The best way to maximize enterprise security is not to patch every vulnerability as soon as it happens. Any good security professional knows that’s simply impossible, even with a huge budget and massive security team. Instead, the most secure enterprises are the smartest enterprises – the companies that can prioritize their time and leverage data and insights to minimize business risk through continuously improving their security posture.
The Four Big Threats Facing Security Teams
Information security is at a crisis point. Enterprises today have never had to protect so many assets, across network, cloud, desktop and laptop, and servers, in so many places, against so many threats. Across the board, the number and type of attacks are increasing. According to Symantec’s 2019 Internet Security Trends Report, the enterprise is increasingly under siege. Web attacks will increase by 56% and enterprise ransomware attacks are up 12% in 2019. Across nearly all categories, focus of attacks is increasingly targeting the enterprise. At the same time, security teams are being forced to cover ever more ground due to changes in the way modern businesses operate. Here is a quick summary of the four big threats facing security teams and why they matter.
First, businesses are moving faster to roll out new products and services; these time-to-market pressures and rapid rollouts of increasingly diverse systems is a growing challenge to security teams. This includes a variety of changes, from the rise of microservices and cloud-native architectures that allow for more developer autonomy to the increasing use of connected devices, to innovations in DevOps that allow for more agile software development and, subsequently, more frequent code releases.
Second, attacks are continuously evolving and attackers continue to be more and more successful. The adversarial security market is a fast growing market. This game puts defenders at a disadvantage as attackers have many failed attempts and need only one success. In contrast, defenders are not allowed to fail – ever. With this ever evolving attack landscape point in -time testing like pen-testing and vulnerability scans are inadequate.
Additionally, there is no super human team that can test all these new and existing attacks on an ongoing basis across the entire network. Humans simply can’t keep up with this problem.
Third, enterprises are dealing with massive technical debt and cognitive overload from the proliferation of security tools and controls. Today, the average large enterprise has between 70 and 100 security controls deployed. But as recent research from Blackhat shows one of the top three things a security team spends their time on is measuring and understanding their security posture. According to a 2018 Enterprise Security Group study for Cisco, 83% of practitioners said that network security is either somewhat more complex or much more complex over the past two years. So, not surprisingly, security teams still struggle to piece together the full risk picture.
Fourth, the massive talent shortage — according to ISC2, there is currently a global infosec pro shortfall of 3 million– leaves a lot of Enterprise companies stranded with infosec risks rapidly rising. Most security teams are understaffed, overwhelmed and hard-pressed to keep up with the most pressing threats and this trend is going to become worse. In other words, no CISO can hire himself out of the talent shortage problem.
Going Beyond Basic BAS With Four Critical Capabilities
In the past few years, BAS has become table stakes for forward thinking information security teams. The great promise of BAS is to enable organizations to understand their security posture by exposing security holes which originate in lack of controls, misconfigured controls or policies or process related causes. According to Gartner 95% of all firewall breaches are caused by misconfiguration, not flaws.
That said, there are four key elements to look for in a BAS platform in order to make sure it will have maximum impact. And some of these elements do not exist in most BAS platforms right now. This should come as no surprise. SafeBreach has long strived to deliver BAS that is a cut above the rest. Our Hacker’s Playbook is the most detailed and most up-to-date programmatically accessible compendium of known attack types, all of which can be run by SafeBreach’s system on a continuous basis without impacting an organization’s assets or networks. So what are the four capabilities?
