On September 6, the Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), and Multi-State Information Sharing and Analysis Center (MS-ISAC) issued a joint advisory highlighting the recent and ongoing ransomware attacks on educational institutions by a threat group known as Vice Society. Additional details about this group and its associated tactics, techniques, and procedures (TTPs) are available in US-CERT Alert (AA22-249A) #StopRansomware: Vice Society.
For the last several years attackers have disproportionately attacked the educational vertical, especially targeting kindergarten through twelfth grade (K-12) institutions. These attacks have impacted their regular, day-to-day functions including massive issues like restricted access to networks and data, delayed exams, canceled school days, and unauthorized access to and theft of personal identifiable information (PII).
The FBI, CISA, and MS-ISAC have warned of increasing attacks as the 2022/2023 school year has just begun and opportunistic threat actors may capitalize on vulnerable school districts with limited cybersecurity capabilities and constrained resources. K-12 institutions may be seen as particularly lucrative targets due to the amount of sensitive student data accessible through school systems or their managed service providers.
Additional Technical Details
According to the advisory, Vice Society is a new threat group that first appeared in the summer of 2021 and focuses primarily on infiltration, exfiltration, and extortion. They do not have a signature ransomware strain that they leverage. Instead, they have been observed using existing variants like Hello Kitty/Five Hands and Zeppelin ransomware. It is important to note that since they are still relatively unknown, they may leverage other ransomware variants in the future.
Vice Society threat actors are likely to obtain initial access to educational institution networks through compromised credentials by exploiting web-facing applications. Prior to ransomware payload deployment, they spend time scouring and exploring the network to identify opportunities for privilege escalation and exfiltration of data for the purpose of double extortion. Double extortion is when threat actors threaten to publicly release stolen sensitive information unless their ransom demands are met. These threat actors have also been observed using proxy malware like SystemBC, PowerShell Empire, and Cobalt Strike for lateral movement.
Vice Society has been observed exploiting the PrintNightmare vulnerability for privilege escalation and they maintain persistence by leveraging scheduled tasks, creating undocumented autostart Registry keys, and pointing legitimate services to their custom malicious dynamic link libraries (DLL) through DLL sideloading. Upon achieving privilege escalation and gaining access to domain administrator accounts, they run scripts to change victim passwords and prevent the victim from remediating.
Important Note for SafeBreach Customers – Coverage for AA22-249A
September 7. It is important to note that since the Vice Society threat actors have been leveraging known ransomware variants and other known TTPs, SafeBreach customers already had an existing level of protection against Vice Society attacks if their security controls were validated against these known TTPs.
