On June 14th, the Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), the Multi-State Information Sharing and Analysis Center (MS-ISAC) along with its international cybersecurity partners released an advisory calling out the various indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) being leveraged by the LockBit ransomware operation over the past 3 years. Detailed information is listed in US-CERT Alert AA23-165A – Understanding Ransomware Threat Actors: LockBit.
According to the advisory, LockBit was the most deployed ransomware variant in the world in 2022 and continues to be prolifically used in 2023. Threat actors leveraging LockBit ransomware variants have targeted organizations of all sizes in various critical infrastructure sectors including financial services, food and agriculture, education, energy, government and emergency services, healthcare, manufacturing, and transportation. As the LockBit IOCs and TTPs vary widely depending on the threat actors leveraging them, it is a challenge for organizations to ensure continual protection against them.
Technical Details About LockBit
The LockBit operation typically uses the Ransomware-as-a-Service (RaaS) model. Threat actors maintaining the functionality of a particular LockBit ransomware model typically sell access to that variant to its affiliates, typically for some upfront money and an ongoing cut of the affiliates’ profit. According to the advisory, LockBit has been successful through innovation and ongoing development of the group’s administrative panel and the RaaS supporting functions. Additionally, affiliates that work with LockBit and other notable variants are constantly revising the TTPs used for deploying and executing ransomware, making it harder to detect and stop.
The LockBit ransomware has been involved in over 1700 attacks in the U.S. since 2020 and operators have managed to collect nearly $91M in ransom payments since January 2020 (in the U.S. alone). Once the threat actors steal data from their victims, they typically publish victim names and their data if ransom demands are not met. Since 2021, LockBit threat actors have begun leveraging double extortion – first encrypting victim data and then exfiltrating that data while threatening to post that stolen data on leak sites.
During their intrusions, LockBit affiliates have been observed using various freeware and open-source tools that are intended for legal use. When repurposed by LockBit, these tools are then used for a range of malicious cyber activities, such as network reconnaissance, remote access and tunneling, credential dumping, and file exfiltration. PowerShell and batch scripts are used during system discovery, reconnaissance, password/credential hunting, and privilege escalation.
LockBit threat actors also exploit several vulnerabilities to gain access to victim networks and conduct their malicious operations. Some of these vulnerabilities include:
- CVE-2023-0669: Fortra GoAnyhwere Managed File Transfer (MFT) Remote Code Execution Vulnerability
- CVE-2023-27350: PaperCut MF/NG Improper Access Control Vulnerability
- CVE-2021-44228: Apache Log4j2 Remote Code Execution Vulnerability,
- CVE-2021-22986: F5 BIG-IP and BIG-IQ Centralized Management iControl REST Remote Code Execution Vulnerability,
- CVE-2020-1472: NetLogon Privilege Escalation Vulnerability,
- CVE-2019-0708: Microsoft Remote Desktop Services Remote Code Execution Vulnerability, and
- CVE-2018-13379: Fortinet FortiOS Secure Sockets Layer (SSL) Virtual Private Network (VPN) Path Traversal Vulnerability.
Important Note for SafeBreach Customers – Coverage for AA23-165A (LockBit)
As soon as details were made available, the SafeBreach Labs teams mapped existing attacks and added new attacks to the Hacker’s Playbook immediately. It is important to note that existing SafeBreach customers already had a wide amount of coverage against the IOCs and TTPs being leveraged by the LockBit group. Please run/ re-run the attacks listed below to ensure your environments are protected against this ransomware variant. Additionally, you can also re-run the attacks listed in SafeBreach’s previous LockBit-related coverage blogs: US-CERT Alert (AA23-075A) LockBit 3.0 and SafeBreach adds coverage for new ransomware variants.