\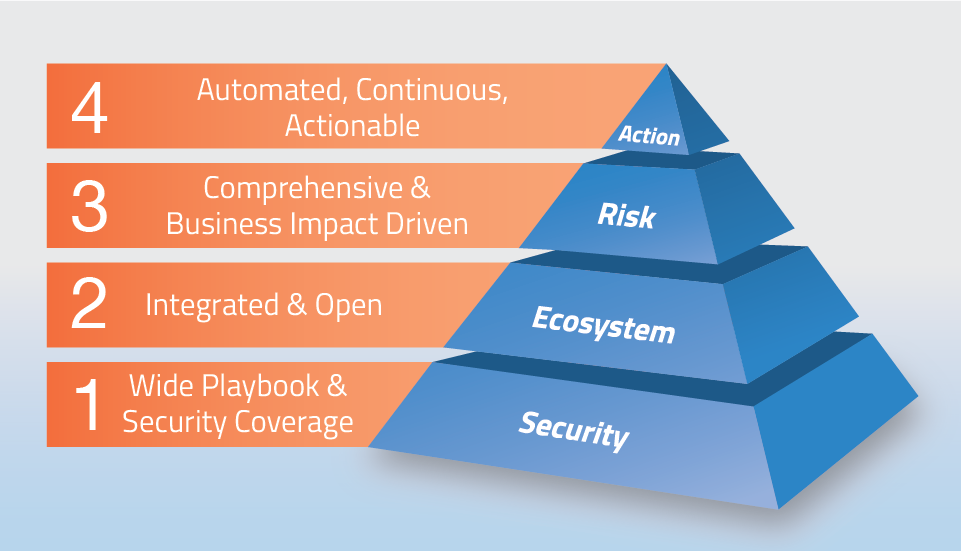
Security Coverage
Comprehensive attack simulation capabilities are the basis of BAS. All BAS platforms include attack simulation capabilities but the differences in their attack simulation approach and efficacy may vary significantly. There are a number of questions that any CISO or VP of Infosec should ask to qualify the security capabilities of a BAS include:
- Does the platform cover enough attacks to be comprehensive? (SafeBreach covers over 7,000, to give you an idea).
- Does the platform cover enough threats across the entire kill chain?
- How are attacks updated in the platform to account for the updates in threat landscape?
- Does the platform enable testing according to the use cases you are interested in comprehensively?
- How safe is the platform in simulating attacks? Is it executing as a form of malware of some other safer form of simulation method?
- How much manual configuration is required in order to run the relevant use case and scale it in an enterprise network?
Ecosystem Integration
Integrating to the technology ecosystem being tested and the existing processes and workflows is key to being successful and getting holistic visibility of your infrastructure. There are several integration types which makes life easier in getting the value out of BAS. The first is automated analysis, the ability to pull events from SIEM and security controls and correlate with simulations performs. This allows an infosec team to understand if a simulation was prevented, detected or missed altogether. Also, correlating automatically with security tools saves loads of time in analysis of the data. By default, this means that a BAS system should integrate out-of-the-box with the majority of widely used security systems across any number of security categories.
BAS should also integrate with SOAR platforms. These platforms can be used to automate remediation workflows including information gathering, analyst checkpoints and actual configuration changes. Workflows can also include retriggerring simulations to validate configuration updates were indeed effective. SOAR platform integrations should also cover integrations with other workflow tools used by DevOps, operations of IT teams, such as Jira, ServiceNow or even DataDog and Slack. The main point is that BAS tools, if properly designed, will integrate seamlessly into workflows that teams already have rather than force behavior changes.
Risk Context
BAS platforms that include a wide playbook of attacks and are able to test those attacks across large networks will usually find a large number of results and security gaps that should be addressed. But throwing a long list of gaps to remediate is not terribly useful. Rather, a modern and effective BAS platform should also answer the questions “Where to start?” and “What should you do first?” To help security teams answer these questions correctly and quickly, BAS platforms must be able to associate each security issue with related business risks – even down to elements such as PII, credit card, or financial data exposure. In this way, BAS rises from platform of detection to platform of intelligence – a critical component of proper risk management. This is a new capability that is delivered in SafeBreach’s new GRID product, elevating SafeBreach BAS to a tool of intelligence.
Insights with Actionable Recommendations
The fourth and final capability an effective BAS platform today must possess is the ability to deliver actionable insights and step-by-step remediation guidance, or the ability to trigger programmatic remediation via DevOps tools. Today very few BAS platforms have this capability. (We are biased but we believe only SafeBreach has this). Effective BAS platforms must package, and make accessible, the data required for each remediation action. This can be done at a single simulation level but preferably, the platform can package a single remediation action to impact multiple simulations and hence significantly reduce risk in one action by allowing security teams to kill many birds with one stone.
Conclusion
With constantly evolving threats and growing business pressures, Information security teams have less margin for error than ever before. And they also need to do more with less – to be smarter and leverage information more effectively to protect their organizations against the biggest risks. A BAS could give you all the information you needed for a decision but lacked the guidance to make decisions effectively – let alone guidance on how much each security fix was actually worth to your business in terms of risk mitigation. Going a step beyond, BAS today should provide precise mitigation steps for every fix- and helps security teams by directing their attention to the most impactful risks, first. We believe that BAS will continue to evolve and incorporate more and more intelligence as it evolves and grows inside the enterprise. If you are thinking of buying BAS, however, make sure to ask about the four areas we discuss above. A bad BAS can actually suck up your team’s time and so more confusion rather than improve security. Choose your BAS wisely and objectively.