S
- #9424 – Email Play (data gathering tool) (465deb) ransomware as a compressed attachment
- #9425 – Email Play (data gathering tool) (465deb) ransomware as a compressed attachment
- SystemBC
- #9432 – Write SystemBC (226212) hacktool to disk
- #9433 – Pre-execution phase of SystemBC (226212) hacktool (Windows)
- #9434 – Transfer of SystemBC (226212) hacktool over HTTP/S
- #9435 – Transfer of SystemBC (226212) hacktool over HTTP/S
- #9436 – Email SystemBC (226212) hacktool as a compressed attachment
- #9437 – Email SystemBC (226212) hacktool as a compressed attachment
- Gmer
- #9438 – Write Gmer (fd12f7) rootkit to disk
- #9439 – Transfer of Gmer (fd12f7) rootkit over HTTP/S
- #9440 – Transfer of Gmer (fd12f7) rootkit over HTTP/S
- #9441 – Email Gmer (fd12f7) rootkit as a compressed attachment
- #9442 – Email Gmer (fd12f7) rootkit as a compressed attachment
- New Vulnerability Exploitation Attack (CVE-2018-13379)
- #9443 – Remote exploitation of FortiOS vulnerability CVE-2018-13379 (WAF)
Existing Behavioral Attacks Mapped to the CERT Alert
- All ransomware execution attacks available in the SafeBreach playbook
- #794 – Extract Login Information using MimiKatz
- #1220 – Inject Mimikatz using PowerShell to Extract Credentials
- #1339 – Remote command execution by PSExec
- #1693 – Collect Windows system data using CMD
- #2188 – Extract Process List using Windows Commands
- #2194 – Extract Credentials from the Registry using System Commands
- #2206 – Extract Security Packages using PowerShell
- #2208 – Extract Credentials using Get-GPPPassword (PowerShell)
- #2273 – Pass the Hash over SMB using Mimikatz
- #2306 – Domain Trust Discovery
- #3819 – Windows Credentials Collection using LaZagne
- #3829 – Run obfuscated Mimikatz on host
- #5833 – Extract Login Information using MimiKatz DCSync
- #6473 – Agentless lateral movement via RDP
- #6513 – Agentless lateral movement via SMB and RCE, using Mimikatz
- #6801 – Credential harvesting using Mimikatz DCSync with interactive session token
- #6802 – Credential harvesting using Mimikatz DCSync with user credentials
- #7043 – Disable Cortex XDR using its default password (Windows)
- #7144 – Unregister anti malware scanning interface providers
- #7167 – Covert data asset exfiltration over TOR (Windows) (exfiltration)
- #7168 – Enable a default account and add it to a Localgroup (Windows)
- #7211 – Collect Azure credentials (Windows)
- #7554 – Clear Windows Event Logs
- #7834 – Add Exclusions to Windows Defender
- #7835 – Disable Windows Defender From Registry
- #8853 – Disable rules in Windows Defender to allow credential harvesting using Lazagne
- #8856 – Create rule in Windows Defender to delete arbitrary file
- #8857 – Add Mimikatz as exclusion to Windows Defender and execute Mimikatz
Existing IOC-based Attacks Mapped to the CERT Alert
- Mimikatz
- All existing Mimikatz attacks from the SafeBreach playbook
- winPEAS
- #6817 – Pre-execution phase of winPEAS malware
- #6818 – Write winPEAS malware to disk
- #6819 – Transfer of winPEAS malware over HTTP/S
- #6820 – Transfer of winPEAS malware over HTTP/S
- #6821 – Email winPEAS malware as a compressed attachment
- #6822 – Email winPEAS malware as a compressed attachment
- Play ransomware
- #8536 – Write Play ransomware (d3f0) to disk
- #8537 – Transfer of Play ransomware (d3f0) over HTTP/S
- #8538 – Transfer of Play ransomware (d3f0) over HTTP/S
- #8539 – Email Play ransomware (d3f0) as a compressed attachment
- #8540 – Email Play ransomware (d3f0) as a compressed attachment
- #8541 – Write Play ransomware (1934) to disk
- #8542 – Transfer of Play ransomware (1934) over HTTP/S
- #8543 – Transfer of Play ransomware (1934) over HTTP/S
- #8544 – Email Play ransomware (1934) as a compressed attachment
- #8545 – Email Play ransomware (1934) as a compressed attachment
What You Should Do Now
The playbook has been updated with new attacks that map to the IOCs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
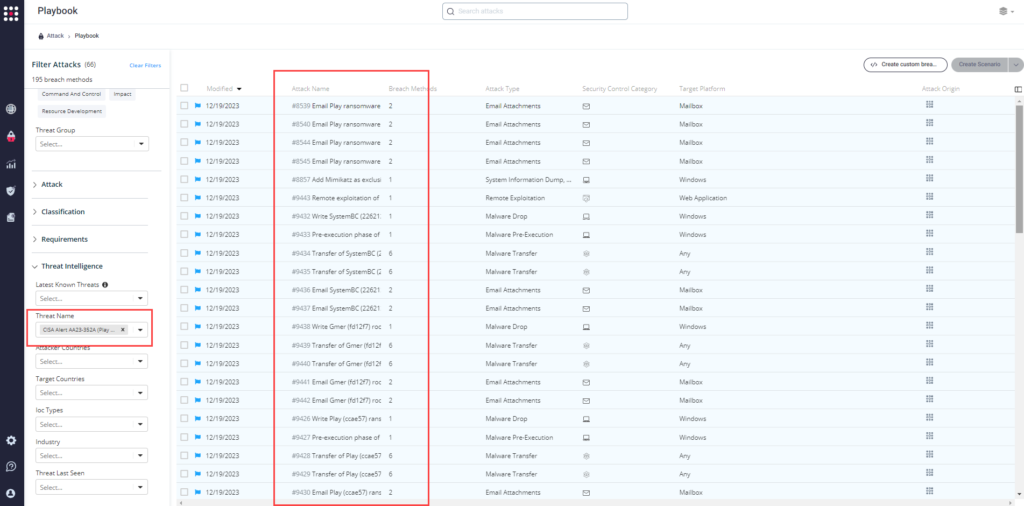
Method 1 – You can go to the “SafeBreach Scenarios” page and choose the AA23-352A (Play Ransomware) scenario from the list of available scenarios.
