SafeBreach Labs has updated the Hacker’s Playbook™ with new attack methods for malware samples described in US-CERT FASTCash 2.0: North Korea’s BeagleBoyz Robbing Banks which addresses yet another serious attack from the Democratic People’s Republic of Korea (DPRK). The BeagleBoyz is identified as a new Threat Group, which is made up of Lazarus Group and APT38 that specifically targets Financial Institutions. The attack is focused on financial gain by accessing bank accounts to steal money from ATMs and also through SWIFT to transfer funds.
The North Korean threat groups are notorious for devastating attacks, including the infamous WannaCry attack in 2017 from Lazarus Group, the attack against Sony Pictures in 2014 in retaliation for ‘The Interview’ film by Guardians of Peace, and the Bangladesh Bank Heist in 2016 where \$81 million was stolen via the SWIFT network, among others. SafeBreach Labs has been tracking their progress and updating the SafeBreach Hacker’s Playbook throughout the years.
Here is an overview SafeBreach Hacker’s Playbook timeline based on US-Cert Alert updates only:
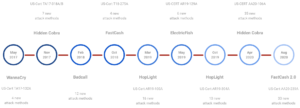
Similar to most DPRK attacks, the BeagleBoyz uses numerous TTPs and malware samples, most of which are already covered in the SafeBreach Hacker’s Playbook. The new attack methods have been added based on this latest US-CERT Alert.
CROWDEDFLOUNDER
Existing Coverage
5 attack methods already covered
ECCENTRICBANDWAGON
New Coverage
#5413 – Write ar20-239a malware to disk (Host-Level)
#5414 – Transfer of ar20-239a malware over HTTP/S (Lateral Movement)
#5415 – Transfer of ar20-239a malware over HTTP/S (Infiltration)
#5416 – Email ar20-239a malware as a ZIP attachment (Lateral Movement)
#5417 – Email ar20-239a malware as a ZIP attachment (Infiltration)
#5429 – Pre-execution phase of aa20-239a_FASTCash_MSIL_exe malware (Host-Level)
#5430 – Write aa20-239a_FASTCash_MSIL_exe malware to disk (Host-Level)
#5431 – Transfer of aa20-239a_FASTCash_MSIL_exe malware over HTTP/S (Lateral Movement)
#5432 – Transfer of aa20-239a_FASTCash_MSIL_exe malware over HTTP/S (Infiltration)
#5433 – Email aa20-239a_FASTCash_MSIL_exe malware as a ZIP attachment (Lateral Movement)
#5434 – Email aa20-239a_FASTCash_MSIL_exe malware as a ZIP attachment (Infiltration)
ELECTRICFISH
Existing Coverage
7 attack methods already covered
FASTCash
Existing Coverage
5 existing attack methods already covered
New coverage
- #5402 – Write ar20-239c malware to disk (Host-Level)
- #5403 – Transfer of ar20-239c malware over HTTP/S (Lateral Movement)
- #5404 – Transfer of ar20-239c malware over HTTP/S (Infiltration)
- #5405 – Email ar20-239c malware as a ZIP attachment (Lateral Movement)
- #5406 – Email ar20-239c malware as a ZIP attachment (Infiltration)
- #5418 – Write aa20-239a_FASTCash malware to disk (Host-Level)
- #5419 – Transfer of aa20-239a_FASTCash malware over HTTP/S (Lateral Movement)
- #5420 – Transfer of aa20-239a_FASTCash malware over HTTP/S (Infiltration)
- #5421 – Email aa20-239a_FASTCash malware as a ZIP attachment (Lateral Movement)
- #5422 – Email aa20-239a_FASTCash malware as a ZIP attachment (Infiltration)
- #5423 – Pre-execution phase of aa20-239a_FASTCash_exe malware (Host-Level)
- #5424 – Write aa20-239a_FASTCash_exe malware to disk (Host-Level)
- #5425 – Transfer of aa20-239a_FASTCash_exe malware over HTTP/S (Lateral Movement)
- #5426 – Transfer of aa20-239a_FASTCash_exe malware over HTTP/S (Infiltration)
- #5427 – Email aa20-239a_FASTCash_exe malware as a ZIP attachment (Lateral Movement)
- #5428 – Email aa20-239a_FASTCash_exe malware as a ZIP attachment (Infiltration)
HOPLIGHT
Existing Coverage
23 existing attack methods already covered
VIVACIOUSGIFT
New Coverage
- #5407 – Pre-execution phase of ar20-239b-MAR-10301706-2 malware (Host-Level)
- #5408 – Write ar20-239b-MAR-10301706-2 malware to disk (Host-Level)
- #5409 – Transfer of ar20-239b-MAR-10301706-2 malware over HTTP/S (Lateral Movement)
- #5410 – Transfer of ar20-239b-MAR-10301706-2 malware over HTTP/S (Infiltration)
- #5411 – Email ar20-239b-MAR-10301706-2 malware as a ZIP attachment (Lateral Movement)
- #5412 – Email ar20-239b-MAR-10301706-2 malware as a ZIP attachment (Infiltration)
Looking back at North Korean attacks on financial institutions BeagleBoyz could be attributed to cyber-enabled financial theft and money laundering, extortion campaigns, and cryptojacking. It is clear they are attacking for financial gain, with estimated thefts of \$2 billion to date.