10 newly added playbook methods for US-CERT Alert AA22-249A:
- #7565 – Email Vice Society GUI malware as a ZIP attachment (INFILTRATION)
- #7564 – Email Vice Society GUI malware as a ZIP attachment (LATERAL_MOVEMENT)
- #7563 – Transfer of Vice Society GUI malware over HTTP/S (INFILTRATION)
- #7562 – Transfer of Vice Society GUI malware over HTTP/S (LATERAL_MOVEMENT)
- #7561 – Write Vice Society GUI malware to disk (HOST_LEVEL)
- #7570 – Email Vice Society Console malware as a ZIP attachment (INFILTRATION)
- #7569 – Email Vice Society Console malware as a ZIP attachment (LATERAL_MOVEMENT)
- #7568 – Transfer of Vice Society Console malware over HTTP/S (INFILTRATION)
- #7567 – Transfer of Vice Society Console malware over HTTP/S (LATERAL_MOVEMENT)
- #7566 – Write Vice Society Console malware to disk (HOST_LEVEL)
31 previously available playbook attacks for AA22-249A:
- WMI Leverage
- #1527 – Remote command execution by WMIC (information gathering)
- #1528 – Remote command execution by WMIC (remote download and execute)
- #1529 – Remote command execution by WMIC
- #1562 – Remote command execution by WMIC
- #2250 – Execute VBScript using XSL with wmic.exe
- #5672 – Agentless lateral movement via WMI
- #6918 – Execute remote VBScript using XSL with wmic.exe
- Scheduled Task/Job
- #1269 – Creating Windows schedule task (schtasks)
- #2164 – Scheduled Task
- Persistence
- # 2293 – Create and Start a Service
- Registry Run Keys/ Startup Folder
- #2221 – Modify the Registry Run keys
- DLL Side Loading
- # 6809 – Execute DLL by signed executable (igfxtray.exe)
- Privilege Escalation
- #6481 – Local Privilege Escalation using CVE-2021-1675 (PrintNightmare)
- #6482 – Remote Code Execution via CVE-2021-34527 (PrintNightmare)
- Masquerading
- # 2248 – Masquerading
- #2293 – Create and Start a Service
- Process Injection
- #2246 – Hooking of GetSystemTime function using mavinject.exe with a custom DLL
- #4136 – Execute EXE file using process hollowing (PowerShell)
- #7220 – Process Injection – Thread Execution Hijacking
- Sandbox Evasion
- # 2279 – Virtualization/Sandbox Evasion
- Existing Malware Coverage
- #6661 – Pre-execution phase of HelloKitty malware
- #6662 – Write HelloKitty malware to disk
- #6663 – Transfer of HelloKitty malware over HTTP/S
- #6664 – Transfer of HelloKitty malware over HTTP/S
- #6665 – Email HelloKitty malware as a ZIP attachment
- #6666 – Email HelloKitty malware as a ZIP attachment
- #7445 – Write Zeppelin malware to disk
- #7446 – Transfer of Zeppelin malware over HTTP/S
- #7447 – Transfer of Zeppelin malware over HTTP/S
- #7448 – Email Zeppelin malware as a ZIP attachment
- #7449 – Email Zeppelin malware as a ZIP attachment
What You Should Do Now
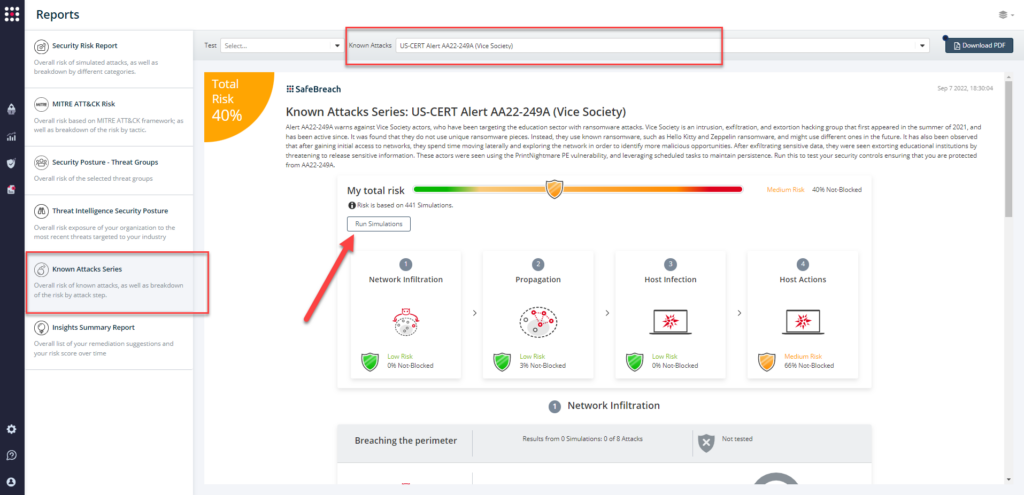
Attack methods related to US-CERT Alert AA22-249A are ready to run across your simulators. The Known Attack Series report has been updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT Alert AA22-249A (Vice Society) report and select Run Simulations which will run all attack methods.