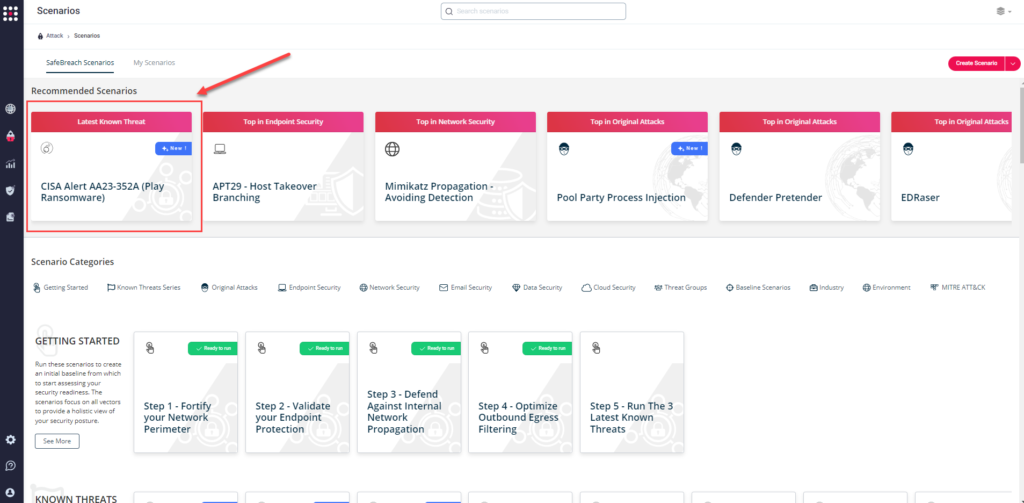
Method 2 – From the Attack Playbook, select and filter attacks related to US-CERT Alert AA23-352A (Play Ransomware) . Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
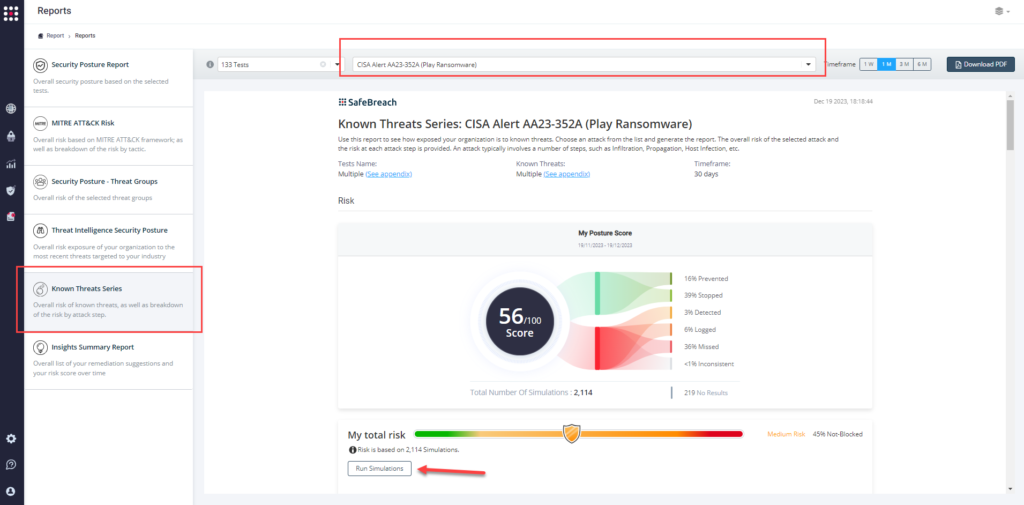
Method 3 – From the Known Attack Series report, select the AA23-352A (Play Ransomware) report and select Run Simulations which will run all attack methods.
NOTE – FBI, CISA, and ASD’s ACSC recommend continually validating your security program, at scale, in a production environment to ensure optimal performance against growing threat of advanced cyber threats. Additional recommendations include:
- Resources to mitigate a ransomware attack: #StopRansomware Guide.
- Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers.
- Require all accounts with password logins to comply with NIST’s standards for developing and managing password policies.
- Identify, detect, and investigate abnormal activity and potential traversal of the indicated ransomware with a networking monitoring tool.
- Enable multifactor authentication (MFA) for all services to the extent possible, particularly for webmail, VPN, and accounts that access critical systems.
- Implement time-based access for accounts set at the admin level and higher.
- Keep all operating systems, software, and firmware up to date.
- Deploy software to identify suspicious behavior on systems.
- Ensure backup data is encrypted, and immutable.
- For detailed information about mitigations and incident response, please refer to the full advisory.