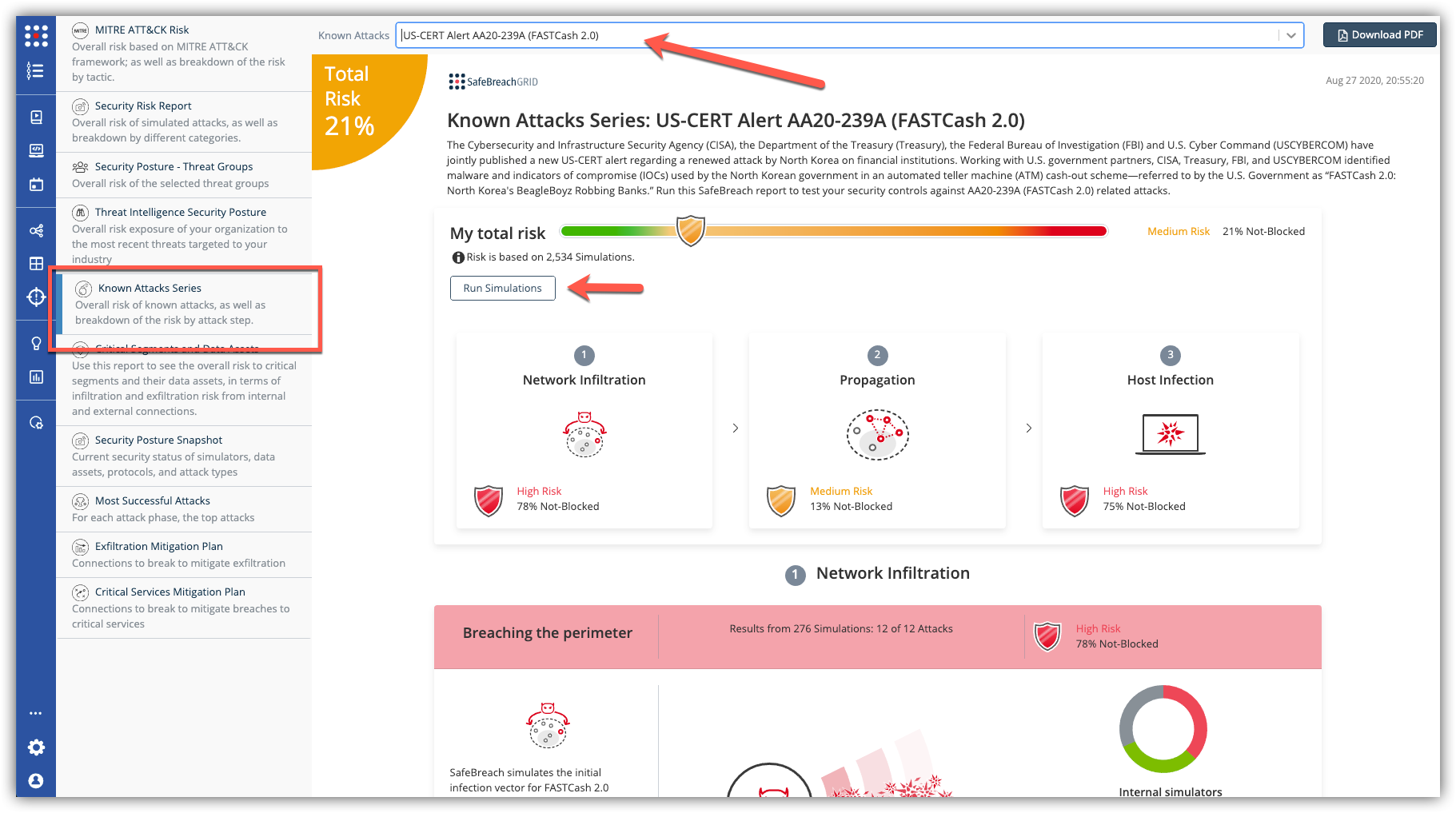
What you want to do
The new attack methods for US-CERT AA20-239A are already in the SafeBreach Hacker’s Playbook and ready to be run across your simulators. The Known Attack Series report is being updated so you can run specifically the attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT Alert AA20-239A (FastCash 2.0) report and select Run Simulations which will run all the attack methods.