Existing Attacks Related to LockBit in SafeBreach Hacker’s Playbook
- #1220 Inject Mimikatz using PowerShell to Extract Credentials)
- #1339 Remote command execution by PSExec
- #2220 Modify a Shortcut using VBScript
- #2221 Modify the Registry Run keys
- #2241 Time providers
- #2267 Add an exclusion to Windows Defender using PowerShell
- #2273 Pass the Hash over SMB using Mimikatz
- #2346 Add a Login Item using AppleScript
- #2350 Modify list of macOS re-opened applications
- #2389 Modify Firewall Rules using netsh.exe
- #2630 Edit the Port Monitor Registry Key
- #2632 Edit the Authentication Package DLL Registry Key
- #3819 Windows Credentials Collection using LaZagne
- #3829 Run obfuscated Mimikatz on host
- #5107 Stop a service using net stop command
- #6001 Full FIN6 attack
- #6127 Extract LSASS memory dump using PowerShell and Rundll32
- #6163 Pre-execution phase of lockbit malware
- #6164 Write lockbit malware to disk
- #6165 Transfer of lockbit malware over HTTP/S
- #6166 Transfer of lockbit malware over HTTP/S
- #6167 Email lockbit malware as a compressed attachment
- #6168 Email lockbit malware as a compressed attachment
- #6473 Agentless lateral movement via RDP
- #6513 Agentless lateral movement via SMB and RCE, using Mimikatz
- #6514 Carbanak UAC Bypass and Credential Dumping
- #6532 Pre-execution phase of LockBit2 malware
- #6533 Write LockBit2 malware to disk
- #6534 Transfer of LockBit2 (8871) malware over HTTP/S
- #6535 Transfer of LockBit2 (8871) malware over HTTP/S
- #6536 Email LockBit2 (8871) malware as a compressed attachment
- #6537 Email LockBit2 (8871) malware as a compressed attachment
- #6538 Pre-execution phase of LockBit2 malware
- #6539 Write LockBit2 malware to disk
- #6540 Transfer of LockBit2 (16cf) malware over HTTP/S
- #6541 Transfer of LockBit2 (16cf) malware over HTTP/S
- #6542 Email LockBit2 (16cf) malware as a compressed attachment
- #6543 Email LockBit2 (16cf) malware as a compressed attachment
- #6544 Pre-execution phase of LockBit2 malware
- #6545 Write LockBit2 malware to disk
- #6546 Transfer of LockBit2 (ba76) malware over HTTP/S
- #6547 Transfer of LockBit2 (ba76) malware over HTTP/S
- #6548 Email LockBit2 (ba76) malware as a compressed attachment
- #6549 Email LockBit2 (ba76) malware as a compressed attachment
- #6552 Pre-execution phase of LockBit 2 malware
- #6553 Write LockBit 2 malware to disk
- #6554 Transfer of LockBit 2 malware over HTTP/S
- #6555 Transfer of LockBit 2 malware over HTTP/S
- #6556 Email LockBit 2 malware as a compressed attachment
- #6557 Email LockBit 2 malware as a compressed attachment
- #6990 Edit the ‘Active Setup’ Registry Key
- #6991 Modify XDG Autostart Entries
- #6995 Register executable to Winlogon Helper DLL
- #7001 Install a print processor
- #7043 Disable Cortex XDR using its default password (Windows)
- #7044 Disable Cortex XDR using its default password (Linux)
- #7144 Unregister anti malware scanning interface providers
