In my previous blog, I highlighted the growing prevalence of ransomware attacks and outlined how breach and attack simulation (BAS) tools can effectively help security teams prepare for such threats. But, not all BAS tools are created equal. SafeBreach offers a powerful and versatile BAS tool that allows security teams to safely execute a variety of realistic and advanced attacks against their security controls to gain visibility into security gaps. As a result, they are able to improve the efficacy of the security operation center (SOC) by reducing the mean-time-to-detect (MTTD) and mean-time-to-respond (MTTR). When helping prepare for a ransomware attack, SafeBreach offers a host of unique, built-in capabilities that enable security teams to understand the scope and nature of the attack by thinking like the attacker.
Below, I’ll provide an in-depth overview of these capabilities, including the SafeBreach Hacker’s Playbook™, the industry’s largest continuously updated attack playbook, and our 24-hour commitment to adding newly identified relevant attacks. I’ll also explain the benefits of SafeBreach Scenarios, our customizable executive dashboards that help organizations understand, manage, and communicate their posture, and the newly launched Ransomware Assessment Challenge, executed by SafeBreach cybersecurity experts.
The Hacker’s Playbook is constantly updated by the SafeBreach Labs research team with the latest attack tactics and techniques. SafeBreach users can immediately check if their organization is protected against any newly discovered ransomware and other advanced threats.
The SafeBreach 24-hour US-CERT Alert SLA
Our researchers continuously identify and publish new, original threat research and attack methods as part of our commitment to provide users with the most up-to-date “simulated hacker” experience available. SafeBreach is the only BAS solution in the industry to offer a 24-hour SLA—we add attacks identified from US-CERT Alerts and other high-priority alerts into our Hacker’s Playbook within 24 hours of being notified, guaranteed.
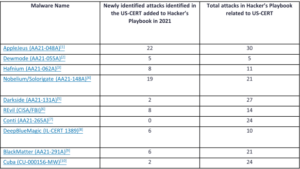
In 2021 alone, we added 120 new attacks identified in US-CERT and other high-profile alerts, including several new malware, 0-days, and critical vulnerabilities. 78 additions were ransomware-specific attacks in 2021, as noted in the table below.
SafeBreach Scenarios
SafeBreach Scenarios provide templates to create and run tests that cover prevalent attacker behaviors that may lead to cyberattacks on organizations. Each SafeBreach Scenario covers a use case from the real world that is organized into a sequence of steps, mimicking the threat’s progression. This enables an organization to validate its protection against those threats more realistically.
By providing pre-defined attack stories, SafeBreach makes it quicker and easier to leverage the various attack capabilities and understand which attack methods need to be tested. SafeBreach Scenarios enable security teams to easily find and execute attacks that help them reach the level of continuous visibility needed to achieve a hardened security posture. They can search for specific ransomware scenarios or for a more comprehensive ransomware baseline to quickly identify and select the threats that matter most to their organization.
MITRE ATT&CK® Board
SafeBreach’s MITRE ATT&CK board mirrors the MITRE ATT&CK Enterprise matrix, summarizing the findings for each technique and tactic run as a simulation in an organization’s specific environment. Security teams can simulate ransomware-focused attacks and leverage the MITRE ATT&CK board to understand the scope and the breadth of the attack behaviors based on the MITRE ATT&CK lifecycle. This interactive heatmap helps organizations quickly visualize their security posture, focus on the areas most in need of remediation, and bring security and infrastructure teams together to update security controls and more effectively harden defenses.

SafeBreach Ransomware Assessment (SafeBreach-as-a-Service)
The NEWLY launched SafeBreach Ransomware Assessment is a free assessment designed to help organizations understand their level of vulnerability to specific ransomware attacks and provide actionable intelligence about the immediate steps they can take to minimize their risk. This proprietary, research-based assessment tests against credential theft, malware transfer and execution, and post-exploitation behaviors, including command and control communications and reconnaissance. Participants will receive a customized report with key findings and actionable remediation guidance. Click here to learn more about our new offering.
Preparing for Advanced Malware Attacks with SafeBreach
Using SafeBreach to prepare against ransomware or other malware attacks can provide immediate value with a clear business impact, including the ability to understand the efficacy of existing security stacks, identify gaps, reduce risk, inform budgeting decisions, and support alignment across the company. SafeBreach can provide quantitative metrics around an organization’s current state of preparedness across all stages of the advanced attack execution (end-to-end), as well as the ability to track baselines over time.

Conclusion
SafeBreach can be a crucial ally in any organization’s fight against advanced ransomware threats, helping to develop a more offensive security strategy and hardening security postures based on contextual, data-driven insights. SafeBreach helps organizations proactively understand their risk, make informed decisions, and prioritize improvement efforts and resources that will make the biggest impact in protecting their environment.
Ready to get started now? Apply to participate in our SafeBreach Ransomware Challenge today and see how SafeBreach can help secure your organization against ransomware and other advanced threats.
References
[1] AppleJeus (AA21-048A) – https://www.safebreach.com/blog/2021/us-cert-alert-aa21-048a-applejeus-analysis-of-north-koreas-cryptocurrency-malware/
[2] Dewmode (AA21-055A) – https://www.safebreach.com/blog/2021/us-cert-alert-aa21-055a-web-shell-dewmode/
[3] Hafnium (AA21-062A) – https://www.safebreach.com/blog/2021/us-cert-alert-aa21-062a-mitigate-ms-exchange-server-vulnerabilities/
[4] Nobelium/Solorigate (AA21-148A) – https://www.safebreach.com/blog/2021/us-cert-alert-aa21-148a-sophisticated-spearphishing-campaign-targeting-government-organizations-igos-ngos/
[5] Darkside (AA21-131A) – https://www.safebreach.com/blog/2021/darkside-randsomware-attacks/
[6] ReVil (CISA/FBI) – https://www.safebreach.com/blog/2021/kaseya-vsa-ransomware-attack/
[7] Conti (AA32-265A) – https://www.safebreach.com/blog/2021/existing-coverage-in-safebreach-hackers-playbook-for-us-cert-alert-aa21-265a-conti-ransomware/
[8] DeepBlueMagic (IL-CERT 1389) – https://www.safebreach.com/blog/2021/safebreach-hacker-s-playbook-updated-for-il-cert-alert-1389-deepbluemagic-ransomware-attacks/
[9] BlackMatter (AA21-291A) – https://www.safebreach.com/blog/2021/safebreach-hacker-s-playbook-updated-for-us-cert-alert-aa21-291a-blackmatter-ransomware/
[10] Cuba (CU-000156-MW) – https://www.safebreach.com/blog/2021/safebreach-hacker-s-playbook-updated-for-fbi-flash-alert-cu-000156-mw-cuba-ransomware-attack-campaign/