In light of the ongoing situation in Ukraine, the Cybersecurity and Infrastructure Agency (CISA) has warned that businesses and entities across certain sectors, including finance, energy/utilities, and local and state governments, should be prepared for cyber attacks that could attempt to damage critical infrastructure, disrupt markets, and undermine the security of countries and governments around the world.
As a cybersecurity organization, we understand the significance of this warning and recognize the sensitivity of this situation in particular. We also understand that organizations around the world—many of whom are our own customers—are attempting to identify their level of risk arising from these attacks and the proactive steps they can take to ensure their protection today.
While there is uncertainty about how exactly events will unfold, we do have data about the threat groups that will likely be active during this time, as well as the attack methods and vulnerabilities they may attempt to exploit. As SafeBreach’s CISO, it is my goal to provide resources, links, and best practices that may be helpful to any organization—whether you are a SafeBreach customer or not—as you navigate this challenging time.
SafeBreach coverage for Russian APT Group–related US-CERT Alerts
- SafeBreach coverage for US-CERT AA22-047A
- SafeBreach coverage for US-CERT AA21-148A
- SafeBreach coverage for US-CERT AA20-296A
- Maze Ransomware
APT 28 and APT 29 Vulnerabilities and Associated Attacks
Based on the information available and on their reputations, we believe APT 28 and APT 29 have the potential to play a significant role in any cyber events related to the current geopolitical situation. As such, we recommend ensuring that your organization has completed a risk assessment specifically for these vulnerabilities and has mitigation strategies in place.
For SafeBreach customers, the tactics, techniques, and procedures (TTPs) associated with these attacks have already been included in the SafeBreach Hacker’s Playbook™. Attacks related to APT 28 and APT 29 can easily be run from within the SafeBreach platform—> SafeBreach Scenarios (see screenshots below).
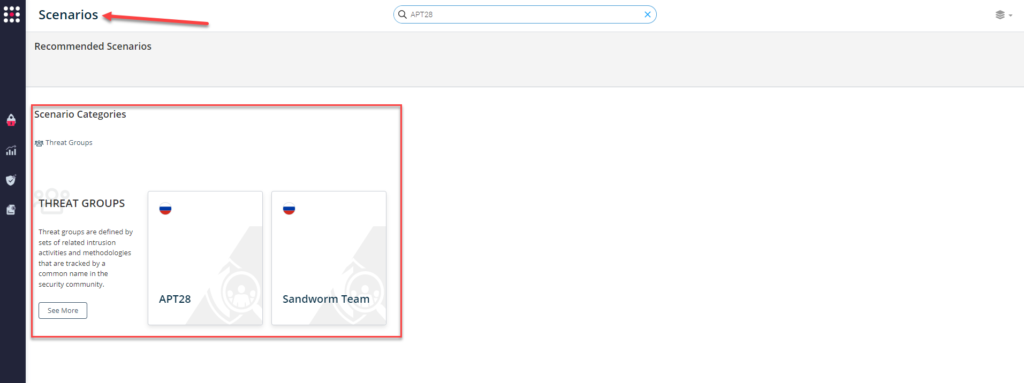
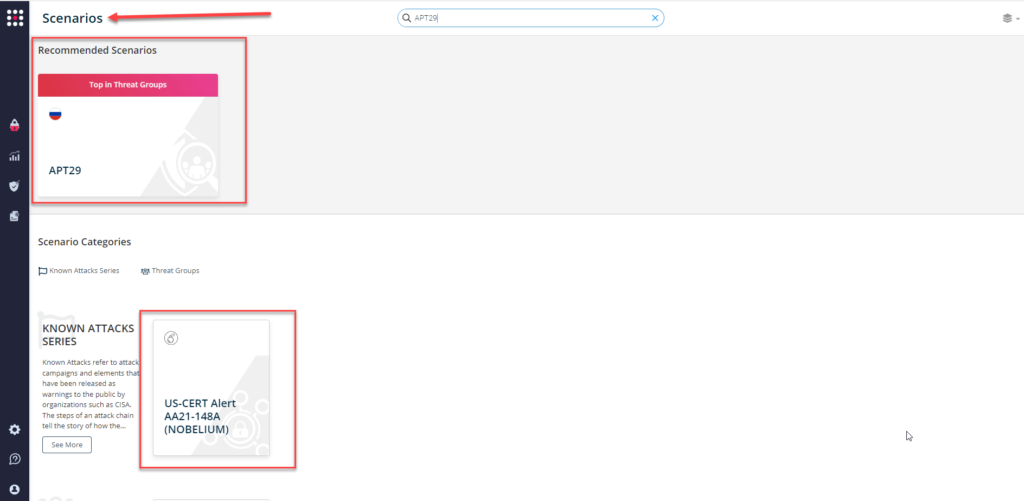
Background and Other Relevant Federal Government Resources:
- CISA Shields Up Technical Guidance
- US-CERT AA22-054A — New Sandworm Malware Cyclops Blink Replaces VPNFilter
- CISA — Russia Cyber Threat Overview and Advisories
- US-CERT AA22-A57A – Destructive Malware Targeting Organizations in Ukraine
- US-CERT AA22-011A — Understanding and Mitigating Russian State-Sponsored Cyber Threats to U.S. Critical Infrastructure
- Joint Cybersecurity Advisory — Technical Approaches to Uncovering and Remediating Malicious Activity
Relevant Resources from our Technology Partners
As always, we’re passionate about improving security on a global level and will continue to provide updates (including updates about new associated attacks being added to the Hacker’s Playbook) as additional information becomes available. Please feel free to reach out to our team at any time to discuss this or any cybersecurity-related topic.