- #7266 Write LockBit 3 YXCGT malware to disk
- #7267 Transfer of LockBit 3 YXCGT malware over HTTP/S)
- #7268 Transfer of LockBit 3 YXCGT malware over HTTP/S
- #7269 Email LockBit 3 YXCGT malware as a compressed attachment
- #7270 Email LockBit 3 YXCGT malware as a compressed attachment
- #7271 Write LockBit 3 YXCGD malware to disk
- #7272 Transfer of LockBit 3 YXCGD malware over HTTP/S
- #7273 Transfer of LockBit 3 YXCGD malware over HTTP/S
- #7274 Email LockBit 3 YXCGD malware as a compressed attachment
- #7275 Email LockBit 3 YXCGD malware as a compressed attachment
- #7326 Execute The LockBit Ransomware on user files
- #7554 Clear Windows Event Logs
- #7834 Add Exclusions to Windows Defender
- #7835 Disable Windows Defender From Registry
- #794 Extract Login Information using MimiKatz
- #8018 Web application port scanning
- #8019 Port scanning target simulator
- #8020 Port scanning of local subnet network
- #8023 EDR evasion by overriding `ntdll` .text section
- #8024 EDR evasion by overriding `ntdll` hooked functions
- #8053 Download Lockbit 3.0 ransomware using web browser
- #8101 Write LockBit3 (62db) malware to disk
- #8102 Transfer of LockBit3 (62db) malware over HTTP/S
- #8103 Transfer of LockBit3 (62db) malware over HTTP/S
- #8104 Email LockBit3 (62db) malware as a compressed attachment
- #8105 Email LockBit3 (62db) malware as a compressed attachment
- #8106 Write LockBit3 (da37) malware to disk
- #8107 Transfer of LockBit3 (da37) malware over HTTP/S
- #8108 Transfer of LockBit3 (da37) malware over HTTP/S
- #8109 Email LockBit3 (da37) malware as a compressed attachment
- #8110 Email LockBit3 (da37) malware as a compressed attachment
- #8111 Write LockBit3 (ab92) malware to disk
- #8112 Transfer of LockBit3 (ab92) malware over HTTP/S
- #8113 Transfer of LockBit3 (ab92) malware over HTTP/S
- #8114 Email LockBit3 (ab92) malware as a compressed attachment
- #8115 Email LockBit3 (ab92) malware as a compressed attachment
- #8116 Write LockBit3 (ea95) malware to disk
- #8117 Transfer of LockBit3 (ea95) malware over HTTP/S
- #8118 Transfer of LockBit3 (ea95) malware over HTTP/S
- #8119 Email LockBit3 (ea95) malware as a compressed attachment
- #8120 Email LockBit3 (ea95) malware as a compressed attachment
- #8121 Write LockBit3 (5a56) malware to disk
- #8122 Transfer of LockBit3 (5a56) malware over HTTP/S
- #8123 Transfer of LockBit3 (5a56) malware over HTTP/S
- #8124 Email LockBit3 (5a56) malware as a compressed attachment
- #8125 Email LockBit3 (5a56) malware as a compressed attachment
- #8126 Write LockBit3 (0bd7) malware to disk
- #8127 Transfer of LockBit3 (0bd7) malware over HTTP/S
- #8128 Transfer of LockBit3 (0bd7) malware over HTTP/S)
- #8129 Email LockBit3 (0bd7) malware as a compressed attachment
- #8130 Email LockBit3 (0bd7) malware as a compressed attachment
- #8131 Write LockBit3 (32ce) malware to disk
- #8132 Transfer of LockBit3 (32ce) malware over HTTP/S