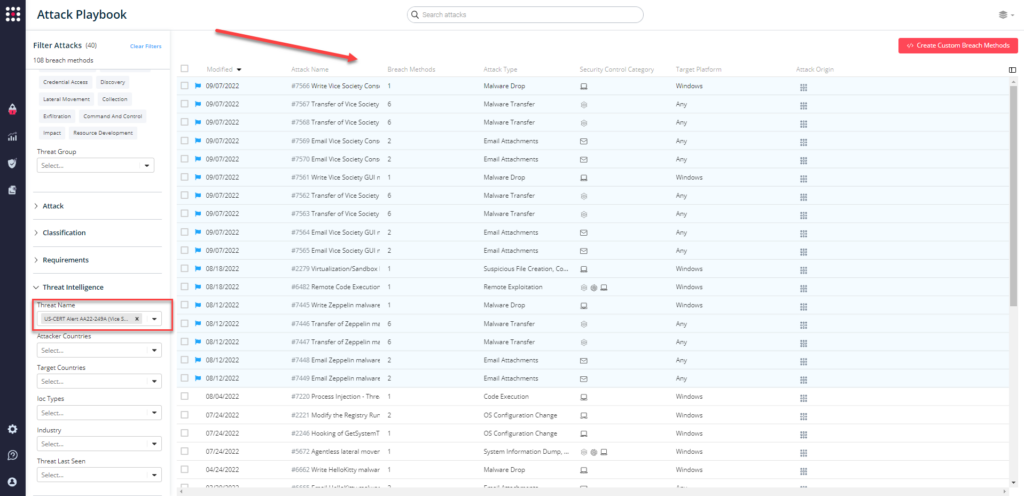
You can also select all the attacks related to US-CERT Alert AA22-249A by going to the SafeBreach Playbook and filtering by Threat Name – US-CERT Alert AA22-249A (Vice Society)
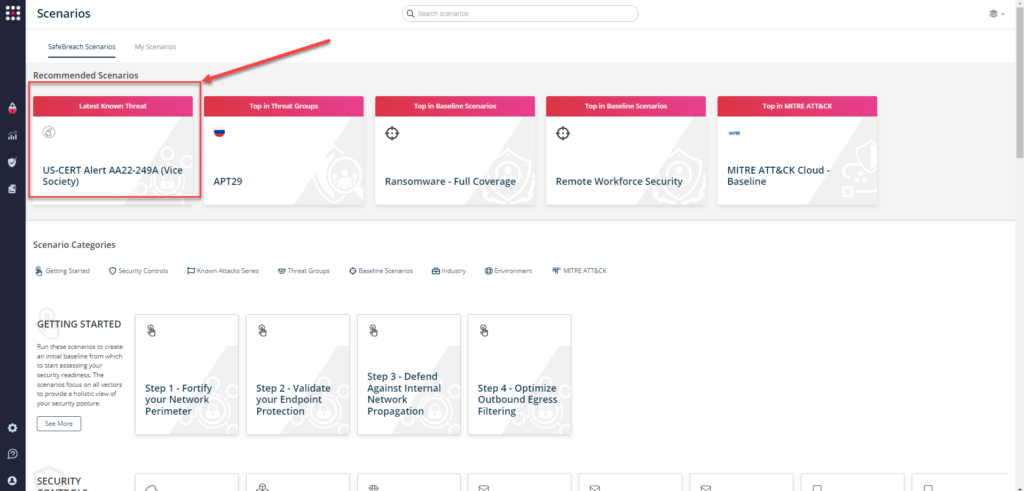
or you can go to “SafeBreach Scenarios” page and choose the US-CERT Alert AA22-249A (Vice Society) scenario from the list of available scenarios.
NOTE: The following actions have been recommended by CISA and the FBI to mitigate any threat arising from Vice Society:
- Prioritize and remediate known exploited vulnerabilities.
- Train users to recognize and report phishing attempts.
- Enable and enforce multifactor authentication.
- Additional recommendations can be seen in the “Mitigations” section here.