- #8133 Transfer of LockBit3 (32ce) malware over HTTP/S
- #8134 Email LockBit3 (32ce) malware as a compressed attachment
- #8135 Email LockBit3 (32ce) malware as a compressed attachment
- #8136 Write LockBit3 (3f6e) malware to disk
- #8137 Transfer of LockBit3 (3f6e) malware over HTTP/S
- #8138 Transfer of LockBit3 (3f6e) malware over HTTP/S
- #8139 Email LockBit3 (3f6e) malware as a compressed attachment
- #8140 Email LockBit3 (3f6e) malware as a compressed attachment
- #8323 Register security support provider (Windows)
- #8774 Write LockBit ransomware to disk
- #8775 Transfer of LockBit ransomware over HTTP/S
- #8776 Transfer of LockBit ransomware over HTTP/S
- #8777 Email LockBit ransomware as a compressed attachment
- #8778 Email LockBit ransomware as a compressed attachment
Newly Added Attacks
- #8962 – Write LockBit3 (7a51) ransomware to disk
- #8963 – Pre-execution phase of LockBit3 (7a51) ransomware (Windows)
- #8964 – Transfer of LockBit3 (7a51) ransomware over HTTP/S
- #8965 – Transfer of LockBit3 (7a51) ransomware over HTTP/S
- #8966 – Email LockBit3 (7a51) ransomware as a compressed attachment
- #8967 – Email LockBit3 (7a51) ransomware as a compressed attachment
What You Should Do Now
The playbook has been updated with new attacks that map to the IOCs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
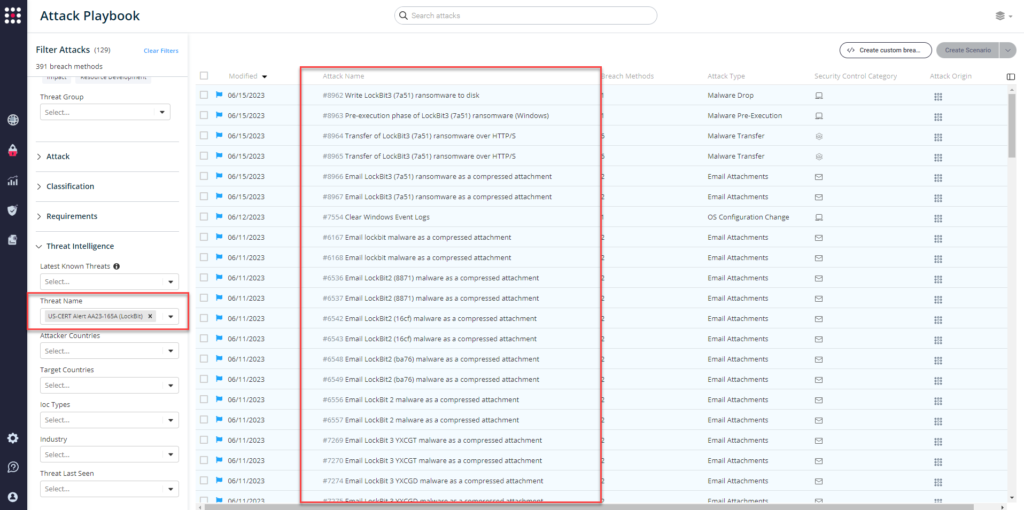
From the Attack Playbook, select and filter attacks related to US-CERT Alert AA23-165A. Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
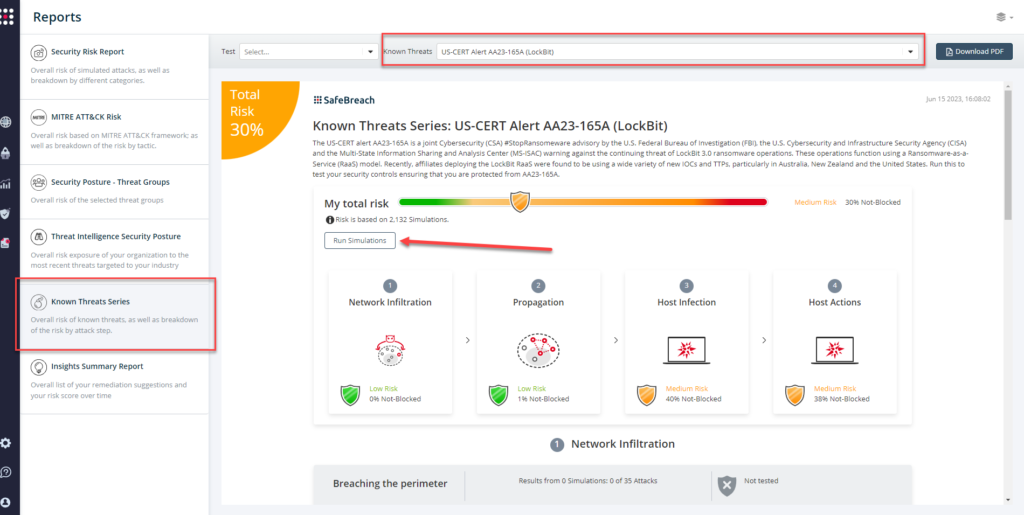
From the Known Attack Series report, select the AA23-165A (LockBit) report and select Run Simulations which will run all attack methods.
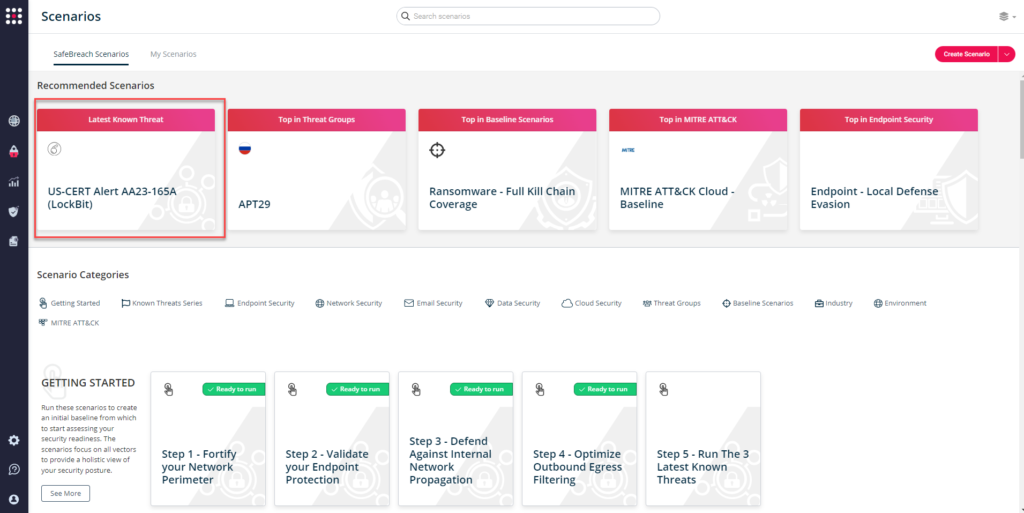
You can also go to “SafeBreach Scenarios” page and choose the AA23-165A (LockBit) scenario from the list of available scenarios.
NOTE: CISA recommends continually validating your security program, at scale, in a production environment to ensure optimal performance against the growing threat of advanced cyber threats. Additional recommendations include:
- Consider implementing sandboxed browsers to protect systems from malware originating from web browsing.
- Require all accounts with password logins.
- Implement filters at the email gateway to filter out emails with known malicious indicators.
- Implement application controls to manage and control execution of software, including allowlisting remote access programs.
- Implement time-based access for accounts set at the admin level and higher.
- Raise awareness for phishing threats in your organization.
- Strictly limit the use of RDP and other remote desktop services.
- Configure the Windows Registry to require UAC approval for any PsExec operations requiring administrator privileges to reduce the risk of lateral movement by PsExec.
- For detailed information about mitigations and incident response, please refer to the full advisory

